Network traffic analysis for IR: TFTP with Wireshark
The Trivial File Transfer Protocol (TFTP) is designed to provide a bare-bones method of sending data from a server to a client. Its main use is for firmware upgrades and similar applications, where the client requesting the data has limited processing capabilities.
While TFTP is simple to use and effective, it is also extremely insecure. The protocol includes no encryption or authentication, meaning that it should only be used in a LAN (if then).
Learn Network Traffic Analysis for Incident Response
TFTP in Wireshark
TFTP is designed to be a stripped-down file transfer protocol without authentication or many of the features that FTP and other protocols offer. Instead, it has two main options: file read requests and file write requests.
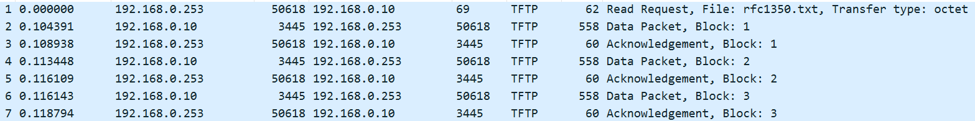
The screenshot above shows an example of a TFTP read request (GET) in Wireshark. It is interesting to note that TFTP is unusual in that it has a well-known port but doesn’t use it for all traffic. As shown in the packet capture above, the first TFTP request is made to port 69 (the TFTP server), but after that, the TFTP server selects another high-number port to send its responses. This makes it difficult to filter for TFTP traffic in a live capture in Wireshark since the built-in ftp filter does not work and filtering for port 69 will only catch the initial request.
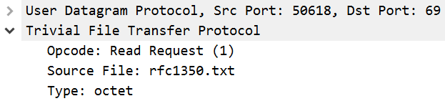
As shown in the screenshots above, TFTP packets are designed to be extremely simple. The image on the left is of the first packet in this sequence, a read request. It includes the opcode (1 for read request), the desired filename and the type of content that it is requesting (octet).
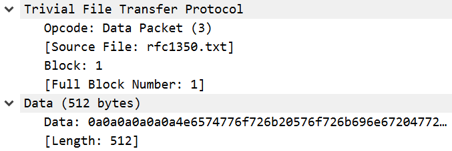
The packet on the right shows the first data packet (packet 2). Its header specifies an opcode (3 for data packet) and the block number, and the body contains the requested data.
While TFTP uses UDP, it has TCP-like features built in. Each TFTP data packet contains a block number and is acknowledged by the recipient. This ensures proper packet ordering and packet receipt without the overhead of a TCP connection.
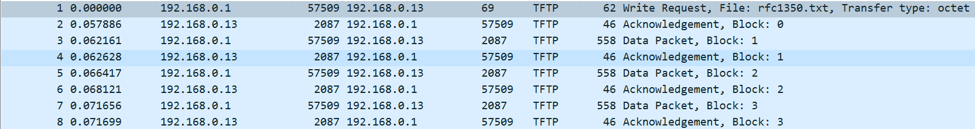
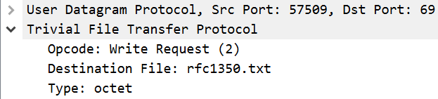
The screenshot above shows the flow of a write request (PUT). Since the client is driving this request, all that the server does is acknowledge the receipt of the initial request (Block 0) and all of the data sent after it.
As shown above, the structure of a write request packet is essentially identical to that of a read request. The only difference is the opcode (2 for write).
The stripped-down nature of TFTP makes it very efficient and good for situations like loading boot information because it requires little overhead and processing. However, its lack of encryption and authentication make it extremely insecure.
TFTP analysis for incident response
TFTP is a file transfer protocol. This means that its main malicious uses are for moving data into and out of the network. TFTP can be used for data exfiltration once an attacker has compromised a network and found what they are looking for or for sending malware into a network.
Data exfiltration
As a file transfer protocol, TFTP is an ideal choice for an attacker wanting to perform data exfiltration. Since responding to requests for files is a core function of a TFTP server, traffic doing so is unlikely to look suspicious.
The main challenges in using TFTP for data exfiltration are the lack of encryption and TFTP traffic crossing network boundaries. Since TFTP is a plaintext protocol, it is easy to perform string matching against its contents to detect attempted data exfiltration. If TFTP traffic contains encrypted data, it may be worth performing additional analysis to see why.
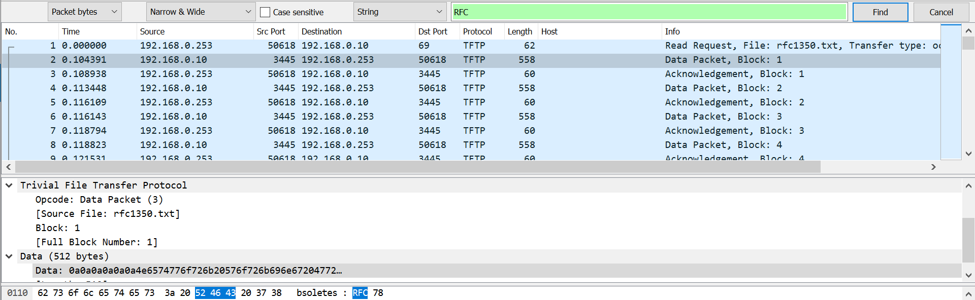
The screenshot above shows an example of performing a string-matching operation in Wireshark. To perform string matching in Wireshark, select Edit → Find Packet. To search in packet bytes, select “Packet bytes” in the leftmost menu of the search toolbar. Finally, type a string to match. Wireshark also allows matching display filters, hex values and regular expressions.
In the example above, the search text was rfc, which appears in multiple data packets. However, the actual filename is not matched since it is part of the TFTP command rather than packet data. Keyword searches for filenames can be performed using Wireshark filters (checking the value of tftp.source_file).
The other main challenge with using TFTP for data exfiltration is that it is known to be an insecure protocol and should be blocked at the network border. This makes it more difficult for an attacker to use it to move sensitive data out of a network. However, TFTP can be abused to make data transfers within a network more difficult to detect.
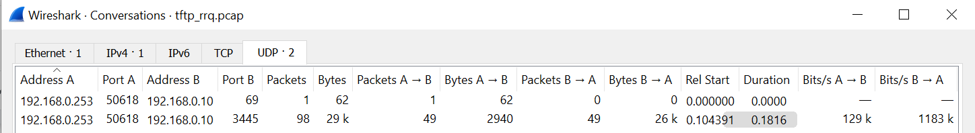
Moving data from one compromised computer to another via a TFTP server does not create the anomalous, direct connections between machines that could raise red flags. However, unusual TFTP activity can be detected in Wireshark. Selecting Statistics → Conversations and moving to the UDP tab (as shown above) summarizes the UDP connections performed in a traffic capture. If a display filter is applied (like tftp), checking the box to limit the display filter makes it possible to determine if any unusual or unauthorized TFTP connections exist. In the example above, the first flow is the TFTP command flow (requesting the file to be read) and the second is the actual file transfer.
Malware installation
As a file transfer protocol, TFTP is also invaluable to an attacker attempting to install malware within a target network. Since the protocol requires no authentication, if an attacker can access a TFTP server, they could upload malware or hacking tools to that machine.
While TFTP does not allow execution of the files uploaded to the server, it can be used to make other campaigns possible. Upload of hacking tools to a TFTP server can make it possible to access them from a compromised machine within the network without suspicious requests from the compromised machine crossing the network boundary. Malware or infected files uploaded via TFTP could also be used to make a spearphishing attack more likely to succeed, since the victim would be more likely to believe that a certain file is trustworthy if it was already within the network (on a shared file server) rather than attached to an email.
TFTP communications for malware installation can work both ways. A TFTP server within the network could be accessed and have files put on it; however, this traffic may be blocked by “default deny” firewall rules for inbound traffic. Alternatively, the hacker could run their own TFTP server outside the network and get malicious files using a TFTP client on an infected machine. Either way, it is a good idea to monitor for (and block) any traffic on port 69 trying to cross the network boundary or between machines on the internal network (since a secure protocol like encrypted FTP should be used instead).
Conclusion: Monitoring TFTP in Wireshark
TFTP is an insecure file transfer protocol with many more secure alternatives. If TFTP traffic exists in a network traffic capture, it is a good idea to track down and disable the TFTP server in use. TFTP should also be blocked at the network boundary, and TFTP clients on internal workstations should be disabled to prevent it from being misused.
Learn Network Traffic Analysis for Incident Response
Sources
- SampleCaptures, Wireshark Wiki
- Trivial File Transfer Protocol (TFTP), Wireshark Wiki
- Trivial Transfers With TFTP, Part 1: Why Use It?, linux.com