Network Traffic Analysis for Incident Response: Internet Protocol with Wireshark
Introduction to the Internet Protocol
The Internet Protocol (IP) is the most widely-used network-level protocol. Common transport-level protocols, the Transport Control Protocol (TCP) and the User Datagram Protocol (UDP), are encapsulated within IP packets.
The purpose of IP is to make networks like the internet possible. Within a subnet, it is possible to route traffic at the physical layer using MAC addressing; however, this approach doesn’t scale. As a result, the internet works using IP addresses, which uniquely identify computers on the internet. The Internet Protocol layer contains these addresses and is used to route traffic through the internet.
Learn Network Traffic Analysis for Incident Response
IP in Wireshark
IP is unusual in that there isn’t only one version of IP traffic headers. Most of the internet operates based off of IP version 4 or IPv4. This form of traffic header uses IP addresses in the range of 0.0.0.0 to 255.255.255.255 .
However, IPv4 isn’t the most recent version of the IP protocol. In 1995, RFC 1883 was published, officially specifying the current version of the IP version 6 (IPv6) protocol. IPv6 was designed to solve the problem of IPv4 address exhaustion, which was the concern that there would be more computers on the internet than there were possible IP addresses. This concern was valid, especially since there are at least 4,536,248,808 internet users and only 4,294,967,296 possible IPv4 addresses (not taking into account the private IPv4 address ranges that cannot be allocated to a specific user).
The planned switchover from IPv4 to IPv6 never happened due to the widespread usage of Network Address Translation (NAT). With NAT, an entire organization’s network can have a single IP address on the public internet and be uniquely addressed internally using private IP address ranges (10.0.0.0/8,172.16.0.0/12 and 192.168.0.0/16).
However, some computers and subnets have switched over to IPv6. As a result, it is possible that a network traffic capture will contain IPv6 traffic carried over the IPv4 protocol.
IPv4
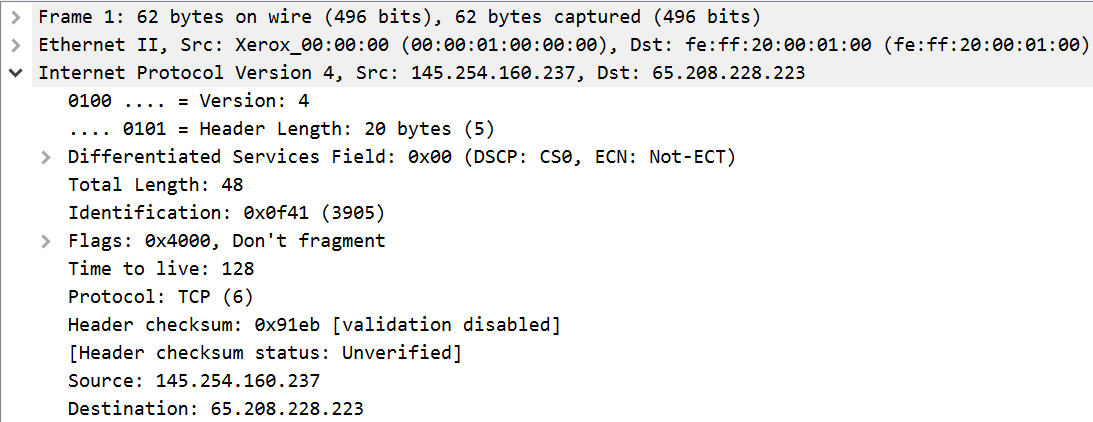
IPv4 is the primary Internet Protocol in use. Its addresses are written as four dot-separated octets, each with possible values of 0–255. A range of IPv4 addresses can be specified by writing the first address in the range and the number of bits that are uniquely specified. For example, 10.0.0.0/8 indicates the range 10.0.0.0–10.255.255.255 (since only the first eight bits are specified), while 10.0.0.0/16 indicates the range 10.0.0.0–10.0.255.255.
The image above shows a screenshot of an IPv4 header in Wireshark. The purpose of this header is to describe how a certain packet should be handled during routing. Significant ones for routing include:
- Version: Specifies that this is an IPv4 header (important since IPv6 is also in use)
- Differentiated Services: Specifies special requirements of the traffic (like how VOIP requires real-time data streaming)
- Identification: Uniquely identifies a set of fragments
- Flags: Specify if a packet can be fragmented and if so, whether or not the current packet contains the final fragment
- Time to live: The number of jumps that a packet can pass through before being dropped
- Protocol: The type of traffic encapsulated within the IPv4 packet
- Source and Destination: IPv4 address of sender and recipient
IPv6
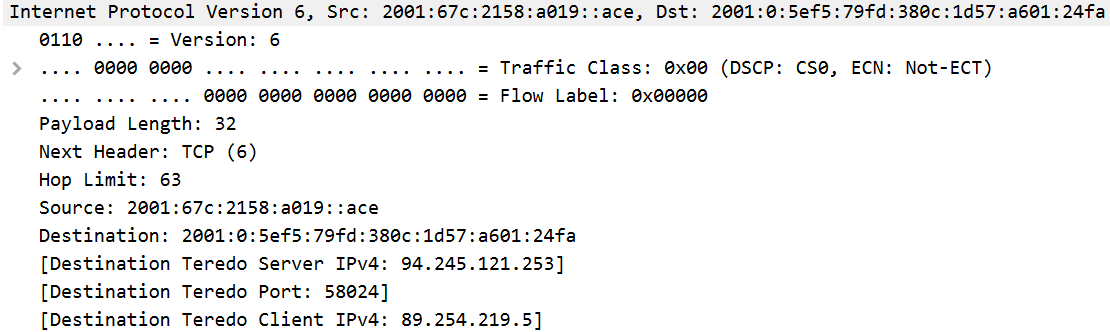
IPv6 is designed to expand the space of possible addresses on the internet. As a result, it uses a much longer address. An IPv6 address looks like 2001:0:5ef5:79fd:380c:1d57:a601:24fa, where each value between the colons is written in hexadecimal and can be in the range of 0000–ffff.
IPv6 addresses are also more condensable than IPv4. An IPv6 address can be written so that a group of all zeros (or a series of them) can be dropped and leading zeros within a group don’t need to be included. For example, 2001:067c:2158:a019:0000:0000:0000:ace is simplified to 2001:67c:2158:a019::ace. Since the number of dropped groups is not specified and is calculated from context, this can only be done once within an IPv6 address.
The screenshot above shows an IPv6 header in Wireshark. As shown, the fields are largely the same as those in IPv4 but organized differently.
IPv6 over IPv4
IPv6 is an accepted standard for addressing and routing on the internet. However, there has never been an official shift from IPv4 to IPv6 since the expected exhaustion of IPv4 addresses never occurred.
Since the majority of the internet runs on IPv4, IPv6 users wishing to communicate using existing infrastructure must use IPv6 tunneling protocols. A variety of different options exist, but two of the more common are 6in4 and 6to4.
The image above is a screenshot of the 6in4 protocol in Wireshark. As shown, the IPv6 packet is encapsulated within an IPv4 packet. This protocol is used with pre-configured tunnels, where IPv4 is used to route the traffic to the destination IPv6 network’s gateway and IPv6 is then used to route the packet to the intended destination.
Another option for carrying IPv6 traffic over IPv4 infrastructure is 6to4. In this protocol, all IPv6 relays are assigned the IPv4 address of 192.88.99.1, so this will always be the destination address of the IPv4 header.
In 6to4, IPv6 addresses are based off of IPv4 addresses. The screenshot above shows headers using 6to4. In binary, the source IPv4 address of 70.55.213.211 is:
01000110.00110111.11010101.11010011
In binary, the source IPv6 address of 2002:4637:d5d3::4637:d5d3 is:
0010000000000010:0100011000110111:1101010111010011:0000000000000000:0000000000000000:0000000000000000:0100011000110111:1101010111010011
The bolded characters in each are identical, so the complete IPv4 address is embedded in the IPv6 address.
IP analysis for incident response
As one of the most common routing protocols, IP is used in the vast majority of cyberattacks. The main feature of IP that is abused by attackers is the fact that the source IP address of a packet can be spoofed. This is used in a variety of different attacks, including idle scans and distributed denial-of-service (DDoS) amplification attacks.
However, the time to live (TTL) field in IPv4 and the hop count in IPv6 are also useful in hacking. Tools like traceroute and Firewalk, which is used to learn what types of traffic a firewall allows or filters, modify the TTL or hop count fields in an IP header.
By sending a number of different packets with incrementing TTLs and examining the resulting error messages, the user can learn the number and IP addresses of the hops between the sender and the target. In the case of Firewalk, sending traffic with a TTL one hop further than the firewall for different protocols enables the attacker to differentiate allowed protocols (which result in ICMP_TIME_EXCEEDED errors) and filtered protocols (which receive no response).
Conclusion: Investigating IP in Wireshark
When investigating suspicious traffic in Wireshark, typically the attack will be detected at a higher level in the OSI model. Once the attack is identified, it is possible to draw conclusions about how the IP header may have been modified. Scanning using traceroute or Firewalk can be identified by packets with unusual TTLs or a high rate of ICMP_TIME_EXCEEDEED errors.
Learn Network Traffic Analysis for Incident Response
Sources
- RFC 1883 - Internet Protocol, Version 6 (IPv6) Specification, tools.ietf.org
- SampleCaptures, Wireshark
- 3.1. Configured Tunnels (Manual Tunnels / 6in4), tools.ietf.org