IoT Security Fundamentals: Detecting and Exploiting Web Application Vulnerabilities
Introduction
In this article, we will be learning how to emulate a firmware for exploiting a web application vulnerability called blind command injection. This is found in the older firmware version of Netgear.
For sake of understanding, this post has been divided into two parts: firmware emulation and command injection exploitation.
Learn IoT Security
Part 1: Firmware emulation
What is emulation? Let’s understand the meaning of emulation in simple words. Suppose you get a firmware file (bin/img) from any source like their official website and you want to run that file, i.e., firmware img/bin file. How can you do so?
There are two ways:
- Hardware emulation: In this, you get a hardware device like a router, upload the firmware file onto the router and interact with the firmware via the router interface. The issue with this method is you always need an additional hardware device to run the firmware
- Software emulation: In this, we use software instead of hardware. Thus, the software mounts the firmware and you interact with the firmware interface. Biggest advantage using this method is you don’t need any separate hardware and you can run as much as firmware you wish to
In this post, we will focus on software emulation for mounting and interacting with the firmware.
Tools of the trade
The following tools are available for software emulation.
- Firmware Analysis Toolkit (FAT): FAT is the most widely used toolkit for firmware emulation. It uses tools such as Firmadyne, Binwalk, Firmware Mod Kit, MITM Proxy and Firmwalker for emulation. Please refer to FAT for setting up FAT on your system. We will use this tool for exploiting blind command injection.
- QEMU: QEMU is the emulator used for emulating firmware. More info on QEMU can be found here. For setting up QEMU please refer to QEMU-SETUP and for a firmware emulation demo using QEMU, you can check out this link.
We will be using FAT for our exploitation purpose. I hope you have set up FAT for firmware emulation using the abovementioned steps.
Now what we need to do is to mount the firmware. Please download Netgear Firmware for the demo.
Firmware emulation walkthrough
Step 1: Copy Netgear firmware in the Firmadyne folder, as shown.
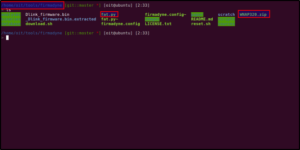
Now you should have the firmware file WNAP 320.zip and fat.py in the same folder. fat.py is the Python script which will help us in emulating the firmware.
Step 2: Run the fat.py script and enter the following details, as highlighted.
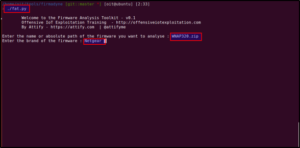
After pressing enter, it will ask you for a password 2-3 times. Enter the same password you have used for setting up Firmadyne. In my case, the password is firmadyne. After entering the password, wait for two minutes and it will give you the IP address of the firmware, as shown:
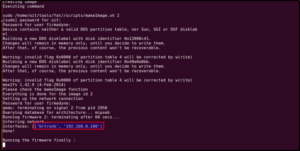
Step 3: Query the IP obtained in the above step. It may happen you may not be able to access the firmware on the first attempt. Try it four or five times and you should see the router page.
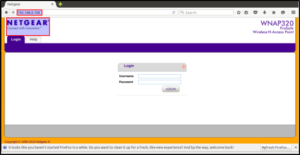
Step 4: Log in with the default username/password — admin/password.
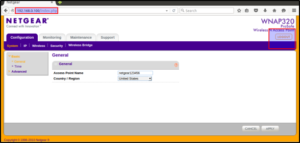
This is how we emulate firmware using Firmadyne.
Part 2: Command injection exploitation
We have already emulated the firmware. In this part, we will exploit the blind command injection present in it.
Overview
- Extract the firmware for viewing the source code of the file present in the firmware
- Inspect the source code for blind command injection exploitation
- Request the file in the browser
- Intercept the HTTP request of the file via a proxy tool (Burp Suite, Paros and so on) and change the parameters
- Command injection exploitation
Steps
Extract the firmware using binwalk -e and follow the steps, as highlighted:
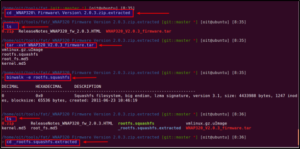
We are in the _rootfs.squashfs.extracted folder, which contains all the files present in the firmware.
Now we need to find PHP files present in the firmware. This can be done using following command -
find . -name “*.php”
- find — Name of the command
- . — Starting from current directory
- *.php — Any file ending with .php extension
This command will list all the php files present in the firmware, as shown:
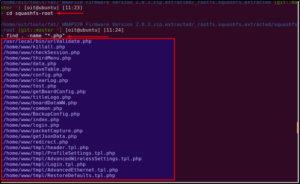
There exists a file called boardDataWW.php, which asks for the MAC address.
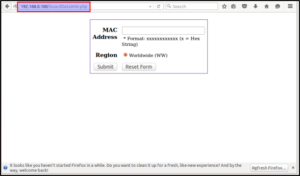
File boardDataWW.php is present in the home/www/ folder. Let’s see the source code of the boardDataWW.php file.
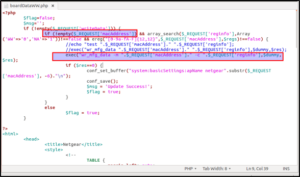
As highlighted, parameter macAddress is passed to the exec command (the second highlighted part) and the input is not filtered (first highlighted). exec is the function in PHP used for executing OS commands. The input is taken as-is; thus, we can also pass OS commands with the macAddress parameter.
Now intercept the request response in Burp Suite or OWASP ZAP. I am using Burp Suite and the process for intercepting in Firefox can be found here.
Intercepted request as shown:

Send this request to the repeater tab by right-clicking on it and select “Send to Repeater” option. Now we can enter any command in the macAddress field and check the response. Let’s enter 001122334455 -c ; ls # in the macAddress field.
- ; — Terminate the first command.
- # — Whatever comes after # will be treated as a comment.
So we are asking the exec function to execute mac_address_value -c ; our_command only and nothing after that.
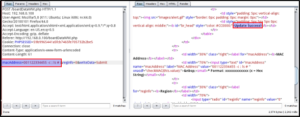
As seen, the response is Update Success!
We were expecting a list of directories in the response since we have passed the ls command, but we received Update Success in response. It means the command has been executed but did not return the result of our input. This is a typical example of blind command injection.
Let’s exploit blind command injection by outputting the result of the ls command in a file named demo.txt:

Now let’s access demo.txt from the browser and see the output.
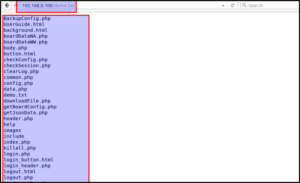
Voilà! It returns a list of all the files present in the firmware. Similarly, we can execute any OS command and get the output in the demo.txt file.
This is how one can exploit command injection vulnerabilities present in the firmware.
Learn IoT Security
Sources
- Unsecured IoT: 8 Ways Hackers Exploit Firmware Vulnerabilities, Dark Reading
- Pen-testing IoT Devices for Vulnerabilities, CloudSEK
- IoT Device Penetration Testing, OWASP









