Network Traffic Analysis for IR — Discovering RATs
Introduction
A Remote Access Trojan (RAT) is part of the malware family. It enables covert surveillance, a backdoor channel and unfettered and unauthorized remote access to a victim’s computer. Using this malware, attackers can remotely perform various illegal activities on a victim machine, such as manipulating files and installing and removing programs.
Discovering RATs is not an easy task, as they neither show up on running processes nor slow down the computer speed. Nevertheless, incident response (IR) teams can perform a network traffic analysis to discover RATs.
Learn Network Traffic Analysis for Incident Response
Before knowing how IR teams discover RATs in networks, we need to understand the working of RATs on victim machines. In this article, we will explore content about RAT operations, as well as how RATs are discovered.
How do RATs work?
First and foremost, intruders gain access to the victim machine by covertly installing the RAT. This is often done through malicious links, crafted email attachments or infected torrents. After said intrusion, attackers establish direct connectivity with a compromised computer through a command-and-control (C2) server, which establishes a remote connection between hackers and the victim computer(s). This mechanism is based on a client-server architecture.
Hackers often use remote access tools to establish a remote C2 server connection. These tools might include Team Viewer, Ammyy Admin, LogMeIn and Go2Assist. You can go here to learn more about remote access tools.
Discovering RATs
RATs are sophisticated in their operations because in many cases, they don’t show up in systems running processes and tasks. RATs also don’t have any effect on the speed of your computer. Instead, they consume the bandwidth of your internet connection.
Although RATs are wily, some techniques can be used on network traffic analysis to discover them. Here are some helpful tips.
Fix Windows DLL: SVCHOST.EXE
SVCHOST.EXE is the Windows DLL that gets installed on an exploited host as a Windows service, which is a server side of the RAT. The attackers use a “dropper” application to install SVCHOST.DLL on the victim machine. It is important to note that the server application, such as SVCHOST.DLL, gets installed on the compromised computer, whereas the client application is controlled by malicious actors. An example of a client application may include a browser or a Telnet client.
The SVCHOST.EXE can infuse malicious traffic and can gather details into properties of a network session, including protocols, frequency and the ratio of bytes sent to the bytes received. During a network traffic analysis, IR teams will notice that there is a high ratio of bytes sent versus received. In fact, this is an indication of malicious traffic and data theft, which is occurring through the RAT.
Although a RAT has been discovered, the rest of the investigation still must be performed. This usually involves conducting a further network traffic analysis to look for lateral movement such as investigating other computers with the same DLL to identify the signs of further attack.
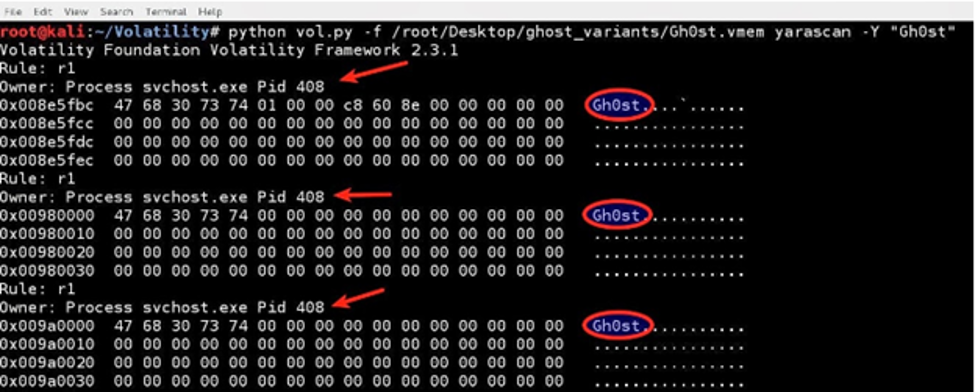
Another way to discover the RAT is to detect its “GhOst RAT process.” It is rather critical in an incident response perspective. The GhOst RAT process hides in network traffic, which resides in memory. Incident responders can discover this process if they have successfully detected network traffic in memory. The following screenshot demonstrates the process — namely svchost.exe with Pid 408 — which incorporates the magic keyword “GhOst.”
According to Trend Micro, a new variant of “GhOst” has been introduced that replaces it with the “LURKO” header. However, deep discovery can detect both headers, as well as generically detecting this kind of communication.
Foil the use of listening ports and TCP communication
The RAT server opens a listening port on the victim computer in order to enable its communication with the attacker-held client. The listening port may create problems due to limited privileges and the possibility of conflicts with other installed applications. To address these issues, threat actors normally use a non-privileged higher port such as 1024.
Initially, each RAT had its own default communication port number. Incident responders could easily discover RATs if they had a knowledge of different port numbers associated with each RAT. They used to simply map a listening port to the corresponding RAT name.
Today’s Trojans are very sophisticated and do not have any specific port numbers, unlike their predecessors. Rather, they can be configured to any port number and, therefore, their identification by mapping a port number with Trojan name is out of the question. However, they cannot work with impunity. Modern security tools can detect every type of RAT.
Nowadays, hackers use TCP communication for their client-server model. To discover even modern Trojan horses, incident response teams use firewalls that filter both inbound and outbound network traffic. Other additional tools, such as the anti-Trojan system and Intrusion Detection System (IDS) can also be a part of the security defense.
How can TCP connectivity be foiled? No sooner than the server uses a listening port on the victim computer than a firewall, performing a network traffic analysis, would generate a security alert and subsequently block this malicious attempt. Due to its configuration rules, a firewall doesn’t allow unknown applications to communicate over the internet.
Conclusion
A RAT is undoubtedly one of the most dangerous types of malware. Using a RAT, an attacker can cause damage from a remote place. However, incident responders can discover RATs if they are using some useful techniques, such as Fix Windows DLL: SVCHOST.EXE and by foiling the use of listening ports and TCP communication.
Do you want to know more about RATs? You can read another detail-oriented article regarding RATs here.
Learn Network Traffic Analysis for Incident Response
Sources
- What is Remote Access Trojan? Prevention, Detection & Removal discussed, TheWindowsClub
- MALICIOUS PROTOCOLS: GH0ST RAT, RSA
- Hunting and Decrypting Communications of Gh0st RAT in Memory, Cysinfo
- Detecting APT Activity with Network Traffic Analysis, Trend Micro
- Advanced communication techniques of remote access trojan horses on windows operating systems, GIACⓇ Certifications