Common misperceptions about PCI DSS: Let’s dispel a few myths
You’ve probably heard many things that aren’t necessarily true about the Payment Card Industry Data Security Standard (PCI DSS).
We’ll do our best to demystify PCI DSS as a framework and a requirement so your organization can make more informed decisions on your information protection journey. Let’s dive right in.

Get your free course catalog
The most common misconception I’ve heard is from small businesses.
“We run the local convenience store at the corner; surely PCI DSS compliance can’t be for me”
Size doesn’t matter.
Unless, of course, you’re OK with fines or data breaches, your business must meet the base PCI requirements, even if you’re so small that you only process a single credit card payment each year.
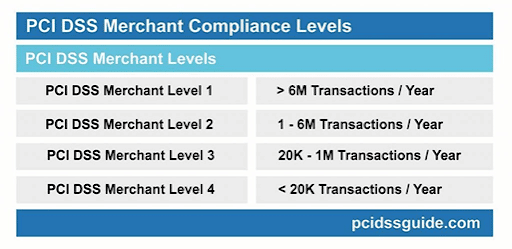
Having said that, as you will see from the table below, there are different levels of compliance expected by each of the biggest credit card vendors (including VISA, Mastercard etc.), so a small business doesn’t have to adhere to the same requirements as a multi-billion dollar multinational would need to.
So, Level 1 merchants must file a Report on Compliance (ROC) through a Qualified Security Assessor (a QSA) or a certified Internal Auditor, submit an annual Attestation of Compliance (AoC) and (if required, as guided by the QSA), a quarterly network scan by an Approved Scan Vendor (ASV). (That’s an awful lot of acronyms!)
On the other hand, for Levels 2 to 4, the annual PCI validation requirements are all the same. Annually, these merchants must complete a Self-Assessment Questionnaire (SAQ) and also submit an Attestation of Compliance (AoC). In addition, they are required to have a quarterly network scan per Approved Scan Vendor (ASV).
"PCI is only for technical folks to worry about"
Although your IT staff may implement your PCI-related controls, management still needs to be the driving force behind reaching the holy grail of compliance; and every employee in your organization should be aware of the requirements needed to protect your customers’ information. For example, janitorial staff who don’t necessarily have access to the organization’s network still need to understand the basics around securing company information; they are a key ally in keeping everyone else honest when we get sloppy with our disposal!
PCI compliance is wholly and truly a team effort. And once you get to the finish line, you keep going. Compliance is an ongoing process of assessing, addressing, and maintaining those data protection processes and controls. The risks of non-compliance influence your customers' perception of you, your reputation in the market and the entire organization.
"Only e-commerce companies have to be PCI compliant"
Again, that’s an emphatic “no!”
If your company stores, processes or transmits cardholder information, complying with PCI DSS is important, regardless of whether your sales are online or in a more traditional brick-and-mortar shop.
Organizations that must be PCI compliant include financial institutions (banks, lenders and insurance companies), merchants (retailers, restaurants and hospitality), as well as service providers (data centers, call centers).
For example, because of the higher likelihood of card skimming and poor password hygiene, the Point of Sale (PoS) systems in traditional retail shops are typically even more at risk than e-commerce solutions with more stringent security measures built in.
Simply put, if you’re running a business, even where you don’t sell merchandise online, it’s more crucial than ever to follow PCI requirements.
"I’ve outsourced my credit card processing, so I’m covered for PCI compliance"
Accepting credit card payments online through a third-party vendor may seem like the easy way out. You know they process your payments for a small fee, worry about the regulations, and you get paid, right? Not quite.
While it’s true that some vendors act as the recordkeeper for your transactions and assume the responsibility of maintaining PCI compliance, that doesn’t mean you’re automatically PCI compliant or off the hook.
Your internal business environment must still remain compliant too. Your accountant storing credit card data on a Sharepoint site with access permissions set to public, users sharing system accounts or not using a firewall or antivirus software are all violations of core PCI DSS requirements, and they remain your responsibility.

Get your free course catalog
"PCI requirements are way too complex"
When you look at the evolving versions of the framework, with addendums and subsections galore, it’s easy to see why so few businesses put in the effort to comply with PCI DSS requirements.
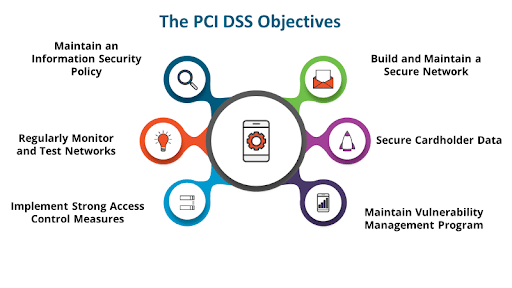
However, when you break it down into the basic principles, it becomes easier to digest and make sense of. At the time of writing, only 12 PCI requirements addressed six control objectives (see below).
In addition, when you consider that maintaining compliance protects your customers’ information and your business reputation and saves you money (data breaches are costly and a heck of an inconvenience), you realize that it is worth putting in the leg work.
The importance of keeping credit card data safe at your business
Now that we’ve debunked some myths, it’s important to get the help you need to understand and implement the requirements of the PCI DSS framework for your organization's specific needs. Countless organizations have done it, so putting in place leading information security safeguards is very doable as long as your organization remains committed to the journey.
View my Infosec PCI-DSS for Developers course to learn more, and read my article, How PCI DSS acts as an (informal) insurance policy.