Reporting of Cybersecurity Incidents
This article is about the reporting of cybersecurity incidents in the USA. While it covers three main types of reporting—corporate, institutional and civil—focus is placed on the business level.

Learn Incident Response
Learn Incident Response
Reporting as a Civic Duty
Like any other crime, an Internet-based crime should be reported to those law enforcement authorities assigned to tackle it at a local, state, Federal, or international level, depending on the nature and scope of the criminal act. Hence, citizens who are aware of Federal crimes should notify the local offices of Federal law enforcement. Here is the list of the main Federal law enforcement agencies that investigate domestic Internet crimes: the Federal Bureau of Investigation (FBI), the United States Postal Inspection Service, and the Bureau of Alcohol, Tobacco and Firearms (ATF).
The site of the U.S. Justice Department contains a convenient table that helps visitors chose the most appropriate Federal agency to handle specific cybercrimes:
Appropriate Federal investigative law enforcement agencies
- FBI local office
- if imported, U.S. Immigration and Customs Enforcement
- Internet Crime Complaint Center
- FBI local office
- U.S. Secret Service
- Federal Trade Commission (online complaint)
- if securities fraud or investment-related SPAM e-mails, Securities and Exchange Commission (online complaint)
- Internet Crime Complaint Center
Reporting Intellectual Property Crime
Type of Crime
Appropriate Federal investigative law enforcement agencies
Source: The U.S. Justice Department
For the Federal notification system to work efficiently, some kind of node between local and Federal level is needed. A two-page document titled "Law Enforcement Cyber Incident Reporting: A Unified Message for State, Local, Tribal and Territorial (SLTT) Law Enforcement" settles this matter, and it can be seen here.
The document serves as a directory of when/what/how SLTT agencies should report cyber-incidents to Federal agencies.
Reporting among Government Institutions
Federal Contractors
The Department of Defense ("DoD") has issued an interim Rule ("Rule") on 08/26/2015, which imposes new security and reporting obligations on Federal contractors and the conclusion of DoD cloud computing contracts. Through this move, which highlights the wind of change in Federal cybersecurity policy, the Federal contractors and subcontractors are obliged to report cyber-incidents resulting in an actual or potential "adverse effect" on covered defense information (only unclassified), system, or the contractor's ability to provide critical support.
Basically, defense contractors must report security breaches of information systems and networks, and must then give DoD staff access to evaluate the impact of the reported incident. The Rule requires a contractor who is defined as operationally critical to report each negative cyber-occurrence happening on the contractor's network. In addition, there are new policies for procurement of cloud computing services from Federal contractors.
On the other hand, cyber-incidents that pertain to classified information on contractor systems are to be reported under the terms of the National Industrial Security Program Operating Manual. In the event of the cyber-incidents that trigger the reporting obligation, the contractor must do the following:
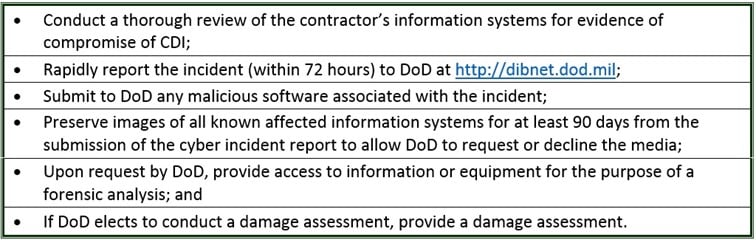
Source: Davis Wright Tremaine LLP
Although the Rule is applicable only to the Defense Federal Acquisition Regulation Supplement (DFARS), its influence is expected to extend to the Federal Acquisition Regulations (FARS).
Agency to Agency
Federal incident notification guidelines applicable to Federal agencies came into effect on 1 October 2014. US-CERT is the central reporting point, and every computer incident within the Federal Government as defined by NIST Special Publication 800-61 must be reported to this central authority within one hour.
This excerpt provides more information about the procedure:

Source: US-CERT
Corporate Reporting
SEC Guidance
When speaking of cybersecurity as a disclosure issue, perhaps one of the most important documents on that matter is a guidance published by the Division of Corporation Finance of the Securities and Exchange Commission (SEC) in October 2011. This guidance focuses on examining whether cybersecurity-related information of a corporate nature represents a considerable risk factor and/or a material "known event, trend or uncertainty". It highlights the areas that may impose obligation to disclose cybersecurity incidents – Risk Factors, Management Discussion & Analysis, Description of Business, Legal Proceedings, Financial Statements, and Disclosure Control & Procedures.
According to the SEC guidance, one of the goals before the extant Federal security laws is to elicit "disclosure of timely, comprehensive, and accurate information about risks and events that a reasonable investor would consider important to an investment decision."
Interestingly, cybersecurity risks should also be disclosed if they represent a potential threat likely to have a material effect on the registrant's operations, services, products, relations with customers or suppliers, overall financial well-being, or competitive condition. The theft of material intellectual property is an example of a cyber-incident that would necessitate filing an official report, according to the SEC. Another example is "if a registrant has a new product in development and learns of a cyber-incident that could materially impair its future viability, the registrant should discuss the incident and the potential impact to the extant material." Furthermore, if the company is a party to a legal proceeding related to a cyber-incident, then the company in question may need to reveal all the information directly connected to the litigation. Finally, provided that cyber-incidents endanger a company's ability to record and report information, the company's decision-makers should submit their assessment of how effective are disclosure controls and procedures.
Companies that deal with and store huge quantities of personal data should particularly consider the risks ensuing from a cybersecurity breach. Such companies should take into account that revealing a successful attack could lead to reputational damages, lost business opportunities, and fines because of non-compliance with privacy laws. In addition, with every cyber-attack misusing various customer information, there is a great probability of triggering obligations enshrined in disparate breach notification laws of numerous jurisdictions with which the company will have to comply.
Businesses in specific sectors, for instance, the healthcare industry, which have to operate with sensitive patient information, must overcome increased cybersecurity risks. Patient data accessed by unauthorized parties may result in sanctions or criminal prosecution on the grounds of violation of privacy rules under HIPAA.
The Biggest Question – "Should I report it?"
A report from Citigroup's cyberintelligence center issued at the beginning of 2015 casts light upon the question of why most law firms in the United States do not acknowledge breaches:
"Due to the reluctance of most law firms to publicly discuss cyberintrusions and the lack of data breach reporting requirements in general in the legal industry, it is not possible to determine whether cyberattacks against law firms are on the rise."
Law firms are indeed targets of hackers because they function as repositories for corporate deals, business strategies, and confidential data of all kind. In fact, even though law firms, especially bigger ones, are mindful of their cybersecurity, the improvements in this department remain below the standard in comparison to other industries. Owing to these reasons, law firms will continue to be a tempting target for malicious actors.
Federal law enforcement authorities constantly advise law firms to be more open when it comes to reporting incidents. At a March 2015 American Bar Association conference that took place in New Orleans, John P. Carlin, assistant attorney general for national security, impressed also on the attending lawyers that reporting cybersecurity incidents should not be seen as "a badge of shame."
Just like law firms, many companies in other sectors decide not to disclose cybersecurity events that worth reporting out fear of reputation-related issues. The exact wording in the SEC guidance on reporting obligations imposed on companies sounds like that:
Although no existing disclosure requirement explicitly refers to cybersecurity risks and cyber-incidents, a number of disclosure requirements may impose an obligation on registrants to disclose such risks and incidents. In addition, material information regarding cybersecurity risks and cyber-incidents is required to be disclosed when necessary in order to make other required disclosures, in light of the circumstances under which they are made, not misleading.3 Therefore, as with other operational and financial risks, registrants should review, on an ongoing basis, the adequacy of their disclosure relating to cybersecurity risks and cyber-incidents.
Even though the SEC guidance is not mandatory, it would nevertheless be useful for an internal check-up on whether a corporation has enough security measures in place. Unfortunately, the corporate decision-makers are seldom in a favorable position to decide whether a disclosure will bring positives or negatives. In this respect, Caitlin Hayden, a National Security Council spokesperson, announced:
"I'd refer you to the SEC on their requirements for reporting on cyberattacks, but there are reasons why companies may choose not to disclose cyber-incidents. First, they may not be aware that their networks are being compromised. Second, they may know, but believe that disclosing information will negatively impact the confidence of their customers or shareholders."
What she omitted to mention was that some firms under attack are concerned every time they give details on the incident, since they feel that whatever they share might eventually be used by a malicious actor if he can lay his hands on that information. Fortunately, there is a provision in the SEC guidance on that matter:
"We are mindful of potential concerns that detailed disclosures could compromise cybersecurity efforts—for example, by providing a "roadmap" for those who seek to infiltrate a registrant's network security—and we emphasize that disclosures of that nature are not required under the Federal securities laws."
Hayden also pointed to a series of disclosures in recent weeks from several companies as evidence that things could be changing for the better. Despite the fact that more and more companies tend to be upfront about cybersecurity incidents, they generally claim that the damages are minor. SEC spokesman John Nester commented on the guidance:
"We issued guidance intended to help companies better understand their disclosure obligations as they relate to cyber-incidents and risks. In the guidance, we confirmed that a number of our existing requirements impose disclosure obligations if the information related to a cyber-incident or risk of one is material to investors."
Therefore, convincing companies to admit to a vulnerability is one thing, convincing them to admit to a breach that has had a material effect is a completely different story. To clear up what is the correlation between non-material attacks and reporting, a reference could be made to the words of Michelle Leder, editor of the website Footnoted.com, who is familiar with SEC filings:
"With the current crop of 10-Ks, we're starting to see a bit more disclosure, but most of what I've seen continues to refer to the fact that these attacks are not material, which is a pretty high standard to meet. An attack doesn't have to be material to cause reputational damage or cost lots of money to fix, not to mention be a huge distraction for top execs."
Future Regulatory Initiatives
As one White House aide formulated it: "They're going to find every reason not to report it. Unless we create an environment where it's not suicidal for these guys to come clean, they're not going to do it."
The SEC guidance that was issued in October 2011—a year before the wave of DDoS attacks against several U.S. banks – made it clear that businesses that are victims to cyber-attacks, such as computerized theft or disruption, need to report them. In the wake of these assaults that hurt the banking industry, the White House undertook various initiatives to help private sector better cope with such incidents. President Obama, for instance, signed an executive order that aims to help companies in critical areas to shore up their information security and at the same time to improve information sharing about threat data between government and companies. Some corporations in this sector—Level 3 Communications, AT&T, Chesapeake Energy, eBay and LinkedIn have admitted they had difficult times being a victim to intrusions or disruptions. As the president of the financial services trade organizations, BITS, said: "It's almost naïve for most large companies in the critical infrastructure sector to say that they aren't subject to attack. The stepped-up disclosure brings awareness, greater diagnosis, and a desire to find a stronger cure."
To date, neither the SEC nor other major regulator has taken any formal steps to build on the measures available to companies when reporting information threats. While no significant changes in the disclosure rules have been made during the past couple of years, including the standards applicable to the 2014 Form 10-K, companies can anticipate heightened scrutiny and professional skepticism from regulators, outside auditors, and shareholders. Notable events in 2014, such as major corporate cyber-attacks, will definitely underline the importance of transparency as a mitigation strategy.
Both President Obama and U.S. Treasury Secretary Jacob Lew have recommended that Congress should promulgate legislation in 2015 that would give companies immunity to share sensitive information connected to cybersecurity issues. In October 2015, the Senate passed the Cybersecurity Information Sharing Act (CISA). Its supporters deem that the bill will aid the fight against hackers by prompting companies that have been attacked to share information with Federal law enforcement. By way of illustration, businesses that are victims of a cyber-attack can send "cyber-threat indicators" to the Department of Homeland Security, which in turn can spread the word among the rest of the peer group in a way that will preserve the safety of the victim.

Conclusion
The National Security Council spokesperson Caitlin Hayden assures that honesty is the best security policy for victims of cyberattacks:
"We have seen companies come forward recently to discuss cyber-events they've experienced, which we know mirror the situations of individuals and organizations across the U.S. government and private sector. We encourage the sharing of these experiences in order help increase public awareness of these threats to U.S. security."
Across the Atlantic, the EU is about to enact the Network and Information Security (NIS) Directive—a legislative bid to improve the security of critical infrastructure in the EU—which will enable member states to draw up sector-specific rules on what constitute a reportable 'incident.' However, the negotiations have stalled due to disagreement among EU members on the scope of the proposal.
It seems that everywhere there are big changes underway in how data concerning notable information events is to be submitted to the local authorities. More important, it seems that the primary goal of these changes is to develop a cultural and business shift towards complying with the prescriptions that advise every victim of a cyber-attack to file an official report. This wind of change is clearly discernible in the opinion of the senior vice president of the security firm Trustwave, Nicholas Percoco, who thinks "that disclosing — while it may have a short-term impact on a company's brand recognition — is only going to help everybody in the industry. Zero knowledge is never good."
Everything sounds as simple as it can be—step one of course is to disclose the incident as a fait accompli; step two should explain what measures have been, and will be, taken to deal with the current situation and prevent future problems. And if you need more good reasons to report cyber-incidents:
- Finding and sanctioning perpetrators(or at least putting them on trial) is the surest way to repel them once and for all, and to deter others. Normally, you cannot do that on your own, so you need to turn to those who have the means to do it—that is, law enforcement agencies.
- Working with law enforcement will more likely bolster your internal security efforts, rather than undermine them. The government is often in a better position to provide companies with valuable information about the methods, capabilities and motives of the malicious actors, for instance, when a company is the target of a foreign-sponsored campaign.
- Whenever loss of customer PII may trigger state data breach notification requirements, they can be delayed to accommodate a law enforcement request. Moreover, a compliance failure may result in costs associated with cyber-breaches, loss of intellectual property, and even expensive lawsuits.
- Reports on cybersecurity incidents enrich the database of government agencies, which in turn help them cope with the recent trends in this area.
To sum up, being a civil duty, reporting cyber-incidents is not only the right thing to do, but it could be helpful to you, your business, your government and others in your position.
Reference List
Beckner, C. (2014). A "Unified Message" on law enforcement cyber incident reporting. Available at http://www.securityinsights.org/2014/10/a-unified-message-on-law-enforcement-cyber-incident-reporting/ (03/11/2015)
Bryan Cave LLP (2014). When a bank should disclose a cyber attack. Available at http://www.lexology.com/library/detail.aspx?g=c08182f0-f710-453d-b772-d876421994af (03/11/2015)
Chabinsky, S. (2013). Top 5 Reasons to Report Computer Intrusions to Law Enforcement. Available at http://www.securitymagazine.com/articles/84898-top-5-reasons-to-report-computer-intrusions-to-law-enforcement (03/11/2015)
Chellel, K. (2015). Google, Facebook at Center of EU Clash Over Cyber-Attack Law. Available at http://www.bloomberg.com/news/articles/2015-06-05/google-facebook-at-center-of-eu-clash-over-cyber-attack-law (03/11/2015)
Division of Corporation Finance Securities and Exchange Commission (2011). CF Disclosure Guidance: Topic No. 2. Available at https://www.sec.gov/divisions/corpfin/guidance/cfguidance-topic2.htm (03/11/2015)
Goldstein, M. (2015). Citigroup Report Chides Law Firms for Silence on Hackings. Available at http://www.nytimes.com/2015/03/27/business/dealbook/citigroup-report-chides-law-firms-for-silence-on-hackings.html?_r=0 (03/11/2015)
Hill, Е & Haas, A. (2014). New Rule Forces Contractors to Report Cybersecurity Incidents. Available at http://www.nationaldefensemagazine.org/archive/2014/march/pages/newruleforcescontractorstoreportcybersecurityincidents.aspx (03/11/2015)
Javers, E. (2013). Cyberattacks: Why Companies Keep Quiet. Available at http://www.cnbc.com/id/100491610 (03/11/2015)
Kastiel, K. (2015). What's New in 2015: Cybersecurity, Financial Reporting and Disclosure Challenges. Available at http://corpgov.law.harvard.edu/2015/02/18/whats-new-in-2015-cybersecurity-financial-reporting-and-disclosure-challenges/ (03/11/2015)
Law Enforcement Cyber Center (2015). Senate Approves Cybersecurity Bill: What You Need To Know. Available at http://www.iacpcybercenter.org/news/senate-approves-cybersecurity-bill-what-you-need-to-know/ (03/11/2015)
Marchese, L., Hoar, S., and Williams, C. (2015). DoD New Cyber Security Reporting Rules for Contractors. Available at http://www.privsecblog.com/2015/08/articles/cyber-national-security/dod-new-cyber-security-reporting-rules-for-contractors/ (03/11/2015)
Mutch, J. (2013). Beware The Coming SEC Regulations On Cybersecurity. Available at http://www.forbes.com/sites/ciocentral/2013/05/15/how-to-prepare-for-when-the-sec-comes-asking-about-cybersecurity-risk/ (03/11/2015)
Nakashima, E. (2013). More companies reporting cybersecurity incidents. Available at https://www.washingtonpost.com/world/national-security (03/11/2015)
National Conference of State Legislatures (2015). Security Breach Notification Laws. Available at http://www.ncsl.org/research/telecommunications-and-information-technology/security-breach-notification-laws.aspx (03/11/2015)
Savitz, E. (2012). Disclosing Cyber Security Incidents: The SEC Weighs In. Available at http://www.forbes.com/sites/ciocentral/2012/06/04/disclosing-cyber-security-incidents-the-sec-weighs-in/ (03/11/2015)
Olswang LLP (2013). New obligations to report cyber attacks: will they apply to your business? Available at http://www.olswang.com/articles/2013/02/new-obligations-to-report-cyber-attacks-will-they-apply-to-your-business (03/11/2015)
Out-Law.com (2015). Sector-specific guidelines will set out cyber security incident reporting duties, UK government confirms. Available at http://www.out-law.com/en/articles/2015/june/sector-specific-guidelines-will-set-out-cyber-security-incident-reporting-duties-uk-government-confirms/ (03/11/2015)
US-CERT. Federal Incident Reporting Guidelines. Available at https://www.us-cert.gov/government-users/reporting-requirements (03/11/2015)
U.S. Department of Justice. Reporting Computer, Internet-related, Or Intellectual Property Crime. Available at http://www.justice.gov/criminal-ccips/reporting-computer-internet-related-or-intellectual-property-crime (03/11/2015)
Learn Incident Response
Learn Incident Response
Williams, K. (2015). Pentagon unveils data breach rules for defense contractors. Available at http://thehill.com/policy/cybersecurity/252025-pentagon-unveils-data-breach-rules-for-defense-contractors (03/11/2015)









