An Introduction to cybersecurity policy
Security policy
Security policy is the statement of responsible decision makers about the protection mechanism of a company crucial physical and information assets. Overall, it is a document that describes a company's security controls and activities. Security policy does not specify a technological solution, instead, specifies sets of intentions and conditions that will aid to protect assets along with its proficiency to organize business. In more depth, a security policy is the primary way in which administration prospects for security are translated into specific, measurable goals, as well as direct users to build, install, and maintain systems, so they do not have to make those decisions by themselves. Finally, it should be in written form to offer guidance about what kind of behavior, resource uses are required in acceptable from its employees and moreover, about what is forbidden to wield.
Policy makers
Security policy development is a joint or collective operation of all entity of an organization that is affected by its rules. In general, security policies should not be developed by IT team itself as it is a responsibility of everyone that has a stake in the security policy should be involved in its development so that they could too, mold the policy according to their requirement. During policy creating following entity typically involves;
- Board: Company board members must render their advice to some form of a review of policies in response to exceptional or abnormal running condition of business.
- IT Team: IT team members usually are the biggest consumers of the policy information in any company, as it involves making standard around the usage of the computer system, especially security controls.
- Legal Team: This team ensure the legal points in the document and guide a particular point of appropriateness in the company.
- HR Team: HR team typically obtain a certified T&C certificate from each employee that they have read and understood the stipulated policy, as the HR team deals with reward and punishment related issues of employees to implement discipline.
Security policymakers must be aware that choosing a policy that backs a stratagem is a simple task compared to validating that the policy is effective. Security policy development approach involves the following stages as:
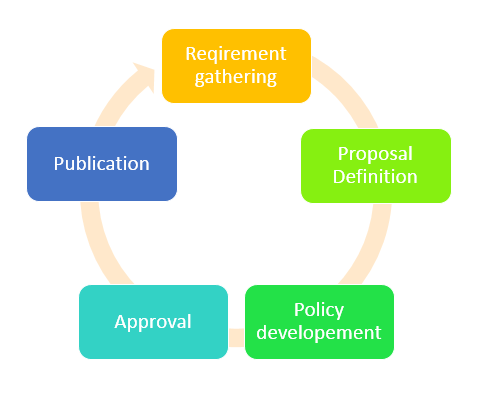
Policy audience
Security policy applies to all senior management, employees, stockholders, consultants, and service providers who use company assets. More importantly, the security policy must be readable, concise, and illustrated, to be effectively comprehensible to its audience and all employees so that everyone adheres to policies and fulfills their defined role. The following figure gives an indication of the organization in a typical company that would need to read the security policy
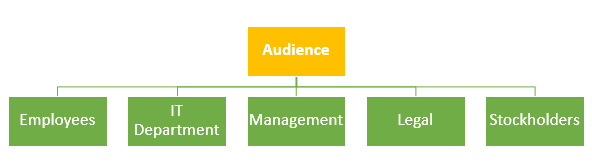
In other words, security policy incorporates all employees, hardware, software, consultants, service provider who use company assets such as computer networks data information or any information that is perceived to be valuable to the business
Policy classification
Every organization typically has three policies: First that is drafted on paper, second, that is in employees' minds, and finally that it is actually implemented. The security policies are a part of the hierarchy of management control, addresses its audience what to be done according to the stipulated terms and conditions of a company. Policy generally requires what must be done, never address how it should be done. Security policies could be informative, regulative, and advisory in a broad manner, generally, be subdivided into following categories as;
- Physical security: It mandates what protection should be wielded to safeguard the physical asset from both employees and management, applies to the prevail facilities including doors, entry point, surveillance, alarm, etc.
- Personnel management: they are supposed to tell their employees how to conduct or operate day to day business activities in a secure manner, for instance, password management, confidential information security, etc., applies to individual employees.
- Hardware and software: It directs the administrator what type of technology to use and what and how network control should be configured and applies to system and network administrators.
Policy audit
Security documents are living documents. Therefore, they ought to be updated at specific intervals in response to changing business and customer requirements. Once, policies are well-established and ready to dictate typical operations, an audit may be performed by outsiders or insider agencies to compare existing practices to the intentions of policy. Security policy audits assist the company to understand better the threat the organization is exposed to and the effectiveness of your current protection. Security audit's goal is to bring all the security policies close as possible. Security auditing is a high-level analysis of the current project progress and company posture on test information security related to existing policies compliance. Auditing is periodically performed to compare existing practices against a security policy to substantiate or verify the effectiveness of security measures. Finally, the goal of a security audit is to provide the company with a verification of best practices already in place. A successful security audit accomplishes the following:
- It compares your security policy with the actual practice in place.
- It determines your exposure to threats from the inside.
- It also determines the exposure of your organization from an outside attack.
Policy enforcement
Enforcement of security policies ensures compliance with the principle and practices dictated by the company because policy, procedure do not work if there are violated. Enforcement is arguably the most significant aspect of a company; it dissuades anyone from deliberately, accidentally violates policies rules. System administrator level enforcement ensures proper maintenance and prevents privilege escalation, and employees level enforcement look after the assurance of daily working activities comply with policies. However, there is proper balance should be maintained between positive and negative enforcement. The best employees that abide by rules rewarded time to time to increase their motivation and boost up their moral high in positive enforcement. In negative enforcement, on the other hand, strict compliance of policies takes the form threat to the employees.
Policy awareness
Company employees are often perceived as "soft" target to be compromised, as the human elements the least predictable and easiest to exploit. Trusted employees either "disgruntle" or are framed to provide valuable information of a company. Therefore, one of the most robust storage to combat this exposure of information by employees is "education." When employees duly able to understand that what they should give or what shouldn't give out confidential information, and also know the reason why then the company internal are less likely to be vulnerable. A good security awareness program must be periodically performed and should include all the existing security policies that are mandated to be compliance from employees' end. Moreover, awareness programs should also integrate communication and reminders to employees about what they should and shouldn't reveal to outsiders. In final words, security policy awareness training and education mitigate the threat of information leakage.
Final words
This article provides insight into the security policy in general introductory form, like as the basics of what you need to know about policies, standards, procedures, and guidelines. Overall, it should tell their audience what must be fulfilled, not deals with the mechanism of fulfillment as it lays the foundation for a productive security program. The gist of this piece is that security should begin with an initial assessment that includes current security policies, identification of objective, review of requirement, and determination of current vulnerability to be used as a baseline for testing the implementation.
Sources
- Barman, Scott. Writing Information Security Policies. New Riders Publishing, 2001.
- Desman, Mark B. Building an Information Security Awareness Program. Auerbach Publishing, 2001.
- Dijker, Barbara L., ed. A Guide to Developing Computer Policy Documents. Usenix Associates, 1996.
- Greene, Sari. Security Policies and Procedures: Principles and Practices. Prentice Hall, 2005.
- Herold, Rebecca. Managing an Information Security and Privacy Awareness and Training






