SockDetour: the backdoor impacting U.S. defense contractors
SockDetour is a new backdoor identified by the Unit42 research team and found on U.S. defense contractors’ networks as a backup backdoor to maintain persistence and access.
SockDetour is a customized backdoor acting as a backup backdoor if the main one is removed from the target systems. The analysis by the Unit42 research team shows this piece of malware is hard to detect as it operates based on a fileless and socketless mode. This backdoor was first identified in the TiltedTemple campaign and used with other tools, including memory dump utilities and various web shells.
According to telemetry data from the collected samples, “we believe the threat actor behind SockDetour has been focused on targeting U.S.-based defense contractors,” says Unit 42’s analysts.
How SockDetour works
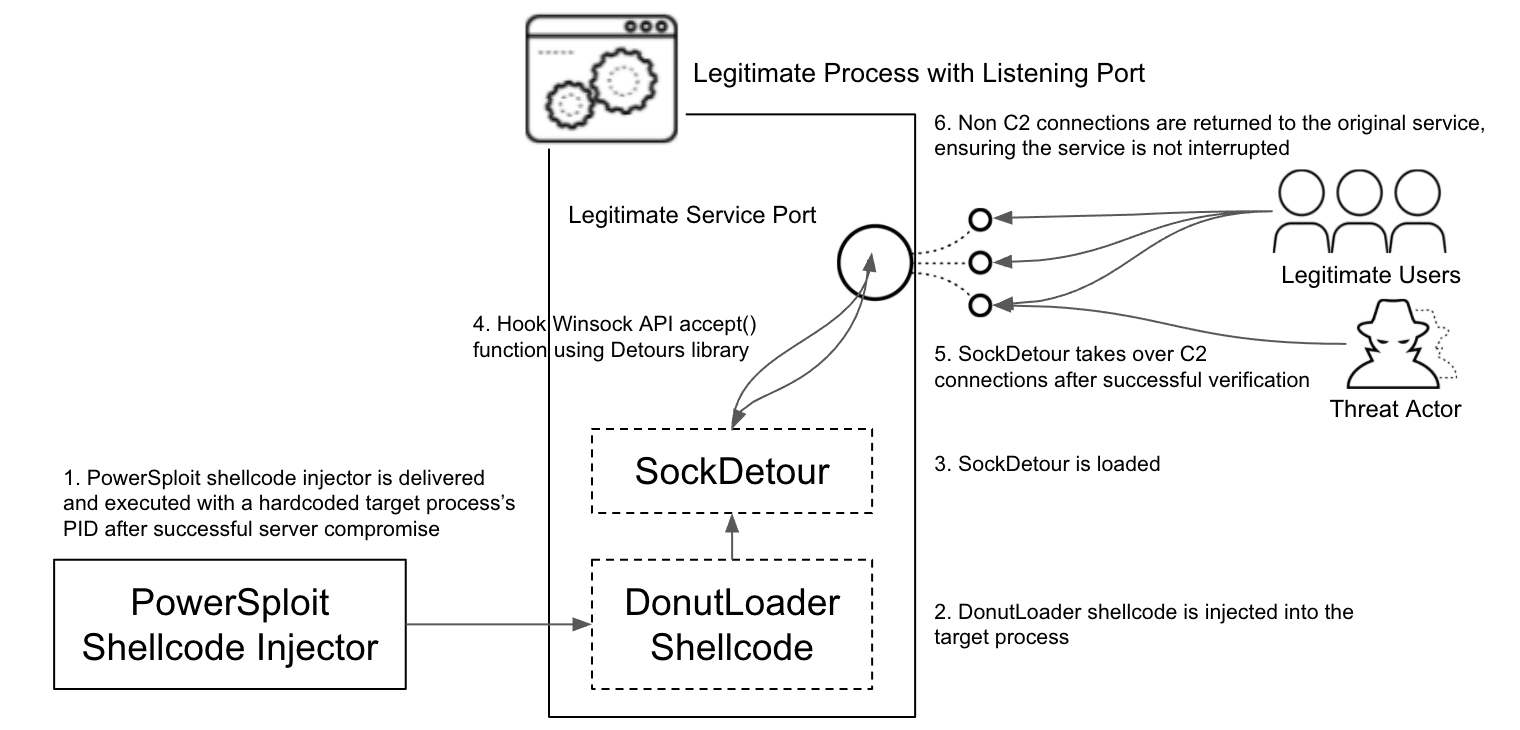
SockDetour is a simple 64bits binary file that does not require a listening port with its C2 server to communicate. Instead, it hijacks an existing socket, but before it needs to be injected into the memory via a fileless mode.
To achieve this step, criminals used the Donut framework to generate a shellcode of this binary and inject it into the memory by utilizing the PowerSploit memory injection utility. In detail, hardcoded processes’ IDs were found by security experts during the backdoor analysis, a clear sign that criminals choose in advance the target processes to use along with the shellcode.
After executing in memory, the Microsoft Detours library is leveraged to hijack network sockets, making it hard to detect. By using the DetourAttach() WinCall, a hook is attached to the Winsock accept(), which allows the creation of a malicious proxy to intercept communications.
According to security experts, “with such implementation, SockDetour can operate filelessly and socketlessly in compromised Windows servers and serve as a backup backdoor if the primary backdoor is detected and removed by defenders.”
Figure 1: SockDetour backdoor high-level workflow (source).
As the backdoor is hijacking a legitimate service, it needs to implement a way of grouping legitimate traffic from its C2 server. In detail, it uses eight steps to filter the received packets and validate if it comes from its C2.
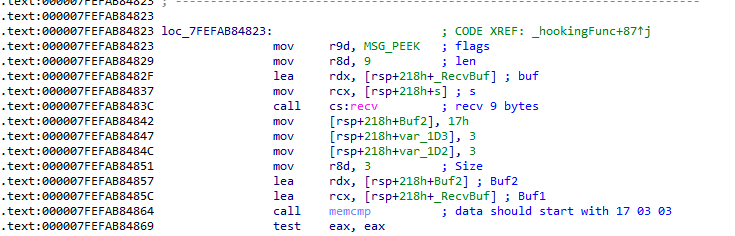
The data is received via recv() call with the MSG_PEEK function that will not interfere with the legitimate traffic. This is crucial to not cause any disruption to the service and remain stealthy over a long time.
Figure 2: SockDetour receives data with the MSG_PEEK option and verifies the data (source).
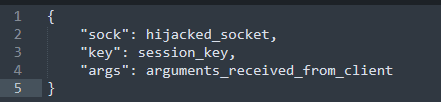
Regarding the features provided by this backdoor, only one is available: DLL plugin loading. The payload is received via the hijacked socket from its C2 server and is expected to be smaller or equal to 5 MB. After that, the payload is decoded and injected into the memory, taking advantage of the TreadProc export function and executed based on a JSON structure presented below.
Figure 3: JSON structure used to load the target DLL.
According to Unit42 analysis, “while plugin DLL samples were not discovered, the above function argument suggests that the plugin also likely communicates via the hijacked socket and encrypts the transaction using the session key.”

Become a certified reverse engineer!
A summary of SockDetour
SockDetour is a kind of backdoor created to bypass detection and remains hidden for a long time. The main purpose of this malware is to maintain access, acting as a backup backdoor if the primary one fails. As it uses a fileless and socketless approach, detecting it on the compromised machine and its communication is really hard.
The usage of host-based monitoring solutions and updated AV/EDR are the best measure to keep away threats of this nature as the vendors are updating their databases continually.
Sources:
- SockDetour analysis, Unit 42