Mekotio banker trojan returns with new TTP
Latin American trojan bankers are on the rise, and Mekotio is one of the most challenging threats to detect and stop these days.
Nowadays, the number of emerging threats is concerning and the sophistication and agility observed in the new variants of well-known malware, including Mekotio. The new comeback brings new features and a significant change in its infection chain. This new wave was distributed some weeks after the arrest of some criminals involved with Mekotio in July 2021 by the Spanish Civil Guard. This is a clear sign that criminals moved fast to modify the malware’s Tactics, Techniques and Procedures (TTPs) to avoid detection and corroborates the strong collaboration between Spanish groups with the malware authors geo-located in Latin America.
Like other popular Brazilian trojan bankers, including Maxtrilha, Javali and Ursa, Mekotio was updated in this release to combine its capabilities with those threats, which denotes a high collaboration between criminal gangs.
Mekotio’s Modus Operandi
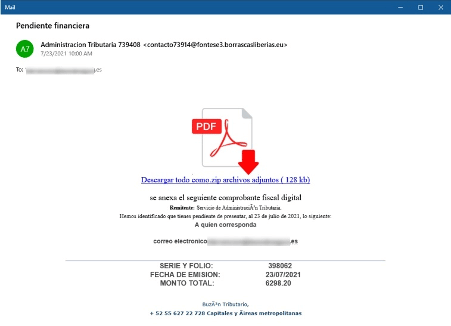
The Mekotio’s infection chain starts with a phishing template that lures the victim to download a zip file from a compromised server. Figure 1 below shows the email template in the Spanish language.
Figure 1: Mekotio email template distributed in Q3 and Q4 2021 (source).
After downloading the ZIP file, an undetectable batch file with at least two obfuscation layers is executed. The initial process is a simple cipher substitution algorithm, replacing all the symbols with a lookup table available on the script.
Figure 2: Obfuscation layer of Metkio first stage.
When the process completes, a well-known PowerShell command is executed. This IEX DownloadString command is often used during red teaming assessments to execute fileless scripts into the memory without touching on disk.
Figure 3: Powershell script executed by the Mekotio trojan.
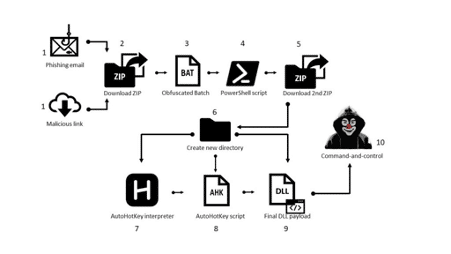
The high-level workflow of Mekotio trojan banker by Checkpoint depicting all the stages is presented below.
Figure 4: High-level diagram of Mektio malware (source).
As observed above, the PowerShell script downloads a new .ZIP file that checks if the victim is geo-located in Brazil, Chile, Mexico, Spain, and Peru and is not running inside a virtual machine. The downloaded file is composed of three additional files including:
- AutoHotKey interpreter with a customized script to perform some malicious tasks; and
- The Mekotio itself is in the form of a DLL packed with Themidas packer version 3.
This workflow is very similar to other Latin American trojan bankers, but a new update within this trojan family. The Mekotio DLL is then executed and loaded into the memory, and some tasks are performed, including:
- collecting credentials from common software
- keylogger and RAT capabilities
- banking overlay windows.
As presented below, some of the banking overlay windows are similar to the Ursa and Javali.
Figure 5: Banking overlay windows from Javali trojan (source).
Finally, the connection between the infected machines with the C2 server is performed with HTTP raw sockets using its cryptographic algorithms — the same modus operandi also observed on the most popular Latin American trojan bankers.

Become a certified reverse engineer!
Understanding Mekotio
Mekotio is a challenge trojan banker to stop and detect. With this set of new features, this malware gained the capability of evading AV and EDR detection, increasing the volume of victims around the globe. Although there is no magic formula to stop malware infections, we can follow a set of points to improve cybersecurity, namely:
- Do not open emails from unknown sources and think before opening attachments
- Be aware of social engineering attacks in general
- Install and update antivirus and protection software; and
- Make sure that different applications and accounts have distinct passwords.
Sources:
- Mekotio analysis, Checkpoint
- Javali trojan, Segurança-Informática