Legal issues of new and emerging technologies
Since the invention of the agriculture in the Fertile Crescent, the humanity has witnessed continuous technological developments. Such developments affect the human society in positive and negative ways. For example, an airplane allows the quick transportation of passengers, whereas an atomic bomb provides its users with an opportunity to destroy entire nations. The governments put efforts to regulate technology in such a way as to enhance its positive effects and ameliorate its negative consequences. For example, there are governmental regulations related to the use of cookies (i.e., small files which are stored on a user's computer), drones, wearable devices (e.g., smart watches and Google Glass), and social networking platforms. The regulation of new and emerging technologies is not an exception.
What does "new and emerging technologies" mean?
The term "New and Emerging Technologies" (NET) encompasses the most novel, advanced, and prominent innovations that are developed within various fields of current modern technology. The current examples of NET include, for example, zero-emission cars that run on hydrogen, next-generation robotics, genetic engineering techniques, developments in artificial intelligence; nanotechnology, social networking, etc.
The scope of the term "New and Emerging Technologies" (NET) has been in a process of continuous expansion. Two decades ago, most NET were related to artificial intelligence machines. The popularity of augmented reality, nanotechnology, Internet of Things, and 3D printing started growing at the beginning of the current century.
Irrespectively of their type, NET have serious social implications. They shape our homes, businesses, and governments. A large number of Facebook's 1,44 billion monthly actively users use social networking at home. One can visit a restaurant in London in which the menus are projected directly onto the tables and orders are submitted digitally to the kitchen. Government authorities have set up facial recognition systems allowing them to identify and monitor people attending public events.
Although NET certainly bring benefits to the humanity, they also pose challenges. For example, the physical objects comprising the Internet of Things can allow hackers to receive far more information about their victims than hackers currently can. The solutions to the challenges posed by NET are three, namely, (1) research, (2) development, and (3) regulation. In this article, we will focus on the latter solution only.
The legal issues related to "New and Emerging Technologies" (NET) fall within the scope of the laws regulating the use of data, evidence, creative works, and inventions. We will further focus on four such laws:
- Privacy law, i.e., the law that regulates the collection, use, processing, and disclose of personal information. Under most privacy laws, personal information is defined as information which identifies an individual or allows an individual to be identified;
- The law of evidence, i.e., the law that governs the proof of facts in legal proceedings;
- Copyright law, i.e., the law that governs the ownership and use of creative works
- Patent law, i.e., the law that regulates the rights to inventions.
Structure of the article
The present article aims to discuss briefly four major categories of legal issues arising out of the use of NET, namely, privacy issues (Section 2), issues related to gathering evidence (Section 3), copyright issues (Section 4), and patent issues (Section 5). Finally, a conclusion is drawn (Section 6).
PRIVACY ISSUES
The privacy issues related to NET can be grouped into two categories, namely, (1) security vulnerabilities threatening the privacy of NET users and (2) the use of NET for unlawful surveillance (see Fig. 1). These two categories are examined in Sections 2.1 and 2.2, respectively. The first category relates to privacy issues caused by security vulnerabilities of NET. Such security vulnerabilities may include, for example, weak authentication, insufficient encryption, and insecure firmware. The second category of issues refers to the use of NET for unlawful surveillance. For example, thieves may use crowdsensing for detecting when a victim is not at home. The term "crowdsensing" refers to sharing data collected by sensing devices with the aim to measure the phenomena of common interest.
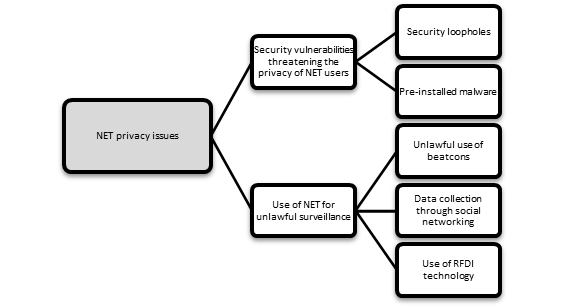
Fig. 1 Privacy issues related to NET
Security vulnerabilities threatening the privacy of NET users
The security vulnerabilities of NET can be broadly categorized into (1) security loopholes and (2) security vulnerabilities caused by pre-installed malware. The security loopholes of NET are programming or others flaws which allow a hacker to reduce NET's information assurance. For instance, a weak password may allow the hacker to penetrate into NET by using a dictionary attack, i.e., a technique for defeating the authentication system of a computer system by using a large number of passwords. Other security loopholes of NET include software bugs, lack of security awareness, and weak or non-existent anti-virus programs.
In addition to security loopholes, some NET may have pre-installed malware. Such malware can be preinstalled either (1) by the manufacturer of NET or (1) by a third-party (a non-manufacturer). The pre-installed malware can affect other computers in a network. Thus, a smartwatch containing pre-installed malware can infect a smart kitchen, a smart phone, a household robot, and a smart air conditioner.
- Weak passwords;
- Software bugs;
- Lack of security awareness;
- Weak or non-existent anti-virus programs.
- NET containing malware pre-installed by the manufacturer;
- NET containing malware pre-installed by a non-manufacturer.
Using NET for unlawful surveillance
The following three types of NET are often used for unlawful surveillance:
- Beacons, i.e., tiny wireless transmitters that constantly send radio signals. Beacons can be used by criminals to track the location of the users of mobile devices. For example, a criminal may install malware on victim's computers which collects location information from beacons and sends the collected location information to the criminal.
- Social networks, i.e., platforms allowing their users to build social network relationships. Social networking can be used by criminals to receive unauthorized access to personal information. For instance, a criminal may create a fake profile in Facebook and send a "friend request" to a victim. By accepting the "friend request," the victim will allow the criminal to access a tremendous amount of personal information about the victim (e.g., personal data, photos, videos, and location information).
- RFID technology, i.e., the wireless non-contact use of radio-frequency electromagnetic fields to transfer data with the aim to automatically identify and track tags attached to objects. A human implanted RFID chip installed without the knowledge and the authorization of the receiving person will make that person a lifelong object of surveillance.
Unlawful use of beacons
The unlawful use of beacons may allow criminals to: (1) identify behavioral patterns of potential victims (e.g., money spending, visited places, and lifestyle) and (2) send spam to potential victims (e.g., customized advertisement). The data collection about the behavior patterns can facilitate criminals in the selection of their victims. For instance, an individual who attends luxurious restaurants may be more attractive to thieves than an individual who regularly visits fast food chains. Thieves' use of information about the behavior patterns of their victims is not a new phenomenon. In 2014, thieves stole jewelry amounting to GBP 100.000 from lawyers after finding on the Internet information about the lifestyle of the lawyers. Similarly, spammers can use the location data to send advertisements customized by the location of the user. By way of illustration, a visitor of a golf club will receive spam related to golf sticks and the visitor of a hospital will receive spam related to medicaments.
Unlawful collection of personal data through social networking platforms
Social networks may be used for obtaining personal data without authorization. The most common methods to unlawfully collect personal data through social networks are:
- The creation of a fake social networking account. Although fake profiles imitating real people (i.e., the so-called impostor accounts) are not allowed by Facebook and other social networking platforms, Facebook reported having around 170 million fake users. Hence, there are more fake Facebook users than the cumulative population of France, Spain, and England.
- Hacking a social networking account. The users of social networking platforms often use weak passwords, e.g., names, birthday, or common phrases found in a dictionary. Such weak passwords make the users susceptible to dictionary attacks.
- Distributing a social networking app which collects data from the users without their authorization. To get personal information about a larger number of victims, hackers often employ social networking malware. The malware may be masked as gaming apps and apps providing access to digital content. Such seemingly innocent apps may request the user to access his/her public profile, friend list, email address birthday, current city, and other personal information. If the user allows the apps to access such information, the apps will collect all available information about the user and send it to a fraudster who may blackmail the user or commit identity theft.
Unlawful use of RFID technology
There are two main security concerns related to the use of RFID chips, namely, (1) infection with computer viruses and (2) cloning of RFID chips. Criminals may obtain unauthorized access to personal information by infecting human-implanted RFID chips or cloning them. The RFID systems have two components, (1) a transponder and (2) a detector. The transponder transfers data to the detector, whereas the detector reads the data transferred by the transponder and/or modifies the data in the transponder. If infected by computer viruses, human-implanted RFID transponders may transfer viruses to the devices which receive information from the infected transponders. Dr. Mark Gasson, a senior research fellow at the University of Reading, has demonstrated how an RFID transponders infected with malware can transfer the malware to the computer system of a secure building. Cloned human implanted RFID transponders can allow hackers to receive unauthorized access to personal information. For example, a hacker may use a cloned RFID transponder to open an RFID door lock.
Issues related to gathering evidence through Net
The digital information processed by NET can be used as evidence. However, due to various issues, digital evidence can be ruled inadmissible by courts or considered to be unreliable. The issues related to evidence collected through NET can be divided into two broad categories, namely, (1) general issues related to gathering evidence through NET and (2) issues related to gathering evidence through social networks (see Fig. 2). The first category encompasses issues which relate to digital evidence in general, e.g., inadmissibility of evidence because it was obtained without authorization and unreliability of evidence due to authentication problems. The second category covers specific issues related to the collection of evidence through social networks, e.g., authenticity and admissibility of evidence collected through social networks. The two categories of issues related to digital evidence are discussed in Sections 3.1 and 3.2, respectively.
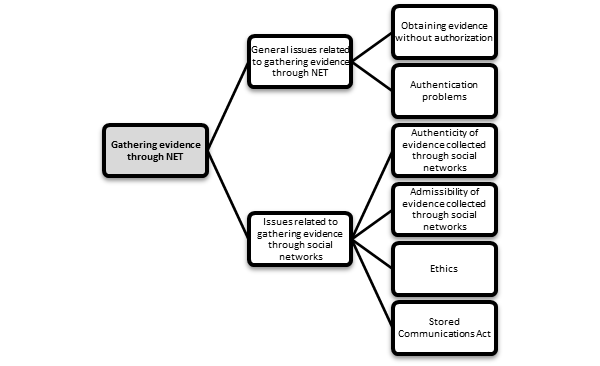
Fig. 2 Issues related to gathering evidence through NET
General issues related to gathering evidence through NET
The two most common issues related to gathering evidence through NET are problems of (1) obtaining evidence without authorization (digital evidence obtained without a warrant may be inadmissible in a court of law) and (2) authentication. Under the laws of most jurisdictions, seizure and investigation of digital devices requires a warrant. The term "warrant" can be defined as a specific type of authorization issued by a governmental institution. Early U.S. court decisions required that authentication of digital evidence called "for a more comprehensive foundation" (U.S. v. Scholle, 553 F.2d 1109 (8th Cir. 1976). Later, the U.S. courts changed their approach by stating that: "computer data compilations (…) should be treated as any other record" (U.S. v. Vela, 673 F.2d 86, 90 (5th Cir. 1982). At present, the "more comprehensive foundation" of the authentication of the digital evidence remains a good practice.
Issues related to gathering evidence through social networking platforms
The term "social networking platform" means an online application which allows its users to share content in virtual communities. Social networking platforms appeared in the last decade of 20th century. Initially, they allowed people to create personal pages and interact with each other through chat rooms. At the beginning of 21st century, social networking websites, such as MySpace and LinkedIn, developed comprehensive profile creation tools. Facebook, a social networking platform introduced in 2004, became the largest social networking site in the world.
There are six categories of social networking platforms. These categories are described below.
- Social networking platforms connecting people in general (e.g., Facebook and MySpace) allow various users to connect with each other. For example, consumers may use such platforms to connect with companies.
- Social networking platforms connecting professionals (e.g., LinkedIn, Plaxo, and Xing) are focused on business communications. These platforms are used mainly for communication between professionals.
- Social bookmarking websites (e.g., Digg, Delicious, and StumbleUpon) allow users to add, edit and share bookmarks of web documents.
- Internet forums (e.g., Meetup and Craiglist) provide their users with the opportunity to hold discussions in the form of posted messages.
- Business directories (e.g., Yelp and CitySearch) list business operating within the same business field.
- Photo and video sharing platforms (e.g., YouTube and Flickr) enable users to sell, view, and purchase photos and videos.
Users of social networking platforms often publish in their profile photos, videos, text, location information, as well as information about their relationship. Such information can be used as evidence in court proceedings. The party who would like to use the evidence does not need to prove each step of the creation of the evidence to guarantee its authenticity. The evidence collected through social networking platforms is not treated differently than the other types of evidence. The most common types of evidence collected through social networking platforms are (1) photos; (2) videos; (3) text; (4) location information; and (5) information about relationships.
We will further discuss four types of issues related to gathering evidence through social networks, namely, issues related to authenticity of evidence collected through social networks (Section 3.2.1), issues related to admissibility of evidence collected through social networks (Section 3.2.2), ethical issues (Section (Section 3.2.3), and issues related to the Stored Communications Act (Section 3.2.2).
Issues related to authenticity of evidence collected through social networking platforms
Social networking evidence that may require authentication includes but is not limited to, (1) social network profiles, (2) social network postings, (3) chats from social networks, and (4) photographs and videos from social networks.
Given the ability of hackers to modify content published on social networking platforms, courts are open to rebuttable evidence. Rebuttable evidence means evidence which repeals, counteracts, or disproves other evidence. For example, a Facebook profile indicating the behavior patterns of the defendant may have no evidentiary value if there is rebuttable evidence showing that the Facebook profile was not created by the defendant, but by a third party which is not related to the defendant in any way.
Therefore, the authentication of social networking evidence requires answering five questions:
- When was the evidence collected?
- How was the evidence collected?
- Where was the evidence collected?
- What types of evidence were collected?
- Who handled the evidence before it was collected?
If no answer to one or more of these questions can be provided, the evidence may be inadmissible.
Issues related to admissibility of evidence collected through social networking platforms
If social networking evidence is collected without authorization or is unreliable, it would be considered inadmissible. The authorization to gather social networking evidence usually takes the form of a warrant (i.e., a specific type of authorization issued by a governmental institution) or a subpoena (i.e., is a legal document obliging a natural or legal person to produce evidence). After the warrant or the subpoena is submitted to the operator of a social networking platform, the operator becomes legally obliged to provide the requested evidence. Most social networking platforms have clearly explained what type of warrants and subpoenas they will consider. For instance, Facebook has published a web page "Law Enforcement & Third-Party Matters" which contains information on how law enforcement authorities and third parties may seek records from Facebook.
To be admissible, social networking evidence must not only be collected with authorization but also reliable. Therefore, a photo posted on a social networking platform may not be reliable evidence if the photo is unclear.
Ethical issues
Examples of ethical issues include (1) obtaining evidence by sending a friend request to an unknown person and (2) obtaining evidence by befriending the person whose evidence will be collected, among others. In U.S. civil litigation, evidence may be admissible even it was obtained unethically. However, some U.S. courts reserved the right to exclude evidence obtained in violation of ethical rules.
Persons who gather evidence in an unethical way risk not only excluding the evidence but also receiving punishments for violation of various ethical rules. For example, the professional rules governing the conduct of attorneys in New York State stress that: "Although a lawyer is not a moral advisor as such, moral and ethical considerations impinge upon most legal questions and may decisively influence how the law will be applied." Therefore, a lawyer who collects evidence in an unethical way may be sanctioned by the bar organization which regulates lawyer's conduct.
The Stored Communications Act
The Stored Communications Act (SCA) regulates the disclosure of "stored wire and electronic communications and transactional records" (the SCA is available at: https://www.law.cornell.edu/uscode/text/18/2701). The term "records" as used by the SCA may include backup copies of files in temporary electronic storage. Section 2701 of the Stored Communication Act provides for criminal sanctions for a person who "intentionally accesses without authorization a facility through which an electronic communication service is provided". Hence, the unauthorized collection of evidence from social networking platforms may lead to imprisonment.
The SCA does not cover information stored on home computers because such information is protected by the Fourth Amendment to the U.S. Constitution. Hence, the SCA covers only information held by third-party providers, such as providers of social networking platforms.
Copyright issues related to Net
The term "copyright" can be defined as "the exclusive right of the author or producer of a literary, scientific, or artistic work to publish and reproduce it." (Kraak and Ormeling, 2011, p. 182) The copyright issues arising related to NET can be categorized into the following three categories (See Fig. 3):
- Unlawful use of user-generated content created by NET;
- Unlawful publication of copyright content on social networks; and
- Unlawful collection of copyrighted content from social networks.
The first category encompasses the unlawful use of user-generated content created by NET in general. Such issues may arise, for example, from the unlawful use of copyrighted photos taken by wearable devices (e.g., Google Glass and smart watch). Under the Berne Convention for the Protection of Literary and Artistic Works, an international copyright treaty applicable in more than 160 countries, copyrights for creative works are automatically in force upon their creation. Hence, anyone who copies or distributes digital content taken by NET will probably infringe the copyright law.
The second category includes issues related to the publication of copyrighted content (e.g., videos, photos, and text) on social networks. In some cases, the publication of such content may fall within the scope of the "fair use" doctrine. "Fair use" is a legal doctrine that permits limited use of copyrighted material without obtaining the permission of the copyright holder. In the United States, examples of "fair use" may include, without limitation, criticism, parody, news reporting, commentary. If the person who posted copyrighted content on social networks cannot prove that the "fair use" of content, he/she will be liable for a copyright infringement.
The third category covers issues related to the unlawful collection of copyright content from social networking platforms. For instance, such issues may arise from the use of data mining technologies which automatically collect a large amount of copyrighted user-generated content posted on social networking platforms.
 Fig. 3 Classification of NET copyright issues
Fig. 3 Classification of NET copyright issues
The three categories of NET copyright issues are examined in Sections 4.1, 4.2, 4.3, respectively.
Unlawful use of copyrighted user-generated content created by NET
User-generated content can be defined as content created by the users of online services. Examples of user-generated content include: (1) advertisements, (2) audio, (3) blogs, (4) chats, (5) forums, (6) pins, (7) podcasting, (8) posts, (9) tweets, (10) video, and (11) wikis. The popularity of user-generated content is a result of the emergence of the second phase of development of the World Wide Web, namely, Web 2.0. In the first phase (i.e., Web 1.0), the users were merely consumers of content, whereas in the second phase users are active creators of content.
Under the Berne Convention, an international copyright treaty applicable in more than 160 countries, copyrights for creative works are automatically in force upon their creation (the text of the Berne Convention for the Protection of Literary and Artistic Works can be accessed at http://www.wipo.int/treaties/en/text.jsp?file_id=283698).
Under the laws of most countries, authors automatically obtain the copyright in their user-generated content upon its creation. The authors do not need to (1) assert the copyright in the user-generated content (e.g., by adding the © symbol) or (2) register their copyrighted content (e.g., by using the services provided by the United States Copyright Office).
If a person uses the whole or a substantial part of a copyrighted work without permission, that person is liable for a copyright infringement. The copyright holder may commence court proceedings in order to: (1) stop the infringement; (2) receive compensation for damages suffered as a result of the infringement; and (3) order the infringer to give up the infringing materials to the copyright holder. However, since court proceedings may take a long time, it is preferable if the copyright holder tries to resolve the matter with the infringing party.
Digital Millennium Copyright Act (DMCA) notifications. If a copyright holder finds that a company (e.g., a search engine or a web host) is hosting or linking to copyright infringing material, the copyright holder may submit to the company a DMCA notice requesting the removal the copyrighted works. Under the DMCA, if the company quickly removes the content specified in the DMCA notice, the company will not be liable for hosting or linking to that content.
The DMCA notice must comply with strict legal requirements. For instance, the DMCA notice must contain: (1) the signature of the copyright holder; (2) identification of the copyrighted work claimed to have been infringed; (3) identification of the allegedly infringing material; and (4) contact details of the complaining party. The full list of requirements can be found in the DMCA, available at http://www.copyright.gov/legislation/dmca.pdf .
Unlawful publication of copyrighted content on social networking platforms
The publication of copyrighted content on social networking platforms without the permission of the copyright holder constitutes a copyright infringement unless such a publication falls within the scope of the "fair use" doctrine. However, there is no a clear-cut line between fair use and copyright infringement. Therefore, the users willing to post copyrighted content on social networking platforms need to consult an intellectual property lawyer before the publication of such copyrighted content. Otherwise, they may be liable for a copyright infringement. The sanctions for a copyright infringement include, without limitation, fines, and imprisonment.
Unlawful collection of copyrighted content from social networking platforms
The unlawful collection of copyrighted content from social networking platforms constitutes a copyright infringement unless such a collection falls within the scope of the "fair use" doctrine. The automatic collection of a large amount of data from social networking platforms may constitute a severe copyright infringement, punishable by fines and imprisonment.
Patent issues
The term "patent" can be defined as: "an exclusive right or rights provided by a government to an inventor for a certain period of time in exchange for the public disclosure of an invention" (Dimov, 2013). Since most NET are software-based, in this section, we will focus on software patents.
Software patents are a controversial topic. While some countries prohibit the grant of software patents, others allow inventors to receive patents for software. Interestingly, the proponents and the opponents of software patents use the same reasoning to justify their position.
More specifically, the proponents of software patents argue that the prohibition of software patents will "stiff" innovation because the inventors would not have an incentive to invest in software which cannot be protected by a patent. The opponents of software patents argue that software patents "stiff" innovation because the owners of the software patents use them against start-ups which do not have enough financial resources to defend their inventions in court.
A discussion of the software patents from an international point of view follows in Section 5.1. In Section 5.2, this article examines the software patents in the United States. In Section 5.3, we elaborate on the future of the software patents.
Software patents all over the world
Most countries place limits on the patenting of software. However, those limits differ amongst the countries. For example, the European Patent Office does not grant patents for computer programs or computer-implemented business methods that make no technical contribution. In the same vein, the United States Supreme Court stated in Alice Corp. v. CLS Bank International that: "merely requiring generic computer implementation fails to transform [an] abstract idea into a patent-eligible invention."
Although most countries impose limits on patenting software, software patents have been widely granted. A large number of software patents cover NET. For instance, on February 23, 2010, Facebook was granted US Patent No. 7,669,123, which discloses a method for dynamically providing a news feed about a user of a social network.
Software patents in the United States
The United States patent law does not explicitly mention software patents. Hence, the patentability of software invention has been addressed by courts. The history of the United States patent law started with the adoption of the U.S. Constitution. Article I, Section 8 of the U.S. Constitution states: "The Congress shall have Power (...) to promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries." Since the software patents appeared in the 20th century, the U.S. patent law had to be expanded to address such patents. The expansion was done by the U.S. courts in a large number of court decisions. The cases Bilski (Section 5.2.1) and (2) Alice (Section 5.2.2) are two of the most important U.S. cases related to software patents.
Bilski case
Prior to Bilski case, an invention was patentable only if: (1) an invention is implemented by a particular machine or (2) an invention transforms an article from one state to another. In the Bilski case, the U.S. Supreme Court stated that an invention can be patentable even if it is not implemented by a particular machine or transforms an article. Thus, the U.S. Supreme Court opened the door to software patents, including software patents related to NET. The case Bilski resulted in a flood of patent applications for various types of software. Further, the case put the U.S. Patent and Trademark Office (USPTO) in a difficult situation because the USPTO was left without guidelines on the patentability of inventions failing to comply with the "machine-or-transformation" test.
Alice case
In Alice case, which follows Bilski case, the U.S. Supreme Court stated that the implementation of abstract ideas on a computer was not enough to transform the ideas into patentable subject matter. Therefore, the Alice case resulted in a significant drop in the number of U.S. software patents. Federal Circuit Judge William Curtis Bryson explained the post-Alice drop in the number of U.S. software patents as follows: "In short, such patents, although frequently dressed up in the argot of invention, simply describe a problem, announce purely functional steps that purport to solve the problem, and recite standard computer operations to perform some of those steps. The principal flaw in these patents is that they do not contain an "inventive concept" that solves practical problems and ensures that the patent is directed to something "significantly more than" the ineligible abstract idea itself. "
The future of software patents
There has been an increase in the number of countries which seriously limit the patentability of software. For example, in the United States, such a limit was set by the Alice case in 2014. In New Zealand, computer programs were excluded from patentability in 2013. Similarly, in Germany, the German Parliament adopted in 2013 a motion "against the growing trend of patent offices to grant patents on software programs." In the future, we can expect more and more countries to restrict the patentability of software.
Conclusion
This article discussed four categories of legal issues related to NET (i.e., privacy issues, issues related to gathering evidence, copyright issues, and patent issues). These issues can be overcome to a large extent by a joint cooperation between private organizations and governments. The role of each of these two actors for overcoming the aforementioned issues is explained below.
- The role of industry self-regulation for the development of NET. The term "industry self-regulation" can be defined as a process through which an organization monitors its own adherence to standards (including legal standards) and enforce those standards. Since NET are developing with a significant speed, governmental regulation often lacks the flexibility to adapt to the rapid development of NET. Industry self-regulation allows the businesses to use their expertise in NET in order to solve issues arising out of the use of NET.
- The role of government for the development of NET. The governments can enhance the development of NET in two ways, namely, (1) by funding research projects falling within the scope of NET and (2) by adopting regulation of NET which complement the industry self-regulation.
Sources
- Alice Corp. v. CLS Bank International, 573 U.S., 134 S. Ct. 2347 (2014);
- Bilski v. Kappos, 561 U.S. 593 (2010);
- Dimov, D., 'Software Patent Law: EU, New Zealand, and the US compared', InfoSec Institute, 2013;
-
Kraak, M., Ormeling, F., 'Cartography, Third Edition: Visualization of Spacial Data', Guilford Press, 2011.
Co-author
 Rasa Juzenaite works as a project manager in an IT legal consultancy firm in Belgium. She has a Master degree in cultural studies with a focus on digital humanities, social media, and digitization. She is interested in the cultural aspects of the current digital environment.
Rasa Juzenaite works as a project manager in an IT legal consultancy firm in Belgium. She has a Master degree in cultural studies with a focus on digital humanities, social media, and digitization. She is interested in the cultural aspects of the current digital environment.






