Behind Conti: Leaks reveal inner workings of ransomware group
The Ukraine conflict comes to significant attention from the cybersecurity community because of cyberattacks conducted against Ukraine's infrastructure. One threat group that has increased its operations is Conti Ransomware Group.

Become a certified reverse engineer!
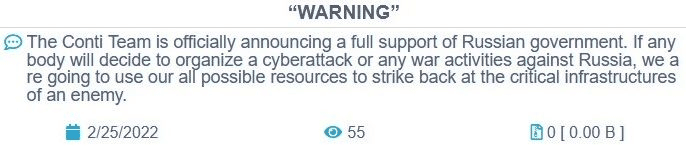
Conti Ransomware Group is one of the most emergent threat groups these days. After the beginning of the conflict in Ukraine, Conti released a statement informing the group is supporting the Russian government. The statement was published on its website, as observed below.
Figure 1: Conti's statement fully supports the Russian government.
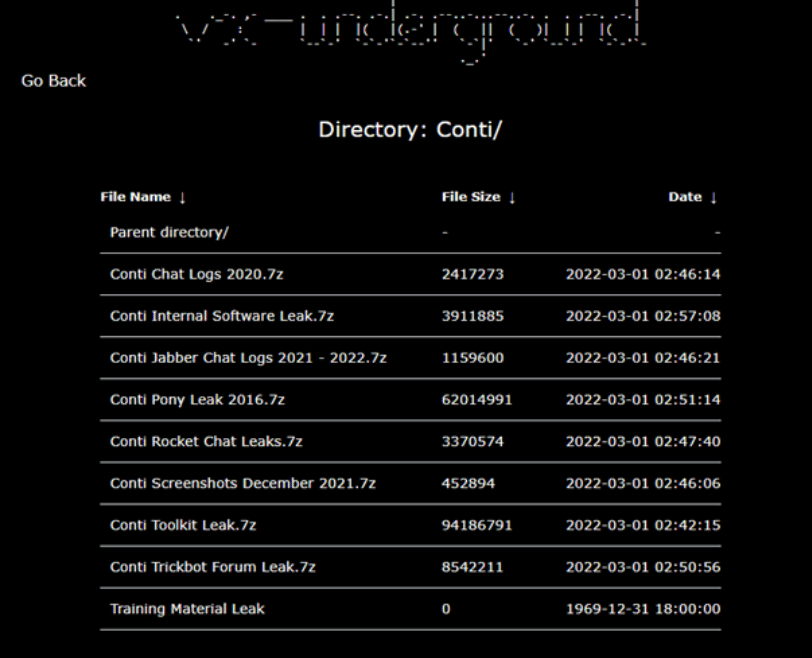
Two days after (Feb. 27, 2022), a new Twitter account was created to publish a large log containing hundreds of thousands of Jabber and Rocket Chat messages related to the internal group communications.
Figure 2: Conti leaks published online.
Several entities have conducted global research, revealing some of the operations, TTP, software and crimes associated with the threat group.
Although it is not the purpose of this article to present a full analysis of the entire process, we will present below some of the artifacts identified during this mega operation against the malicious group.
Conti's internal hierarchy
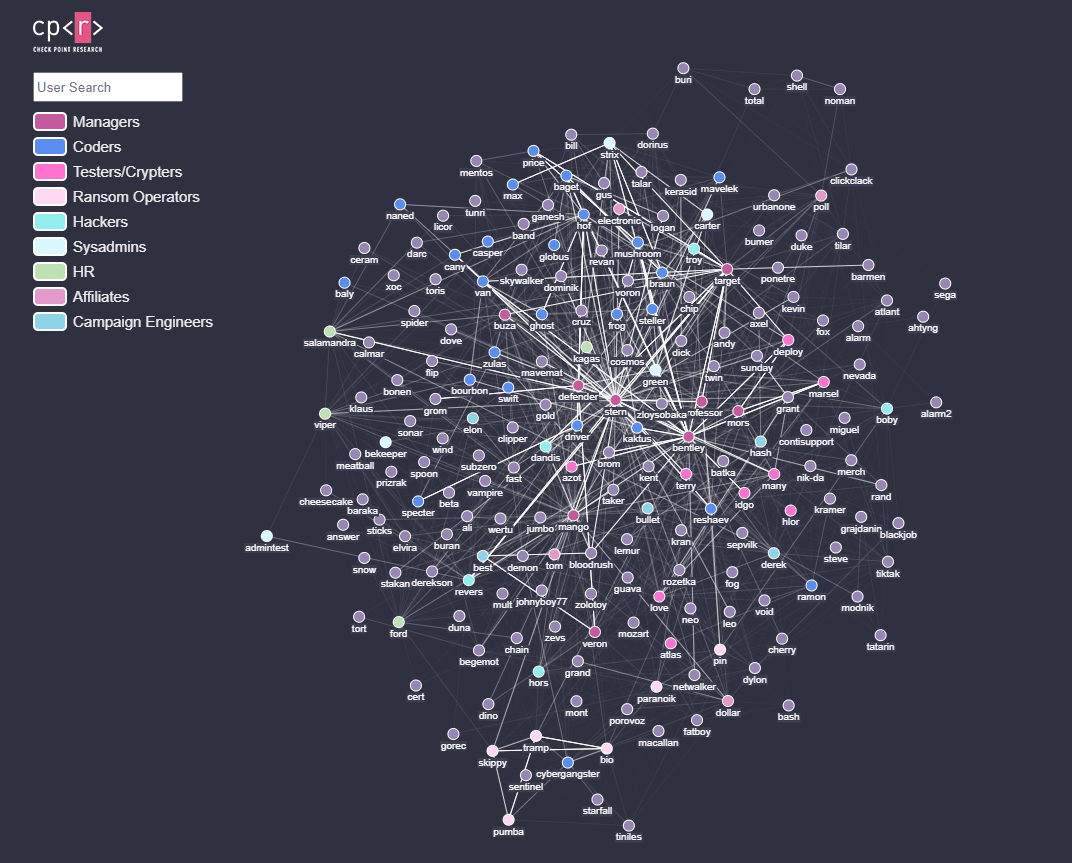
From a hierarchy graph by the CheckPoint research team, getting a high-level perspective about the teams and their responsibilities is possible. The next graph presents a graphical relation between the users present on Jabber logs and their professional occupation within the Conti hierarchy.
The principal groups observed are:
- Coders: Team responsible for maintaining malware code, back-end servers and admin web pannels.
- Testers/crypters: This team test and develop proof-of-concept codes to bypass detection. The knowledge acquired is then transmitted to the coders to implement bypassing features on the developed malware.
- Ransom operators: A team responsible for controlling all the ransomware operations.
- HR: A team responsible for making new hires, online interviews etc.
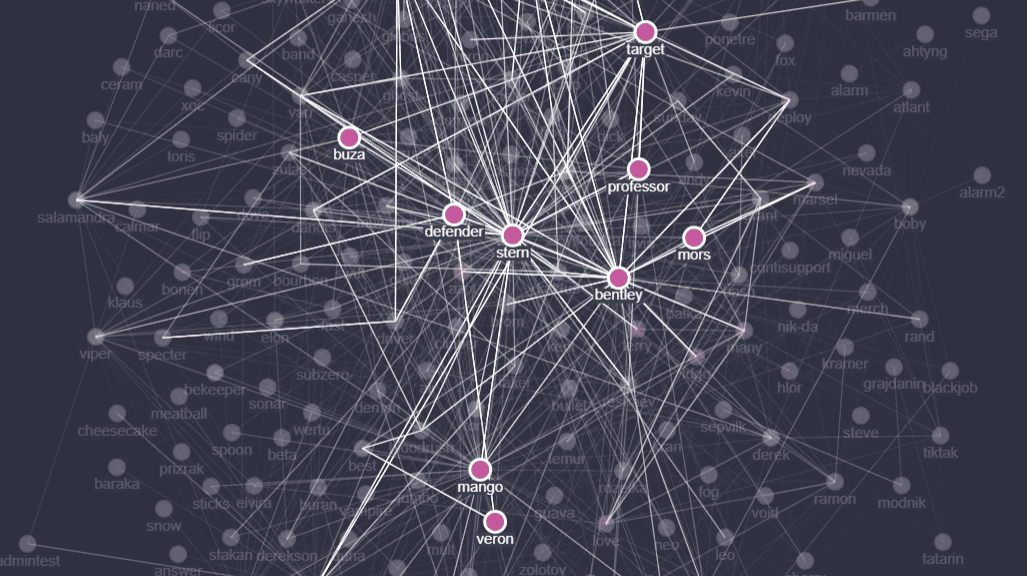
Regarding the CheckPoint analysis, it's also important to emphasize the following image where Conti's key members are highlighted.
Figure 3: Key members and their communications based on the leaked messages (source).
This graph reveals that "Stern" is potentially the big boss or leader of the group. The user behind the "Bentley" handle is a technical lead of the group with responsibilities for testing and evasion tasks.
On the other hand, "Mango" is a global team manager, "Buza" is a technical manager, and "Target" is the person responsible for the hacking team.
Finally, "Veron" aka "mors" is seen as the key point behind the entire operations related to Emotet malware.
The reverse side of the coin
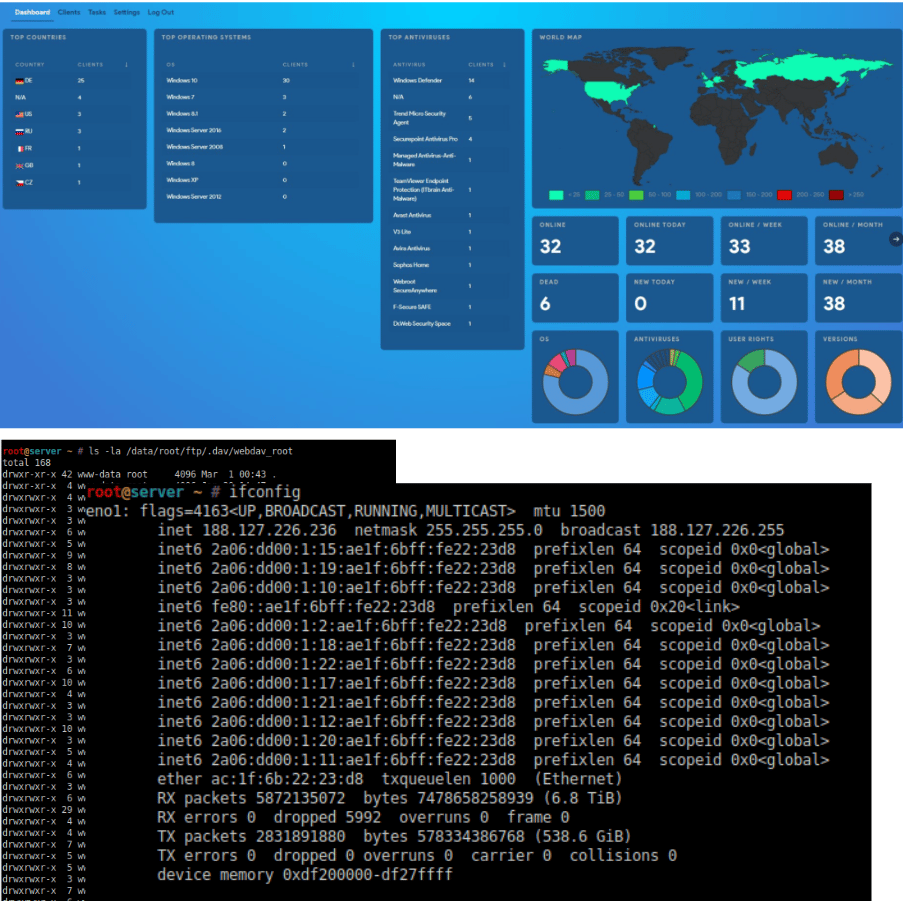
After the publication of several private data from the Conti Ransomware Group, as presented in Figure 2, a lot of information was also shared as a continuous work of a group of cyber security individuals.
Figure 4: Details about the Conti infrastructure.
Also, the source code of the ransomware used by Conti was shared. Now, a hacking group known as NB65 uses the knowledge and TTP obtained from the Conti group to create its ransomware against Russian organizations.
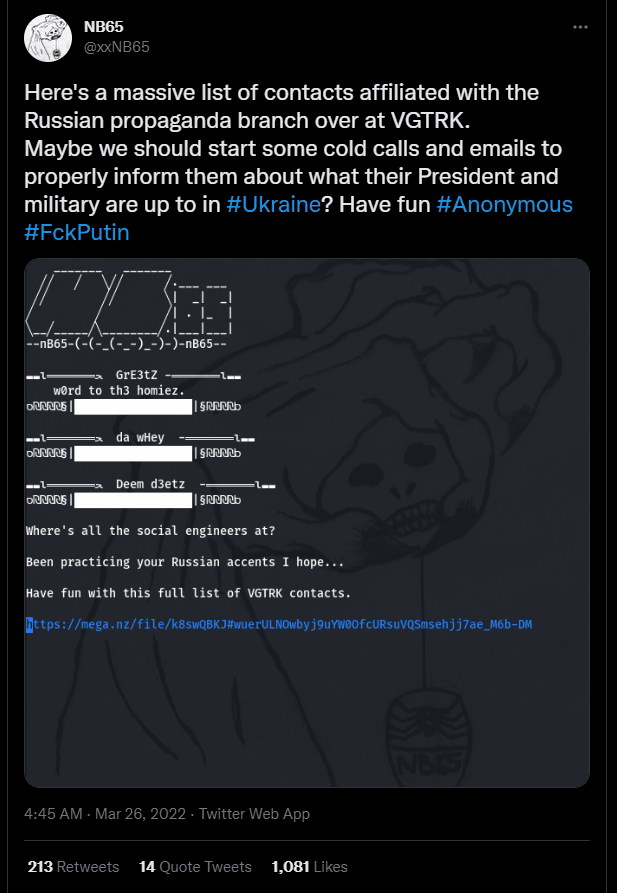
Since the last month, the NB65 group has attacked Russian-based organizations, leaking their data online. Some of the impacted organizations are Document Management Operator Tensor, Russian space agency Roscosmos and VGTRK, the state-owned Russian Television and Radio broadcaster.
Figure 5: Tweet about the recent operations of NB65 against Russian-based organizations.
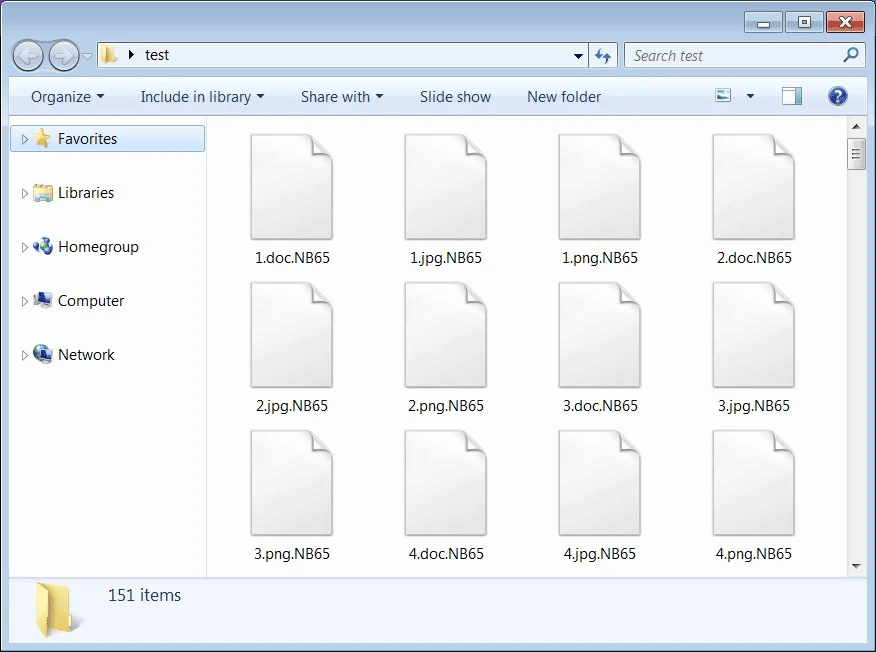
The ransomware takes advantage of the Conti group intelligence and TTP, encrypting all the files and appending the extension. NB65 to the damaged files.
Figure 6: Encrypted files by NB65 ransomware.
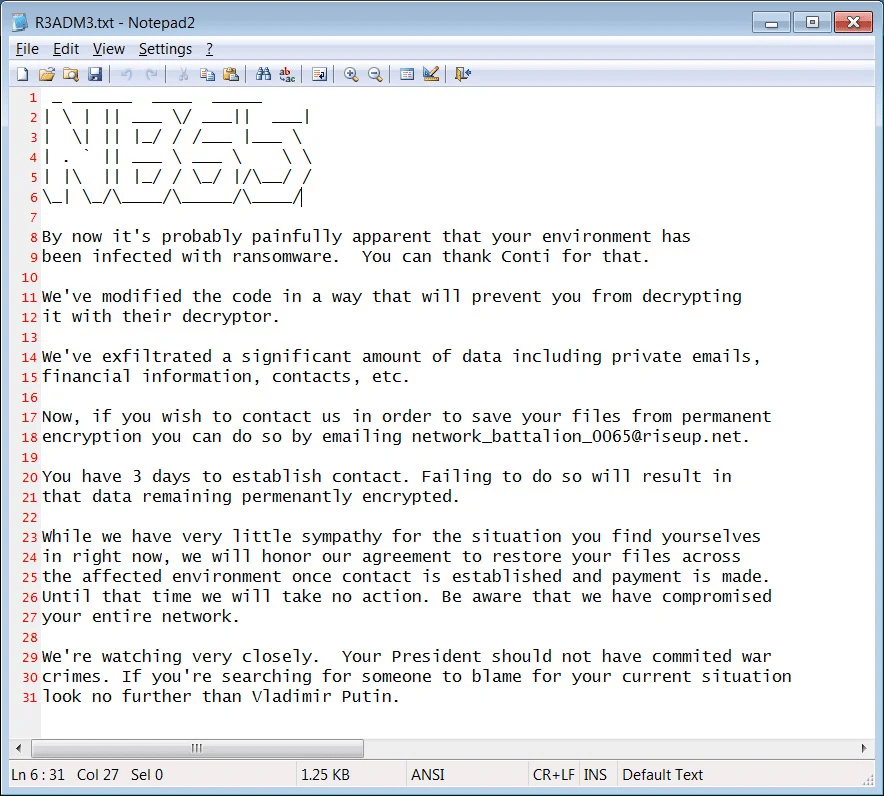
After the termination of its operation, the ransomware drops the ransom note with a specific target message blaming the cyberattack on President Vladimir Putin for invading Ukraine.
Figure 7: Ransomware note of NB65 ransomware.
Cyberattacks against Ukraine
The Conti leaks have high importance due to this Russia — Ukraine conflict. These leaks show how these giant ransomware gangs are operating and are often supported by governments or nation-state entities.
The data leak about the group revealed a lot of the details speculated for a long time by the community. As a result, it also fueled a new wave of attacks, with new pieces of malware emerging and adapted from the codes used by the group.
Sources:
- Leaks of Conti Ransomware Group, CheckPoint Research Team
- Conti Leaks, Trellix
- Hackers using Conti ransomware, BleepingComputer