Malware analysis: Ragnarok ransomware
Ragnarok is recent ransomware used in targeted attacks against unpatched Citrix ADC servers vulnerable to the CVE-2019-19781 vulnerability. This article will analyze the details of this ransomware, how it works and how to prevent it.
Ragnarok ransomware background
The security firm FireEye released a report about a new ransomware called Ragnarok, which criminals use to attack internal networks after compromising Citrix ADC servers vulnerable to the CVE-2019-19781 — flaw that can be abused to execute arbitrary code.
The first stage of the ransomware is a PE file responsible for injecting into the memory a Windows DLL — the 2nd stage — packed inside the binary. The ransomware DLL itself is named cry_demo.dll, which contains the malware configuration, information regarding the encryption activities, whitelisted and target countries, and the ransom note.
Ragnarok: 1st stage analysis
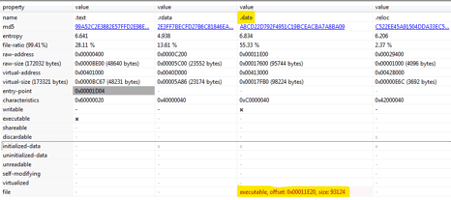
From the analysis of the binary file, we can observe that inside the .data section, there is a hardcoded PE file in the offset 0x00011E20 with the size 93124. This detail reveals that a 2nd file, a DLL, will be injected into the memory, decrypted and the execution flow transferred to it.
Figure 1: First binary reveals another file hardcoded inside the .data section.
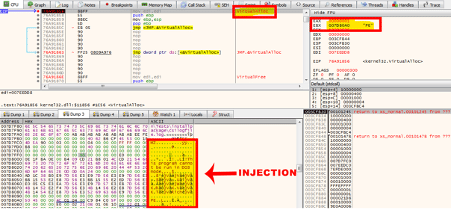
After executing the loader, the binary loads the DLL from the .data section into the memory using the HeapAlloc() call. Next, parts of the string are deobfuscated using a bitwise NOT operation, and the code is injected with the VirtualAlloc() as presented in Figure 2.
Figure 2: Hardcoded DLL injected into the memory (Ragnarok itself).
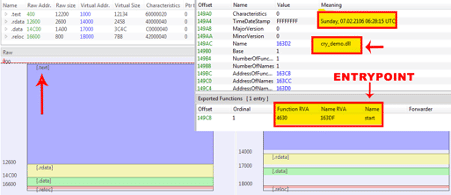
The new DLL (Ragnarok ransomware) has the original name “cry_demo.dll.” It was built with a nonsense timestamp and exports only a function: “start.” This is its entry point to start the infection chain.
Figure 3: Details about the Ragnarok DLL injected into the memory.
Ragnarok DLL
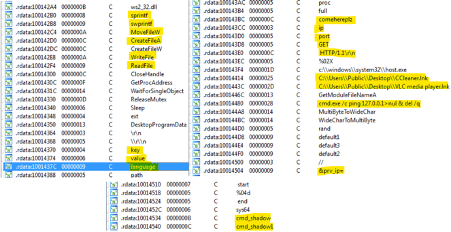
At first glance, the DLL has hardcoded some interesting strings mainly found and related to the file encryption mechanism, namely:
- sprintf() and swprintf(); and
- MoveFileW(), CreateFileA(), WriteFile() and ReadFile();
Figure 4: Strings found during the Ragnarok DLL analysis.
Other interesting strings are the “key,” “value” and “language.” As shown below, the ransomware starts by obtaining the system language to validate it is within a hardcoded allowlist provided by the ransomware developers.
The strings “ip,” “port,” “GET” and “HTTP/1.1” are clear indicators this piece of malware will send some information to its C2 during the infection chain.
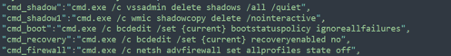
Finally, the ransomware seems to delete the shadow copies after damaging the target machine by observing the strings “cmd_shadow” and “cmd_shadow1” inside the DLL file. However, some information will still look obfuscated. The ransomware configuration is decrypted in run-time.
Digging into the details
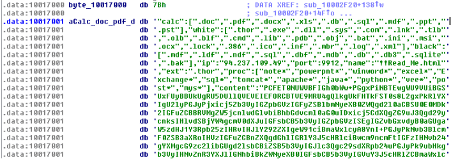
During the execution of the ransomware, the ransomware configuration is decrypted as a JSON object containing the different fields.
Figure 5: Ragnarok configuration in JSON format.
Some interesting key/values available on the JSON file are:
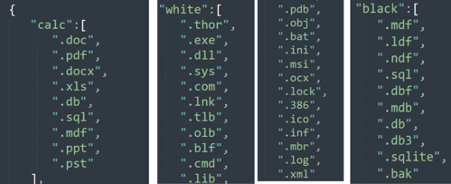
calc, white and black: target files’ extensions to encrypt and extensions to bypass during the encryption process.
Figure 6: Target and allowlisted extensions.
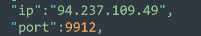
ip and port: C2 IP address and port.
Figure 6: Ragnarok IP address and port.
The ransomware sends an HTTP request to its C2 server (IP and port contained in the configuration fields). The request is composed of the hostname and private IP address fields and the “Start“ parameter, indicating the beginning of the encryption process.
name: the name of the ransomware note.
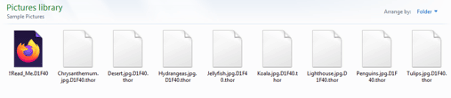
Figure 7: Encrypted files with the extension .thor.
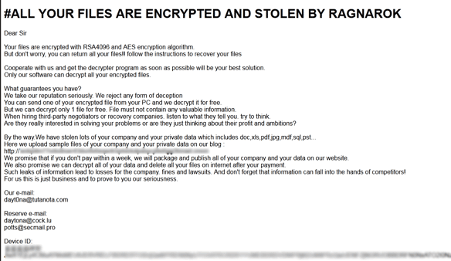
The malware encrypts the files with RSA 4096 and AES cryptographic algorithms. The file extension “.thor” is appended to the damaged files, and a new file called “!!Read_Me.html” is created into each encrypted folder. This HTML file contains the ransomware note and the other details criminals provide to convince the victims to pay to recover the original files.
Figure 8: Ransomware note of Ragnarok.
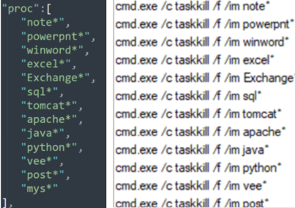
proc: processes to terminate during the ransomware execution. In detail, the proc field contains a list of processes that can lock some files, and the ransomware needs to kill those processes before starting the encryption activity.
Figure 9: Processes terminated by Ragnarok during the encryption process.
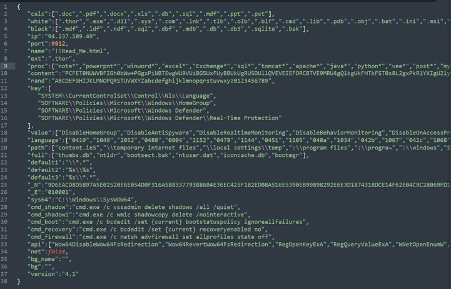
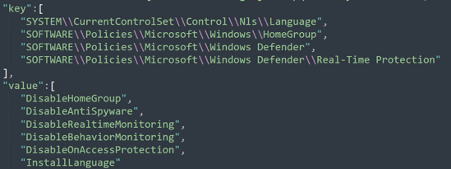
key: registry paths with processes to disable (firewall, shadow copies and so on).
The ransomware executes the operations present in the cmd_shadow, cmd_shadow1, cmd_boot, cmd_recovery and cmd_firewall fields according to the operating system architecture. For instance, the execution of the cmd_shadow command will delete the Windows shadow copies. The firewall is also disabled, and some options are added to the boot’s settings. Additionally, the ransomware also disables the Windows Defender.
Figure 10: Operations performed by Ragnarok during its execution. The shadow copies are deleted, and Windows Defender and firewall are disabled.
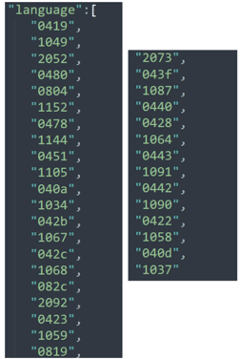
language: allowlisted countries on the ransomware configuration.
During its execution, the ransomware performs some queries to obtain additional information from the Windows registry. The ransomware terminates its execution if any of the following languages’ codes match.
Figure 11: Allowlisted language codes contained inside the ransomware config. If any language matches, the ransomware terminates its execution.
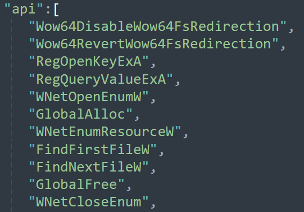
api: API hashing (the original call names).
Many Windows API calls are mapped during run-time. This is a technique used by malware developers to evade AV detection.
Figure 12: Part of the API names available on the configuration file.
At the end of the encryption process, the ransomware sends an HTTP request containing a parameter named end informing its C2 server that the encryption process has been terminated.
Final thoughts
Ransomware attacks like Ragnarok are now common. The general recommendations for prevention against them are relatively standard, namely:
- Create a security mindset and keep operating systems, software and security appliances up to date.
- Create different backup zones: offline and online.
- Be aware that email is the most used vehicle to distribute malware in the wild. Thus, email monitoring and spam engines are the first layer to block external threats, including ransomware.
- Use a VPN channel to protect internal networks, namely, exposed RDP services.
- Promote a continuous employees training program around the basics of cybersecurity.
Sources
- Nice Try: 501 (Ransomware) Not Implemented, FireEye
- Ragnarok, BleepingComputer