Malware analysis arsenal: Top 15 tools
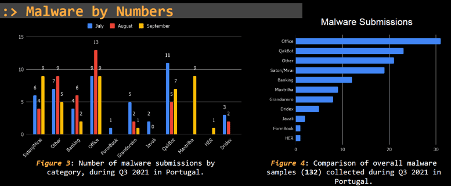
We live in an era where digital transformation is part of our lives. With this, malware has become a critical and huge threat to organizations and people around the globe that are faced every day with the most recent and sophisticated malicious schemas disseminated by well-organized cyber gangs. According to the Threat Report Q3 Portugal, many malware families were disseminated in Portugal during Q3 2021, as presented below.
Figure 1: Different malware families disseminated during Q3 2021 in Portugal (source).
The vehicle used by criminals to target victims is often the email or a simple SMS which can cost a company millions of dollars if the right controls are not in place.
Popular tools for reversing malware
Debuggers/disassemblers
IDA Pro
IDA is a multi-platform, multi-processor disassembler that interprets machine-executable code into assembly code, allowing the debugging and the reverse engineering process. IDA PRO is commercial software and the most used worldwide until Ghidra’s release in 2019 by NSA. IDA has a panoply of plugins developed by the community, and some popular pieces are VT-IDA Plugin, BinDiff and Bincat.
URL: https://hex-rays.com/ida-pro/
GHIDRA
GHIDRA is a software reverse engineering (SRE) framework created by NSA. This framework provides a suite of tools that enable experts to analyze compiled code on various platforms, including Windows, macOS and Linux. It is an open-source tool maintained by the NSA and the community on GitHub and many plugins, including VTGrep, Binwalk and Golang Renamer.
URL: https://github.com/NationalSecurityAgency/ghidra
Radare2
This is a command-line debugger that can be used on Windows and Linux. Radare2 is open-source and can be used over a GUI interface known as iaito.
URL: https://rada.re/n/
x64dbg
x64dbg is an open-source debugger for Windows for reverse engineering purposes. There are a lot of features available, and it comes with a comprehensive plugin system. More plugins can be found on the wiki page here.
URL: https://github.com/x64dbg/x64dbg
Decompilers
DotPeek
DotPeek is a standalone tool based on ReSharper’s bundled decompiler. It can decompile any .NET assembly into equivalent C# or IL code. The decompiler supports multiple formats including libraries (.dll), executables (.exe), and Windows metadata files (.winmd).
URL: https://www.jetbrains.com/decompiler/
Interactive Delphi Reconstructor (IDR)
IDR is a popular decompiler written in Delphi and executed in Windows32 environment capable of decompiling Delphi code. It is free-of-use and most used to analyze banking malware.
URL: https://github.com/crypto2011/IDR
PE Analysis
PEstudio
PEstudio is a tool used to perform Malware Initial Assessment. It’s very useful to perform an initial analysis and collects details and IoCs from a binary file.
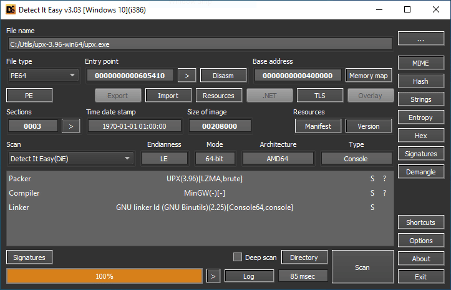
Detect IT Easy
"DIE" is a cross-platform application. Apart from the Windows version, there are also available versions for Linux and Mac OS. It is used to analyze executable files, change the binary protections, search by strings, calculate the binary entropy etc. It is a useful tool to analyze binary internals.
URL: https://github.com/horsicq/Detect-It-Easy
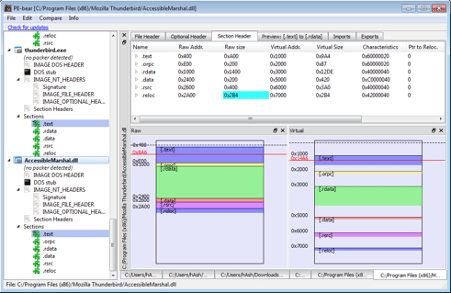
PE-bear
PE-bear is a freeware reversing tool for PE files. Its objective was to deliver a fast and flexible “first view” tool for malware analysts, stable and capable of handling malformed PE files.
URL: https://github.com/hasherezade/pe-bear-releases/
Deobfuscation
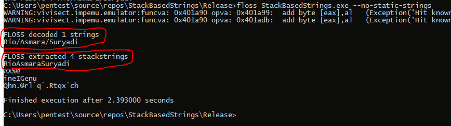
FLOSS
The FireEye Labs Obfuscated String Solver uses advanced static analysis techniques to automatically deobfuscate strings from malware binaries.
URL: https://github.com/mandiant/flare-floss
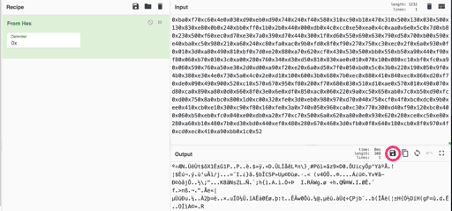
CyberChef
CyberChef is a simple and intuitive web app to perform a panoply of "cyber" operations within a web browser. It is known as the Cyber Swiss Army Knife.
URL: https://gchq.github.io/CyberChef/
Monitor
Process Monitor
It is an advanced monitoring tool for Windows programs developed by Microsoft. It shows real-time file system, Registry and process/thread activity.
URL: https://docs.microsoft.com/en-us/sysinternals/downloads/procmon
Process Explorer
This is an advanced task manager for Windows and lists the currently active processes, including the names of their owning accounts. This tool was developed and maintained by Microsoft.
URL: https://docs.microsoft.com/en-us/sysinternals/downloads/process-explorer
PE-Sieve
PE-Sieve scans a given process, recognizes and dumps a variety of potentially malicious implants such as replaced/injected PEs, shellcodes, hooks and in-memory patches.
URL: https://github.com/hasherezade/pe-sieve
Fakenet
This tool simulates a network so that malware interacting with a remote host runs, allowing the analyst to observe the malware’s network activity within a safe environment. This is my favorite tool to fake DNS responses.
URL: https://github.com/mandiant/flare-fakenet-ng
Please see here for more details about these tools and a complete list of tools used during malware analysis.
Sources
- Malware reverse tools, GitBook - Segurança-Informática
- 11 Best Malware Analysis Tools, Varonis