Taidoor malware: what it is, how it works and how to prevent it | malware spotlight
Taidoor is the name of the last persistent threat analyzed and described by Reversing Labs team, and we’ll be using some of their research in this article. Traidoor has been linked to the Chinese government, and the last versions are being used along with proxy servers to create persistence on the target networks and be used on further activities. Like other malicious tools, this piece of malware needs to be stealthy to maintain its activity for large months and even years.
The new updates of this version of Taidoor RAT are composed of two principal parts:
- An initial loader in a DLL form
- The RAT main module comes as RCE-encrypted binary data.
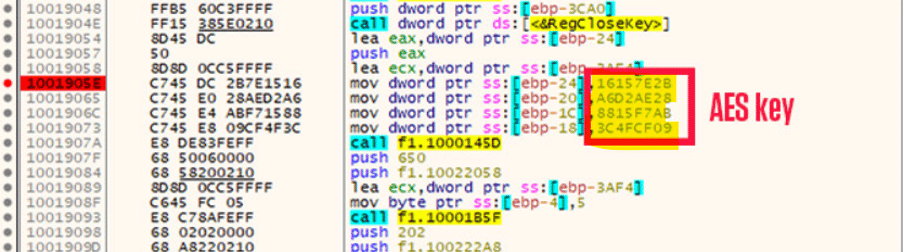
In detail, the Taidoor loader starts by decrypting the encrypted main module and executes the “Start” call present on the DLL Export Address Table (EAT).
Figure 1: Exported functions present on the EAT of Taidoor RAT.
Put the pieces together
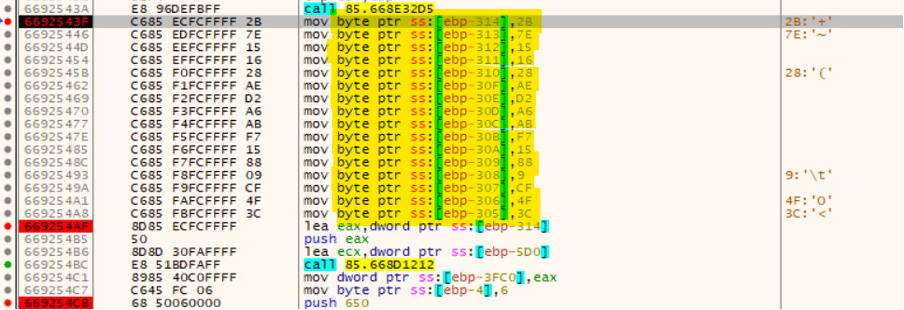
By analyzing some samples of this threat, it’s possible to learn they are using the same AES key (16157E2BA6D2AE288815F7AB3C4FCF09). Nonetheless, there is an additional encryption layer in place developed by crooks responsible for configuration decryption - AES key and S-Box initialization.
Figure 2: AES key hardcoded inside the malicious DLL.
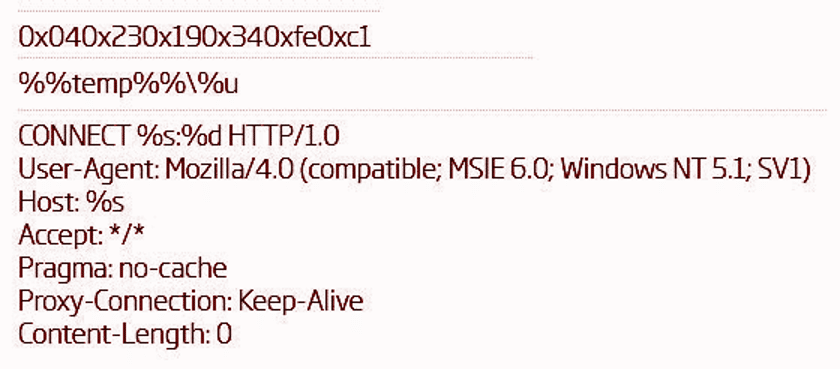
The next decryption process is then used to reveal the encrypted data inside the binary, including strings related to HTTP activity, C2 config, and other details about the Taidoor configuration.
Figure 3: Loading of AES decryption key after the first decryption process.
The symmetric AES key makes it possible to get the original strings hardcoded inside the malicious binary and the PDB path, as presented below.
During the analysis of different malware samples, two different PDB paths were found, namely:
These PDB paths are crucial to understanding that the samples were created in 2016 and 2017 and that this piece of malware is active for a decade without being detected by AV and EDR security solutions.
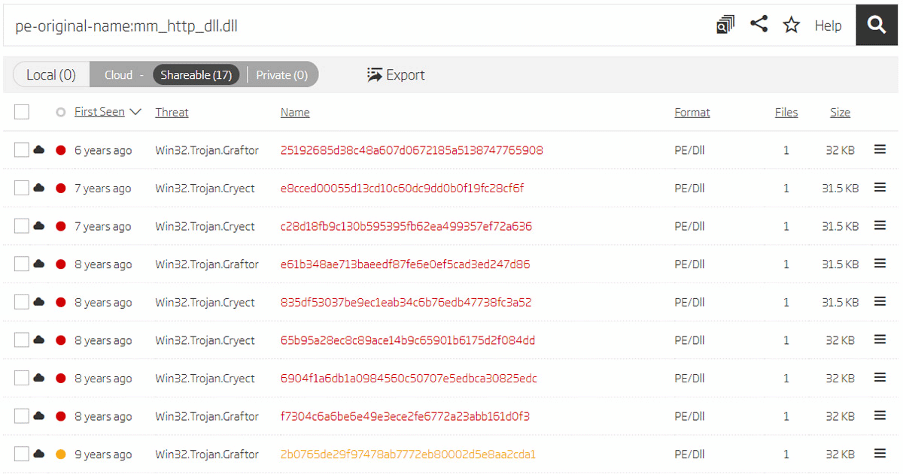
As mentioned by Reversing Labs here, the found RC4 symmetric key had been used by several samples of Taidoor RAT for several years (first seen nine years ago at least).
“A search query indeed finds 17 samples with this name, and analyzing them in disassembler shows they also have the configuration encrypted with the same “0xA1 0xA2” RC4 key.”
Figure 4: Samples of Taidoor undetected for a decade.
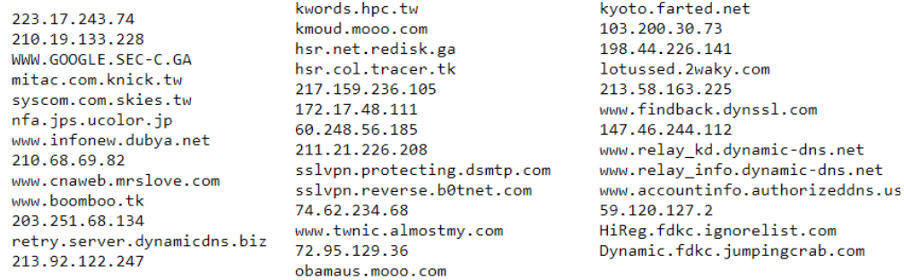
The C2 config was also extracted from several samples that remained undetectable and their remote servers available on the internet. Next, the list of the C2 used by Taidoor for several years in its malicious operations.
Figure 5: C2 list used by Taidoor RAT.

Become a certified reverse engineer!
Taidoor's threat
Nowadays, different kinds of attacks and threats have emerged in volume and sophistication. Taidoor is one of the malicious tools that remained undetectable for a decade, avoiding detection from security solutions such as antivirus, EDR systems, network-based firewalls and SIEMs.
It’s notorious that Taidoor’s creators had something specific in mind: maintain the malware activity stealthy and FUD (fully-undetectable). In this sense, it’s crucial to apply the proper steps to mitigate infections of this nature. Below, we are going to provide some recommendations to fight, in general, threats to this line, namely:
- Use monitoring software: monitor new and existing types of malware using an antivirus or EDR system. With these kinds of software, you can prevent, defend and mitigate threats of this nature in advance.
- Keep operating systems and software updated: this is the key to success. It’s crucial to keep operating systems and other software with the latest patches applied to mitigate flaws that can be abused by threats, in general, to fully compromise assets.
- Create a cybersecurity mindset: remind users about the origin of the emails, links, attachments and more. All sources should be verified. Remember that phishing is still the most used vehicle to distribute malware over the internet.
- Enforce password policy: your old friend. Employ a firm password policy and ensure passwords are updated frequently.
Sources
Taidoor analysis, Reversing Labs
Taidoor IoCs, US-CERT