Redline stealer malware: Full analysis
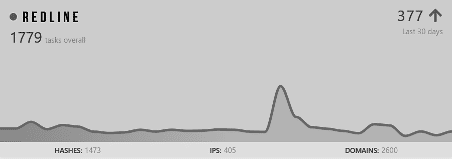
Redline malware was first observed in March 2020, but it continues to be the most prominent cyber threat impacting users worldwide in 2021. According to the AnyRun trend tracker, 1,473 samples were submitted onto the online sandbox in September 2021, an increase of 377 samples in contrast to August, with a total of 2,600 domains and 405 unique IP addresses.
Figure 1: Total of samples Redline malware in September 2021 (source).
Redline is a piece of malware that has been updated during the last few months, with features for credentials exfiltration and cryptocurrency wallets, browser information and FTP authentication data. It also collects information about the infected machine, such as OS information, system hardware, processes, system language and more. Capabilities to load remote payloads and a SOAP protocol for C2 communication were also implemented — a clear sign this malicious piece should be put under the cyber radar.
Modus Operandi of Redline malware
This info stealer operates on a MaaS (malware-as-a-service) model and is distributed on underground forums according to the users’ needs; $150 lite version; $200 pro version; $100/month subscription option. In the Telegram channel, the malware can be acquired and paid in Bitcoin, Ethereum, XMR, LTC and USDT.
Figure 2: Redline official Telegram channel.
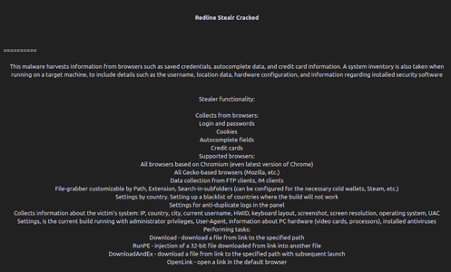
Figure 3 below shows the features of Redline shared by criminals in a specific forum where it is distributed in the wild by its authors.
Figure 3: Detailed features of Redline malware.
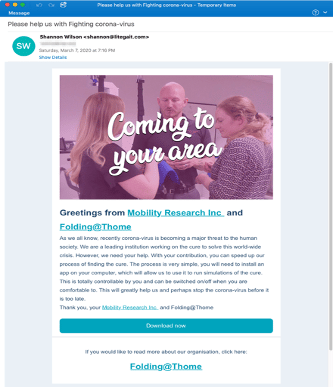
The vehicle used by criminals to disseminate the Redline stealer is the email. A malicious and convincing message is sent along with an URL responsible for downloading the binary file installed on the target machine. Healthcare (taking advantage of the COVID-19 situation) and manufacturing were two industry sectors affected by this threat in the last few months.
Figure 4: Email template of the Redline malware related to the COVID-19 pandemic situation.
Redline C2 server
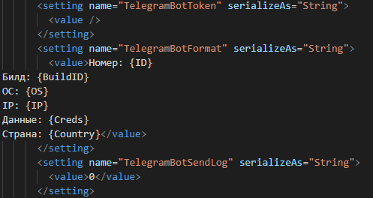
This malware is written in C# and uses a SOAP API to establish communication with its C2 server. As observed on the clandestine Horus Eyes RAT, this stealer takes advantage of the powerful features of the Telegram API to notify criminals about new infections in an easy way. Some details about this mechanism can be seen below.
Figure 5: Redline Telegram bot configuration.
After receiving a ping via a Telegram channel, criminals can interact with the Redline agent installed on the victim’s device using the C2 panel installed on a Windows machine. The command and control server is also written in C# and its communication is based on a WSDL with a SOAP API to interact with the malicious agents.
As observed below, the C2 panel includes several features, including:
- Displaying information from the infected machine
- Exporting and commenting details
- Searching mechanism
- Creating and downloading remote files
- Running tasks such as password exfiltration, FTP data, Browser details including passwords and so on.
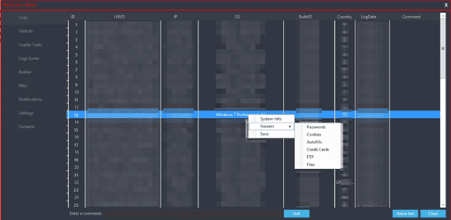
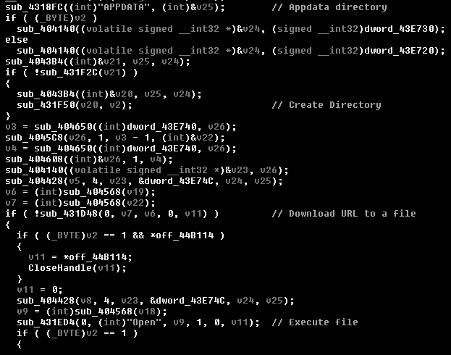
In addition, the C2 panel can execute additional payloads on the agents-side and even open specific URLs on the default web browser. Figure 6 shows some details about the Redline C2 panel with sensitive data redacted and the code block responsible for executing extra payloads.
Figure 6: Details about the Redline C2 panel and block of code responsible for executing additional payloads.
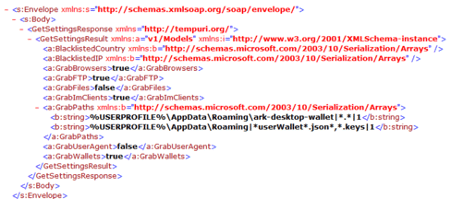
Although this malware is equipped with a lot of modern features also observed on stealers of this nature, Redline doesn’t use cryptography to create a secure channel when it communicates with the C2 server, and all the packets and data can be easily identified on the network layer by security appliances by creating customized rules to detect it.
Figure 7: SOAP envelope of Redline malware when a specific task is started (password stealer module).

Become a certified reverse engineer!
Understanding Redline malware
Redline malware is a recent malware written in C# with notable growth in 2021 and disseminated using templates related to the COVID-19 pandemic. It includes modules of stealing credentials and collecting information from the infected machine and the capability to download remote files and execute additional payloads, including other malware.
In general, users should be trained against threats of this nature and focus on the social engineering schemas that proliferate via email. The email continues to be the most used vehicle for distributing malicious campaigns in the wild, especially messages with hardcoded URLs or files attached that can lead to the deployment of malicious payloads.
Let’s take malware protection seriously and stop from scratch the dissemination of these kinds of threats with practical awareness training.
Sources
- New Redline Password Stealer Malware, Proofpoint
- Redline Stealer, CyberInt
- Redline Trend, AnyRun
- HER analysis, Segurança-Informática