Blackguard malware analysis
Blackguard malware is a popular stealer with recent tactics, techniques and procedures present and capable of stealing sensitive information from the victims’ machines.
Blackguard is a kind of MaaS (malware-as-a-service) software announced on underground forums with a lifetime price of $700 or a monthly price of $200.
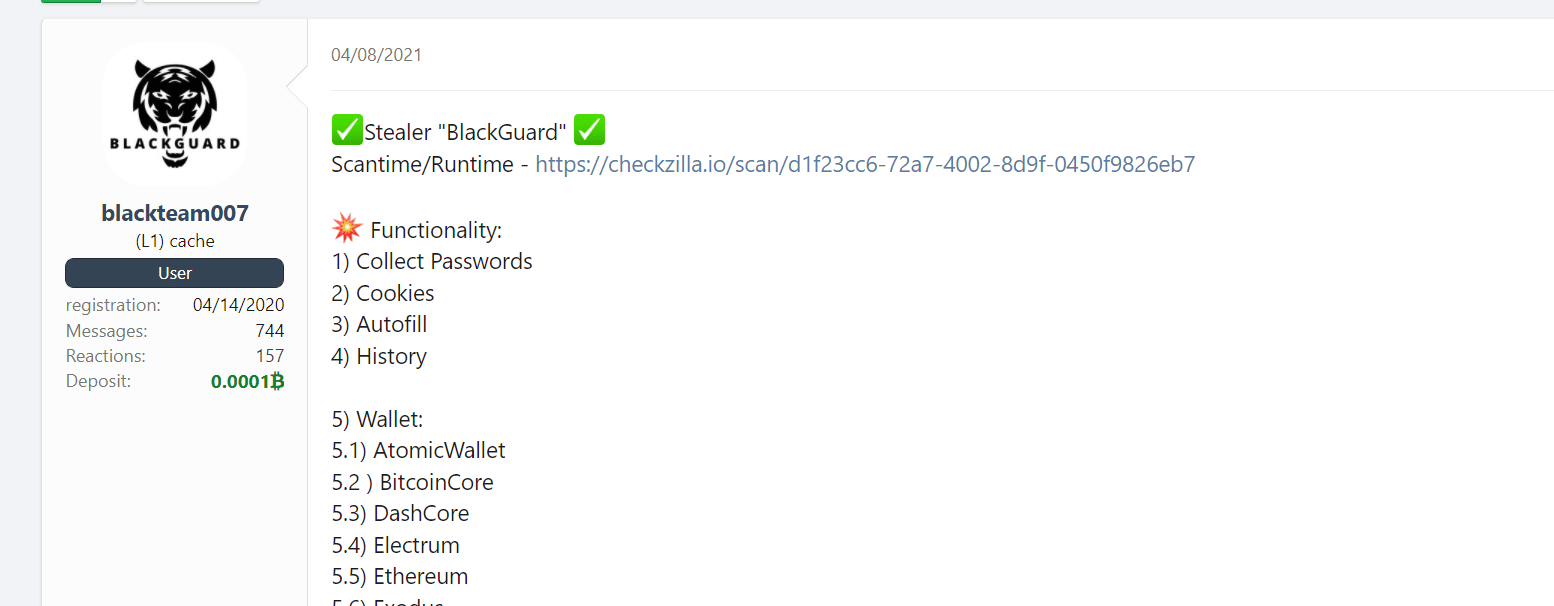
Figure 1: Blackguard stealer shared on underground forums in January 2022.
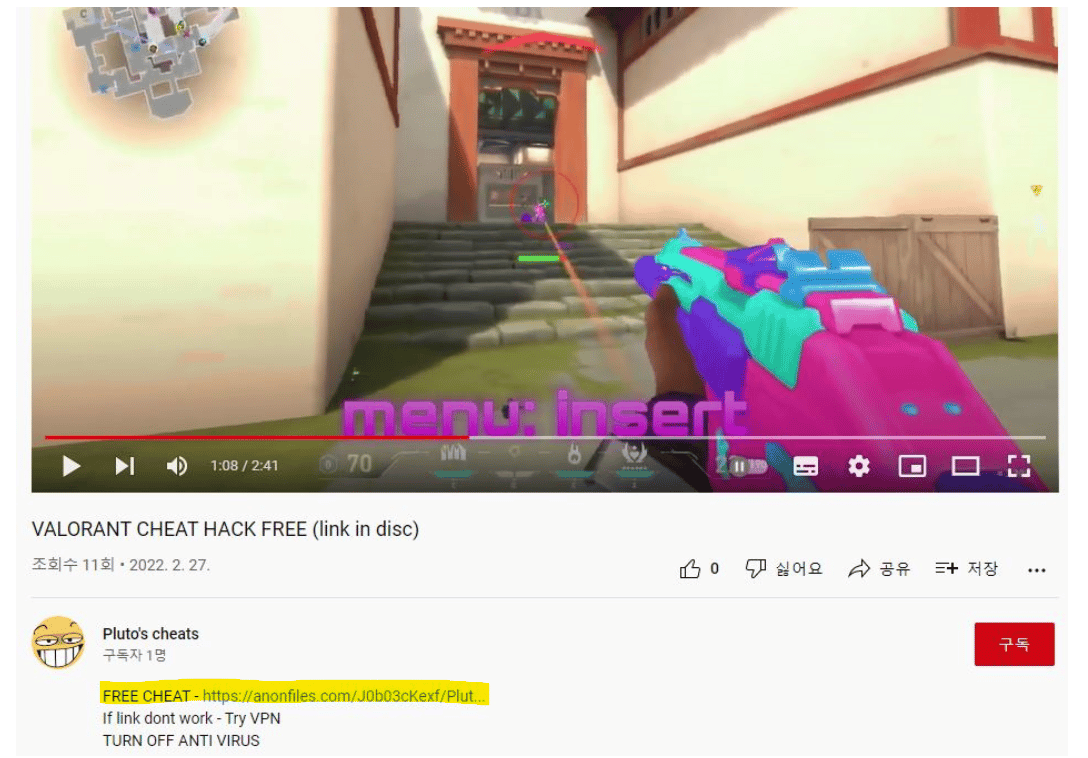
It is developed in C# and typically distributed in the wild through email, impersonating some legitimate software such as Windows Update files, Office documents, office installers, cleaning software etc. Also, Youtube videos promoting this piece of malware were found, potentially referring to a “Free cheat” software.
Figure 2: Blackguard malware disseminated on Youtube via attached URLs on videos’ descriptions (source).
Blackguard stealer is an improvement from the 44Caliber malware, and they are using the same TTP to steal credentials and details from the infected machines. It has been active since Jan. 12, 2022, and it was released on the Russian-based Forums, as presented in Figure 1. The available features depend on the package paid and the period of use.
Digging into the details
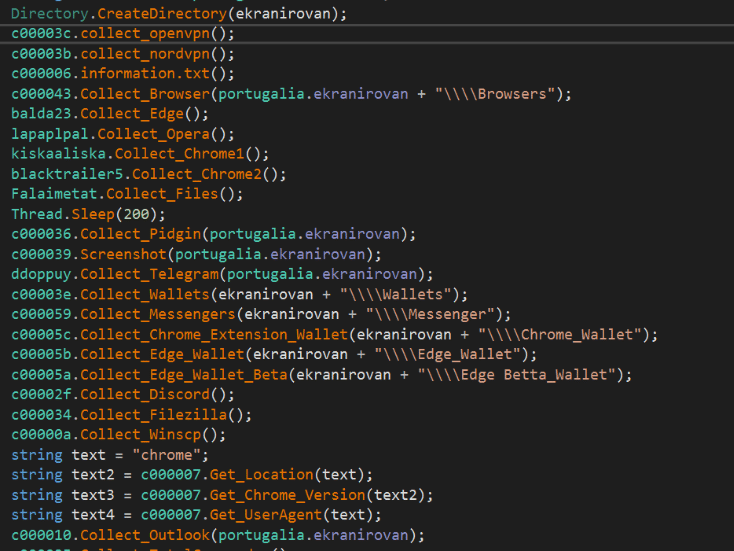
The workflow of Blackguard is simple: it validates if it is being executed under a sandbox environment, decodes its internal strings in memory, collects sensitive information, including browser information and crypto-wallets, and sends all the information to the Telegram channel.
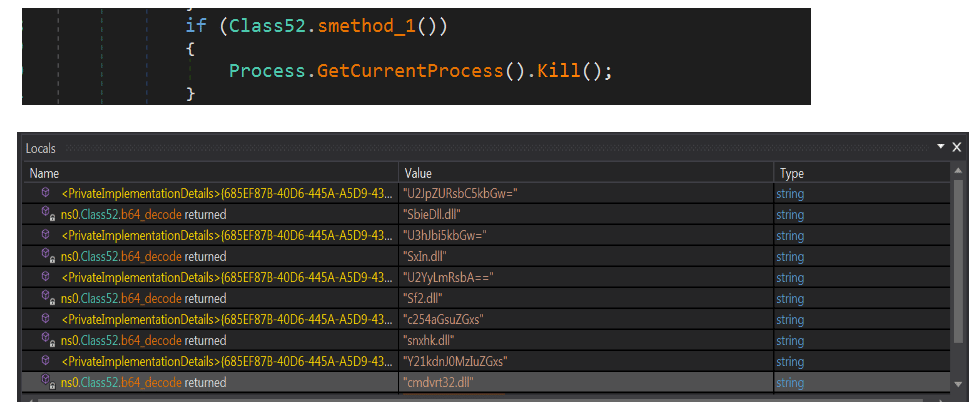
Figure 3: Blackguard malware detects AV processes and terminates its execution (source).
The malware strings are obfuscated with a base64 encoder and decoded in runtime. Although no effective string encryption algorithm is found, the base64 encoder prevents the plain-text strings are presented during the malware static analysis phase.
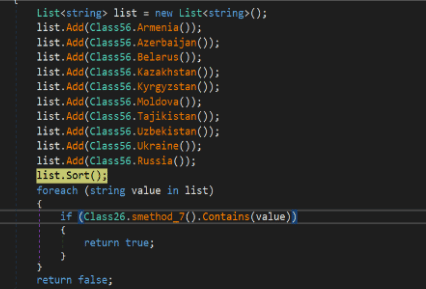
Like other malware from Russia, it checks if the target machine is geolocated in the Commonwealth of Independent States (CIS).
Figure 4: List of CIS countries and malware bypass infection.
The stealing process
At the time of collecting data, Blackguards calls several modules that will collect sensitive information from several locations, including:
- VPN credentials (OpenVPN and nordVPN)
- Browser data (cookies, passwords, etc.)
- Details from popular IM software (Telegram, Pidgin etc.)
- Screenshot feature
- Crypto-wallets
- Passwords from popular software (Outlook, WinSCP, FileZilla and Discord).
Figure 5: Collected details during the Blackguard execution.
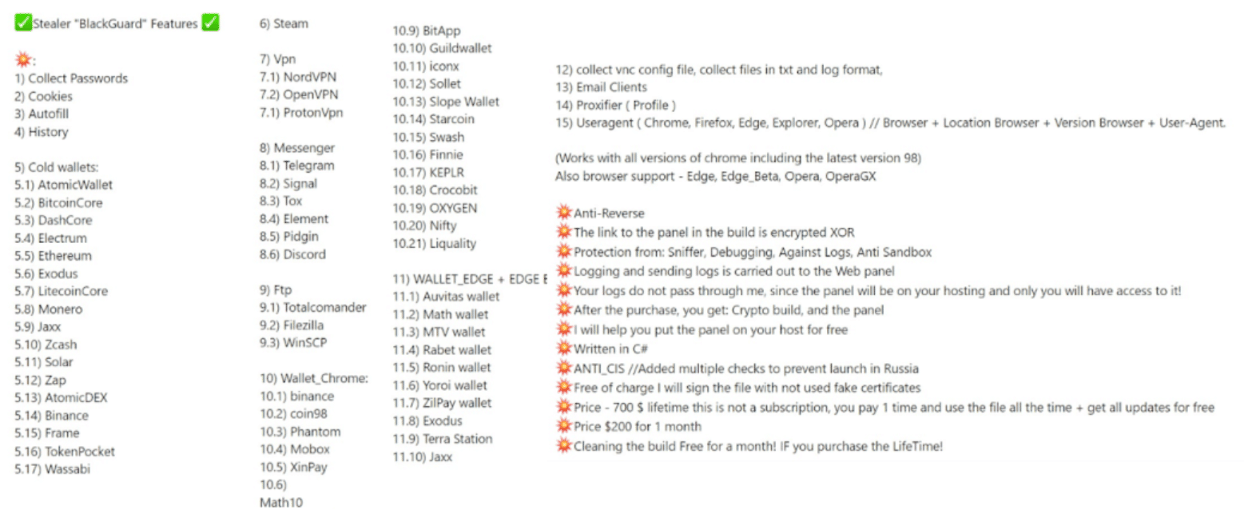
According to the Blackguard developers, the malware features depend on the price plan, and they are embedded in the malware binary as a result. The full features list can be obtained from the Russian-based forum and are present in Figure 6 below.
Figure 6: Complete list of Blackguard features depending on the malware plan.
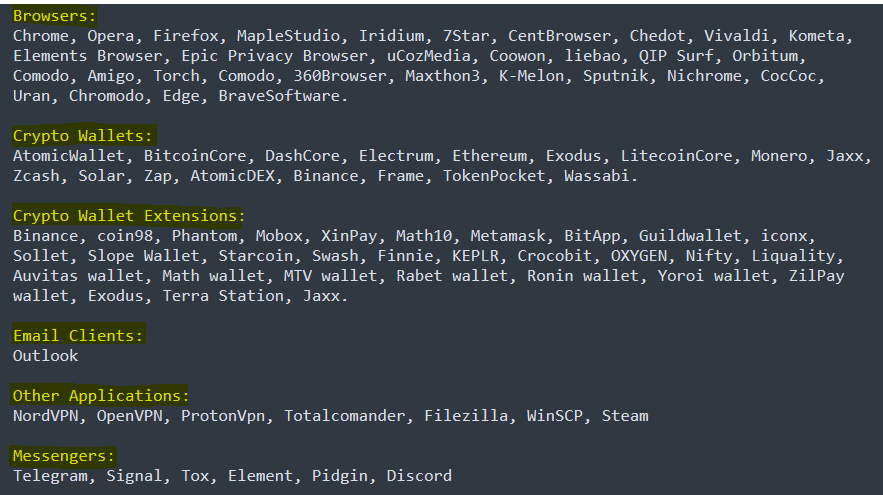
In detail, the targeted application of Blackguard are the following:
Figure 7: Targeted applications found inside the Blackguard binary file (the full version).
C2 communication
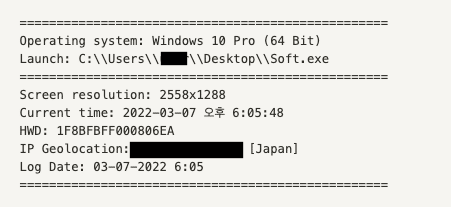
The popular use of Telegram within this context is on the rise. Criminals are using a Telegram channel to receive notifications about new infections. On the other hand, a C2 server is also used to receive a POST request with the ZIP file with all the information obtained from the victims' machines. Also, some details about the machine are captured, including a screenshot, screen resolution, current time, HWD and victims' geolocation. The geolocation is an important field to group the victims by country on the malware web pannel.
Figure 8: Captured information about the victim machine during the malware execution and stored in a file called info.txt.
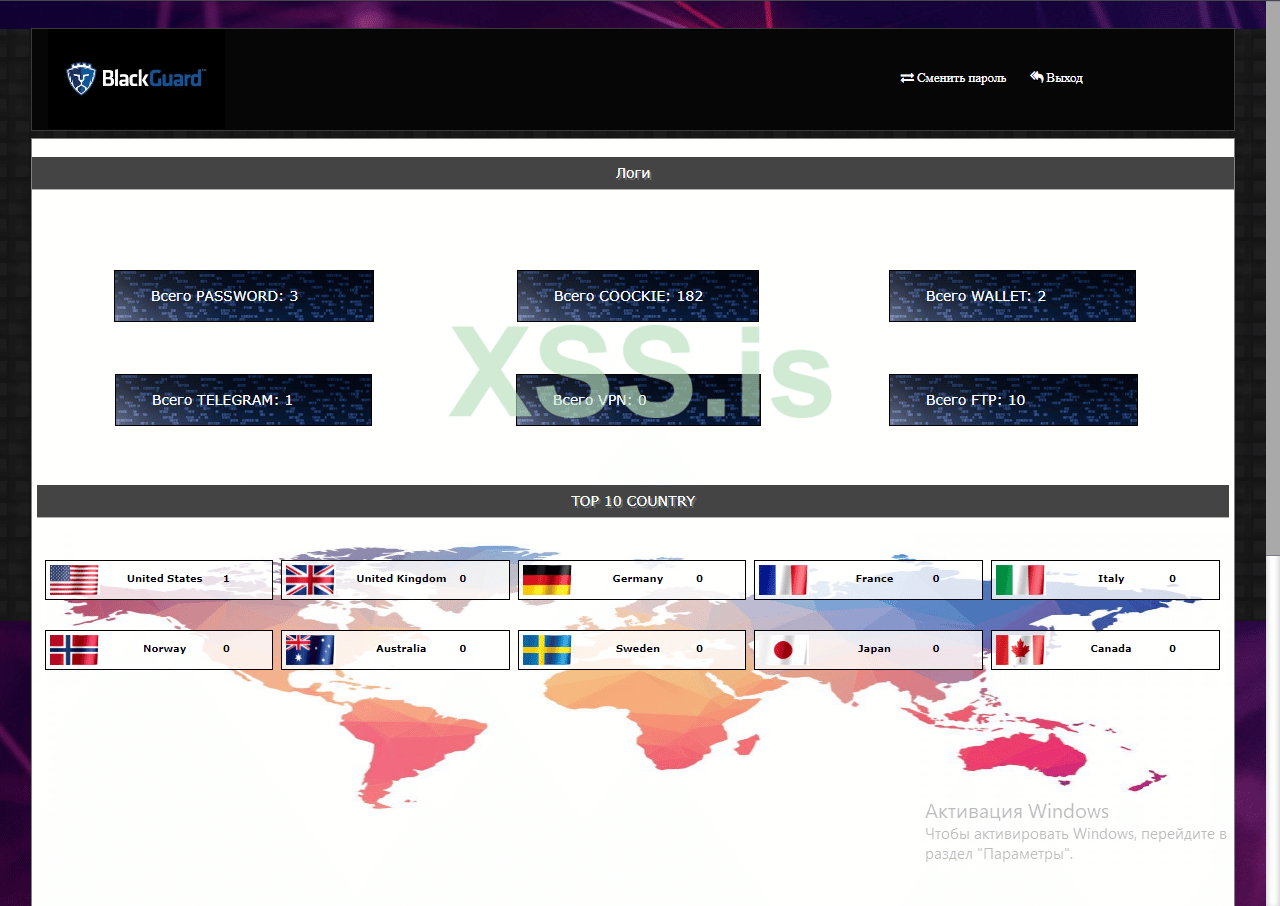
Figure 9: Blackguard web panel (source).

Become a certified reverse engineer!
Understanding the Blackguard malware
Blackguard stealer has been active since January 2022 and shared on Russian-based forums as a MaaS. As it is a malware in development, it can cause a high impact on organizations and be a mediatic stealer in the next months, such as Redline and Raccoon stealers.
Although no formula magic exists to fight this threat is specific, a group of measures can be taken to reduce the attack surface, including:
- Use a simple paper wallet for single keys or a hardware wallet for a large volume of keys.
- Prevent the usage of the same password in multiple services.
- Don’t download and execute files from unknown and not trusted websites.
- Be aware of social engineering and phishing in general.
Sources:
- Blackguard analysis, Asec
- Analysis of Blackguard stealer, ZScaler
- Rising stealer in Q1 2022, Medium
- Malware sample, Any.Run