Network traffic analysis for IR: Analyzing fileless malware
Introduction to fileless malware
Fileless malware is malware authors’ response to traditional malware identification and analysis techniques. Many antiviruses operate by using signature-based analysis to identify malicious files on a computer. By ensuring that a malicious file is never saved on the filesystem, malware authors can make their attacks much more difficult to detect and remediate using traditional analysis techniques.
Malware authors can avoid writing their malicious code to the filesystem in a variety of different ways. Some malware “lives off the land” by using functionality built into legitimate Windows programs. Tools such as PowerShell on Windows have a great deal of power and the functionality desired by hackers. The ability to execute PowerShell commands on a computer is as good as, if not better than, dropping and running a malicious executable on the machine.
Learn Network Traffic Analysis for Incident Response
Other options include the use of DLL injection and similar techniques that insert malicious code into a legitimate process. Reflective DLL injection can accomplish this without saving a file to the filesystem, making the malware harder to analyze.
Regardless of the method used to make malware fileless, the important information about the attack is stored in network logs. Many fileless malware infections are implemented as multi-stage malware, where a Trojan (like a malicious Word document) is used to infiltrate the system and later downloads the malicious code to be injected into a running process. The ability to extract this downloaded malware from packet captures can be invaluable for incident response.
Extracting files from packet captures
The ability to examine malicious code is often a critical step in digital forensics and incident response. Being able to examine the code and configuration information of a malware sample can help to determine the intended functionality of the malware or determine how to interpret command-and-control traffic in order to determine the scope of data exfiltration efforts.
The purpose of fileless malware is to ensure that a copy of the malware’s code is not left on the file system. However, if the malware is transferred over the network, a full copy of the code may be included in network traffic logs. By extracting the fileless malware from traffic capture files, an incident responder can collect the necessary information for forensic analysis.
NetworkMiner and Wireshark are two tools commonly used in network traffic analysis. Both of them have the ability to extract files from a network traffic sample.
NetworkMiner
NetworkMiner is a network traffic analysis tool produced by NETRESEC. It is available in a free or paid version from their website. Unlike Wireshark, NetworkMiner isn’t designed for examination of individual packets. Instead, it makes it easy for an analyst to extract a large amount of specialized information from a packet capture.
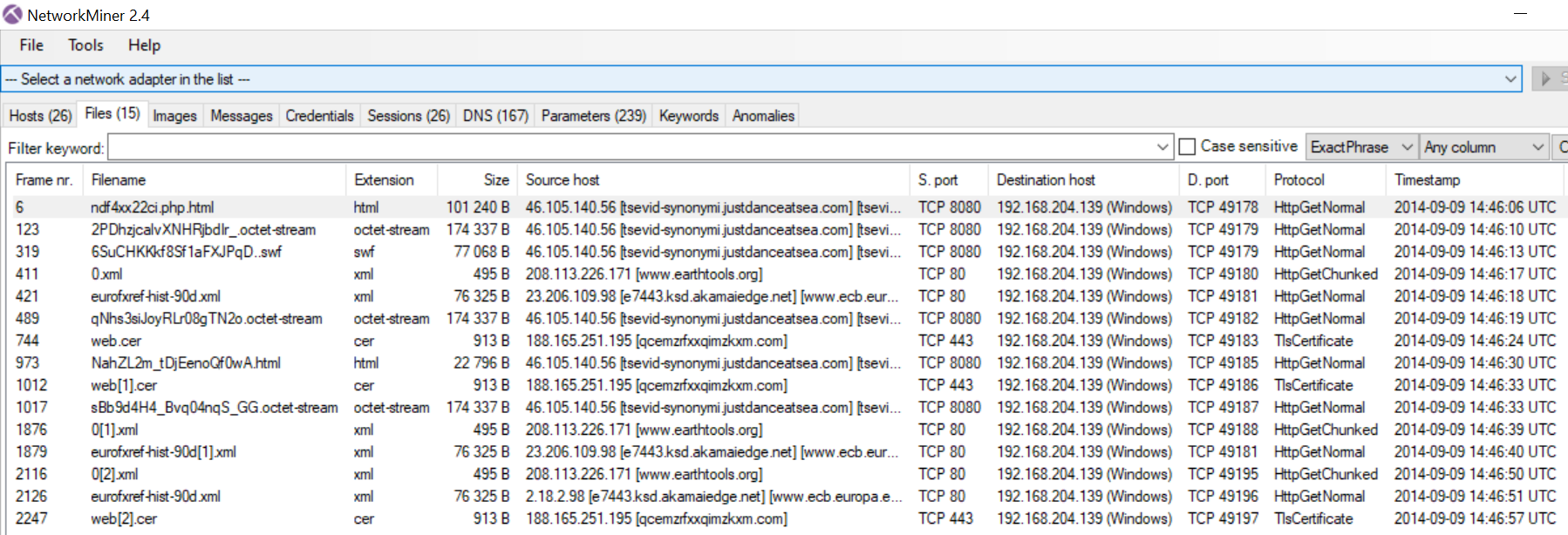
One of the main benefits of NetworkMiner is the ease of extracting files embedded in a network packet capture. The tool includes a Files tab that is automatically populated with any files that NetworkMiner identifies within a traffic capture.
The image above shows the Files tab of NetworkMiner after opening a packet capture in the tool. As shown, the tool provides a great deal of information about an identified file including:
- Frame number
- File name, extension and size
- Source and destination host and port
- Timestamp
Right-clicking on a particular file provides the option to calculate file hashes, which is useful when using tools like VirusTotal that use this information for identifying and indexing files.
NetworkMiner also automatically extracts and reconstructs files found in network traffic captures. They are placed in the Assembled Files folder within NetworkMiner’s directory. This makes NetworkMiner one of the most convenient tools available for extracting files from network traffic captures.
Wireshark
Wireshark is a free and open-source network traffic analysis tool. It is commonly used for examining packets that are flowing over the network, but it can also be used to extract files from network traffic captures.
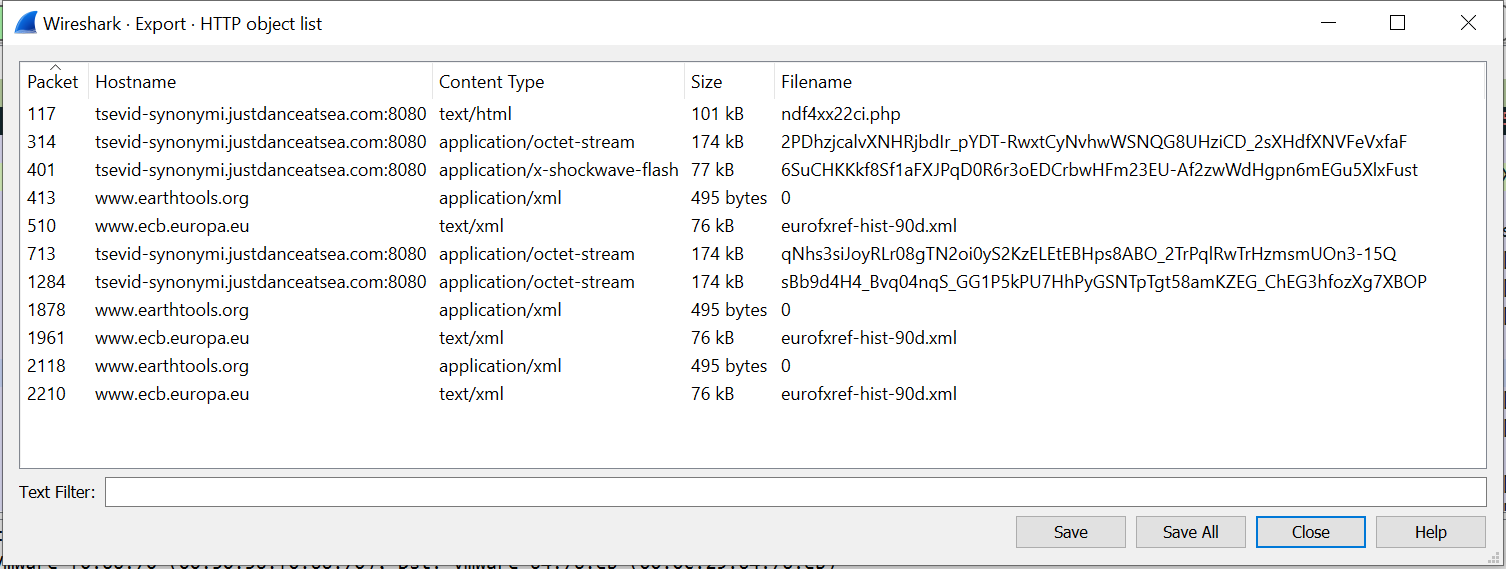
In order to extract a file from Wireshark, it’s necessary to know how it is being transferred over the network. For example, a malware sample may be retrieved using an HTTP GET request. Once the protocol is known, files can be extracted via File → Export Objects → <Protocol Name>.
The image above shows the results of attempting to extract HTTP objects via Wireshark from the same traffic capture used in the NetworkMiner example. The same files are available for extraction and can be saved individually or all together.
Conclusion: NTA for fileless malware analysis
Network traffic analysis can be a critical stage of analyzing an incident involving fileless malware. Some malware variants delete files from the machine after execution to complicate reverse engineering; however, these files can often be restored from the file system or backups. Fileless malware takes this logic a step further by ensuring that malware is never saved to the file system at all. This complicates the use of host-based antivirus programs and collection of malware samples for forensic analysis.
However, even fileless malware cannot avoid being stored in network traffic logs if the initial infection vector is via a network connection with logging enabled. Assuming that an incident responder has the ability to read the traffic flowing over a network connection (i.e. performing TLS decryption if necessary), fileless malware can be viewed in the network traffic logs. With tools like NetworkMiner and Wireshark, these malware samples can be extracted from the logs for analysis with traditional malware analysis tools like IDA Pro or Ghidra.
The ability to perform forensic analysis of fileless malware is extremely valuable for the incident response process. A great deal of research and development effort has been poured into tools designed to make malware analysis easier for the analyst and to enable rapid extraction of indicators of compromise. Since these techniques are often based upon access to a sample of the malware or knowledge of its file hash (for services like VirusTotal), the ability to extract the malicious code from traffic captures is extremely important.
Learn Network Traffic Analysis for Incident Response
Sources
- Fileless malware isn't new, but it's becoming an increasingly prevalent threat., Roland Schorr & Tower
- NetworkMiner, Netresec
- Download Wireshark, Wireshark