Modus operandi of BlackByte ransomware
We are living in an era where ransomware is a trending topic. BlackByte is a piece of ransomware that takes advantage of Proxyshell vulnerabilities to gain initial access. This article will learn about this ransomware, how it operates, describe the most important tactics, techniques and procedures (TTP), and guide on ransomware protection.
BlackByte has been a data encryption malware targeting organizations in the wild since July 2021. As mentioned by redcanary experts, the authors behind the ransomware have exploited ProxyShell vulnerabilities present on Microsoft Exchange servers to gain internal access via CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207.

Become a certified reverse engineer!
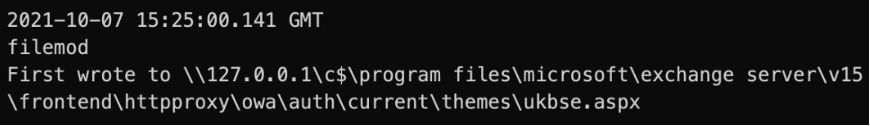
As the exploits can drop a file into a specific Operating System (OS) path, criminals use it to create a web shell ASPX to initiate the infection chain.
Figure 1: Web shell dropped into the target path via ProxyShell.
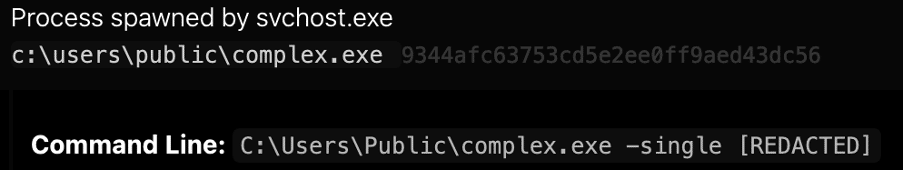
After obtaining the initial foothold, criminals drop a CobalStrike beacon in the form of a Portable Executable File (EXE) that is used to spawn the ransomware and start the encryption process.
Figure 2: CobalStrike beacon used to spawn the ransomware.
Digging into the BlackByte details
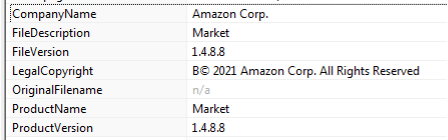
At first glance, the ransomware files impersonate Amazon Corp., as observed in Figure 3.
Figure 3: BlackByte ransomware details.
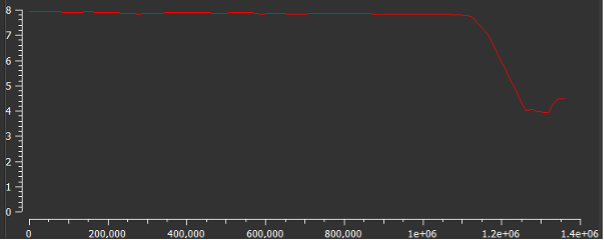
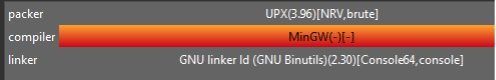
The file has a high entropy (8.0), a clear sign the file is protected with the UPX packer, as observed below. Malware creators often use this kind of approach to hide binary strings, import and export tables, Windows API calls, and so on.
Figure 4: BlackByte ransomware protected by UPX packer.
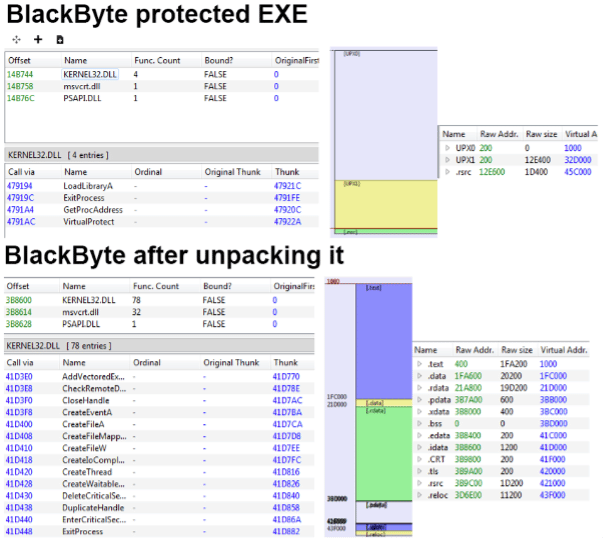
The following images present the comparison between the packed vs. unpacked BlackByte ransomware file. The protected file has only six calls on the import address table and four from the Kernel32.dll. A scenario with few calls listed on the IAT indicates that a packer was used to obfuscate data.
On the other hand, after unpacking it, 111 API calls and 12 binary sections were listed, allowing us a precise static and dynamic analysis of the ransomware file from this point.
Figure 5: Packed vs. unpacked BlackByte ransomware sample.
After executing the ransomware file in memory, some validations are performed. If the language of the target system is the same as the hardcoded codes, then the ransomware terminates its operation. The complete list is presented below.
Figure 6: BlackByte hardcoded languages; when a match happens, the ransomware terminates.
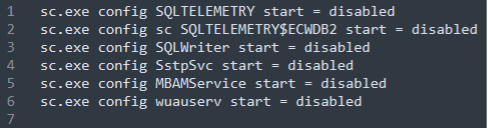
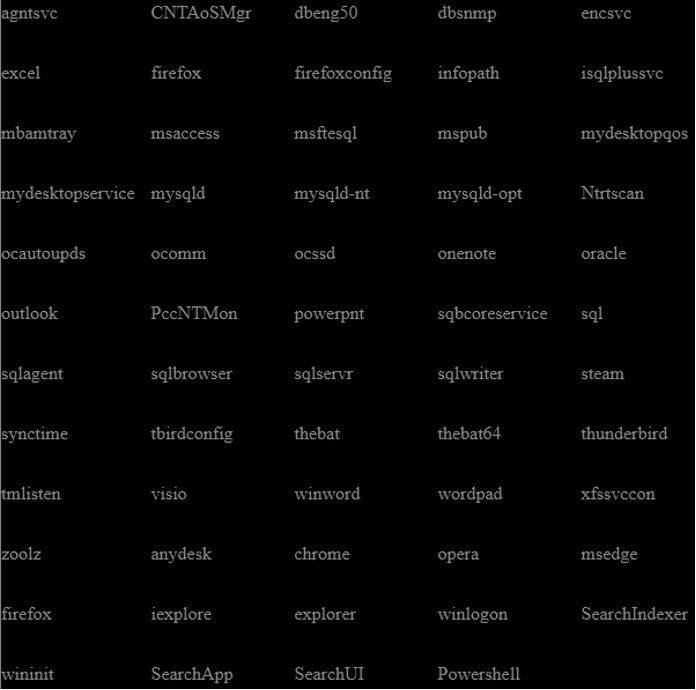
As observed on other threats of this nature, BlackByte ransomware disables some services and stops target processes before starting the encryption process. This is a well-known TTP used by criminals to avoid errors during the ransomware operation, as opened files or processes cannot be encrypted and accessed by other programs in run-time.
The list of disabled services and all the hardcoded processes to terminate can be found below.
Figure 7: List of disabled services.
Figure 8: List of all the processes terminated during the BlackByte ransomware execution.
BlackByte tries to escalate privileges on the internal network by using three different steps, namely:
- By elevating local privileges on the registry
- Enabling the setting to share network connections between different privilege levels; and
- Setting up long path values for file paths, names, and namespaces ensures that all file names are encrypted without errors.
In addition, BlackByte executes network reconnaissance, including queries to the Active Directory for all of the collected computer hostnames.
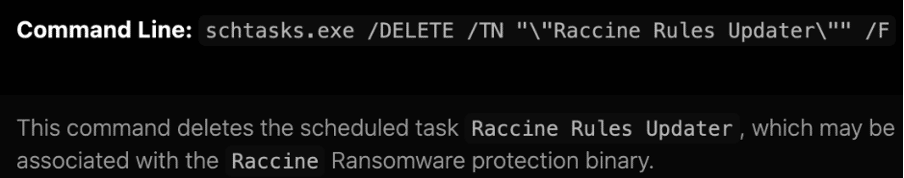
The "Raccine Rules Updater" point
An interesting behavior observed during the ransomware execution is creating a new thread responsible for deleting the scheduled task "Raccine Rules Updater" and disabling the SQLTelemetry service. Raccine is a ransomware vaccine created by Florian Roth and capable of intercepting and preventing precursors and active ransomware behavior.
Figure 9: BackByte tries to remove the Raccine task during its execution.
The encryption process
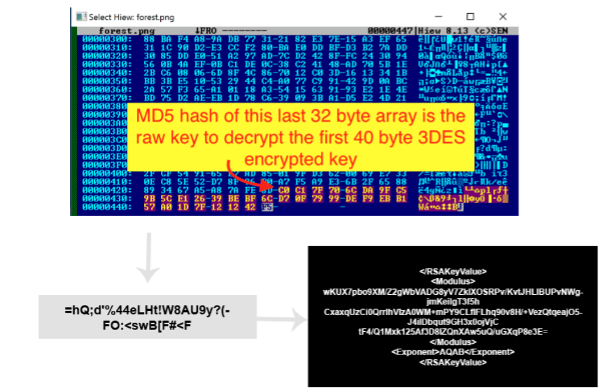
According to the Trustwave research, seconds before the encryption process starts, BlackByte tries to download a .png file from a hardcoded domain that contains an AES key to be used as the encryption key. If the connection fails, the ransomware process crashes.
Figure 10: AES key (symmetric key) used during the encryption process.
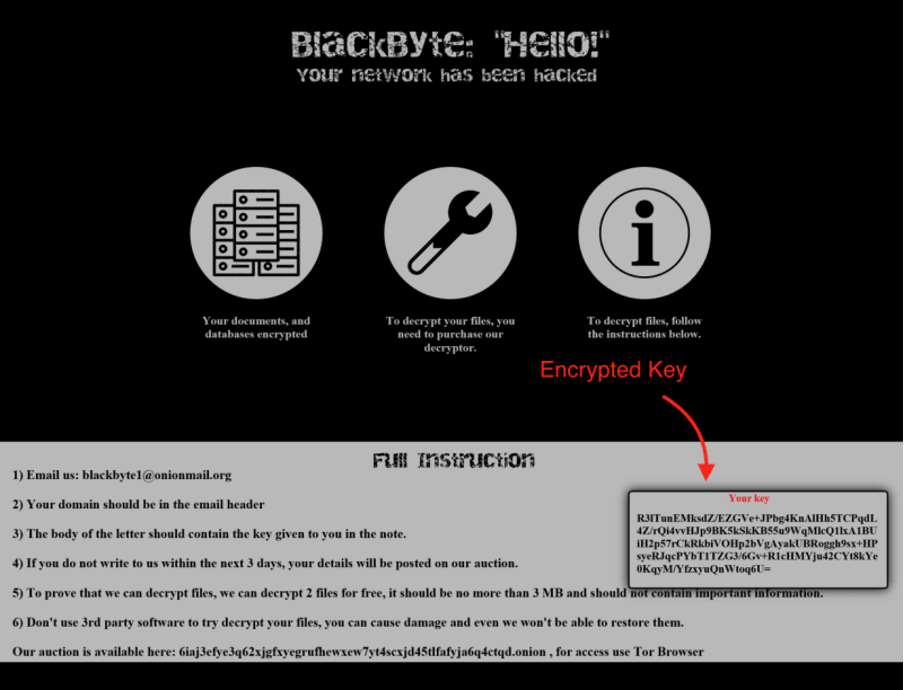
The ransom note is created during the encryption process containing instructions on how to contact criminals. The file is an HTA file called "BlackByte_restoremyfiles.hta" as observed below.
Figure 11: BlackByte ransomware note file with all the instructions.
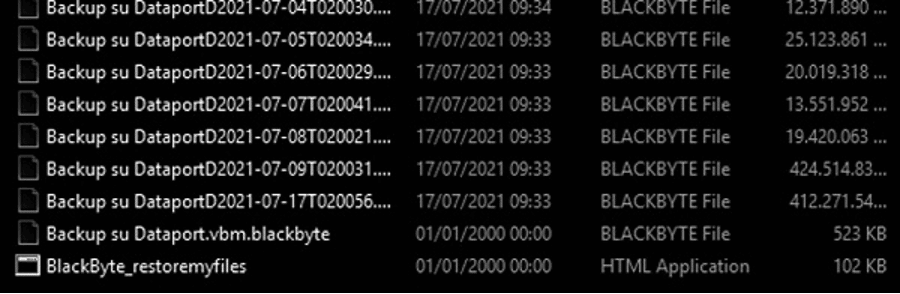
All the damaged files have the" .blackbyte" extension associated. For instance, the file "a.txt" is renamed to "a.txt.blackbyte" and so on.
Figure 12: Example of damaged files after running the BlackByte ransomware.
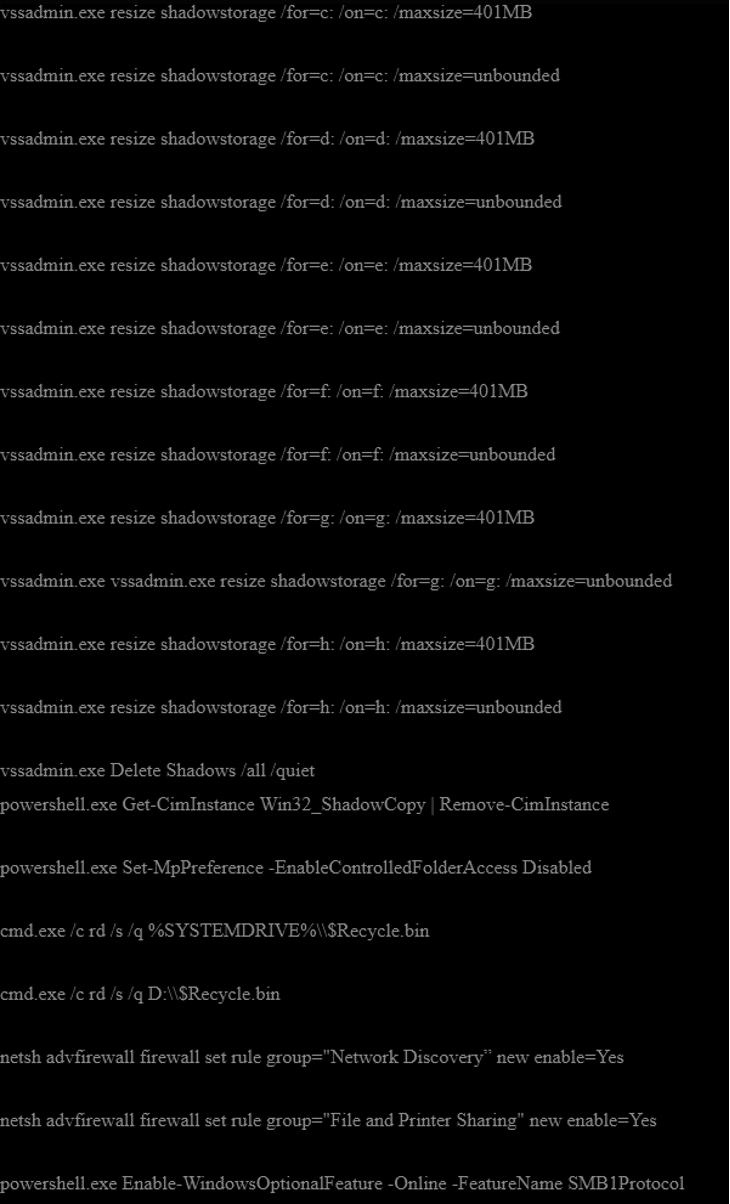
Finally, BackByte executes living-off-the-land commands to delete all the shadow copies, Windows restore points, disable network discovery, change permissions on files and delete the recycle bin folder. The complete list of commands can be found below.
Figure 13: List of commands executed by BlackByte during its execution.
BlackByte ransomware
Ransomware is an emerging threat that has increased in volume and sophistication in recent years. BlackByte is one of the active data encryption malware types operated by criminals in the wild, and that is using known vulnerabilities to gain initial access and impact organizations worldwide.
Although there is no magic way to stop ransomware in general, sometimes the malware authors introduce some weaknesses during the development of their software which can be used to minimize the impact of a cyberattack by security specialists.
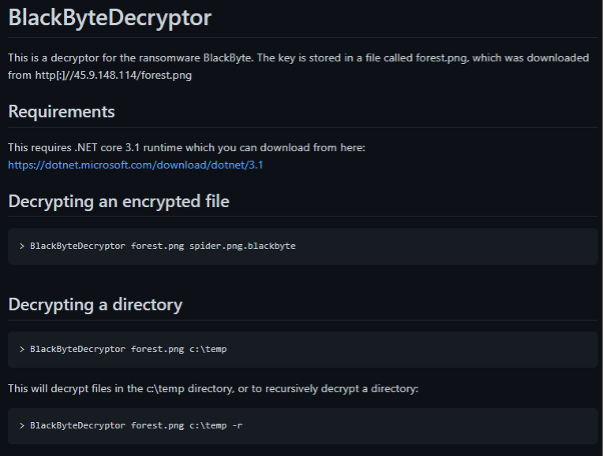
Within the context of the BlackByte ransomware, the experts from Trustwave explained the downloaded png with the AES encryption key is used in both the encryption and decryption process (see Figure 10). As the same file was used to compromise different organizations worldwide, Trustwave uses that key to create a decryptor that can recover the victim's files for free.
Source: https://github.com/SpiderLabs/BlackByteDecryptor
The command lines on how to use the decryption can be found on the GitHub page, and now, all the affected victims can recover their files without paying the ransom.
Sources:
- Ransomware analysis, RedCanary
- Blackbyte TTPs, Trustwave