A full analysis of Horus Eyes RAT
While continuously developing new techniques to bypass security mechanisms, cybercriminals have combined private and underground projects and brought them to update their cyber arsenal. Horus Eyes RAT (HE-RAT) is one of the latest tools used along with the recent ‘warsaw’ banking trojan circumventing security appliances, AV and EDRs during its execution.
In this article, we will learn how ‘warsaw’ works, how Horus Eyes RAT has been used by criminals in their operations, and provide general measures to protect against threats of this type.
Warsaw loader as a vehicle to deploy HE-RAT
Horus Eyes RAT has been used in relatively high-profile activities involving a new banking trojan called warsaw as a vehicle to deploy the RAT on the victims’ machines at runtime. As detailed by Segurança-Informática, “Warsaw trojan banker tries to trick victims into proceeding with the infection chain using an overlay window from a popular bank.”
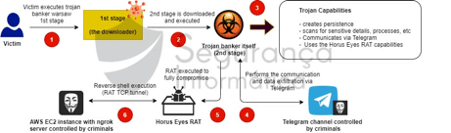
Figure 1 below shows the first stage, warsaw trojan, launched as the vehicle to install a modified version of the HE-RAT on the victims’ machines as its source code is now available on GitHub, and criminals are free to change it.
Figure 1: Malicious campaign using HE-RAT to fully compromise the victims’ machines (source).
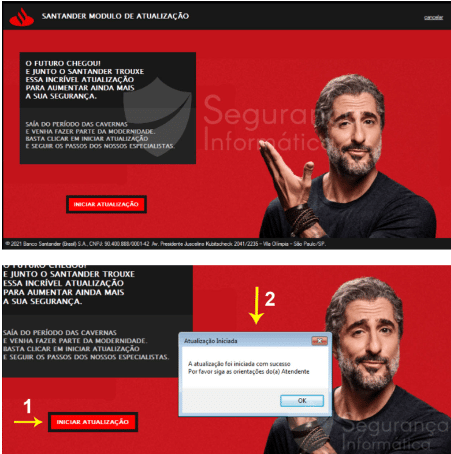
The warsaw trojan presents a fake popup window to lure the victim into downloading the second stage from the internet.
Figure 2: Fake popup window is shown by warsaw trojan to lure the victims (source).
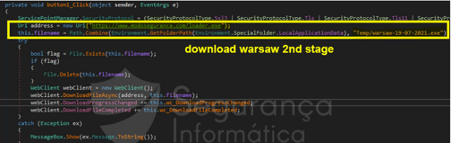
The deployment of HE-RAT relies on user interaction. After clicking on the “Iniciar ATUALIZAÇÃO” [“Start UPDATE”] button, the RAT binary is downloaded from a compromised domain used by criminals to distribute the threat in the wild. As observed in Figure 3, the PE file is downloaded into the “AppData/Local/Temp” OS folder and then executed.
Figure 3: Downloading the HE-RAT trojan into the “AppData/Local/Temp” dir and executed on the victim’s machine (source).
At that moment, the first stage of the infection chain is completed by the warsaw trojan, which downloaded and executed the RAT on the target machine. From this point on, a modified version of the Horus Eyes RAT is ready to capture the user’s activity, collect credentials, control the user navigation and allow the criminals remote access to the machine to fully compromise the system.
Modus operandi of Horus Eyes RAT
This sample of HE-RAT is an iteration of the Horus Eyes RAT source code available on GitHub that the cyber gang has improved. This fresh release introduces new features, e.g., it can gain persistence, gather details from the target machine, capture data from windows, match it with the target banking organization, and execute remote commands on the machine (RAT-like functionalities).
As stated by a Segurança-Informatica analysis that compared both the binaries: this fresh sample and the original code are available on GitHub; the improvement introduces some changes, including:
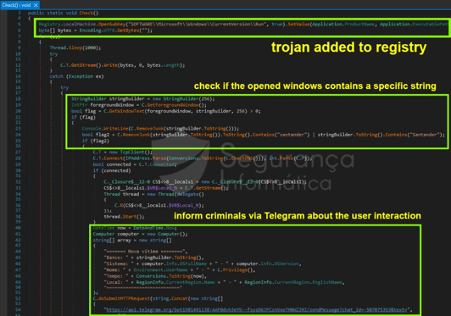
- A routine to add the binary on the registry CurrentVersion/Run to auto-execute the trojan at the Windows startup.
- It is a mechanism for notifying criminals via Telegram when a new victim is infected and then taking advantage of the Telegram API and protocol as it is secure to perform this kind of malicious activity.
- Use the full capabilities of the HE-RAT to gain control over the infected machines.
Figure 4: New features introduced by criminals on this HE-RAT release (source).
The RAT collects some information during its execution, including:
- Computer name
- Windows version
- Current region plus language
- Name of the target bank portal
- Get user privileges (normal user or administrator)
- Check the system architecture (x86 or x64).
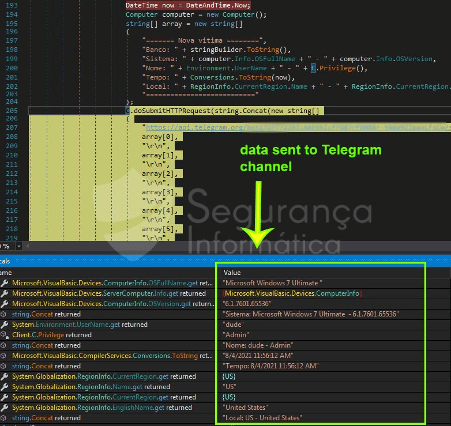
As observed in Figure 5, the gathered information is then organized into a string object and sent to the Telegram channel via the doSubmitHTTPRequest() call.
Figure 5: Information collected at runtime and sent to the Telegram channel controlled by criminals (source).
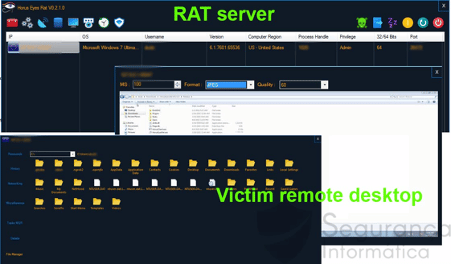
After this point, criminals have to monitor and cross-reference the information of the Telegram channel with the Horus Eyes RAT dashboard, where all the infected machines are available.
Figure 6: Horus Eyes RAT server dashboard (source).
With the full capabilities provided by the HE-RAT, criminals can remote access the compromised machines, execute remote code, collect and steal the victim’s secrets and impersonate the victim to access legitimate online services such as home banking portals, email and so on.
Understanding Horus Eye RAT
We are living in an era where malware regularly makes headlines. In recent years, many private tools have been brought by criminals from underground forums to enrich their arsenal with the most advanced techniques to bypass security mechanisms, thus impacting the most significant number of targets. Horus Eyes RAT is the actual proof of this scenario, especially noting the customized version we described and analyzed during this article.
Although there are no perfect measures and mitigations to fight malware in general, we can provide some guides to improve the security of your devices, namely:
- Do not open or download documents from unknown and untrusted sources. Put this into practice regularly when you are checking your email inbox.
- Update your software and the operating system. This is the principal pillar to face malware infections.
- Get into phishing training and cyber security programs. Keep in mind that social engineering is still the principal vehicle for distributing threats in the wild.
Sources
- Warsaw and Horus Eyes RAT analysis, Segurança-Informática