Top tools for password-spraying attacks in active directory networks
Password guessing is essentially an art form when this attack is performed on a large scale against a large group of users. Password spraying attacks are part of this landscape, and they can be carried out in different situations, including active directory networks. In short, this attack attempts to authenticate into many user accounts using the same password. Because of this, corporate networks are often targeted, as obtaining usernames from a company can be an easy task these days with the help of OSINT techniques simply by using social networks such as LinkedIn or Facebook.

What should you learn next?
According to Microsoft, the three steps to conduct a password-spraying attack are:
- Acquire a list of usernames: starting with a list of names: firstname.lastname@company.com
- Spray passwords: testing popular and common passwords (123456, password, and Winter21!). See the top 10,000 passwords. )
- Gain access: one of the tested attempts works, and the account can be abused to enumerate assets in the AD network, exploit authenticated services and put the organization at risk.
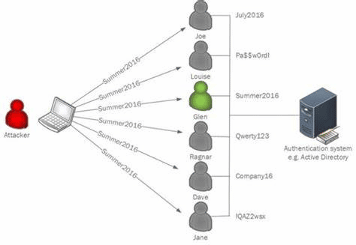
Figure 1: Workflow where the password "Summer2016" was spread against an Active Directory network. The user "Glen" was a match, and privileged access over the corporate network was obtained.
Popular tools for password spraying attacks
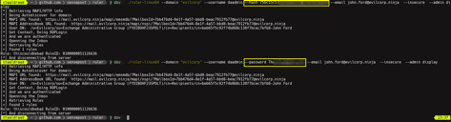
MSOLSpray
MSOLSpray is a password spraying tool used against Microsoft Online accounts (Azure/O365). In detail, the script logs if a user cred is valid, the MFA mechanism is enabled, if the user account doesn't exist, is locked, or is disabled.
This tool can be used with the following commands:
Import-Module MSOLSpray.ps1Invoke-MSOLSpray -UserList .\userlist.txt -Password Winter2020
URL: https://github.com/dafthack/MSOLSpray
Ruler
Ruler is a tool used to interact with Exchange servers. The main goal of the ruler is to abuse the client-side Outlook features, including performing password-guessing attacks and gaining remote privileges.
URL: https://github.com/sensepost/ruler
CrackMapExec
CrackMapExec, also called CME, is a tool that helps to automate the security of large Active Directory networks. To perform password spraying attacks with CME, we can use the next command:
#~ cme smb 192.168.1.101 -u /path/to/users.txt -p Summer18Other CME commands can be seen here.
URL: https://github.com/byt3bl33d3r/CrackMapExec
Kerbrute
Kerbrute is a tool created to guess and enumerate Active Directory accounts through Kerberos Pre-Authentication.
Kerbrute can be executed using the following commands:
./kerbrute_linux_amd64 userenum -d lab.ropnop.com usernames.txt./kerbrute_linux_amd64 passwordspray -d lab.ropnop.com domain_users.txt Password123
./kerbrute_linux_amd64 bruteforce --dc 192.168.x.x -d domain users.txt --safe -o out.txt
URL: https://github.com/ropnop/kerbrute
Talon
Talon is a tool created to execute password guessing attacks while remaining undetected. Talon can use a single domain controller or multiple ones to perform these guessing attacks, randomizing each attempt between the domain controllers and services (LDAP or Kerberos).
Talon can be used with the following command:
root@kali:~# ./Talon -Hostfile DCs -Userfile ValidUsers -D STARLABS.local -P "Password!" --sleep 2URL: https://github.com/optiv/Talon
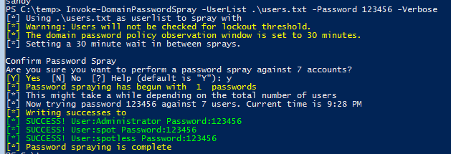
DomainPasswordSpray
DomainPasswordSpray is a tool developed in PowerShell to perform a password spray attack. By default, it will automatically generate the user list from the domain.
Command to execute the script:
Invoke-DomainPasswordSpray -UserList .\users.txt -Password 123456 -VerboseURL: https://github.com/dafthack/DomainPasswordSpray
Lyncsmash
This is a collection of tools to enumerate and attack self-hosted Skype for Business and Microsoft Lync installations.
The tool can be executed with the following commands:
python lyncsmash.py enum -H 2013-lync-fe.contoso.com -U usernamelist.txt -P passwordlist.txt -d CONTOSO -o CONTOSO_output.txtpython lyncsmash.py enum -H 2013-lync-fe.contoso.com -U usernamelist.txt -p Winter2017 -d CONTOSO
URL: https://github.com/nyxgeek/lyncsmash

What should you learn next?
Password spraying
Password spraying attacks are often the first test conducted to verify the security of a corporate network. As it is easy to obtain valid usernames from a target corporation, criminals have abused this attack to get an initial foothold over internal networks. Because of this, active defense is needed, ensuring that weak and popular passwords are not used by employees to put at risk the internal servers.
On the other hand, setting account lockout policies after some failed attempts is also a good measure to mitigate the risks. Implementing a CAPTCHA mechanism and the usage of multi-factor authentication can also limit the possibility of a well-succeeded attack.
Sources
- Protecting your organization against password spray attacks, Microsoft
- Password Spraying, GitBook - Segurança-Informática
- Password Spraying Attack, OWASP