Fileless malware uses event logger to hide malware
Malware is on the rise and is emerging with novel techniques and sophistication that make it difficult to detect and identify in its early stages. The proof is a new piece of fileless malware analyzed by Kaspersky researchers that can take advantage of the Windows event logger utility to perform its actions.
According to researchers, this malware detected in February 2022 is “taking advantage of Windows event logs to stash chunks of shellcode for the first time in the wild.” However, some malicious actions and implants were observed in September 2021, in which the victims were lured to download .RAR files infected with Cobalt Strike and Silent Break implants.
These modules were then utilized as launchpads to implant the code into system processes and legitimate applications.
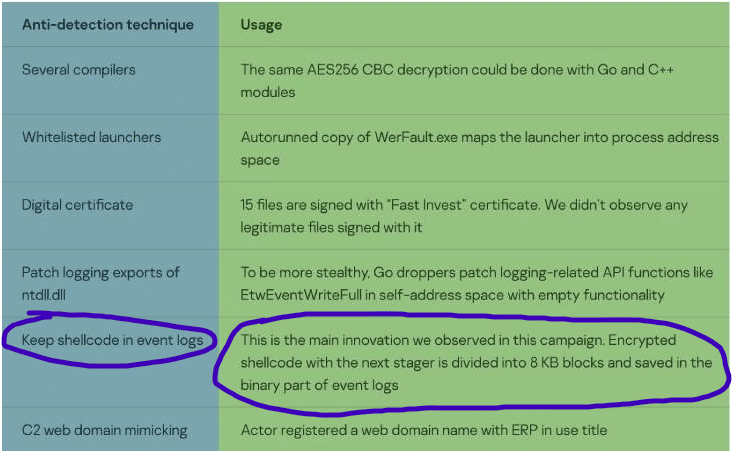
As explained by Kaspersky, it’s also notable that the use of anti-detection wrappers is part of the malicious arsenal — a clear sign the authors behind this schema can stay a long time under the radar.
Playing with the shellcode chunks
As a result of this campaign, crooks are now storing chunks of a shellcode on the Windows event logger and executing it later to hide their malware.
One of the methods highlighted above keeps encrypted shellcode that contains the next-stage malware as 8KB pieces in event logs. This is a new technique never seen before in the wild, in which all the pieces are combined and executed in a single payload.
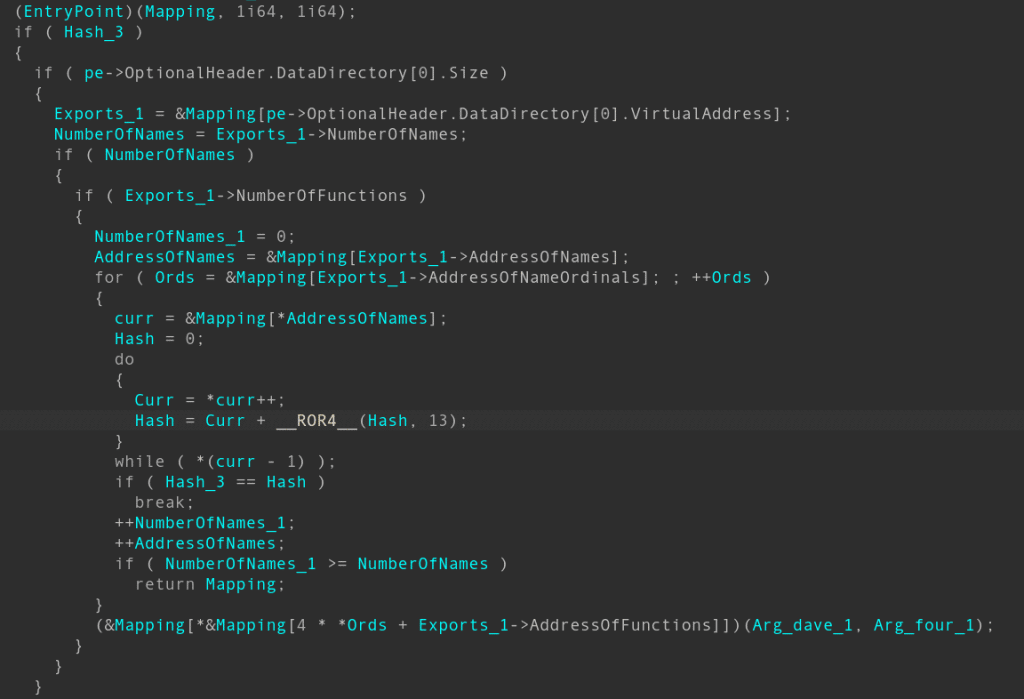
This modus operandi is uncommon and, due to its nature, can evade AV and EDR detection, maintaining its activity for a long time. Before executing the shellcode, the launcher transfers the control to the first byte of the shellcode, and three arguments need to be spotlighted:
- Address of next stage (trojan). The address is extracted from the event logs via the shellcode previously implanted.
- The standard ROR13 hash of exported function name load inside the trojan (0xE124D840)
- Addresses of the string “dave” and constant “4,” which become the arguments of the exported function, found by hash.
Trojan execution
After executing the shellcode, the trojan is launched and executed; it should be noted that two different types of communication are present:
- HTTP traffic with RC4 encryption
- Named pipes
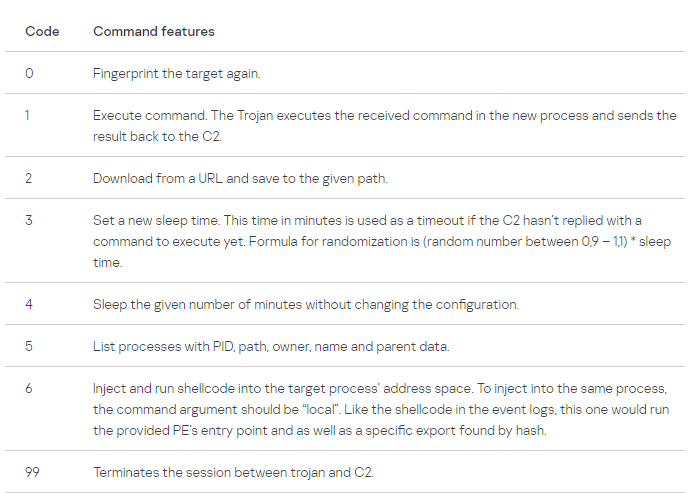
Before establishing the connection, the trojan sends an ICMP ping to check if it can connect with its C2 server using a hardcoded 32-byte long RC4 key. As observed in other strings, the key is encrypted with the Throwback XOR-based algorithm. If the connection with port 80 of the C2 server is available, then the communication starts and the following C2 commands are available:
The communication via named pipes is conducted over SSL, and the trojan communicates with the submit.php file available under port 443 of a hardcoded domain. In detail, the communication is performed via POST requests between the trojan and C2 server, over SSL with self-signed certificates, and the traffic is encrypted with an RC4 algorithm key.
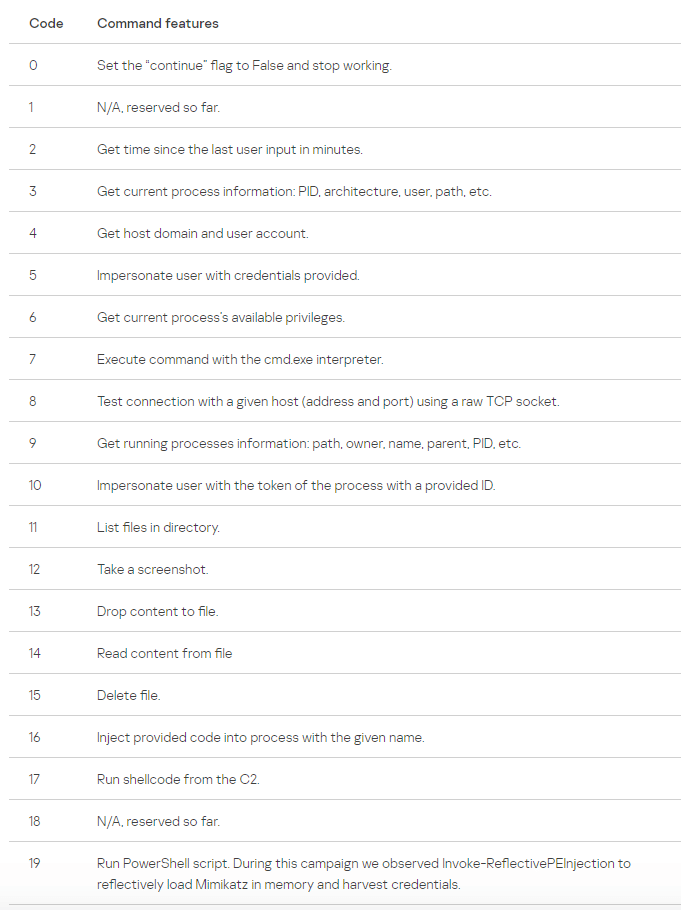
The available commands for this approach are:
Criminals can delete files, deploy additional payloads, take screenshots, escalate privileges and so on.

Become a certified reverse engineer!
Final Thoughts
Fileless malware is a modus operandi that is hard to detect and block early. This article demonstrates how the event logs technique, never seen before, can be a new way of circumventing security defenses.
Host-level monitorization should be seen as a first step in detecting and blocking threats of this nature and artifacts related to the Windows event logger. These scenarios allow persistence and evade detection, reinforcing the importance of hunting for malicious activity on the host level.
Sources:
Fileless malware, Kaspersky
Fileless malware using Event Logger, HackerNews