The Rise of the IoT Botnet: Beyond the Mirai Bot
In the beginning, it was the Mirai botnet
IoT botnets are probably one of the most dreaded menaces in the threat landscape, poorly configured and flawed 'Internet of Things' devices represent privileged attack vectors for hackers in the wild.
In August 2016, the researcher MalwareMustDie analyzed samples of a new ELF Trojan backdoor, dubbed ELF Linux/Mirai, specifically designed to target IoT devices. Mirai is today the most popular IoT bot that was involved in large-scale attacks in the wild, but it is not the only one. Much other malware has been detected by security firms while targeting IoT devices; another dangerous thing both appeared in the wild such as the Leet Botnet and the Amnesia botnet.
Learn IoT Security
In this post, we will analyze the major IoT botnets recently discovered in the wild, and we will study the attack scenarios in which they were involved.
The Leet Botnet
Just before Christmas, on the morning of Dec. 21, experts from the firm Imperva observed a massive attack against the company. The massive DDoS attack was powered by the Leet Botnet and reached 650 Gbps. The Leet Botnet targeted several anycasted IPs on the Imperva Incapsula network.

Figure 1 - Leet Botnet malicious traffic
The experts who investigated the attack discovered that the botnet was composed of thousands of compromised IoT devices.
The attack was not launched against a specific customer of the company, likely because hackers were not being able to resolve the IP address of the victim that was hidden by the Incapsula mitigation proxies.
"It's hard to say why this attack didn't focus on a specific customer. Most likely, it was the result of the offender not being able to resolve the IP address of his actual victim, which was masked by Incapsula proxies," reads the analysis published by Imperva.
Incapsula observed two distinct DDoS burst, the first one lasted 20 minutes and peaked at 400 Gbps, while the second burst lasted around 17 minutes and reached 650 Gbps.
"The first DDoS burst lasted roughly 20 minutes, peaking at 400 Gbps. Failing to make a dent, the offender regrouped and came back for a second round. This time enough botnet "muscle" to generate a 650 Gbps DDoS flood of more than 150 million packets per second (Mpps)," continues the analysis.
Both attacks failed, but the researchers were not able to track the real source of the attacks because hackers used spoofed IPs.
The analysis of the content of the packets composing the malicious traffic revealed that the attack was powered by Leet botnet, so called due to a 'signature' within the packets.
"The first thing we noticed was that the offender left a "signature" of sorts in some of the regular-sized SYN packets. In the TCP Options header of these packets, the values were arranged so they would spell "1337". To the uninitiated, this is leetspeak for "leet", or "elite."" states Imperva.
Experts also noticed that the large content of the SYN payloads (799 to 936 bytes) that were populated by seemingly random strings of characters, others contained shredded lists of IP addresses.
"It seems that the malware we faced was programmed to access local files (e.g., access logs and iptable lists) and scramble their content to generate its payloads."
IoT Amnesia Botnet targets DVRs due to unpatched flaw
The Amnesia botnet exploits an unpatched remote code execution vulnerability that was disclosed more than one year ago by the security researcher Rotem Kerner.
The Amnesia botnet targets embedded systems, particularly DVRs manufactured by the Chinese TVT Digital that is currently sold under more than 70 brands worldwide.
Kerner reported the flaw to the DVR manufacturer in March 2016, but he received no response, so after a year he decided to reveal the details of the vulnerability.
According to the researchers at Palo Alto Networks who analyzed the threat, the Amnesia is a variant of the Tsunami botnet that is a downloader/IRC Bot backdoor used by cyber criminals to power DDoS attacks.
The vulnerability is still unpatched, and according to the results of an Internet scan conducted by Palo Alto Networks, there are roughly 227,000 vulnerable DVR devices in worldwide.
"Based on our scan data shown below in Figure 1, this vulnerability affects approximately 227,000 devices around the world with Taiwan, the United States, Israel, Turkey, and India being the most exposed," states the analysis published by PaloAlto Networks.

Figure 2 - Amnesia botnet
The Amnesia botnet was built exploiting the remote code execution vulnerability that allowed the attackers to take complete control of the devices.
A different analysis conducted with the Censys search engine revealed more than 700,000 IP addresses.
"Additionally, by using the fingerprint of "Cross Web Server," we discovered over 227,000 devices exposed on the Internet that are likely produced by TVT Digital. We also searched the keyword on Shodan.io and on Censys.io. They reported about 50,000 and about 705,000 IP addresses respectively," states PaloAlto Networks.
1. Taiwan 47170
2. United States 44179
3. Israel 23355
4. Turkey 11780
5. India 9796
6. Malaysia 9178
7. Mexico 7868
8. Italy 7439
9. Vietnam 6736
10. United Kingdom 4402
11. Russia 3571
12. Hungary 3529
13. France 3165
14. Bulgaria 3040
15. Romania 2783
16. Colombia 2616
17. Egypt 2541
18. Canada 2491
19. Iran 1965
20. Argentina 1748
The Amnesia bot is considered very sophisticated by experts because it implements evasion techniques, malware researchers believe it is the first Linux IoT malware adopting virtual machine evasion techniques to elude malware analysis sandboxes.
"Virtual machine evasion techniques are more commonly associated with Microsoft Windows and Google Android malware. Similar to those, Amnesia tries to detect whether it's running in a VirtualBox, VMware or QEMU based virtual machine, and if it detects those environments it will wipe the virtualized Linux system by deleting all the files in the file system," continues the analysis. "This affects not only Linux malware analysis sandboxes but also some QEMU based Linux servers on VPS or public cloud."
Experts at PaloAlto speculate the Amnesia botnet has the potential to become one of the major botnets in the threat landscape and would be used for large-scale attacks.
Brickerbot botnet permanently destroys IoT devices
On March 20, a few weeks ago, researchers at Radware have discovered a new botnet, dubbed Brickerbot that presented many similarities with the popular Mirai botnet.
The main difference between the Mirai botnet and the Brickerbot is this latter malware permanently destroys poorly configured IoT devices.
The Brickerbot botnet was discovered by Radware because it was targeting the honeypots deployed by the company for the malware analysis. The honeypot logged 1,895 infection attempts by Brickerbot botnet in just four days, most of the attacks were originated from Argentina, while 333 attempts came from a Tor node.
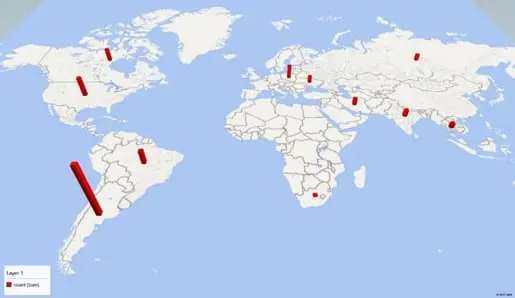
Figure 3 - Brickerbot botnet
"Over a four-day period, Radware's honeypot recorded 1,895 PDoS attempts performed from several locations around the world. Its sole purpose was to compromise IoT devices and corrupt their storage,"reads the analysis shared by Radware. "Besides this intense, short-lived bot (BrickerBot.1), Radware's honeypot recorded attempts from a second, very similar bot (BrickerBot.2) which started PDoS attempts on the same date – both bots were discovered less than one hour apart –with lower intensity but more thorough and its location(s) concealed by TOR egress nodes."
The Brickerbot botnet targets IoT devices by powering Telnet brute force in the attempt to compromise them; this technique was also implemented by the Mirai botnet.
The Bricker was very hard to analyze because it does not try to download a binary, this implies that experts from Radware were not able to retrieve the complete list of credentials used by the malware to brute force attempts. The malware researchers were only able to observe that the first attempted username/password pair was 'root'/'vizxv.'
"Bricker does not try to download a binary, so Radware does not have a complete list of credentials that were used for the brute force attempt but were able to record that the first attempted username/password pair was consistently 'root'/'vizxv,'" continues the advisory.
Experts explained the malware targets Linux-based IoT devices running the BusyBox toolkit which have their Telnet port open and exposed on the Internet.
The Permanent DoS (PDoS) attempt attacks were originated from a limited number of IP addresses, the targeted IoT devices expose the port 22 (SSH) and run an older version of the Dropbear SSH server. The majority of the devices targeted by the botnet was classified by the Shodan search engine as Ubiquiti network devices.
The malicious code first gains access to the device then it starts scrambling the onboard memory using rm -rf /* and disabling TCP timestamps. It also limits the max number of kernel threads to one.
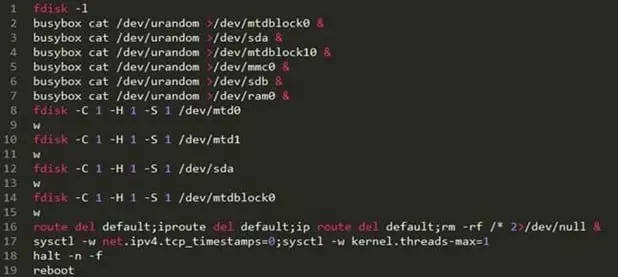
Figure 4 - Brickerbot Bot source code
Brickerbot malware also flushes all iptables firewall and NAT rules and adds a rule to drop all outgoing packets. It tries to wipe all code on the vulnerable IoT making them unusable.
Experts at Radware provided the following suggestions to protect IoT Devices:
- Change the device's factory default credentials.
- Disable Telnet access to the device.
- Network Behavioral Analysis can detect anomalies in traffic and combine with automatic signature generation for protection.
- User/Entity behavioral analysis (UEBA) to spot granular anomalies in traffic early.
- An IPS should block Telnet default credentials or reset telnet connections. Use a signature to detect the provided command sequences.
Conclusions
Unfortunately, the number of IoT botnets will continue to increase, these powerful infrastructures are very flexible and could be used by crooks for many criminal purposes.
The lack of security of most IoT devices exposed on the Internet represents today one of the greatest problems of the IT industry.
IT vendors will have to work to secure their IoT devices implementing a security by design approach.
References
/the-mirai-botnet-a-milestone-in-the-threat-landscape/
http://securityaffairs.co/wordpress/57839/malware/brickerbot-botnet-iot.html
http://securityaffairs.co/wordpress/57803/malware/iot-amnesia-botnet.html
http://securityaffairs.co/wordpress/54825/uncategorized/leet-botnet.html
https://www.incapsula.com/blog/650gbps-ddos-attack-leet-botnet.html
http://securityaffairs.co/wordpress/50929/malware/linux-mirai-elf.html
http://securityaffairs.co/wordpress/52544/breaking-news/dyn-dns-service-ddos.html
http://securityaffairs.co/wordpress/52558/iot/dyn-dns-service-ddos-2.html
http://securityaffairs.co/wordpress/52821/hacking/mirai-botnet-2.html
http://securityaffairs.co/wordpress/53054/malware/shadows-kill-liberia-outage.html
http://securityaffairs.co/wordpress/52015/hacking/mirai-botnet.html
http://securityaffairs.co/wordpress/52313/cyber-crime/sierra-wireless-mirai.html
Learn IoT Security
http://securityaffairs.co/wordpress/51669/hacking/internet-takedown.html









