Top 10 Endpoint Security Trends in 2019
The Shodan search engine is an excellent resource for hackers looking for unprotected endpoints. If you have ever played with Shodan, you will probably know that some of the most popular searches are the searches for unprotected devices using default logins for usernames. At the time of writing, there were 6,630 routers out there which used the login credentials of username=admin / password=1234.
While there were similar resources and alternative software producing similar results before Shodan came along, the search engine has received a lot of publicity and media attention, making non-techies more aware of endpoint security.
Learn Network Security Fundamentals
What Is Endpoint Security?
An endpoint is simply one end of a communication channel – e.g., a laptop, desktop, wireless router, smart phone or network server. When we talk about endpoints we are usually talking about Internet-connected hardware devices, but even a URL in an API is an endpoint through which a client interacts with a server’s resources. The seemingly innocuous endpoint is the Achilles heel of cybersecurity and vulnerable to attack, as it is often a convenient entry point to a system where criminals can execute their malicious code and gain access to devices and victims’ sensitive data.
Endpoint security is the practice of securing devices against attack from criminals. At its most basic, it is the physical protection of devices in an organization (e.g. ensuring only employees with the proper credentials can access IT equipment.) In cyberspace, endpoint security is about employing complex software to identify system vulnerabilities, protect systems from attack and ensure there are processes in place to patch breaches that do occur.
Endpoint security has evolved over the years from using basic antivirus solutions and firewalls to high-tech, modern solutions that employ artificial intelligence algorithms, advanced automation technologies and predictive analytics software. These new security solutions use highly-skilled security professionals (including ethical hackers) to secure system perimeters.
In this article, we will look at the top trends in endpoint security today and point to some resources to help your business mitigate endpoint vulnerability risks.
The Evolution of Endpoint Security
The imperative for organizations to invest more in cybersecurity in terms of more sophisticated technology and more specialized labor is a response to multiple factors, including:
- Increasingly sophisticated cyber-attacks by criminals at huge cost to businesses
- Attack latency when attackers leave undiscovered calling cards, the equivalent of unexploded landmines, at digital crime scenes
- Growth in the sheer number of networks, devices and software applications, and a demand for them that creates a bigger target market for criminals
- Pace of development and pressure on developers to quickly produce more sophisticated software for tech-hungry users, with possibly less focus on best security coding practices
- Large number of vulnerabilities that continually need to be patched, with suppliers and vendors barely able to keep up-to-date with plugging holes let alone implementing brand-new security systems
Top 10 Endpoint Security Trends in 2019
1. WiFi endpoint security
WPA3 has recently been released. While it does harden wireless security, the impetus to develop it was in large part due to the discovery of the KRACK vulnerability. There is no documented evidence of a KRACK attack in the wild, but organizations need to address potential risks for Wi-Fi devices before they are breached.
2. Tanium peer-to-peer network and natural language search
Touted as the Google of endpoint security, the Tanium security interface provides an integrated single-source solution that connects an organization’s teams, systems and endpoints. It provides a consolidated view for stakeholders as diverse as DevOps teams and business leaders. The platform’s complexity is transparent to users, in no small way due to the use of natural language searching, allowing users to quickly and easily query big endpoint data.
3. Machine learning and AI
As the number of endpoints increase, so does the amount of big data that needs to be secured. Humans simply cannot cope without complex security automation that can intelligently predict and block attacks. There is a growing need for human automatons, however, who can follow up the false positives and false negatives that robotic analysis may produce.
451 Research found that “many efforts in the past year have been directed to build up capabilities in endpoint threat detection and response (EDR), to detect and hopefully contain and defeat increasingly sophisticated attacks that find their way past preventive measures.” A product like Webroot® Threat Intelligence Platform claims to scan 95 percent of the Internet three times a day to detect potential new threats and protect against them proactively.
4. Exaggerated security claims and informed customers
Even a cursory trawl of vendor sites offering endpoint security solutions is confusing to potential customers; each apparently offers the complete security that, for some unexplained reason, their competitors do not. 451 Research warns: “The industry keeps evolving, and the days of ‘legacy vendors only do signatures’ or ‘next-gen vendors are one-trick ponies’ are long gone. Playing to a customer’s lack of information about the trends is bound to fail as information becomes plentiful.” As with all new technologies, there is a steep learning curve. In time, customers will become more circumspect about endpoint security claims and more knowledgeable shoppers.
5. Fileless attacks
Fileless attacks are increasing, warns security specialist McAfee, and are most often directed at Microsoft PowerShell. The best protection is keeping your software up-to-date.
6. Reduced trust in antivirus solutions
According to a study by Barkly and Ponemon Institute, four out of five organizations replaced or improved on their antivirus solution in 2017.
7. Ease of use and consolidation
A growing trend in endpoint security, as evidenced by Tanium, is simplicity. A report produced by 451 Research on behalf of Barkly predicts an increasing demand for solutions that “can show effective security results in the real world while simplifying operational aspects.”
8. Sophisticated analysis techniques
Sophisticated analysis techniques focusing on endpoint behavior on millions of devices play an important role in security and help to detect attack behaviors and identify endpoints participating in dangerous actions.
9. Behavioral authentication
Instead of traditional passwords, behavioral authentication can be used to more reliably identify endpoints.
10. The way staffing structures are organized
The way staffing structures are is changing. There is a rise in the employment of specialized security professionals, like computer forensics experts, white-hat hackers and penetration testers. A study by the Ponemon institute (The 2017 State of Endpoint Security Risk) found that "In addition to failing to stop new attacks, many existing endpoint solutions are also putting an untenable strain on staff, resources, and overall productivity."
Help! The Cost of a Professional Security Solution
Basic Solution Costs
The pressure to stay ahead in the endpoint security game can be costly and resource-intensive. If you shop around, you should be comparing annual license fees for a package that covers a single endpoint, protects most types of devices (from servers to smart phones) and includes a combination (preferably all) of the following:
- Advanced malware detection
- Smart scanning and use of behavioral heuristics to detect zero-day threats
- Central management console with complete organization visibility
- Hardware layering technologies
- Learning intelligence that continually refines threat classifications
- Dynamic whitelisting
- Automatic sandboxing of suspicious executables
- Protection across files, apps, messaging, browsers, internal and external networks, URLs and more
Vendors are often shy to advertise their prices online, and sometimes their prices vary, but to give you an idea of what comprehensive endpoint security might cost you:
- McAfee’s Complete EndPoint Protection Enterprise + 1 Year Gold Business Support is $39.99 (per node) from CDW. The license is based on volume usage and is suitable for 251-500 users. The price goes up to $89.99 for 101 to 250 users
- Webroot’s SecureAnywhere Business Endpoint Protection – $30 (per endpoint with a 5-endpoint minimum, which makes this solution $150)
Staffing Costs
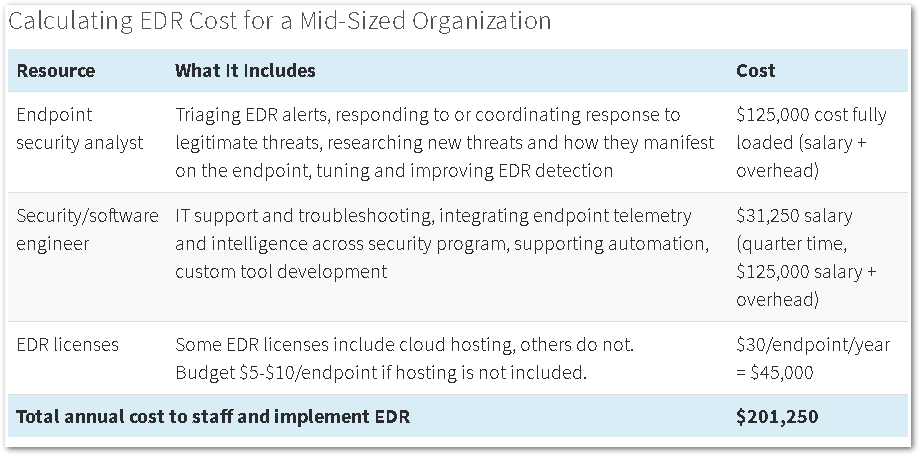
Red Canary has taken a stab at calculating the cost of implementing EDR (Endpoint Detection and Response) at a mid-sized company.
Source: Red Canary
The company stresses this only buys you basic EDR capability. You may also need to invest in additional staff – threat researchers, threat hunters (at a salary of between $95,000 and $145,000 a year, according to Indeed, and quite rare on the ground), incident responders, data scientists and endpoint specialists ($75,000 to $140,000 a year, according to Indeed) – and software, e.g., Security Information and Event Management (SIEM) software.
Endpoint Security Awareness
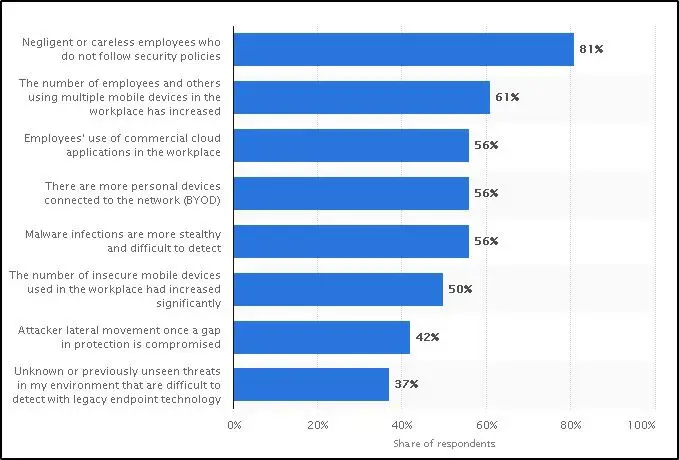
A survey of 694 IT and security professionals in 2016 indicated that employees using multiple mobile devices in the workplace were one of the biggest threats to endpoint security. The biggest threat, though, was negligent employee behavior when it came to following organizations’ security rules and procedures.
What are the biggest threats to endpoint security in your organization? (Source: Statista)
Security awareness is vital for all echelons in an organization, from the cleaner to the CEO. InfoSec Institute’s SecurityIQ offers free awareness training that will give staff a new perspective on how vulnerable the endpoints they use can be.
Before you go, look on the lighter side and share some tips for your developers from OWASP on how to write insecure code.
Learn Network Security Fundamentals
Sources
- Shodan
- Cybercrime costs business over 2 trillion, Juniper Research
- Two Remarkable Cyber Security Companies to Join in 2016, Medium
- Security, Wi-Fi.org
- Asking questions, Tanium
- Meet Tanium, The Secret Cybersecurity Weapon Of Target, Visa And Amazon, Forbes
- 2018 Trends in Information Security, 451 Research
- Webroot® Threat Intelligence Platform, Webroot
- McAfee says fileless cyber attacks are on the rise, Cybersecurity Insiders
- 3 Key Findings from the Upcoming 2017 State of Endpoint Security Risk Report, Barkly
- The push toward comprehensive endpoint security suites, CSO Online
- Endpoint Security – Most Enterprises May Be Wasting Money on Ineffective Solutions, Comodo
- The 2017 State of Endpoint Security Risk, HubSpot
- What’s the Cost of Endpoint Detection & Response?, Red Canary
- Senior Cyber Hunter jobs, Indeed
- Endpoint Staffing jobs, Indeed
- What are the biggest threats to endpoint security in your organization? Statista
- How to write insecure code, OWASP
- SecureAnywhere Business Endpoint Protection, Webroot
- Complete EndPoint Protection Enterprise + 1 Year Gold Business Support and Complete EndPoint Protection Enterprise + 1 Year Gold Business Support, McAfee