Ursnif Malware
These days, along with the unforeseen climatic conditions, several unpredictable malware campaigns are also occurring across the connected world. Mostly Offenders are relying on spam email and associated malicious macros, to drop and infect the targeted victims with other atrocious malware.
Studies show 95% of successful security attacks are created by Human mistakes!

Become a certified reverse engineer!
Security sensitive entities are hardening the controls to their maximum to escape from these types of campaigns or infections. On the other hand, malware authors are taking a lot of inventive steps to evade these, so-called 'hardened security controls.'
That said, let's jump into a very latest Document malware, which evades all the security controls to infect the targeted machines with Ursnif Spyware.
Do you want a brief before kicking off? There you go.
Three spam emails were spotted spreading, each carrying Microsoft document files (.docx) which were password protected. The mail body contained the passwords to open the protected documents. The three document files did not contain any Macro codes (obviously, .docx files may not be), but the body of the Documents contained three OLE Objects embedded in it with icons mimicking word document files. These embedded objects were unique malicious VBScripts, which acts as a malware dropper. Once the user double clicks any of the Ole VBScript objects, the malicious code will drop an atrocious spyware, which is a new variant of Ursnif.
One of the three spam emails is shown in the below:
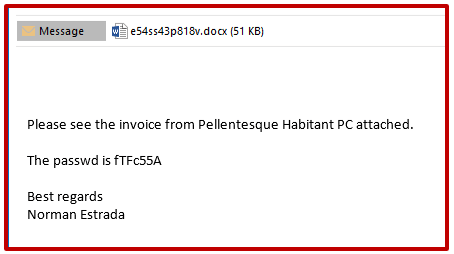
Once the document is opened, a password prompt will pop up before the Document is fully opened. This is a prominent tactic for evading any automated sandboxing technologies, as human intervention is needed to perform the password entry, which is listed in the body of the email.
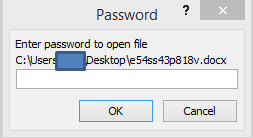
There you go Sandbox! You cannot go beyond this. Bad boy expects human sense, not yours!! ;)
Shall we create a tool to trace the password in the body of the email and feed to password popup while in the sandbox? ;) Please leave a comment if it is out there :)
When the password is entered, the document will open and then shows three embedded OLE objects, which imitates three Document files (only Word Icon and name). However, the truth is that all the three objects are unique malicious VBScript.

It is important to find the architecture and working of this embedded VBScript to identify important IOCs. As we discussed earlier, all the VBScripts were similar and hence safely copied this standalone Script and started debugging. The codes were not fully obfuscated but heavily used random variable names to confuse static analysis and heuristics detections

Immediately when the script is executed, the VBScript will be executed by copying itself to the %temp folder.

My dear Sandbox did you managed to reach this extent. Now the timer ticks, 250 seconds. You failed!
Then the script will call a command shell to start PING to 8.8.8.8, 250 times redirected to nul. The idea is to sleep for 250 seconds before it starts next arguments. This is another technique used by malware to evade the automated malware analysis using Sandboxes.

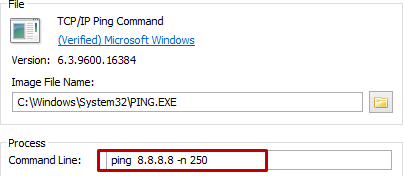

For malware to trigger its command and control communication, we have to wait for 250 PING wait. Luckily if we try to terminate the whole PING process tree manually, immediately the Malware tries to communicate with its Command and control IP address to download a file. ;)
From the below debug code, we can suspect that the code is trying to download a file "img.jpt" from a remote IP address and checks for the HTTP status code successful connection or not (200 OK)

As we suspected, the moment we terminate the PING process the code will be communicating to remote IP addresses to download the files.

All the dynamic analysis is done by emulating the required resources for the malware.
Another Remote IP communication to download a file (for another sample)

Since we are emulating the network communication for malware, it failed to get the actual file and next tries to communicate to another domain to download the same file but with different name and extension: "tmp.pkg" (encrypted file)

Same for another sample:

What happens if both fail?
If both the communication is a failure, the malware itself will drop an encrypted file with ".QdE" (Xorcrypt), extension at: C:Users{username}AppDataRoaming.
Then the malicious macro, on the fly, will decrypt the dropped file into a PE file (executable) in the same destination folder with a ".VIv" extension. The names of these files will be randomly generated (numbers).


Once the executable file is dropped successfully, the wscript shell will then invoke the command line for executing the PE file.


Here ends the role of the Documents, which users received via spam email. Next, the threat will advance to the dropped malware.
Dropped Executable - Ursnif Spyware
Further analysis confirmed that the file which dropped by the document is an infamous atrocious "Ursnif Malware."
- The {randomnumber}.Vlv malware once executed will copy itself as "adprtext.exe" at "C:Users{username}AppDataRoamingMICROS~1adprtext.exe" and executes from there.
- The malware will seek persistence by adding the above path to Path: "HKCUSOFTWAREMICROSOFTWINDOWSCURRENTVERSIONRUN"
- Then the spyware will do its spying activity like keylogging, credential harvesting etc. and would start exfiltration to remote command and control servers
- The sample POST (exfiltration traffic) compromised traffic:

This time providing full IOCs, Prevention is better than a cure! :)
Indicators of Compromise
Spam Mail Sender
nathalie.trepanier@cgocable.ca
amccarron@miracosta.edu
File Hashes - Documents
MD5: 7B9D6ED35A03810AB9FA4389AAA0BC7D
MD5: 505E5ABE91B5214D11DEE94E0069A6CD
MD5: 812129572DAD1887C5C3E4A4B3C8A938
Two variants of VBscript embedded inside the word document
MD5: 6515B987026A1D68DD5C95269F1F7D6A
MD5: 399DE7366D52937E245235F18EBD8117
Dropped File - Encrypted file
Names:
- {randomnumber}.QdE
- img.jpt
- tmp.pkg
- cf.kls
- log.ktg
same MD5: C95A7F3FDDE60FCE15BFA74ED87B62CE
Dropped Files
C:Users{username}AppDataRoaming{randomnumbers}.QdE
C:Users{username}AppDataRoaming{randomnumbers}.VIv
C:Users{username}AppDataLocalWord document.vbs
C:Users{username}AppDataLocalDocument Part.vbs
Communicated IP addresses
8.8.8.8
185.188.183.235
185.180.231.35
74.220.215.248
64.71.35.52
Communicated URLs
http://185.188.183.235/img.jpt
www.legadodevelopmentgroup.com/tmp.pkg
http://185.180.231.35/cf.kls
www.premierautoestates.com/log.ktg
Final Dropped Spyware - Ursnif
Name: {randomnumbers}.VIv
MD5: 15BAA544D5EFCB1B88AA71A99EEC95D3
Spyware Copies itself to below location:
C:Users{username}AppDataRoamingMICROS~1adprtext.exe
DNS query by the Spyware and URLs for POST traffic
psuchyouincl[.]ru
acontributorsthemt[.]ru
verstrictaiphp[.]ru
fromsoftwarezend[.]ru
withbuttoutversionliable[.]ru
IP addresses communicated by Spyware
82.79.209.244
208.67.222.222
89.185.22.170
Threat Intelligence
The analysis shows one of the IP is tagged under Botnet activity. The IP address "89.185.22.170" is seen tagged under "Botnet." Also another IP address "82.79.209.244" contains the same Russian malicious domain which Botnet IP had, which can link as this IP also can be part of this Botnet.


The main IP address of the spyware which we analyzed must be "87.98.254.64" which contains most of the domain to which the spyware is sending POST traffic and DNS request.
The analysis shows that this IP is sink-holed by "zinkhole.org" a sinkhole project – which itself shows this IP is a zombie IP and part of Botnet.



As we can see the relationship contains a lot of branches across internet and lot of malware hosted on the IP address, this IP address must be the seed for an ongoing botnet activity.

Also, we can see the below intelligence stating this IP has also been reported as Botnet IP:

Conclusion
The spam emails are spreading across the internet, utilizing various tricks and tactics to evade all the security measures in an entity. These malicious documents would drop most of the flavors of malware with ease. In this incident, we saw the Document used two evading techniques such as Password protection and sleeping mechanism, dropping a Spyware and letting it execute on the victim machine.
No Macro enabling popup, Evaded Sandbox, AV evasion, passed the Mail Gateway. Hmm... Let's start Security Awareness Training for the end users :)
Reference:
https://digital-forensics.sans.org/blog/2009/11/23/extracting-vb-macros-from-malicious-documents/
https://zeltser.com/malware-analysis-webcast/
https://zeltser.com/automated-malware-analysis/
https://www.decalage.info/en/taxonomy/term/10
https://spreadsecurity.github.io/2016/08/14/macro-malware-analysis.html









