AstraLocker releases the ransomware decryptors
Astralocker is a piece of ransomware first identified in 2021. It is probably a fork from the well-known Babuk and other ransomware like Rook. Version 2.0 of AstraLocker appeared in March 2022 with a modus operandi never seen in other ransomware. It disseminates a weaponized Microsoft Word document to deploy the ransomware on the target instead of compromising the device and performing a data exfiltration scenario. This is, in fact, a different type of operation from other APT groups.

Become a certified reverse engineer!
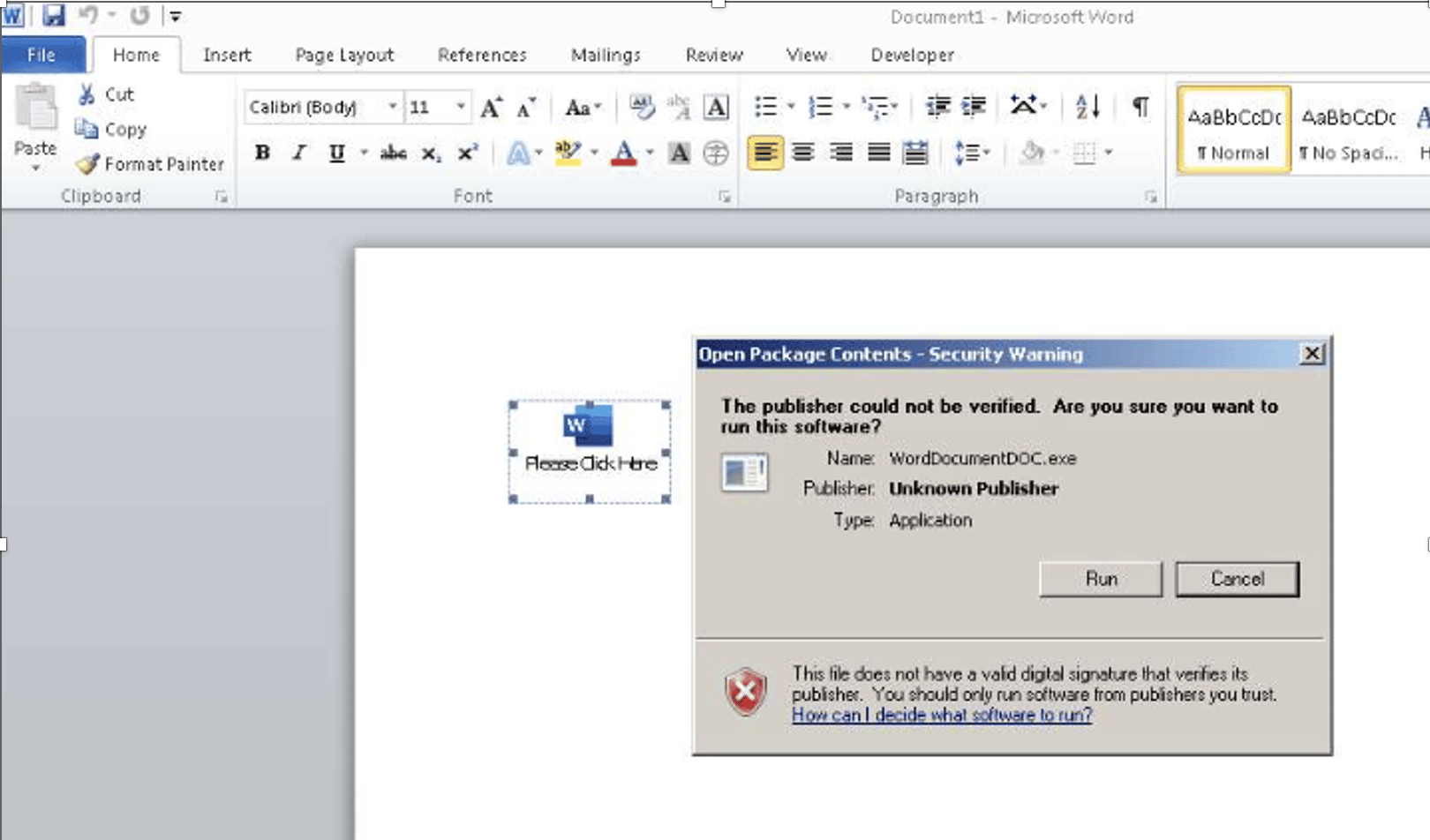
According to a ReversingLabs publication, the infection chain starts by disseminating a hidden OLE object with the ransomware payload that will be installed on the victim’s side after the first execution.
Figure 1: Malicious document with the OLE object containing the ransomware payload (source).
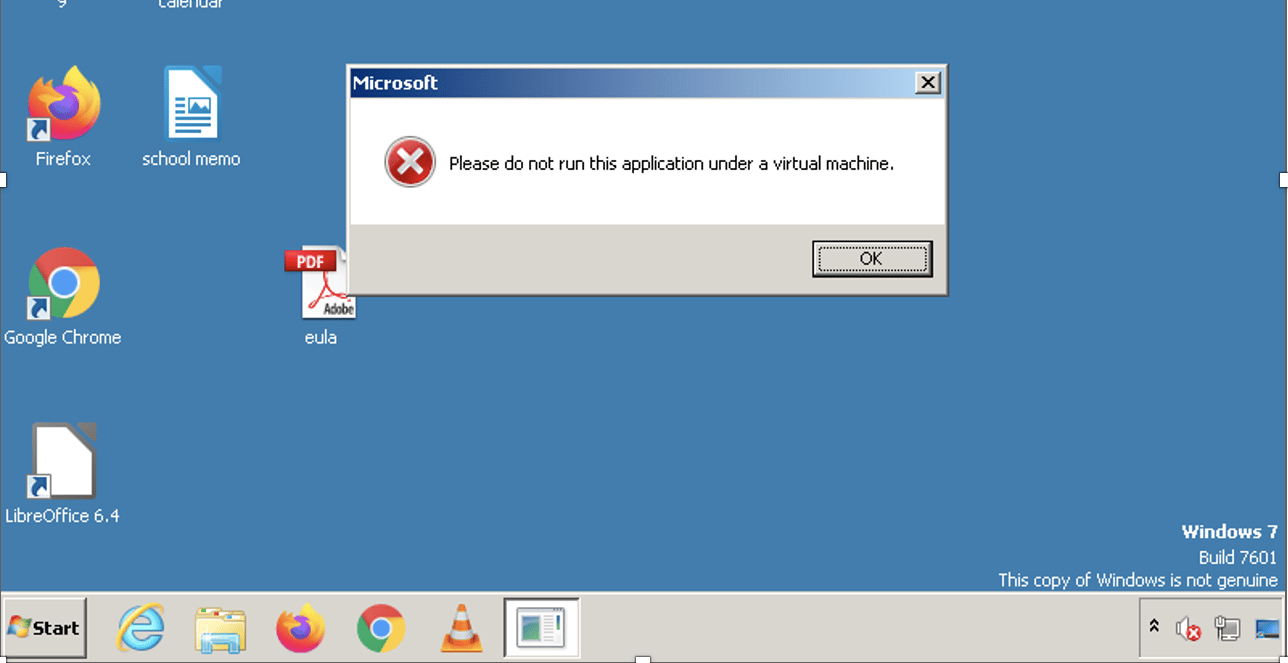
AstraLocker is protected with an outdated packer - SafeEngine Shielden v2.4.0.0 - that makes it difficult to analyze. If the malware is running inside a virtual machine, execution is terminated and a message box is displayed.
Figure 2: Anti-VM techniques used by AstraLocker ransomware.
Processes terminated in run-time
Ransomware typically looks for target processes and services during its execution. If a match occurs, the target process is terminated to have the maximum impact on the victim’s system and even make the data recovery process impossible.
Here is a complete list of backup and anti-malware processes:
On the other hand, a hardcoded list of target processes that could interfere with the encryption process are also terminated by the ransomware. They are:
Making data recovery impossible via VSS
As usual, volume shadow copies (VSS) is used to make data recovery impossible, VSS is deleted in run-time via the following Windows terminal command:
C:\Windows\System32\cmd.exe /c vssadmin.exe delete shadows /all /quietEncryption process
The encryption process is performed by the elliptic curve cryptography algorithm Curve25519. All the available shares and volumes are obtained and damaged during the ransomware execution.
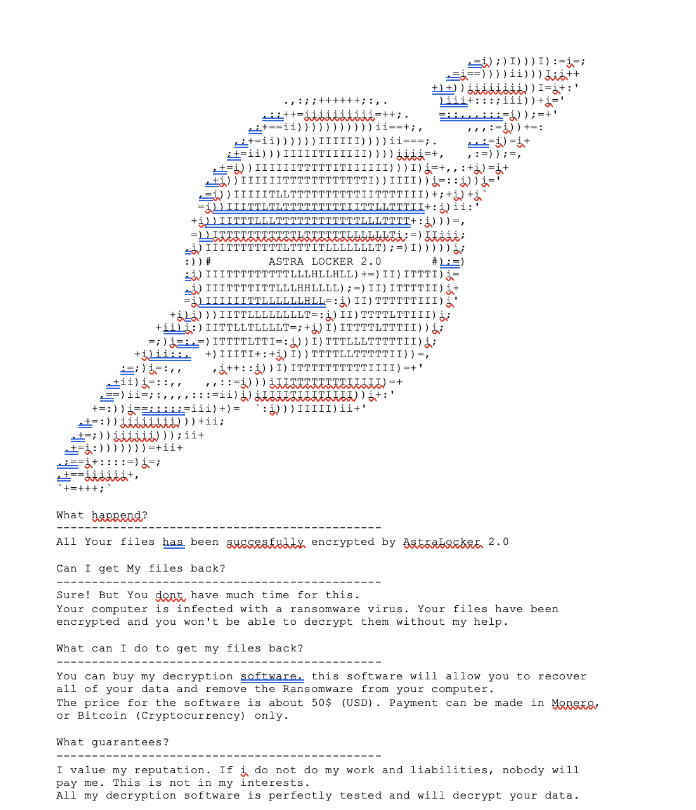
After that, the ransomware note is dropped with instructions on how to retrieve the lost data.
Figure 3: AstraLoker ransomware note.
AstraLocker 2.0 renames files with the .babyk extension, but other extensions are found in different samples, such as:.AstraLocker, .piton, .Astra, and random extension.
Ransomware operators released the decryption keys online
According to the Bleepingcomputer website, “the threat actor behind the lesser-known AstraLocker ransomware said they're shutting down the operation and plan to switch to cryptojacking.”
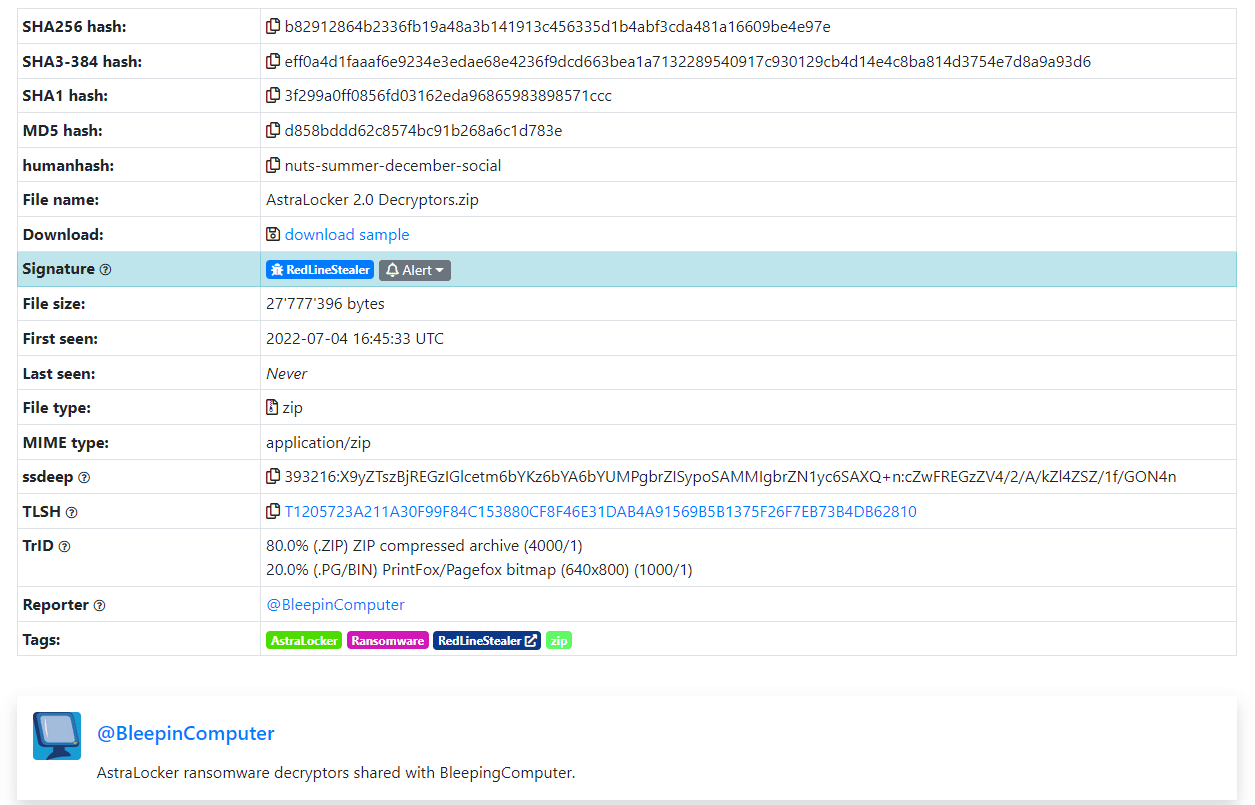
The ransomware operators submitted a ZIP file with the decryption data to the VirusTotal platform.
Figure 4: Decryption keys of AstraLocker 2.0 released online.
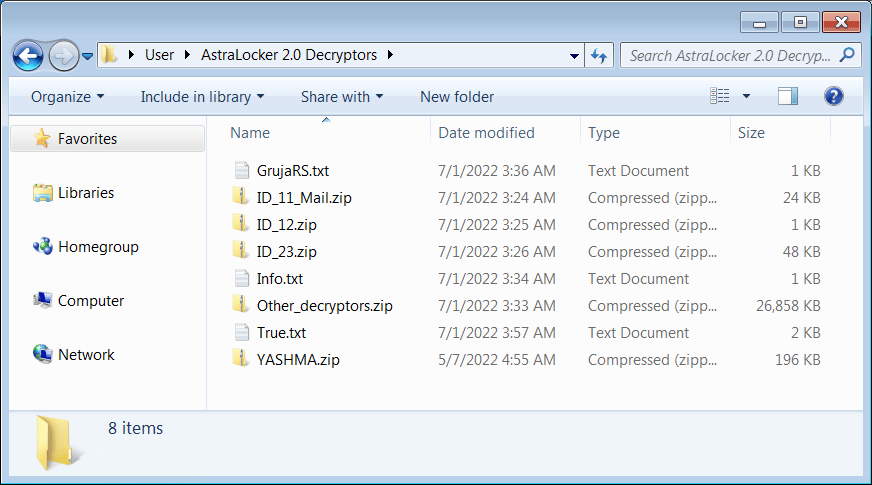
The file contains the decryption material necessary to recover files damaged in previous attacks by AstraLocker.
Figure 5: AstraLocker decryption material.
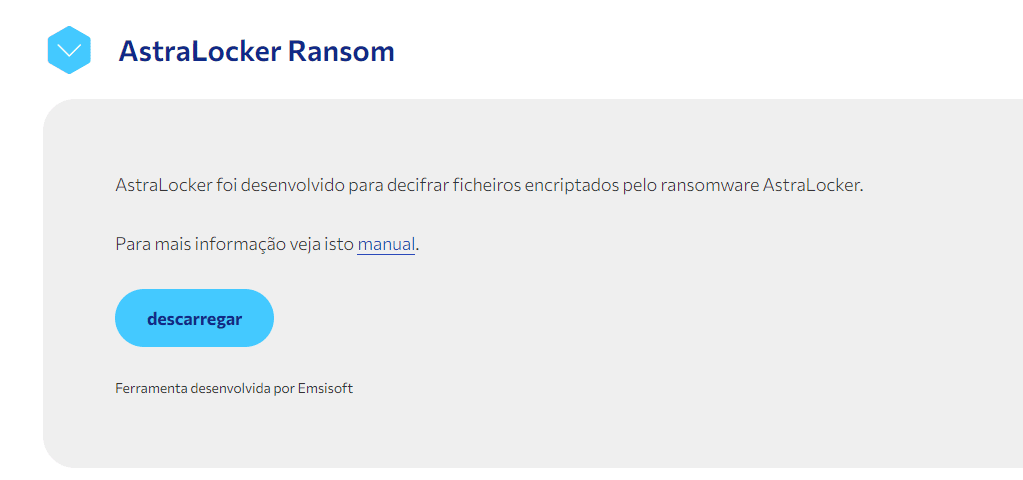
The material has been tested and now it seems safe to fully recover the damaged systems via AstraLocker. In addition, the AstraLocker decryption was added to the NoMoreRansom project, as can be seen below.
Figure 6: AstraLocker ransomware decryption available on the NoMoreRansom project website.

Become a certified reverse engineer!
Final Thoughts
Several wild pieces of malware use weaponized Word documents to target their victims. Many times, the success of infections depends on a victim double-clicking; this process relies on a security warning. With the introduction of Folina vulnerability, victim interaction is no longer needed, and criminals can take advantage of this scenario to deliver threats like ransomware worldwide via email.
All organizations and victims worldwide affected by AstraLocker ransomware can now recover their data for free because the decryption tool was released online by the author of the threat.
Sources:
Rook ransomware analysis, Infosec. Resources Institute
AstraLocker ransomware, BleepingComputer
AstraLocker analysis, ReversingLabs