Insider vs. outsider threats: Identify and prevent
In my last article, we discussed on a step-by-step approach on APT attacks. The origin of any kind of cyber-attack is through an external or an internal source. Multiple sophisticated insider attacks resulted in the exfiltration of highly classified information to the public. The main difference between APT and Insider attacks is that malicious insiders have by definition authorized access to the infrastructure and potentially even to the servers storing sensitive information (Mail server, database servers), while APTs need to gain unauthorized access. One of the motive of an outside attacker is to obtain the credentials of an insider. This article will focus on the Malicious Insider and Outsider threats to an organization which result in multiple cyber-attacks
Before getting a deep understanding of these threats, we first need to define what we mean by the term "Malicious Insider" or "Insider Threat." Firstly, an Insider is an individual with privileged access to an IT system in an organization. An Insider threat can be defined as 'a current or former employee, contractor or other business partner with access to the organization's network, system or data and intentionally misuses them or whose access results in misuse'. In the other hand, an Outsider threat occurs when an individual or a group seeks to gain protected information by infiltrating and taking over profile of a trusted user from outside the organization.
Insider threats aren't just employees, they can also be contractors, vendors, or even volunteers that come in and work in the organization. Vormetric recently released the results of its 2015 Vormetric Insider Threat Report, that found 92 percent of IT leaders felt their organizations were either somewhat vulnerable to insider threats, while 49 percent said they felt very or extremely vulnerable to insider threats.
Who is ignored the most, insider or outsider attackers?
Over the past several years, the CERT Insider Threat Center has conducted empirical research and analysis to develop and transition socio-technical solutions to combat insider cyber-threats. CERT Insider Threat Center has been looking at malicious insider threats, but we're now starting to include non-malicious insider threats and we're about to actually start a new study of those types of insider threats. Dawn Cappelli, formerly of the CERT Insider Threat Center at Carnegie Mellon University, gives an example of an outsider becoming an insider threat. There is also a high growth in unintentional insider threats.
The example cites an employee of a computer networking company with access to a customer's network - in this case, a semiconductor company. This individual used his privileged access to that customer's network to steal sensitive data before taking a job at a competitive semiconductor company and then attempting to use that data for competitive advantage. A major percentage of insiders have access to company data that they shouldn't be able to see.
When insiders steal intellectual property, they usually act within a 30-day window, says Mike Hanley, who coauthored the CERT paper entitled "Insider Threat Control: Using Centralized Logging to Detect Data Exfiltration Near Insider Termination." In the case of an APT attack, the attacker identifies an entry point to bypass perimeter defenses and then exfiltrate data from internal network. A malicious insider has access to sensitive information and has no reason to fear being discovered, since many organizations ignore insider network traffic due to its high abundance.
A medium sized organization would have nearly 20,000 devices connected to the network. It includes mobile phones, laptops, printers, servers, and other devices that communicate through internet. There are myriads of channels used for data transmission: Cloud-based apps like Salesforce and Amazon Web Services, email messaging services, various internet/web portals and social media. The amount of data the company's network connected devices generate is around 20TB or more in a single day. Exfiltration within normal traffic patterns and sizes is already hard to detect and that's compounded by the use of increasingly stealthy encryption when sensitive credentials are compromised.
Types of insiders
One of the most destructive examples of Insider Threats in was the cyberattack on the state-owned oil company Saudi Aramco, which erased the data on about 30,000, or three quarters, of the company's corporate PCs using a virus named Shamoon, and replaced it with an image of a burning American flag. After analyzing the software code from the Aramco attack, security experts say that the event involved a company insider, or insiders, with privileged access to Aramco's network. The virus could have been carried on a USB memory stick that was inserted into a PC.
Compromised actors
Unintentional actors
Insiders who expose data accidentally, such as an employee who accesses company data through public WiFi without the knowledge that it's unsecured. A large number of data breach incidents result from employee negligence towards security measures, policies, and practices.
Emotional attackers
On October 2008 a logic bomb was discovered at American mortgage giant Fannie Mae. The bomb was allegedly planted by Rajendrasinh Babubhai Makwana, an IT contractor who worked in Fannie Mae's Urbana, Maryland facility. The bomb was set to activate on 31 January 2009 and could have wiped all of Fannie Mae's 4000 servers. Makwana had been terminated around 1:00pm on 24 October 2008 and managed to plant the bomb before his network access was revoked. Such events of planting logic bombs by employees intentionally are quite high.
Tech savvy actors
Insiders who react to challenges. They use their knowledge of weaknesses and vulnerabilities to breach clearance and access sensitive information. Tech savvy actors can pose some of the most dangerous insider threats, and are likely to sell confidential information to external parties or black market bidders.
Companies implement sophisticated technology to monitor their employees but it's not always easy for them to distinguish between an insider and an outside attack. Those who target and plan attacks from the outside might create strategies for obtaining insider knowledge and access by either resorting to an existing employee, or by making one of their own an insider. According to 2015 Verizon Data Breach Investigation report, 55% of insider incidents involved abuse of privileges. Someone even leaving a laptop in the car, or emailing/improperly disposing of personal confidential information can have consequences that are just as serious as the malicious insider threat.
Outsider attacks
The percentage of external threats to an organization is very high. It includes well-funded hackers, organized crime groups, and government entities. Attacks can be either active or passive. An active attack generates packets or participates in the network while a passive attack is eavesdropping the network or tracking users. Main motive behind these kind of cyber-attacks include Cyber Espionage, Cyber Warfare, and Hacktivism. These attackers are persistent, and it is important to be aware of the methods used by hackers. This is an important step towards defending sensitive company data. The cost to a company could potentially be millions of dollars, when a hacker exposes sensitive data to the public.
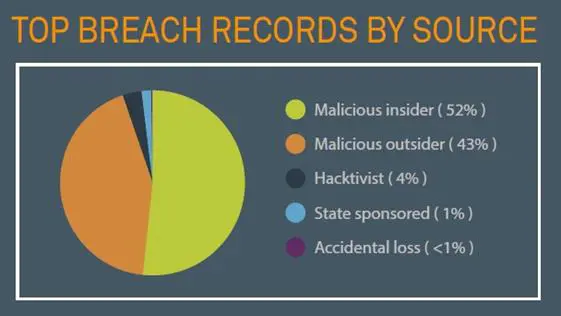
As per 2014 report from Breach Level Index, malicious insiders stole more records than outsiders did, although outsiders were to blame for more incidents during the first quarter. Outsiders took 43 percent of all records in 156 incidents worldwide. Insiders were successful in stealing 52 percent of the total amount of records despite accounting for 11 percent of total incidents.
Building an insider and outsider threat detection and mitigation Plan
Organizations have begun to acknowledge the importance of detecting and preventing insider threats. When evaluating security technologies, breadth and depth of visibility are equally important to gain knowledge about environments and threats. Ask vendors if their technologies will allow you to see and gather data from a full spectrum of potential attack vectors across the network fabric, email and web gateways, mobile devices, virtual environments, and the cloud.
Establishing an insider threat program
According to CERT Insider threat center blog, Insider Threat program includes Threat Training and awareness, insider incident response plan, communication of insider threat events, policies, procedures, and practices, defining the insider threat framework, formal processes for the response, communication, and escalation of insider events. A formalized insider threat program demonstrates the commitment of the organization to due care and due diligence in the protection of its critical assets. It is essential to providing consistent and repeatable prevention, detection and responses to insider incidents in an organization. These mature and well defined processes, designed with input from legal counsel and stakeholders across the organization, ensure that employee privacy and civil liberties are protected.
It provides a measurable response to insider attacks and can show the organization's progress in mitigating insider attacks. Additionally, a formal program creates the opportunity for resources dedicated to insider threat mitigation, an essential step in building a successful insider threat program.
Invest in forensic procedures
A variety of forensic procedures and tools in an organization's toolkit increases the capability to analyze what the employee or contractor has been doing with the company assets. Files may be deleted and unrecoverable through normal means, but are accessible through the forensic tools. Court-presentable evidence can then be provided in the event the case is prosecuted.
Pay increased attention to privileged accounts
Systems administrators have elevated access through the use of privileged accounts. If a system administrator that has the capability to alter or delete the log entries commits the fraud, detecting the event will be more difficult, if even possible. Special monitoring should be applied to these accounts due to the damage that can be caused.
Implementing separation of duties and least privilege policy
Privilege misuse is one of the hardest form of attack to detect or prevent by technical means, since by definition the insider already has legitimate access. There is a very fine line between intent and action, especially when excessive privileges on IT resources are involved.
In a secure and compliant server environment, end users are not entitled to the root password or even super user status because organizations can no longer tolerate the security risks posed by intentional or indirect misuse of privileges. At the same time, system administrators need privileged access to servers, and too often, they share root passwords, manage policy creation, and change manually. With a server-based least privilege solution, they can delegate privileges without revealing root passwords, and privileged access is recorded.
Patch all devices
Upgrading and applying the latest security patches in all devices and systems. According to Verizon 2015 data breach investigation report, many existing vulnerabilities remain open, primarily because security patches that have long been available were never implemented. In fact, many of the vulnerabilities are traced to 2007 a gap of almost eight years.
Conclusion
Both Insider and Outsider threats must be handled with People, Process and Technology(PPT) through defense-in-depth strategy. If the perimeter devices, systems and network are properly hardened as per the companies security policies, duties are segregated, employees are made aware about the trending cyber-threats, every activities in the network are efficiently logged and monitored, then the likelihood of a cyber-attack can be minimized to a good extend. According to the Ponemon Institute, "Over reliance on Antivirus and Intrusion Detection Systems (IDS) solutions has weakened the collective security posture, as these solutions cannot stand up in the face of the advanced threats we now see. New solutions focused on network and traffic intelligence is seen as the best way to combat advanced threats, and much broader adoption is required."
Encrypting data, enforcing two-factor authentication and physical security are few of the common themes in protecting against today's cyber-threats. Whether they originate from the inside or the outside is equally challenging. However, they have a lot in common. They are tapping into many of the same vulnerabilities and methods to accomplish their missions. Allocating resources dedicated to insider threat and outsider threat mitigation will help in thwarting such cyber-events.










