What is a side-channel attack?
Introduction
The origin of the side-channel attack is closely related to the existence of physically observable phenomena caused by the execution of computing tasks in microelectronic devices and common systems. For example, microprocessors consume time and power to perform their assigned tasks. Devices keep their secrets, and if criminals understand the unintended signals, some interesting secrets could be extracted and used to perform a side-channel attack. The same happens, for instance, when a timing attack on a web system is executed to enumerate possible valid users.
These kinds of attacks take advantage of patterns of information. For example, the electric emissions from a computer's monitor or hard drive that could be used to analyze that type of information are displayed on the screen, or the scenario where computer components draw different amounts of power when carrying out certain processes.

What should you learn next?
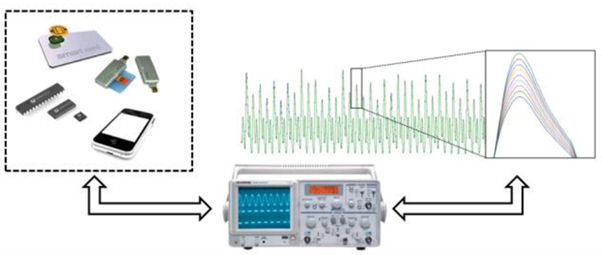
The usage of this kind of attack could be very dangerous because a different landscape is used to explore vulnerabilities in relation to conventional approaches. As shown in Figure 1 below, signals from popular devices such as smartphones, embedded devices and IoT landscape have been used to find vulnerabilities, extract sensitive information or behaviors by analyzing the signal frequency in a specific period of time (inputs and outputs).
Figure 1: Obtaining side signals from popular devices (source)
Another popular side-channel attack example depicting the scenario from Figure 1 is the use of the sounds of a key to create a key replica via 3D printers.
The big picture of side-channel attacks
"Usually when we design an algorithm we think about inputs and outputs. We don’t think about anything else that happens when the program runs," says Daniel Genkin, a computer scientist at the University of Michigan.
Computers run on physics, and there are many lateral physical effects that can be analyzed, including the time, power, and sound. These are three important ingredients that could be explored in the wild by crooks. For instance, a timing attack is a side-channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute cryptographic algorithms.
Another familiar scenario from the web surface is the blind SQL time-based attack. Here, the functions WAIT FOR DELAY can be used to suspend the execution for the specified amount of time or WAIT FOR TIME can be used to suspend the execution of the query and continue it when system time is equal to the parameter. By using this method, an attacker enumerates each letter of the desired piece of data using the following logic:
- If the first letter of the first database’s name is an “A”, wait for 10 seconds.
- If the first letter of the first database’s name is a “B”, wait for 10 seconds.
- [etc.]
In detail, these attacks exploit one of those effects to get more information about the secrets of the used algorithm.
From the attacker viewpoint, practically any accidental information leakage can be harvested to learn something they're not supposed to.
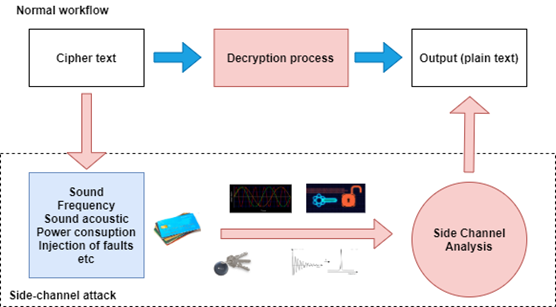
Figure 2 below presents how a side-channel attack could be used to get the secrets of a normal application workflow and take advantage of side information such as sound, frequency, power consumption and so on to get the final output (e.g., the plaintext from a ciphertext).
Figure 2: Normal workflow versus a side-channel attack scenario.
Computing systems are more sophisticated now, with components pushed to their physical limits and going in all directions and using all the possible information to fit the best results. In this sense, side-channel attacks are becoming more plentiful and hard to detect and prevent.
As an example, several bugs were detected in the last years on the most popular physical equipment, with names like Meltdown, Spectre, Fallout, RIDL and Zombieload, all of them taking advantage of side-channel attacks as part of their secret-stealing techniques.
Let’s look at each of those in detail.
Meltdown: This is a hardware vulnerability that affects Intel x86 microprocessors, IBM POWER processors and some ARM-based microprocessors. In detail, it allows a rogue process to get all the memory, even when it is not authorized to do so.
Spectre: This is a vulnerability that affects modern microprocessors that implement branch prediction. On most processors, the speculative execution resulting from a branch misprediction may leave observable side effects that may reveal private data.
Fallout: The Fallout attack allows to get data that the operating system recently wrote and to figure out the memory position of the operating system strengthening other attacks.
RIDL: The RIDL attack can be used to leak information across various security domains from different buffers, such as line-fill buffers and load ports, inside Intel processors.
ZombieLoad: The ZombieLoad attack resurrects private browsing history and other sensitive data. It allows to leak information from other applications, the operating system, virtual machines in the cloud and trusted execution environments.
Free hour-long hacking course!
Learn how to hack and use AI in this free 1-hour course, led by Keatron Evans, 20-year cybersecurity veteran and VP of Portfolio Product and AI Strategy at Infosec!
Final thoughts
Side-channel attacks have been a hot topic in the last few years and becoming a more sophisticated horizon used to explore a group of vulnerabilities on physical equipment or using signals to reveal the secrets of a workflow, communication channel or cipher tunnel.
Meltdown and Spectre are the real proof of this dangerous attack, exploring vulnerabilities that affect microprocessors and taking advantage of a time-based side-channel attack. Each uses different techniques to access the secret information and decode it in a processor’s cache — a part of memory designed to keep certain data close at hand for better efficiency. Within this context, an attacker can analyze the timing of the processor’s responses and learn what the cache is leaking, and thus, the secret information.
Preventing these kinds of scenarios is a hard task, but there is a group of best practices that can be followed as stated by OWASP. For instance, the fix of response times to the worst-case execution time could be a good workaround to prevent time-side channels but with a serious performance impact.
On the other hand, side-channel attacks on web applications can also constitute a big problem. Learn the existence of user name from response times or error messages that could be used to exfiltrate information from a target system.
Side channels appear in various ways. Detection and prevention is a serious challenge and often may have a negative impact on the system’s performance.
Sources
This Radio Bug Can Steal Laptop Crypto Keys, Fits Inside a Pita, Wired
Paul Kocher, Joshua Jaffe, and Benjamin Jun, "Differential Power Analysis", Cryptography Research, Inc.
The Sounds a Key Make Can Produce 3D-Printed Replica, Threatpost
Investigadores descobriram uma maneira de criar um super-malware implantado em enclaves da SGX, Segurança Informática
Side Channel Vulnerabilities on the Web - Detection and Prevention, OWASP