Shodan and IoT: The Problem is here!
Introduction
Shodan a search engine which collects the information about all IPv4 and IPv6 devices connected to the internet and gives us the ability to search devices using filters that can be very sophisticated. It can search by OS Type, Server Banner, Geolocation, and has even an API for developers, which we will discuss later.
Learn IoT Security
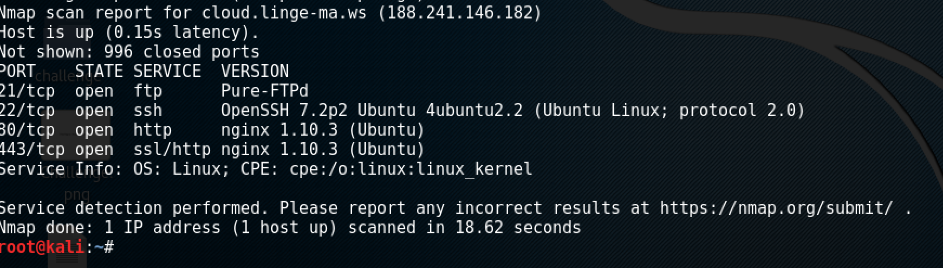
This can be possible because of the banners that Shodan can get by scanning the connected devices. It is a little bit like what we can get using a scanner such as nmap or Nessus. [CLICK IMAGES TO ENLARGE]
Figure 1: Example of scanning result from NMAP
Figure 2: Example of a search result from Shodan
Searching using the web interface
The simplest way to use Shodan is with the web interface. Yes, there is also a CLI that can be used from a Linux-based OS or via an API in multiple programming languages. We will discuss this in further articles.
Figure 3: Shodan search field
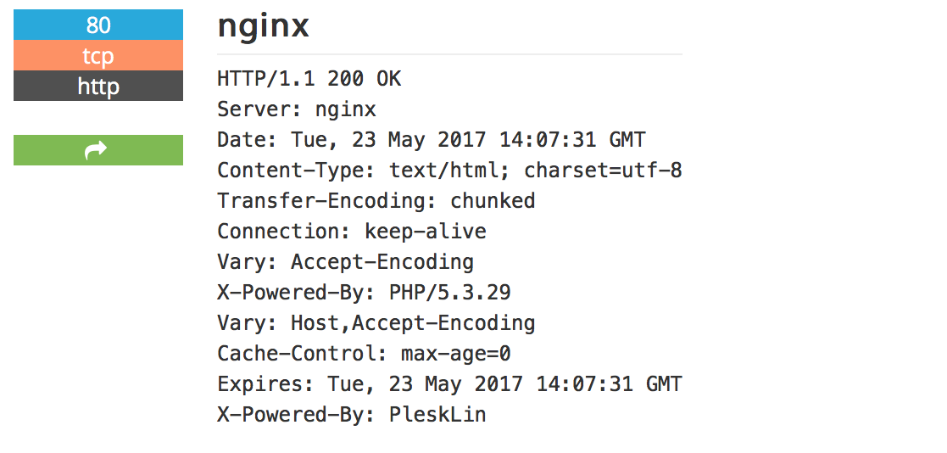
The initial results will only show us the information present in the banners related to the specified keyword, but we can also search using filters, which makes our search more efficient.
To obtain more information about the targets, we must click on details.
Figure 4: Search result sample
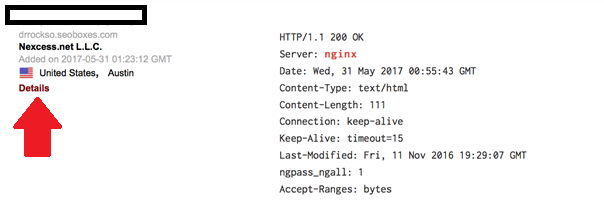
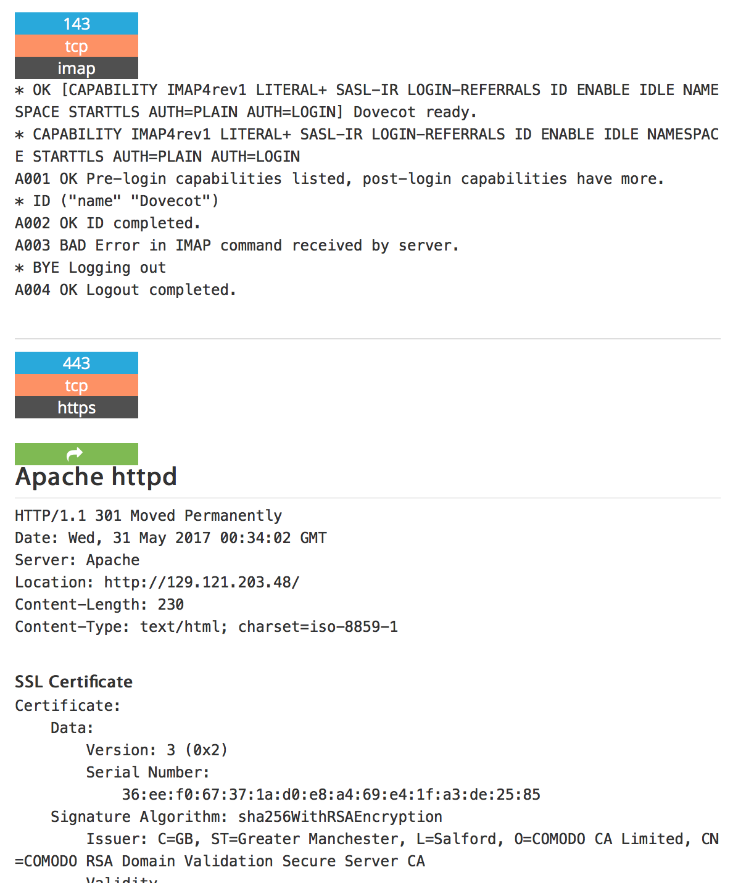
By clicking on details, we can see more information about open ports, services, content of banners, or metadata.
Figure 5: Metadata of a potential target
Figure 6: Open ports related to our potential target
Figure 7: Banners of services related to our potential target
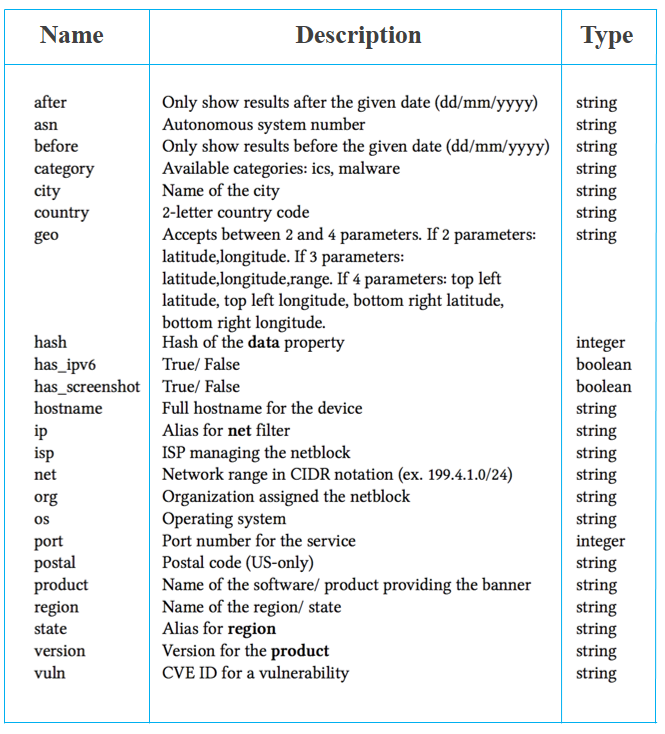
We can also go deep using filters that Shodan provides us, such as country, port, city, or OS.
Here are some examples of filters that we can use:
Figure 8: Filters that Shodan provides
Here are some search examples using filters:
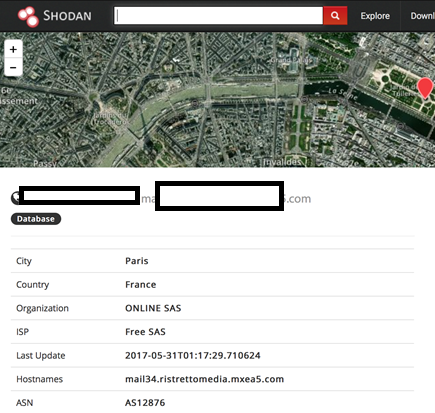
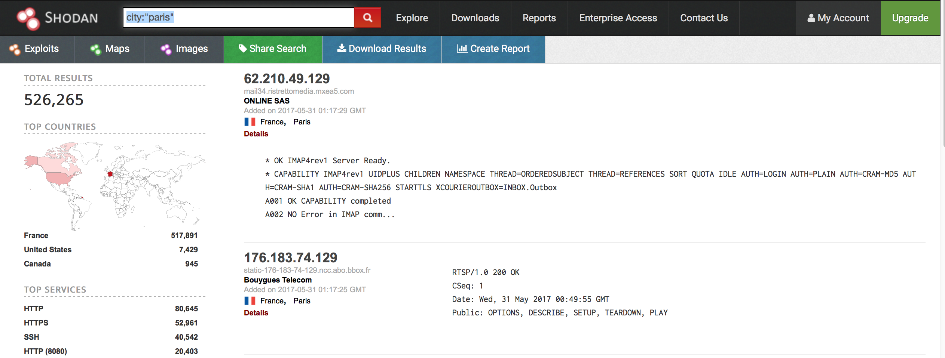
- By City: city: "Paris"
Figure 9: Search result using the 'city' filter
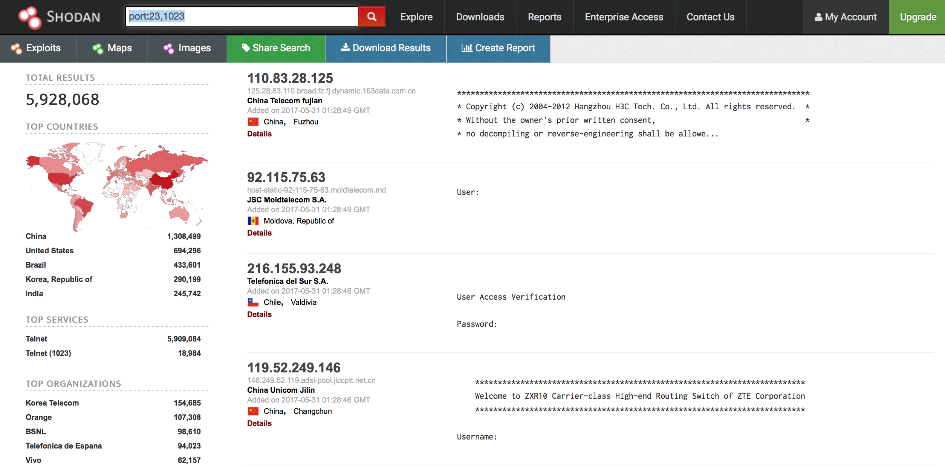
- By Port: port:23,1023
Figure 10: Search result using the 'port filter
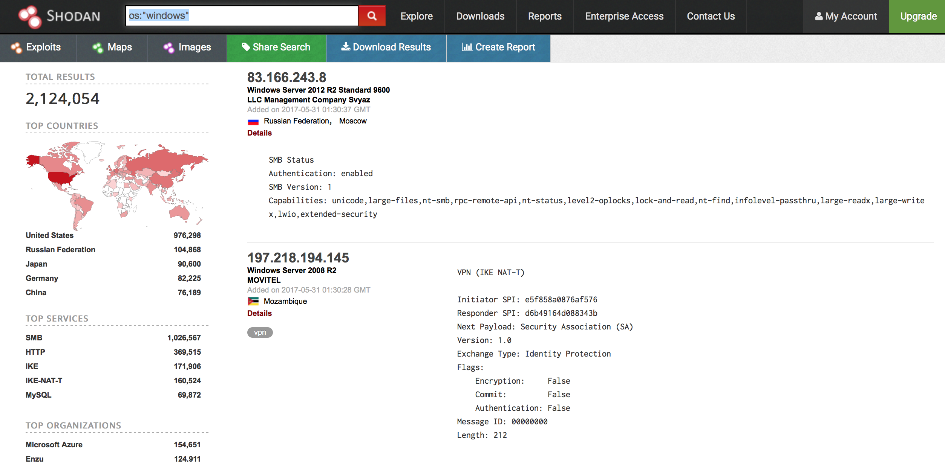
- By operating systems: OS: ''Windows''
Figure 11: Search result using the 'OS' filter
IoT and Shodan
As we know, security represents one of the most important issues of IoT, and as we saw, Shodan makes it possible to collect the address of any device connected to the internet, including the IoT devices. As we will demonstrate, this can be dangerous.
Here are some examples of some security flaws present on some IoT devices which permitted us to control some dangerous features. We used Shodan to find them. Keep in mind that for this article, we are just discussing smart home devices. The ICS are worse, and we will address these dangers in further articles.
Case 1: Heatmiser NetMonitor
The first product that we will talk about is one of the most famous cases of IoT security breaches – the Heatmiser NetMonitor.
The Heatmiser NetMonitor is a net-enabled thermostat with Wi-Fi control. Not only can you control it from a smartphone app, but also with a web browser.
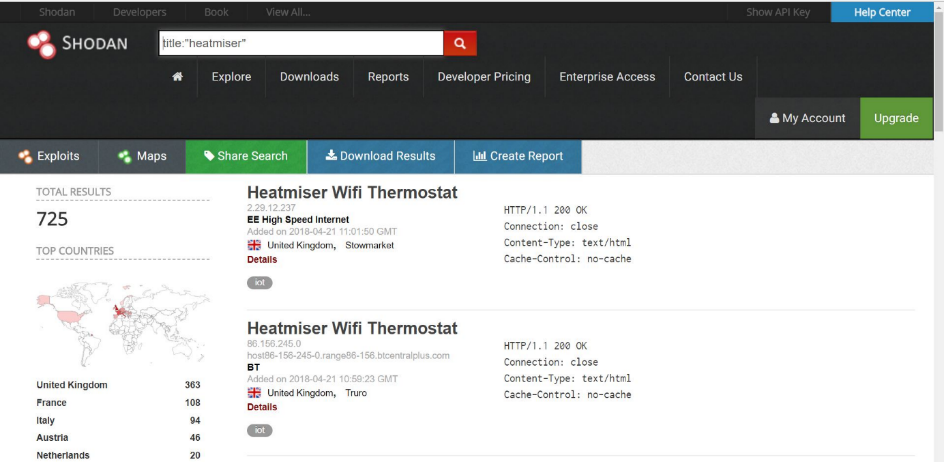
First, let's try to search using Shodan to find how much Heatmiser products are connected and accessible using the internet, and we found that there are 725 now I am writing this article.
Figure 13: Search results for Heatmiser NetMonitor
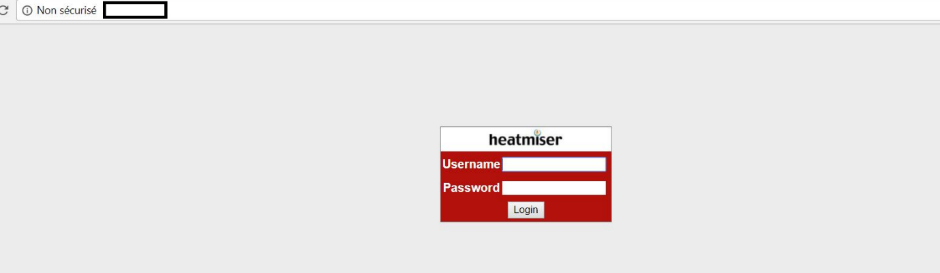
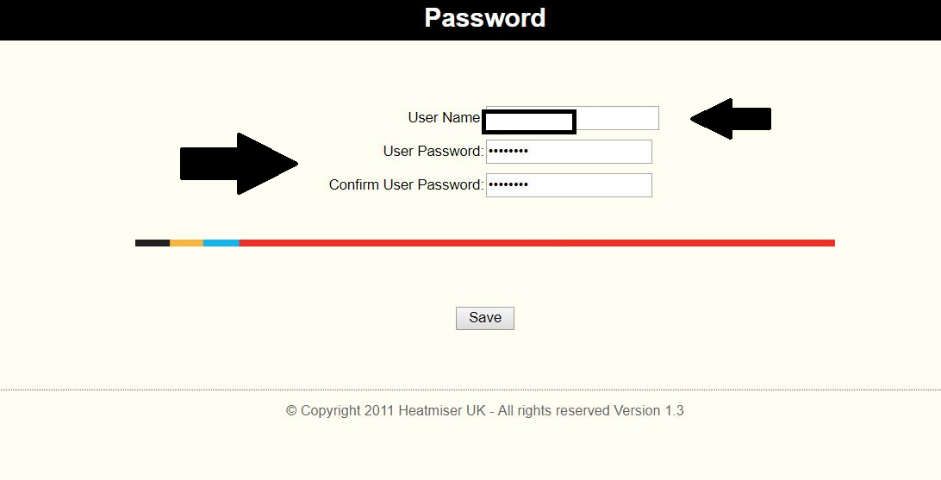
When we try to navigate to the IP address found, we can see the following page, which is an authentication page:
Figure 14: Heatmiser NetMonitor authentication page
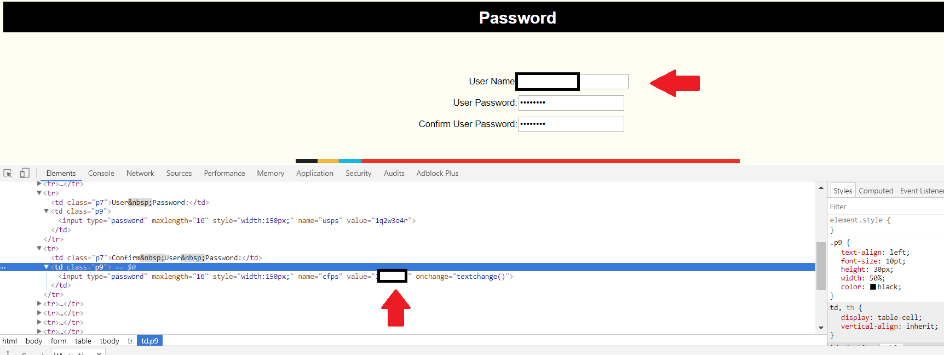
By searching on the net, we found that this product is affected by a vulnerability (Cleartext Admin Password Disclosure) that makes us able to access to the credential reset page and from this moment, all we must do is to inspect the fields and then retrieve the password clearly.
Affected Versions: Heatmiser NetMonitor 1.04, 1.1, 3.02, 3.03, 3.7, 3.8
All we must do now is to navigate to the "/networkSetup.php" page and then retrieve the credentials:
Figure 15: Heatmiser NetMonitor credentials reset page
Figure 16: Inspection of the credentials fields
And here's the admin page
Figure 17: Heatmiser NetMonitor admin page
Figure 18: Heatmiser NetMonitor admin page
The consequences of this simple manipulation could be fatal to a family member, especially the very young or elderly, from overheating or insufficient heat while the family is sleeping.
Case 2: Raytec
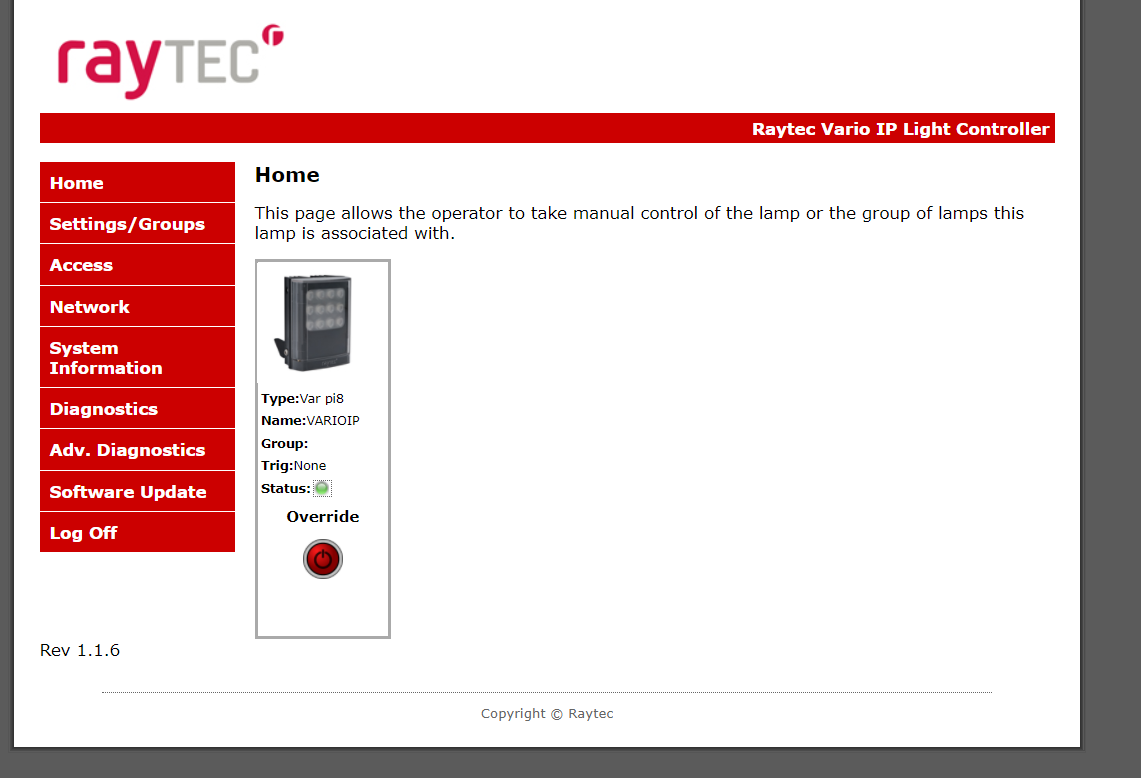
This second case is about the Raytec product, which is a connected light controller.
This time, we found that the most devices present in the search results are not configured properly, nor had the default password been changed for most of them. Just from exploring official documentation, we can access the device using the default credentials.
Figure 19: Raytec default credentials from official documentation
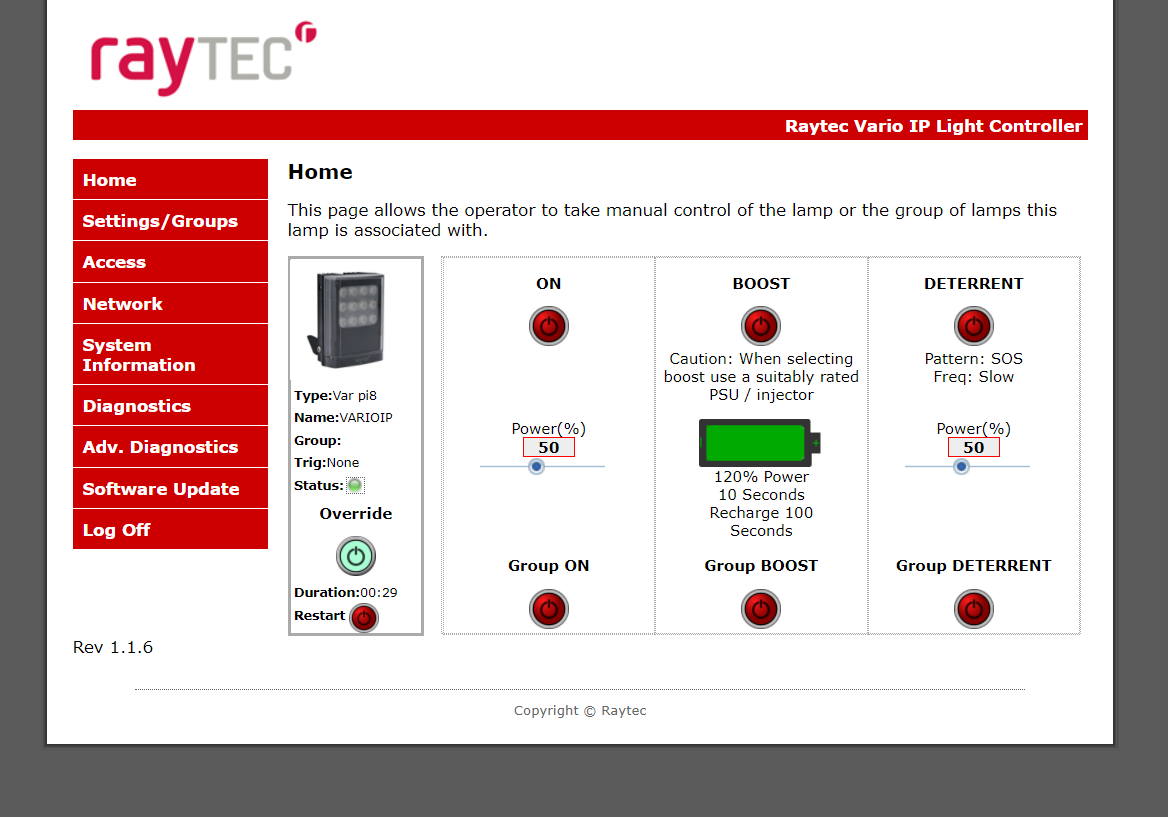
Then, we can access the admin panel:
Figure 20: Raytec light controller admin page
Figure 21: Raytec light controller admin page
This can cause a disturbing situation for the owner of the light controller or financial loss due, for example, to burning the lights all the time while no one is in the house.
Case 3: My Garage Controller
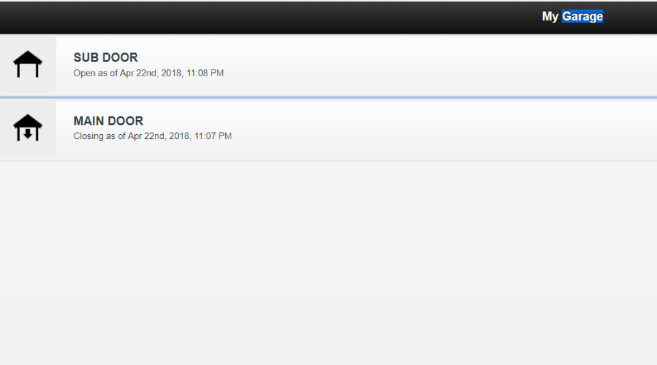
This last example is a sample of an IoT device control panel that is not secured even with a simple PIN or Password.
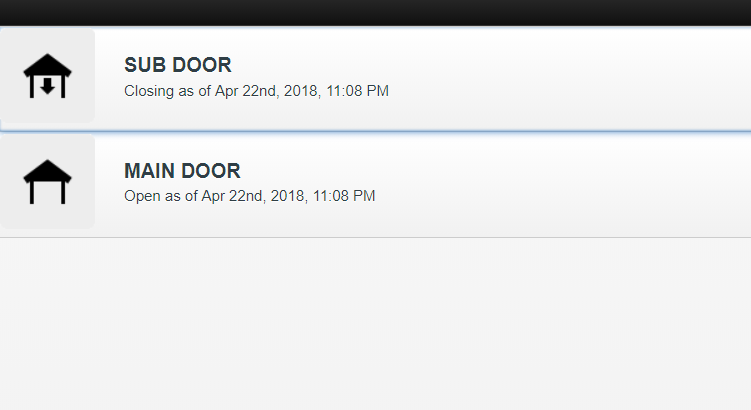
We accessed to the control panel of a garage with only the IP address of the control device. By a simple CLICK!
Figure 22: Garage Control admin panel
Figure 23: Garage Control admin panel
Moreover, in some cases, this can be extremely dangerous. Obtaining access to the garage can mean obtaining access to the entire house! It is not just your bike in danger.
How to defend yourself
- Stop Shodan bots
- Use HTTPS on your IoT devices
- Use Multi-Factor Authentication
- Change default credentials
- Shutdown unused services
- Patch your IoT devices
Learn IoT Security
Conclusion
This article is a simple example of what we can gather of IoT Devices from Shodan and how it can be easy to control generating a very dangerous situation that can even kill people if used by the wrong guys. IoT security is critical.