Emotet malware returns
Emotet is a well-known word within the malware landscape and is seen as one of the most dangerous threats ever granted. After seven months away from the radar, Emotet returned in November 2021, and there was panic in the air.

Become a certified reverse engineer!
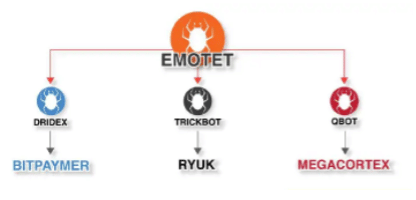
The Emotet malware returns in November 2021 after law enforcement disrupted its infrastructure in a well-coordinated operation involving several countries and agencies in January 2021. According to the CheckPoint advisory, trickbot continues on the top, affecting 5% of organizations worldwide. Still, the returned Emotet is placed in 7th position impacting mainly Education/Research, followed by Communications and Government/Military sectors. The preoccupation is high because this threat — firstly seen in 2004 — has impacted many organizations over the years, and now it is back with new power. Notice that Emotet was used as a start point to initiate the chain of devasting cyberattacks, including implanting ransomware as observed on the triple-chain attack in 2019.
Figure 1: Emotet triple-chain attack (source).
The infection chain starts as usual: phishing emails and social engineering are used to lure the victims. The fake emails contain Word, Excel or zip attachments that deploy the Emotet’s first stage on the victims’ machines, a well-known method primarily used by criminals during the last two decades to increase malware proliferation over the internet.
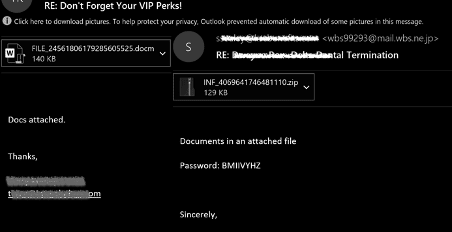
The context of the email templates contains some content related to local news or events, invoices, and fake corporate messages to trigger the victims. Malware operators have used Windows App Installer packages impersonating Adobe software in other emails. Figure 2 below presents two phishing emails of this fresh campaign involving Emotet.
Figure 2: Emotet phishing templates — November 2021.
After downloading and executing the malicious attachment, the victim “needs” to enable the execution of macros (default is disabled).
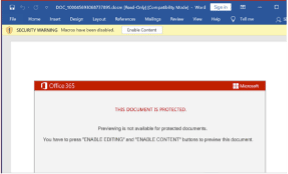
Figure 3: Emotet needs the execution of macros option enabled to continue the infection chain.
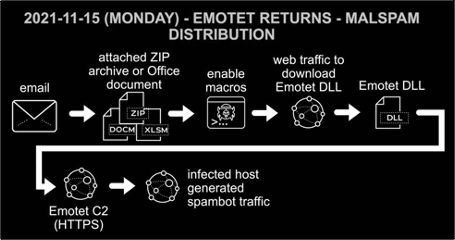
In this case, the macro code downloads a file from a web server that poses as a DLL executable to execute the next stage into the memory. Figure 4 presents a high-level diagram of the Emotet infection chain.
Figure 4: Chain of events for Emotet infection on Monday 2021-11-15 (source).
Emotet next stage
The next stage of Emotet is a CobalStrike beacon executed into the memory after running the DLL file. As observed in some scenarios, the beacon can also be executed directly from the macro code. However, using a DLL before loading the CobalStrike beacon is to perform some extra validation to evade detection.
Anti-reverse techniques
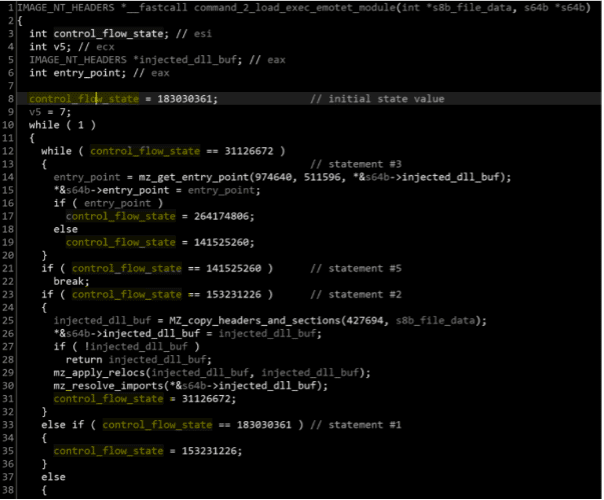
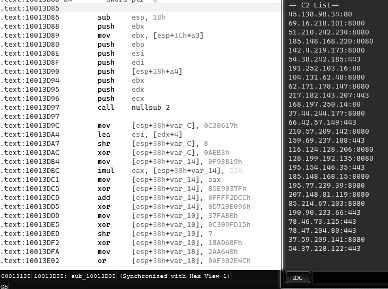
The DLL is equipped with a module of anti-revere engineering to make its analysis difficult. One of the techniques is that the control flow structure is partially removed. In the following image from Zscaler analysis, it’s possible to see a randomized variable that is used as a “control_flow_state” along with several loops, if and else conditions, or other structures to make its analysis difficult.
Figure 5: Emotet call using control flow flattening (source).
Another well-known technique used within the malware landscape and by Emotet operators is API hashing. With this in place, the name of calls are randomized, and an XOR-based algorithm is used. The strings can be decrypted in execution time (call by call) or via a static method by using the XORed algorithm (reverse operation).
The same principle is used to obfuscate the malware configuration that contains the C2 information, the CobalStrike beacon, etc. An elliptic curve Diffie Hellman (ECDH) public key is used to encrypt the communication with the C2 server. An elliptic curve digital signature algorithm (ECDSA) public key is used to verify the responses.
Figure 6: Emotet C2 list after decrypting its config.
Persistence
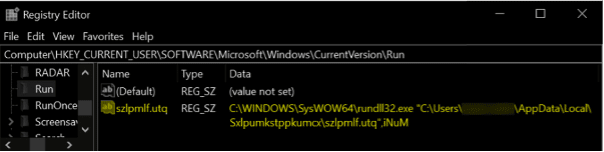
A simple method was introduced to persist the threat: a DLL file dropped into the start-up folder and loaded via Windows Registry. After executing the first time, the DLL creates a random file name and stores a copy into the C:\ProgramData path. After that, it is moved to a random directory under the AppData\Local folder. As observed below, the DLL persists via a Windows registry added during the malware execution.
Figure 7: Emotet persistence technique detected (November 2021).
Emotet commands
In detail, the Emotet commands in this release are composed by:
- Remove itself
- Sleep operation
- Process subcommand
- Update itself
- Load and execute modules
- Download and execute an EXE file (CobalStrike beacon)
- Download and inject a DLL via DllRegisterServer export, regsvr32.exe, or rundll32.exe.
The list of modules present in the Emotet samples is very similar to the previous one:
- Process listing module
- Mail PassView
- WebBrowserPassView
- Outlook stealer and email stealer
- Thunderbird stealer and email stealer
- Email reply chain spam module
- Network proxy module.
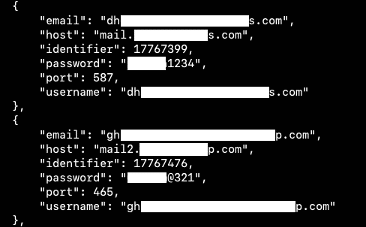
Figure 8: Credentials theft and sent to the C2 server during the Emotet execution.
The new Emotet
The first part of the Emotet infection consists of stealing credentials and disseminating itself through an email replay chain to infect other victims’ and most valuable targets. In addition, criminals deploy a CobalStrike beacon via a module present in its modules and capable of performing lateral moving on the network, accessing other points, enumerating Active Directory networks, and even deploying other threats such as ransomware.
After almost a year out from the radars, Emotet seems to be gaining power and picking up where it left off before law enforcement in January 2021.
Sources:
- CheckPoint advisory December 2021, CheckPoint
- Triple-chain attack, Segurança-Informática
- Emotet analysis, Zscaler