Web server security: Active defense
Introduction
Active defense is an approach taken to prevent attacks from adversaries. In this article, we discuss the various active defenses and countermeasures that can be enforced in an attempt to prevent web server and web application attacks by adversaries. These countermeasures will include tools that you can use to protect your web servers from adversaries on the internet.
Learn Web Server Protection
Overview
Active defense is a term borrowed from security defense to be used. It refers to the actions and steps taken to achieve an advantage over an adversary. When seeking active defense, we look for ways of confusing the adversary or even wasting their time so much as to allow us enough time to properly configure our defenses and thwart the adversary.
The following are some countermeasures that can be put in place:
- Configuring a honeypot to waste an adversary’s time
- Installing an alert system that can alert you to attacks
- Configuring firewalls to detect and block attacks
The intention of the countermeasures above can be to achieve the following:
- Waste the adversary’s time
- Trap the attack to prevent further compromise
- Inform security teams concerning attacks
- Assist in discovering the source of the attack
If active defense is properly executed, then it will be able to thwart the attacker’s campaign plan. Remember, the hacking process begins with reconnaissance, where the attacker attempts to collect as much information on the target as possible. When we limit the hacker’s success within this phase, they are most likely to give up.
Let’s consider a few resources that can come in handy when performing active defense.
Honeypots for web server security
Honeypots can be configured to work as fake services on web servers. The intention is to trick attackers and even alert security personnel concerning incoming attacks.
The following are some tools that can be configured as honeypots:
- OpenCanary: This solution runs a daemon of several canary versions of services which will report when these services are either connected to or abused
- WebTrap: This tool allows security teams to clone existing login web pages (portals) and redirect visitors away from real pages
- HoneyBadger: This tool takes a geographical location of where the attacker is located and can be used to attribute the attack to an attacker
- BeeF: This framework can be used to “hook” the attacker’s web browser with the intention of discovering the activities which the attacker does on their browser
There are many honeypots that security teams can use on their web servers for active defense. A list of the various honeypots, listed according to their categories, can be found here.
WebLabyrinth for web server security
WebLabyrinth is a tool used to create multiple bogus web pages that can throw an attacker off during a web attack. These web pages are intended to delay a web scanner so that security teams can detect the ongoing scan and block it before any sensitive files can be accessed or scanned. In theory, you can install this tool to confuse the adversary; unfortunately, it is largely outdated and might not work very well with today’s technologies.
fail2ban for web server security
fail2ban is an intrusion detection framework that can be used to protect web servers from brute-force attacks.
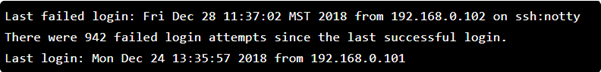
Consider the times you have attempted to login to login to the SSH service and you failed. You most likely received the following error:
In the error above, we can see that the login attempt was unsuccessful due to a couple of login attempts. In this case, 942 attempts to login were made. This many attempts indicates the likelihood of a brute-force attack. We prevent such attacks by installing fail2ban.
We will be installing fail2ban on an Ubuntu 16.04 server. The installation steps can be followed below:
- $ apt-get update
- $ apt-get install fail2ban -y
- $ sudo service fail2ban restart
- $ sudo service fail2ban status
Once it is running, you should be able to see “active (running)”.
You can configure fail2ban by following the steps outlined here. Once the configuration is complete, you can then run fail2ban.
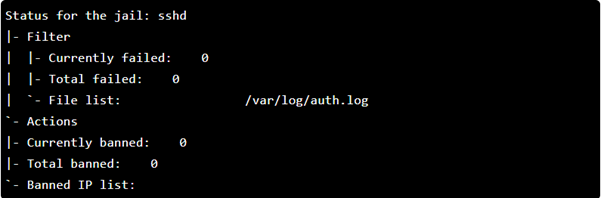
You can view the status of fail2ban by using the command shown below. This will also show you the currently configured jails:
As can be seen below, there is only one jail, for SSH.
We can also view more information on the configured jails. The following is the command used to probe configured jails.
Since we do not yet have any blocked IPs, the following output is received:
Let’s now attempt to log in but deliberately fail a couple of times. In this case, we make five wrong logins. See the login attempts below.
When we assess fail2ban, we can obtain this information:
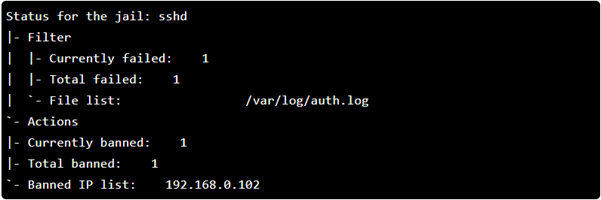
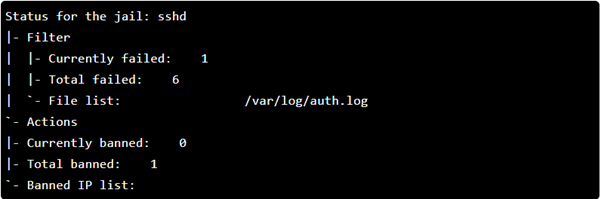
We can see above that fail2ban blocked one IP address after multiple failed login attempts.
Whitelisting banned IP addresses is simple. You simply need to issue the jail name and the banned IP:
The IP above becomes unbanned after the whitelisting. We check the server status once more and are met with the following:
From the screenshot above, we can see that there are six failed login attempts and one total banned IP.
Active response with fail2ban
fail2ban can be configured according to your wishes and preferences. The procedure is simple and straightforward.
First of all, you need to create the file “jail.local”. When you launch fail2ban, it will go ahead and load it. To create this file, use the command below:
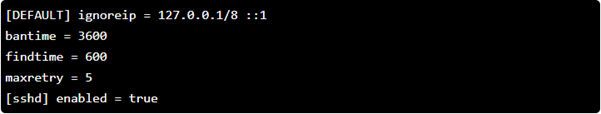
You will then need to edit the file and add the following contents, or at least make it look similar.
The first line tells fail2ban to ignore the localhost on both IPv4 and IPv6. The second line specifies the bantime. This is the amount of time in seconds upon which a violating IP address must be banned. In this case, it’s 3600 seconds, which is one hour.
The third line specifies the findtime, which specifies the time within which wrong attempts are issued. In this case, 600 seconds is five minutes. In five minutes, if invalid login attempts are made, the violating IP will be blocked for one hour.
The fourth line specifies the maxretry, which is the maximum number of retries of login attempts. In this case, only five attempts are allowed before a ban is issued.
The last line specifies the jail. In this case, we are monitoring SSH. It is important to note that you can monitor various protocols here on your web server.
Conclusion
Active defense is an important technique that, if implemented properly, can help secure your web infrastructure and prevent further attacks.
The tools discussed have introduced the active defense concept, but our exploration has been by no means exhaustive. We therefore encourage you to attempt to identify any tools with similar functionalities and determine which tools work best for you. We hope the concepts covered will be beneficial in helping secure your servers.
Learn Web Server Protection
Sources
- How to Install and Configure Fail2ban on Ubuntu Server 16.04, Liquid Web
- weblabyrinth, GitHub
- opencanary, GitHub
- WebTrap, GitHub