Network traffic analysis for IR: FTP protocol with Wireshark
The File Transfer Protocol (FTP), as its name suggests, is designed for transferring files between computers. It is used for a variety of different purposes, but a common one is transferring pages to/from a remote web server.
One of the issues with FTP is that it is a completely plaintext protocol and can be configured to allow anonymous authentication to the service. Since the protocol is designed to allow files to be added to or removed from the FTP server, this can be a significant security concern.
Learn Incident Response
A couple of different protocols exist for securing FTP. FTPS is the use of FTP traffic wrapped in Transport Layer Security (TLS). SFTP is a protocol related to secure shell (SSH) that is also designed to provide encrypted file transfer.
The FTP protocol in Wireshark
FTP is a plaintext protocol that operates over port 20 and 21. It can be identified in Wireshark using the ftp filter.
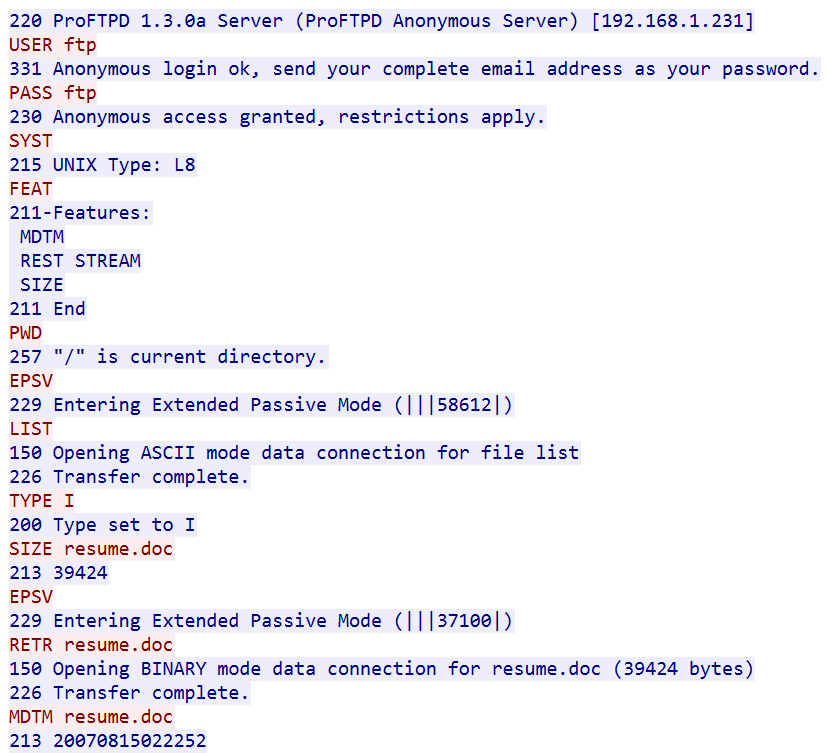
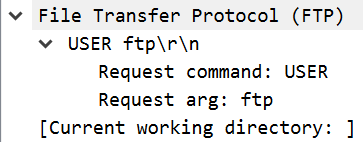
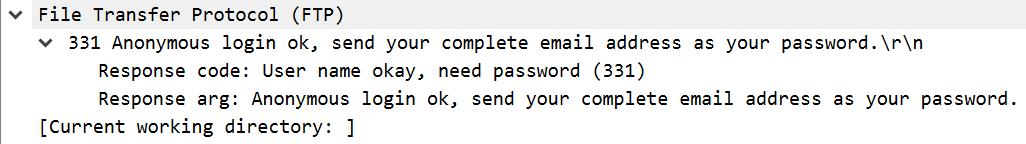
The image above shows a sample of FTP traffic collected by following a TCP stream in Wireshark. As shown, FTP is a request-response protocol. Each request is a command, potentially followed by a set of arguments. Responses include a response code followed by the data requested by the command.
An FTP packet simply contains the text data that is shown from the earlier session. This makes it very easy to read in a network capture. Since FTP operates as a plaintext protocol by default, this also makes it easy for an eavesdropper with access to an organization’s network traffic to extract sensitive data.
While the packets above show examples of anonymous authentication to an FTP server (which should be disabled for security reasons), FTP traffic could also leak a user’s actual network login credentials. For this reason, it is advisable to use one of the many alternatives to FTP for file transfer (SFTP, SCP, FTPS and so on).
FTP protocol analysis for incident response
FTP is a protocol that was designed with a focus on simplicity and functionality rather than security. As a result, it can be abused by an attacker in a variety of different ways if they can gain access to it.
Data exfiltration
FTP is designed to transfer files between a single server and (potentially) multiple different clients. A common use is to create file servers where official copies of files shared across an organization can be stored in a central and easily accessible location.
If an attacker can gain access to an account that is authorized to use an FTP server (and assuming that the server is configured to require authentication), it can create a significant risk for data exfiltration. Since FTP is designed to move files on and off of servers, an attacker could take a copy of any data already stored on an FTP server. Alternatively, the FTP server could be used as a stepping stone for data exfiltration since it is common usage to add/remove files from it, and firewall access control lists (ACLs) may allow FTP traffic to/from it across network boundaries. Monitoring for unusual usage of FTP in network traffic is important to protecting against data exfiltration.
Malware installation
One of the biggest challenges that a cybercriminal faces during a cyberattack is installing and executing their malware on the target machine. The threat of .exe and other executable files has resulted in many organizations focusing on them in anti-phishing training, making it harder to get a user to download and run an application from an email.
However, FTP is designed to allow files to be added to a server within an organization’s network perimeter. If an attacker has access to the internal FTP server and that server allows execution of files in the FTP directory, then the attacker could drop and run the malware on an internal machine themselves. If not, combining the use of FTP with phishing or another exploit may allow them to install and run malware on a target system (since an end user may trust a file that is on the company file server). It is important to lock down access to the FTP server, disallow applications stored there to execute and monitor for attempts to add and execute applications on the FTP server.
Credential stuffing
As the number of online accounts that people have increases, the more difficult it is to keep them secure. As a result, many people use weak and common passwords. In fact, an estimated 10% of people use one of the 25 most common passwords, and 62% use the same password for personal and work accounts. Simply trying weak and common passwords across multiple accounts gives an attacker a high probability of gaining access to a user’s professional account.
This type of attack, called credential stuffing, requires access to either password hashes or an online service that requires authentication. A well-configured FTP service meets this second criterion, since it will require users to authenticate using their work credentials in order to use the service.
An attacker can take advantage of this to test potential options for a user’s password. If the service is not configured with limits on the number of incorrect logins, they may manage to gain access (allowing them to use the account for the other purposes described above). Regardless, monitoring for large numbers of failed authentications, including across multiple accounts, is necessary to protect against this type of attack.
FTP bounce attack
An FTP bounce attack takes advantage of the PORT command in FTP, which is designed to forward FTP traffic to another server. An attacker can take advantage of this to bypass firewall restrictions, allowing them to access systems that are blocked by firewall ACLs. Any use of the PORT command in FTP traffic should be investigated to determine if it is malicious.
Conclusion: Monitoring FTP in Wireshark
The FTP protocol can be useful for businesses but also can be used by an attacker in a variety of different ways. When possible, it’s a good idea to move to a more secure protocol; however, if this isn’t an option, FTP should require authenticated access and be monitored for unauthorized use.
Learn Incident Response
Sources
- File Transfer Protocol (FTP), Wireshark
- The most popular passwords of 2018 revealed: Are yours on the list?, WeLiveSecurity
- Password Reuse Abounds, New Survey Shows, Dark Reading
- FTP Penetration Testing, Briskinfosec