University of Manchester hack and Honda API flaws
The University of Manchester says data was likely stolen in a cyberattack, Honda API flaws expose sensitive customer information and Asylum Ambuscade’s espionage activities. Catch all this and more in this week’s edition of Cybersecurity Weekly.
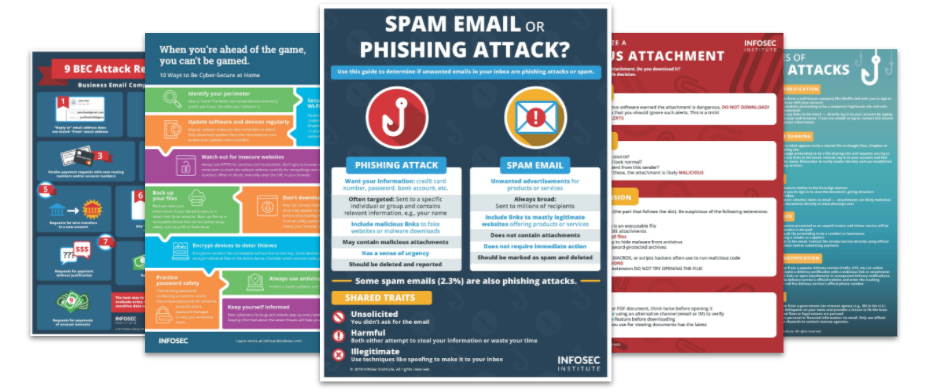
Top Security Awareness Posters
1. University of Manchester suffers a data breach, says information ‘likely’ stolen
The University of Manchester has issued a warning regarding a cyberattack that led to unauthorized access to some of their systems and likely data theft. The breach was discovered on June 6th, prompting an ongoing investigation by internal and external experts. Relevant authorities, including the Information Commissioner's Office and the National Cyber Security Centre, have been notified. The university has expressed regret over the incident and is dedicating all available resources to resolve the issue.
2. Honda e-commerce API vulnerabilities exposed customer and dealer data
Honda's ecommerce platform used for equipment sales suffered serious vulnerabilities that could have exposed customer and dealer information. Discovered by researcher Eaton Zveare, the flaws allowed unauthorized access to customer orders, names, addresses, and phone numbers. Zveare also identified the potential modification of over 1,500 dealer sites and the acquisition of private keys for payment services. Although Honda promptly addressed the issues, the company doesn't have a bug bounty program and didn't reward the researcher. Additionally, no evidence of malicious exploitation was found.
3. Asylum Ambuscade hackers combine cyber heists with espionage
Researchers have linked a series of APT-like espionage activities and financially motivated attacks to a cybercrime group named "Asylum Ambuscade." ESET analysis reveals that the group has been active since 2020, conducting spear-phishing campaigns against European government staff and targeting bank customers and cryptocurrency traders through malicious Google Ads. The compromise chains and malware variants used in both attacks (AHKBOT and SunSeed) are remarkably similar. While the group's motivations and affiliations remain uncertain, researchers emphasize the need to monitor their activities closely.
4. Cybercriminal using new PowerDrop malware to target U.S. aerospace
An unidentified threat actor has targeted the U.S. aerospace industry with PowerDrop, a newly discovered PowerShell-based malware. PowerDroputilizes advanced evasion techniques, including encryption and decoding. Acting as a post-exploitation tool, it gathers information from compromised networks. The malware then communicates with a command-and-control server using ICMP messages and executes PowerShell commands via the Windows Management Instrumentation service. Despite its basic nature, PowerDrop demonstrates the ability to evade endpoint defenses, suggesting the involvement of more sophisticated cybercriminals.
5. 60K+ Android apps spread adware for months without detection
Romanian cybersecurity firm Bitdefender has uncovered a staggering 60,000 Android apps that have been silently infecting mobile devices with adware over the past six months. Using its anomaly detection feature, the firm warns that these malicious apps are disguised as legitimate applications and primarily target users in the United Kingdom, United States, South Korea, Germany, France, and Brazil. The apps are distributed through third-party websites and employ stealthy installation techniques to evade detection. While currently displaying ads, they have the potential to carry more dangerous payloads such as banking Trojans or ransomware.
Phishing simulations & training






