Network traffic analysis for IR: Event-based analysis
Introduction to event-based analysis
Event-based analysis, as its name suggests, focuses on analysis of specific events that occur on the monitored network. This is accomplished by defining the event of interest, like malware detected within a phishing email, in such a way that a “hit” can be easily differentiated from a false positive.
If an incident responder can define a specific event with this level of accuracy and clarity, event-based traffic analysis can be a very valuable tool. Unlike connection-based or statistical analysis, which are primarily designed to draw attention to anomalies, an alert based on event-based analysis provides the analyst with specific information about the type of attack or other event being experienced on the network.
Learn Incident Response
Performing event-based analysis
Event-based analysis is based on signatures: descriptions of a particular event that can be used to test if that event has occurred. A common example of a signature is for malware, where features of the malicious file are extracted for use in an antivirus, intrusion detection/prevention system or other detection and monitoring tool.
While each system can use its own unique scheme for defining systems, the desire for interoperability and the prominence of some solutions have led to a couple of “standard” signature formats: Snort signatures and YARA rules.
Snort signatures
Snort is an open-source, free network intrusion detection and prevention system. This IDS and IPS is extremely powerful, making it a widely used product.
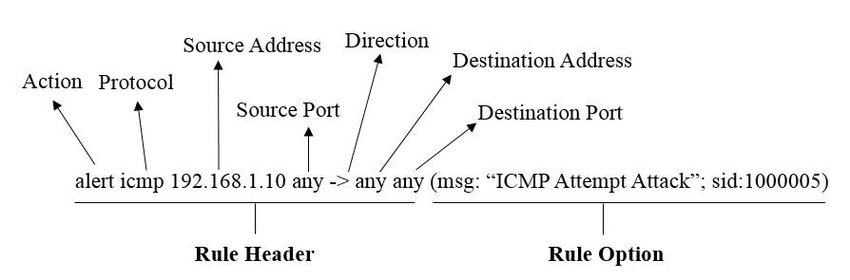
Snort rules are signatures developed specifically for use with the Snort IDS/IPS. They are designed to be extremely readable and flexible, making them a popular choice for defining signatures for event-based analysis.
(Source)
As shown in the image above, a Snort rule has several fields:
- Action: What should occur if the event is triggered (e.g., send an alert to the analyst)
- Protocol: Protocol of interest for this rule
- Source/Destination Address: IP address of the machine initiating/receiving the connection
- Source/Destination Port: Port used by the connection on the source/destination machine
- Direction: Direction of traffic flow (can be unidirectional or bidirectional)
- Message: Information about the event printed when the rule is triggered
- SID: A unique identifier for the rule
These are only a subset of the possible fields that can be used in a Snort rule. However, even a simple rule like this is very informative. In this case, the incident responder is concerned about any ICMP traffic originating from IP address 192.168.1.10. The ports and destination address do not matter; any such traffic will trigger an alert warning the analyst about an attempted ICMP attack.
Snort signatures are particularly useful for network traffic analysis because they are designed to describe network flows. Since many cyber-incidents occur over the network, having a language to succinctly describe a flow of interest is valuable for incident response.
While Snort signatures are primarily designed for use with the Snort IDS system, their flexibility and utility have made them popular. As a result, signatures are commonly developed for and published in Snort when a malware variant or new attack type is discovered.
YARA rules
YARA rules, on the other hand, are not developed for use with a specific tool. In fact, YARA, which stands for Yet Another Recursive/Ridiculous Acronym, was developed by Victor Alvarez of VirusTotal.
Unlike Snort signatures, YARA rules are designed to match text or binary patterns within files. However, they can be (and are) also applied to analysis of network traffic, especially the detection of malicious payloads within network traffic.
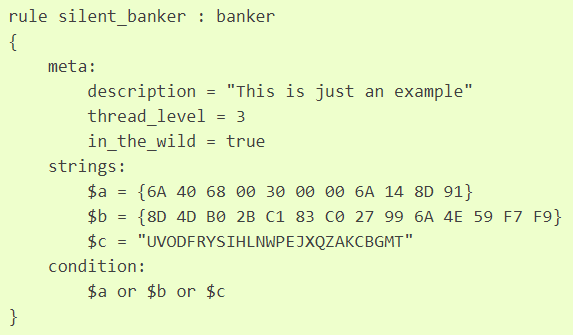
The image above shows a sample YARA rule, pulled from the YARA documentation. As shown, a YARA rule consists of three main sections:
- Meta: Metadata describing the event that the rule is designed to detect
- Strings: ASCII or hex strings defining unique features of the sample of interest
- Condition: Combines strings using Boolean logic to define the detection rule
While the description of the condition field claims that it contains only Boolean logic for combining strings, its true functionality is much more powerful. Among other things, YARA rules can count the occurrences of a string within a sample and look for strings at specific offsets. This functionality makes YARA rules much more powerful and enables the creation of complex rules that will only match the true sample of interest and dramatically reduce false detections.
Wireshark is primarily designed for detection of malicious files, but it can also be a powerful tool for network traffic analysis in incident response. ChopShop is an open-source tool developed by MITRE that has the ability to reassemble network flows and apply YARA signatures to the results, dramatically improving the ability of the signatures to match samples that may be fragmented over multiple packets.
Conclusion: Event-based analysis for incident response
Event-based analysis is an extremely valuable tool for incident response because it helps to solve one of the biggest challenges of IR: knowing where to look. Incident responders commonly need to sift through massive amounts of data in order to identify the particular features that point to the type and scope of an incident that the organization is experiencing.
Event-based analysis is the easiest to automate, and many solutions like Snort and Suricata exist to do so, allowing the analyst to focus their efforts on the data most likely to be of interest.
The main challenges of event-based analysis for IR are based upon the need for a signature in order to perform analysis. Since an incident responder needs to be able to define a certain type of event in order to search for it in this way, they are limited to the types of incidents that they know about and can define.
This is why event-based analysis is increasingly being used in conjunction with statistical analysis and machine learning: event-based analysis finds the known attack types and the other analysis techniques point to anything else. Between them, they have the potential to dramatically reduce the search space for analysts and massively improve the probability of a speedy detection of and response to an incident.
Learn Incident Response
Sources
- Example of Snort IDS Rule, ResearchGate
- Welcome to YARA’s documentation!, YARA
- ChopShop, GitHub