Cellular Networks and Mobile Security
Despite their seemingly endless coverage (your mileage will definitely vary), cellular network security has proven to be surprisingly robust over the years. There have been security issues over the years to be sure, but the lion's share of problems have come from the way that people use the network rather than the network itself being compromised.
These threats can come from all of the usual sources that you would try to protect from online, but there are some that are also uniquely tied to mobile devices. Today we're going to be briefly covering some of the security functions that had been implemented over the years for cellular networks and some of the threats we still face on a day to day basis when it comes to mobile security.
Learn Network Security Fundamentals
![]()
Cellular networks
There are a number of different communication technologies that most users are at least somewhat familiar with but are tied to particular 'Generations' of devices and their associated networks- GSM (Global System for Mobiles) and CDMA (Code Division Multiple Access) were commonplace during the 2G and 3G era, LTE (Long Term Evolution) for 4G, and 5G-NR for 5G networks that are still being rolled out. Starting with 4G, most major vendors globally converted over to the LTE standard, allowing for far less fragmentation of device compatibility. We're going to be referring to a presentation from the National Institute for Standards and Technology on "LTE Security- How Good Is It?" for a considerable amount of the breakdown of functionality.
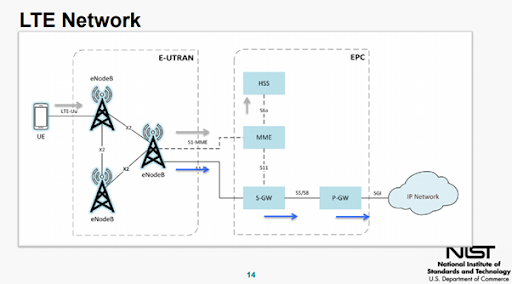
Access to LTE Networks as a rule is provided through a series of mesh-style base stations which send and receive signals from user devices which then forward requests onto a backend core network. The core network itself processes authentication and subscriber services along with connecting users to the rest of the Internet.
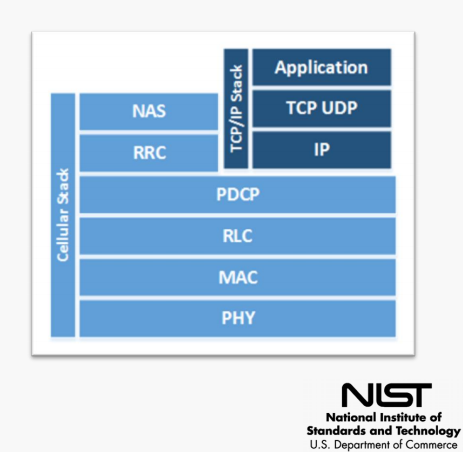
Much like the OSI model, the cellular stack provides connectivity from the physical layer all the way up through application, with TCP/IP doing its own thing and not really lining up properly with the standards. TCP/IP however does sit on top of the packet data convergence protocol (PDCP), which provides header compression and radio encryption.
The IMSI (International Mobile Subscriber Identity) is a unique id for every subscriber. While you might think at first glance that it would just be the user’s phone number, it actually has nothing to do with it. This is usually a 15 digit numeric value stored on the UICC (Universal Integrated Circuit Card), which can be considered a next-gen SIM (Subscriber Identification Module) card. The IMSI contains three separate values- 3 digits comprising the MCC (Mobile Country Code), 2 to 3 digits for the MNC (Mobile Network Code), and then the MSIN (Mobile Subscription Identification Number) from the provider itself.
The UICC operates the same conceptually as a smart card- providing a basis for encrypting communications and authentication. This is far from the only encryption method used for protecting data transfers and calls, as the Authentication and Key Agreement (AKA) protocol is first used to authenticate devices to the network, and only after this has been completed are the crypto keys for encrypting calls generated. As we go up the Cellular Stack, multiple 128-bit and 256-bit keys are used to help protect both internal communications and user traffic.
Once traffic has been received by the base stations from the user, IPsec protects communications on the backend from the base stations to the core network, both of which use PKI certificates to authenticate to each other. Problems come into play however when data has to abide by legacy rules such as the GSM downgrading noted above. This also means that services that exploit elements that cannot be updated or the human factor could still gain access to user data despite strong protections. Let’s quickly go over a few of these Potential Security Issues.
2FA via SMS
Multiple methods have been revealed over the years that allow unauthorized users to gain access to text messages. Sometimes this has been by obtaining access via employees at the cellular provider, 3rd party services that can operate without verification, or malicious apps with elevated permissions.
Because of this, 2FA (2 Factor Authentication) via SMS is considered potentially insecure and exploitable to the point where it is recommended to use any alternative to this system.
Compromised Wi-Fi networks
If a user connects to a compromised Wi-Fi network, most of the protections on the Cellular Network will not apply because it's not being used. Making sure that Wi-Fi is turned off whenever leaving a safe area is critical for users to avoid accidentally connecting to a network that they don't want to.
Out of support devices
The supported lifetime for most mobile devices is significantly less than that of their desktop or laptop counterparts. This means that security updates may possibly stop being received by user devices just a few years after the initial release of the device. If users continue to use these devices long after this date, they run the risk of having their devices exploited through any number of means.
While purchasing new devices and moving over to them can be difficult, the benefits outweigh the potential costs.
App leaks
App developers do not have unlimited resources. They put together a product, ship it out and try to get it approved and on their respective stores as quickly as possible. This means that some legitimate apps may have higher than intended permissions, which would give them access to a significant amount of non-essential data, but without adequate protections for that data because they didn't need it in the first place. Because of this, other apps that have been installed may be able to sniff around for this information and send it off to third parties.
Being careful about what apps we permit on our devices and regularly updating the ones we do have are both excellent ideas. What we can also do though is audit App Permissions on a regular basis and see what apps have been granted which permissions. Removing permissions from apps may cause unexpected errors, but least privilege is worth investigating when it comes to sensitive information.
Social engineering
Social Engineering in the modern age can involve sending SMS messages, emails, phone calls, browser popups, full screen ads and more to users with prompts ranging to polite requests to threatening legal action if they don't do some specific action. This could potentially convince users to give whatever information they are being asked for to a 3rd party that definitely should not have access to it, and cost them dearly as a result.
Some protections have been built into Mobile OS's already, along with spam protection and caller id's flagging potentially suspicious numbers. These bad callers can then be sent to voicemail directly without the user having to deal with it.
Learn Network Security Fundamentals
![]()
Conclusion
Cellular Networks are vastly improved compared to where they were years ago, and are continuing to become better as we move into 5G and beyond. These protections though only go so far however, and we still need to remain vigilant for threats that can that use this network to spread, or bypass it entirely.