How the Javali trojan weaponizes Avira antivirus
Latin American trojans are on the rise, and Javali is another piece of malware that uses a legitimate binary from Avira AV to load into the memory of the malicious payload.
What is the Javali trojan?
The Javali trojan was first observed by the Kaspersky Team in November 2017 and described later in detail by Segurança-Informática. This piece of malware has increased in volume and sophistication in recent months. As noted in other threats from Latin American, Javali is using similar routines and calls also observed on other trojans, such as Grandoreiro, URSA and Lampion.

Become a certified reverse engineer!
As described by Segurança-Informática:
(...) part of these trojan families are using padding to enlarge the binary; empty sections or even BPM images attached as a resource (...). Other trojans use this technique as it allows to evade detection and execute the malicious code on the target machines bypassing detection based on static file signatures.
The researchers said that these trojans are sharing several modules and code, a clear sign of collaboration between the Latin American threat groups. [CLICK IMAGES TO ENLARGE]
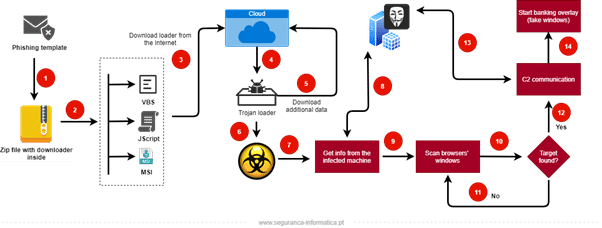
Figure 1: High-level diagram of the modus operandi of the most popular Latin American banking trojans.
Javali’s modus operandi
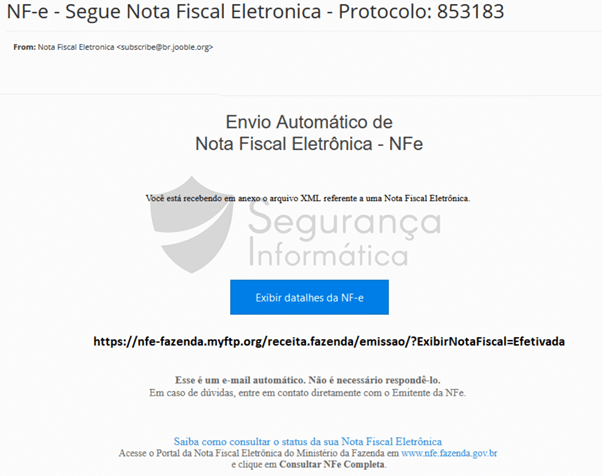
The malicious campaign associated with Javali begins with a common email sent to a large group of users under the radar of the criminal’s gang. The email template impersonates an invoice to lure the victims to open the email and then download the malicious archive.
Figure 2: Malicious template of Javali trojan banker (Portuguese language).
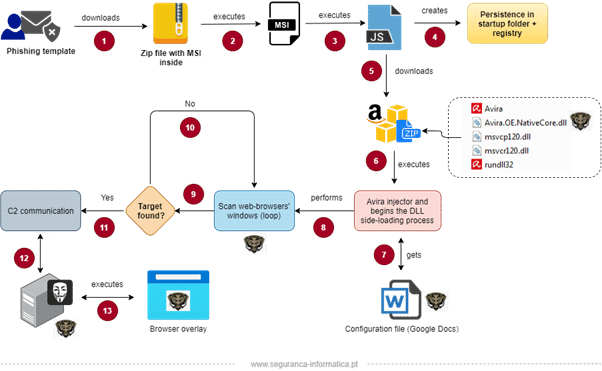
After the download of the zip archive, an MSI file is dropped with a JavaScript payload inside responsible for creating persistence and pushing the next stage from Cloud services including Google, S3 Buckets from AWS, and MediaFire file sharing service. The complete workflow of Javali trojan is presented in Figure 3.
Figure 3: High-level diagram of Javali trojan banker.
Digging into the Avira flaw
As observed above, after downloading the next stage, the trojan is executed by leveraging an Avira binary to load into the memory the final payload (the trojan itself).
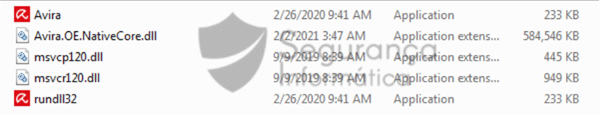
The Avira.exe file, a legitimate PE file from the Avira Antivirus firm, is then used as an injector to take advantage of a technique dubbed DLL side-loading and loading into the memory a huge DLL “Avira.OE.NativeCore.dll” (6) as a child of a legitimate Parent Process ID (PPID), Segurança-Informática said.
Figure 4: Javali trojan and all the files used during the infection chain.
In detail, the Avira.exe binary, a legitimate PE file from Avira, is used to load into the memory the spoofed DLL, Avira.OE.NativeCore.dll, by abusing vulnerabilities specifically occurring when Windows Side-by-Side (WinSxS) manifests are not explicit enough about characteristics of the DLL to be loaded.
Looking at the Windows native called LoadLibrary() and LoadLibraryEx(), if the path of the target DLL is passed, then the library is only loaded from the specific path, otherwise, the following Windows default DLL search order is used:
- The current process image file directory: the application directory.
- The system directory (e.g. system32 folder).
- The 16-bit system directory.
- The windows directory.
- The current working directory.
- The directories listed in the PATH environment variable.
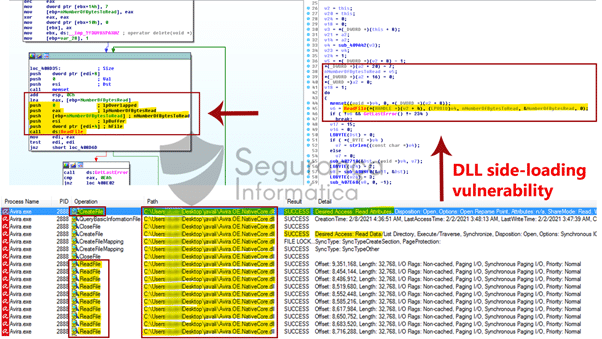
As detailed in Figure 5 below, the target DLL is loaded from the current process image file directory (option one above), and then processed via the CreateFile() and ReadFile() functions.
Figure 5: Avira.exe injector vulnerable to DLL side-loading attack abused by Javali trojan.
Javali’s capabilities
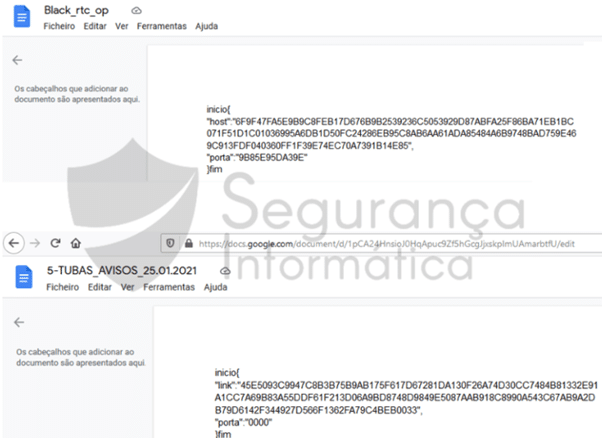
Javali trojan is a sophisticated piece of malware, and its actions are loaded from Google Docs files, including its configuration, commands to execute and the address of the C2 server. As observed, the commands are encrypted and are then decrypted in run-time using its own algorithm also shared in other Latin American pieces.
Figure 6: Javali configuration obtained from Google Docs.
After obtaining its configuration, it starts by harvesting the target machine to potentially find credentials associated with several Cloud services, email clients and so on.
Figure 7: Part of the victim’s credentials obtained from the C2 server.
At the same time, Javali trojan is monitoring the victim’s web browser and looking for specific banking portals or financial portals. When a new match happens, a new thread is executed and a fake windows overlay is presented.
Figure 8: Javali trojan windows overlay capability.
As observed in other banking trojans, Javali supports several backdoor commands. The capabilities of these commands are:
- Obtaining screenshots with the help of the Windows Magnifying API, imported from Magnification.dll
- Logging keystrokes
- Downloading and executing further payloads
- Restricting access to various banking websites
- Mouse and keyboard simulation
- Blocking the access to several Windows applications during the malware execution (such as task manager)
- Self-updating
- Stealing credentials from several email services and banking/financial portals

Become a certified reverse engineer!
Preventing Javali malware issues
Latin American trojans are a popular family of banking trojans that have made headlines in the last decade. These days there exists a large number of technologies to protect the final user, including tokens, e-tokens, 2FA/MFA mechanisms, PIN cards and more. Nonetheless, online fraud is still a real challenge every day, with criminals using new TTPs to evade antivirus and EDR systems.
There is no effective mitigation action to combat this problem. However, there are some steps to make your system as resilient as possible against malware:
- Ensure that your operating system and software are up to date.
- Use an antivirus engine and updated anti-spam software.
- Do not trust emails from untrusted sources. For this, social engineering training should be taken into account as a good way to educate employees and people in general.
- Back up data and store it outside of the network connection.
- Keep a check on bank access and login activity in your accounts regularly. Always use multi-factor authentication to prevent stolen credentials from being used to access your secrets.
Sources:
The Tetrade, Kaspersky
Javali Trojan, Segurança-Informática