Internet of Things: How Much are We Exposed to Cyber Threats?
Introduction
The Internet of Things (IoT) is one of the paradigms that will influence our society most of all in the next few years, and it is already conditioning the IT industry.
With the term "Internet of Things" we commonly refer the objects that could be interconnected and uniquely identified. At the moment, Internet of Things devices could be tagged using several technologies such as the RFID, NFC, digital watermarking, QR code and others.
Learn IoT Security
"The Internet of Things (IoT) is the interconnection of uniquely identifiable embedded computing devices within the existing Internet infrastructure. Typically, IoT is expected to offer advanced connectivity of devices, systems, and services that goes beyond machine-to-machine communications (M2M) and covers a variety of protocols, domains, and applications. Things, in the IoT, can refer to a wide variety of devices such as heart monitoring implants, biochip transponders on farm animals, automobiles with built-in sensors, or field operation devices that assist fire-fighters in search and rescue," reads the definition provided by Wikipedia.
In the near future, every individual will be equipped with a series of smart devices that will exchange information with peers. Humans may be conceptually similar to a data cluster for which we must be able to provide a proper level of security.
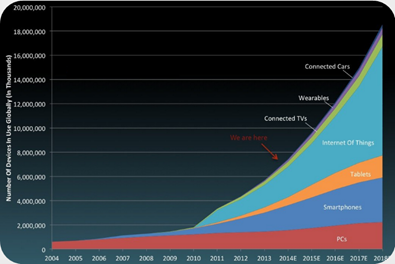
Figure 1 - Internet of Things Diffusion
The number of connected devices is growing apace. Experts estimated that there will be nearly 50 billion connected devices by 2020, and each person will have more than six connected devices. Prominent exponents of the IT industry estimated that the IoT paradigm will generate $1.7 trillion in value added to the global economy in 2019. By 2020 the Internet of Things device will more than double the size of the smartphone, PC, tablet, connected car, and the wearable market combined.
Technologies and services belonging to the Internet of Things have generated global revenues in $4.8 trillion in 2012 and will reach $8.9 trillion by 2020, growing at a compound annual rate (CAGR) of 7.9%.
The diffusion of IoT devices will be able to influence human behavior, for example influencing the movements of individuals in urban areas on the basis of atmospheric parameters or the level of traffic congestion in the particular areas. Let's try to image the effects of an incident that could occur to the network of devices composed by IoT appliances.
Unfortunately, the rapid diffusion of the Internet of Things paradigm is not accompanied by a rapid improvement of efficient security solutions for those "smart objects", while the criminal ecosystem is exploring the technology as new attack vectors.
Technological solutions belonging to the Internet of Things are forcefully entering our daily life. Let's think, for example, of wearable devices or the SmartTV. The greatest problem for the development of the paradigm is the low perception of the cyber threats and the possible impact on privacy.
Cybercrime is aware of the difficulties faced by the IT community to define a shared strategy to mitigate cyber threats, and for this reason, it is plausible that the number of cyber attacks against smart devices will rapidly increase.
Threat Actors, motivations and cyber threats
Who are the treat actors that menace the Internet of Things and which are their motivations? What are the principal cyber threats and what is the related risk of exposure? The security community and IT industry have to work closely to provide the answers to these questions in order to design a new generation o secure IoT devices.
Let's start with the type of attacker that could be interested in the exploitation of Internet of Things devices. The bad news is that the paradigm is menaced by a multitude of threat actors, from cybercriminals to government entities, even hacktivists. The reason is simple: IoT devices manage a huge quantity of information, they are capillary distributed in every industry, and, unfortunately, their current level of security is still low.
Cyber criminals could be interested in stealing sensitive information by hacking IoT devices or could be interested in compromising them to run cyber attacks against a third-party entity. Let's consider, for example, a criminal crew that infects millions of routers or SOHO devices, SmartTVs and other smart devices worldwide to run a cyber attack against a target with extortion purposes. In a similar way, an intelligence agency could exploit smart devices to spy on persons of interest or to conduct cyber attacks on a large scale, making attribution of the offensive very difficult. Also hacktivists could be interested in hacking smart devices to protest against a private company and its commercial politics.
As explained by experts at Symantec, the principal cyber threats for the Internet of Things are:
- Denial of service - DDoS attacks could target all the end points of a working scenario, causing a serious problem with the network of smart devices and paralyzing the service it provides.
- Botnets and malware based attacks – This is probably one of the most common and dangerous scenarios. A malware author specifically designs their codes to compromise architectures used by IoT devices. A malicious code could be used to infect computers used to control a network of smart devices or to compromise the software running on them. In this second scenario, the attackers can exploit the presence of a flaw in the firmware running on the devices and run their arbitrary code, turning IoT components to unplanned use. In November 2013, Symantec experts discovered a new Linux worm, Linux.Darlloz, that was specifically designed to target the "Internet of Things", infecting Intel x86-powered Linux devices. The attackers compromised IoT devices in order to build a botnet (a thingbot) that was used for illegal activities, including sending spam, generating costly SMS messages, or running a DDoS attack.
- Data breaches – Data breaches represent another serious risk for the adoption of Internet of Things devices. Organizations should be aware of the potential for unintended consequences of IoT use cases. Attackers could spy on the communications between peers in a IoT network and collect information on the services they implement. Data accessed through Internet of Things devices could be used for cyber espionage purposes by an intelligence agency or by a private company for commercial purposes. Data breaches represent a serious threat to the privacy of organizations and individuals that make use of smart devices.
- Inadvertent breaches – Data management in an architecture that includes Internet of Things devices is a critical aspect. Sensitive information could be exposed not only by a cyber attack, but information could be also accidentally lost or exposed. Symantec provides the example of the CEO's car broadcasting its location, but more sensitive information could be leaked from the business environment.
- Weakening perimeters – Internet of Things devices are generally not designed with security in mind. Despite that they are Internet-connected devices, the majority of devices lack network security mechanisms. Let's consider, for example, a smart meter. If the attacker is able to compromise it, he could have access to our domestic network, spy on us, or cause physical damage to our domestic environment. The problem is equally serious if we consider the use of IoT devices in any industry.
The OWASP Internet of Things (IoT) Top 10
The Open Web Application Security Project (OWASP) has the primary intent to divulge best practices to improve the security of software. It is natural that the project also analyzed the top 10 security issues related to the popular paradigm.
- Insecure Web Interface
- Insufficient Authentication/Authorization
- Insecure Network Services
- Lack of Transport Encryption
- Privacy Concerns
- Insecure Cloud Interface
- Insecure Mobile Interface
- Insufficient Security Configurability
- Insecure Software/Firmware
- Poor Physical Security
I1 – Insecure Web Interface:
Almost every device has a built-in web server implemented for maintenance purposes, but in many cases, the interfaces exposed by the internal server are not secure. Poor authentication mechanisms, CSRF, XSS and SQL injection are the most common vulnerabilities affecting the web server.
I2 – Insufficient Authentication/Authorization:
Security experts need to carefully verify the adoption of strong passwords avoiding hardcoded credentials. Another aspect to verify is the presence of common vulnerabilities (i.e. sqli) for authentication/authorization processes.
I3 – Insecure Network Services:
SSH, SFTP and other service must be properly implemented. Also in this case, a common error is the hardcoding of service credentials.
I4 – Lack of Transport Encryption:
Credentials and data should be encrypted. The adoption of PKI could help administrators to implement efficient process to secure the information.
I5 – Privacy Concerns:
It is important to analyze every aspect of the IoT architecture that could expose unencrypted sensitive data.
I6 – Insecure Cloud Interface:
IoT devices could have the necessity to be integrated with cloud services for sharing data. The interface with cloud services must be properly implemented and designed to avoid the presence of critical vulnerabilities.
I7 – Insecure Mobile Interface:
Many smart devices provide a "Wireless Access Point" functionality, like SmartTV, and it is necessary to adopt strong encryption algorithms and security best practices (i.e. disabling the broadcast of SSID).
I8 – Insufficient Security Configurability:
IoT devices must give the possibility to configure principal security features requested for the compliance of security policies.
I9 – Insecure Software/Firmware:
Be sure that firmware and software running on the devices could be updated and that upgrade are made through secure processes that avoid any modification/substitution. Avoid software/firmware that have hard-coded credentials, and it is best practice to validate the software through digital signature of the source code.
I10 – Poor Physical Security:
Verify the physical security of smart devices defending the access to each port they expose. Usually, external accesses are left by manufacturers for maintenance purposes.
An attacker could exploit one of these accesses to inject malicious code, to exfiltrate data or to sabotage the smart object. It is suggested to encrypt data stored on the memory of the device and physically protect the USB ports and any other port by disabling the unnecessary accesses.
Under attack
Unfortunately, the attacks against IoT devices are becoming very frequent. Security experts have already spotted numerous threats targeting smart devices on a global scale. A botnet consisting of devices within the Internet of things, also known as thingbot, is already exploited by criminal crews to run cyber attacks against systems worldwide or to send out spam messages.
There are millions of vulnerable devices that could be potentially infected through a remote attack. These intelligent components are connected to the Internet and can potentially pose a risk to corporate networks and individuals.
The number of attacks against routers, SmartTVs, network-attached storage devices, gaming consoles and various types of set-top boxes is increasing. Computational capabilities of IoT devices and the ability to stay always connected to the Internet or any other network make these objects a privileged attack tool for hackers, wh could exploit them to:
-
Send spam.
-
Coordinate an attack against a critical infrastructure.
-
Serve a malware.
-
Work as an entry point within a corporate network.
In November 2013, security experts at Symantec spotted a worm, dubbed Linux.Darlloz, that was exploiting various vulnerabilities in PHP to infect Intel x86-powered Linux devices. The worm was able to compromise home Internet kits with an x86 chip, exploiting them to extend the infection. Routers and other network equipment were compromised by the diffusion of the malicious code.
"The worm, Linux.Darlloz, exploits a PHP vulnerability to propagate itself in the wild. The worm utilizes the PHP 'php-cgi' Information Disclosure Vulnerability (CVE-2012-1823), which is an old vulnerability that was patched in May 2012. The attacker recently created the worm based on the Proof of Concept (PoC) code released in late Oct 2013," states the Symantec blog post.
Despite that the worm was specifically designed to compromise Intel x86-powered Linux devices, the experts at Symantec discovered also a variant of the code compiled to run on ARM and MIPS. Analyzing the worm, the researchers observed that it was able to silently spread itself and wipe part of the system file.
The technique of attack was simple as it was efficient. The malicious code generates random IP addresses and attempts to use commonly used credentials to log into the target machine. The malicious code sends HTTP POST requests specially crafted to exploit vulnerable devices.
Once the malware identifies a not patched device and controls it, it simply downloads the worm from a server and starts searching for other targets running a web server and PHP.
In order to prevent device recovery, the worm kills Telnet services running on the smart component. In this way every remote connection to the device to restore a normal situation is impossible.
A few months later, in January 2014, researchers from Proofpoint uncovered another abuse of Internet of Things (IoT) devices. More than 100,000 refrigerators, SmartTVs and other smart household appliances had been hacked to send out 750,000 malicious spam emails.
"The attack that Proofpoint observed and profiled occurred between December 23, 2013 and January 6, 2014, and featured waves of malicious email, typically sent in bursts of 100,000, three times per day, targeting Enterprises and individuals worldwide. More than 25 percent of the volume was sent by things that were not conventional laptops, desktop computers or mobile devices; instead, the emails were sent by everyday consumer gadgets such as compromised home-networking routers, connected multi-media centers, televisions and at least one refrigerator."
Meanwhile, the attacks continue. Recently, experts at Akamai's Prolexic Security Engineering & Response Team (PLXsert) spotted a new malware kit named Spike, which is used to run DDoS attacks through desktops and Internet of Things devices. The Spike thingbot was able to run different types of DDoS attacks, including SYN, UDP, Domain Name System query, and GET floods against Linux based machines, Windows, and ARM-based Linux hosts.
The thingbot was composed of home routers, smart dryers, smart thermostats and other intelligent devices. Akamai noticed a number of devices for the Spike botnet ranging from 12,000 to 15,000. The researchers highlighted the ability of attackers to customize the malware also for ARM architectures widely adopted by IoT devices.
"The ability of the Spike toolkit to generate an ARM-based payload suggests that the authors of such tools are targeting devices such as routers and IoT devices to expand their botnets for a post-PC era of botnet propagation," says the Akamai advisory.
The researchers noticed that the Spike botnet was used for several "hit and run" DDoS attacks and involved both Windows and Linux machines, IoT devices and Raspberry Pi.
They also noticed that the new strain of Spike malware was based on an updated version of the Chinese language Spike malware that targeted poorly configured Internet-of-Things devices.
Akamai published an interesting report on the Spike botnet that includes details related to DDoS attacks run by the threat actor. The experts observed that one of the attacks clocked 215 gigabits per second (Gbps) and 150 million packets per second (Mpps). The document confirms that, even if the majority of the DDoS attacks launched from low-powered devices could be insignificant, IoT devices could anyway represent a powerful weapon in the hand of the attackers.
"Several Akamai customers have been targeted by DDoS attack campaigns launched from this botnet. One attack peaked at 215 gigabits per second and 150 million packets per second," the company wrote in an advisory.
Figure 2 - Spike botnet control panel
We may linger for hours speaking about the numerous attacks to compromise IoT devices in order to gain their control for illegal activities. One of the most striking cases happened at Christmas, when the networks of popular gaming platforms Sony PSN and Xbox Live were knocked out by an attack by the hacking group known as Lizard Squad.
The group used a DDoS tool dubbed Lizard Stresser for the attack, and according to the security expert Brian Krebs, its firepower is composed of thousands of hacked home Internet routers.
The Lizard Squad recently elaborated a commercial offer for the Lizard Stresser, which is proposing it with an attack-as-a-service model for sale, and the hacking of IoT devices could allow criminals to easily manage such kinds of offers.
Figure 3 -Lizard Stesser DDoS tool
The Lizard Stresser tool is a powerful DDoS tool that draws on Internet bandwidth from hacked home Internet routers worldwide.
In September 2014, experts at Kaspersky Lab uncovered a hacking campaign conducted by Brazilian threat actors which was targeting home routers by using a web-based attack. The attackers adopted different techniques, including social engineering and malicious websites, to change the DNS settings of home routers. The attacks, through the modification of DNS settings, allowed hackers to redirect victims to bogus websites designed to steal banking credentials of Brazilian Banks clients.
In March 2014, researchers at Team Cymru published a detailed report on a large scale SOHO pharming attack that hit more that 300,000 devices worldwide.
Not only malware
DDoS attacks run through a network of compromised Internet of Things devices are a rising trend. One point of strengths for attackers is the lack of security by design for these components.
In the majority of cases, IoT devices lack of any security mechanism and are difficult to maintain. Their firmware is developed without following best practices (e.g. the digital signature of source code, avoiding the presence of hard-coded credentials) and it is often hard to update.
One of the most clamorous cases that recently occurred was the disclosure of the Bash Bug (CVE-2014-6271) vulnerability, a flaw that impacted billion of devices worldwide running on Linux/Unix based architecture, including IoT devices.
Bash Bug is a remotely exploitable critical flaw that potentially still impacts not updated Internet of Things devices. Security firms confirmed that the Bash Bug vulnerability may have already been exploited in the wild by threat actors to hit smart devices adopted in different industries.
As we have said, in many scenarios the maintenance of such devices is very complicated, and sometimes the manufacturers don't provide continuous security updates, leaving them exposed to cyber threats.
Another vulnerability that menaced the Internet of Things is the popular Heartbleed, which can affect routers, PBXes (business phone systems) and many other smart objects.
Let's remember that the Heartbleed flaw allows anyone on the Internet to read the memory of the systems running vulnerable versions of the popular OpenSSL library.
A vulnerable IoT device connected to a server could be compromised if affected by a Heartbleed vulnerability by just sending a malicious Heartbeat message to it. The IoT device will then respond with extra data found in its memory, potentially exposing credentials and other sensitive data.
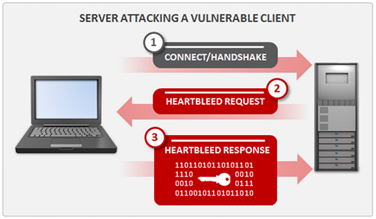
Figure 4 - Heartbleed attack on a client machine (Symantec)
Fortunately, as explained by experts at Symantec, while Heartbleed attacks against servers are not so complicated, offensives against clients on a large scale are hard to run in real-world scenarios. The two main vectors of attack to exploit the Heartbleed flaw in Internet of Things devices are instructing the smart objects to visit a malicious SSL/TLS server or hijacking a connection through an unrelated weakness. In both cases, the attacks are more complicated for the threat actors.
Conclusion
The Internet of Things is a paradigm that is changing our daily life. According to many experts, the paradigm is the link between human and technology. The Internet of Things needs security by design; for this reason it is a business opportunity for IT companies and security firms. Manufacturers must carefully evaluate the cyber threats and the level of exposure of IoT devices, implementing all the necessary countermeasures and allowing the updates of the firmware to respond the evolution of the menaces.
References
http://securityaffairs.co/wordpress/31062/cyber-crime/internet-of-things.html
http://securityaffairs.co/wordpress/18343/hacking/internet-of-things-hacking.html
http://securityaffairs.co/wordpress/21189/hacking/internet-of-things-cyber-threats.html
http://securityaffairs.co/wordpress/21397/cyber-crime/iot-cyberattack-large-scale.html
https://www.owasp.org/index.php/OWASP_Internet_of_Things_Top_Ten_Project
http://www.symantec.com/connect/blogs/securing-internet-things-wheres-risk?sf21585364=1
http://securityaffairs.co/wordpress/20084/malware/internet-of-things-worm.html
http://securityaffairs.co/wordpress/28008/cyber-crime/brazil-attacks-home-routers.html
http://securityaffairs.co/wordpress/30641/cyber-crime/symantec-cybercriminals-targets-iot.html
http://www.symantec.com/connect/blogs/linux-worm-targeting-hidden-devices
http://investors.proofpoint.com/releasedetail.cfm?ReleaseID=819799
Learn IoT Security
http://www.symantec.com/connect/blogs/heartbleed-poses-risk-clients-and-internet-things
http://securityaffairs.co/wordpress/32022/cyber-crime/lizard-stresser-hacking-tool.html









