NIST CSF: The NIST CSF components
Introduction
The National Institute of Standards and Technology (NIST)’s Cybersecurity Security Framework (CSF) consists of three main components. They are:
- Implementation tiers
- Framework core
- Profiles
These CSF components can help both governmental and non-governmental organizations to improve their critical infrastructure cybersecurity. It provides the basic knowledge required to understand the additional online learning pages of the Framework.

Get NIST CSF training
According to the White House’s Executive Order – Improving Critical Infrastructure Cybersecurity (2013), “the term critical infrastructure means systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters.”
This article will serve as a brief but comprehensive overview of all NIST CSF components.
NIST CSF: Implementation tiers
The NIST CSF isn’t designed to be used by every organization as it is. This is because every organization has unique risks, varied risk tolerances and different threats and vulnerabilities that will influence how the guidelines of the framework are implemented.
Moreover, implementing the NIST CSF in an identical manner will also affect large and small organizations. For example, large businesses may already have various security measures in place that will overlap with those of the framework. Likewise, small organizations may have fewer channels for potential data breaches and their data security processes are at the beginning stage.
In order to meet the varied security requirements of different organizations, NIST CSF implementation tiers elaborate the degree to which their cybersecurity risk management practices exhibit the characteristics described in the NIST CSF.
The four implementation are listed below:
- Tier 1 (Partial)
- Tier 2 (Risk-Informed)
- Tier 3 (Repeatable)
- Tier 4 (Adaptive)
These tiers help organizations consider the appropriate level of rigor for their cybersecurity program, how effectively cybersecurity risk decision is integrated into the broader risk decisions and the degree to which the businesses share and receive cybersecurity information from third parties.
Each NIST CSF implementation tier is further broken into three main components:
- Risk Management Processes
- Risk Management Program
- External Participation
NIST explicitly states that these tiers aren’t maturity levels. The higher the tier, the better a business’s risk management practices match those stipulated within the NIST CSF.
NIST CSF: The core
According to the NIST, the Framework Core is a collection of cybersecurity activities, applicable references and the desired outcomes that are prevalent across the critical infrastructure sectors. This essential element of NIST CSF presents best practices, guidelines and industry standards in a manner that enables communication of cybersecurity outcomes and activities across the enterprise, from the executive level to the implementation level. In addition, the Framework Core provides a high-level, strategic view of the life cycle of the business’ management of cybersecurity risks.
The NIST CSF Core consists of five functions: Identify, Protect, Detect, Respond and Recover. These functions are applicable to both cybersecurity risk management and cybersecurity risk management at large.
The next level down is divided into 23 categories. The deepest level of abstraction in the Core contains 108 subcategories. These are outcome-driven statements that are used to create or improve cybersecurity programs.
The core functions are supported by informative references that are broader and more technical than the NIST CSF itself. Examples of these references include ISO, ISA and COBIT.
NIST CSF: The Profiles
Once you’re done with the NIST CSF CORE, you need to achieve its desired outcomes. This is where the Framework Profiles come into place.
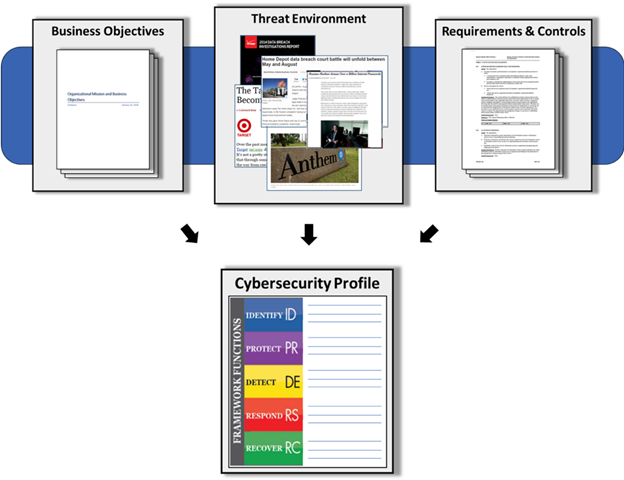
Framework Profiles are a business’s unique alignment of its organizational objectives and requirements, resources and risk appetite in the face of desired outcomes of the NIST CSF Core. Doing this can help you find opportunities to strengthen the cybersecurity defense of your businesses by compartmentalizing a “Current Profile” with a “Target Profile.”
Once you’re able to identify the gaps between the two through gap analysis, you need to create an implementation plan and budget need to beef up your cybersecurity posture. The image below shows an example of the NIST CSF Profile. [CLICK IMAGE TO ENLARGE]
(Source: NIST)
Conclusion
In this article, we’ve explored NIST CSF components, which include implementation tiers, Framework Core and Profiles. You can see how such components can be used to enhance critical infrastructure cybersecurity in organizations.
Sources
An Introduction to the Components of the Framework, NIST
NIST Cybersecurity Framework: A cheat sheet for professionals, TechRepublic
Executive Order -- Improving Critical Infrastructure Cybersecurity, obamawhitehouse.archives.gov
The NIST Cybersecurity Framework Implementation Tiers Explained, Security Boulevard
THE NIST Cybersecurity Framework Implementation Tiers (Part 2 of 3), Twinstate Technologies
NIST Cybersecurity Framework Core Explained, CyberSaint Security
What is NIST? The Complete Guide to the NIST Cybersecurity Framework, FTP Today

Get NIST CSF training
Implementing cybersecurity with NIST Cybersecurity Framework and COBIT 5, ISACA