CA Installation and Use in Windows 10
Certificates issued by a Certificate Authority (CA) have a wealth of uses in Windows 10, but in order to make use of those benefits, we need to first get the certificate installed. This means obtaining a certificate file from any number of CA's — whether they be public on the Web or a private CA on our local network.
In order to obtain a certificate that can be used on your domain, such as an SSL certificate for a secure website, we would first need to generate a Certificate Signing Request (CSR).
Learn Windows 10 Host Security
![]()
What is a CSR?
A CSR is a standardized way to send data about the system you are working on up to your Registrar- typically the domain in question, location information, key size and key type. There are multiple ways to create a CSR — in fact, many Registrars have their own utilities to create a CSR for you.
Alternatively, if you have a local CA Server operating in your network, you may be issued a certificate automatically based on Active Directory policies. Microsoft’s official documentation for Installing Active Directory Certificate Services can be found here, while their documentation for completing auto-enrollment can be found here. Please note in both cases you will need to be running a Windows Server operating system for implementation.
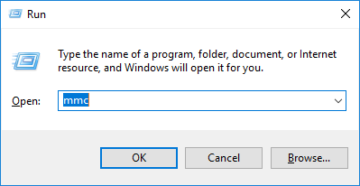
However, if you need to create a CSR manually, install your certificate once you have received it, or just want to view the certificates you currently have installed, we will want to open up the Certificates Snap-In in Windows 10 available via the Microsoft Management Console (MMC). We can do this by holding down the Windows Key + R, and type in 'mmc'.
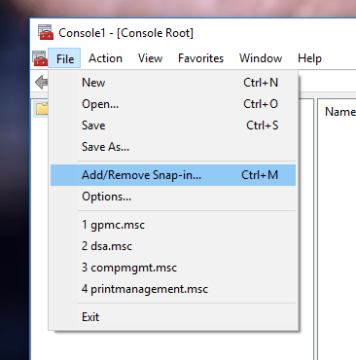
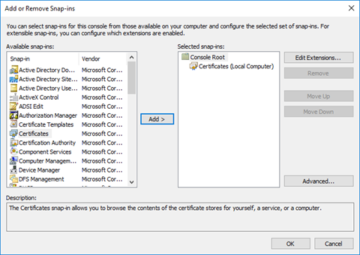
For anyone that has not used the MMC before, it is what powers various areas such as Computer Management- which is one of the most powerful utilities at our disposal in Windows. Once the empty shell has appeared, we will want to go up to the File dropdown menu and select 'Add/Remove Snap-in'.
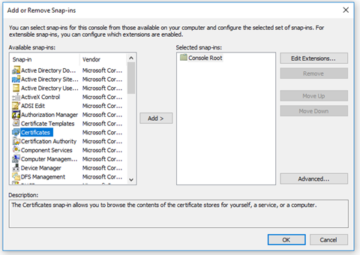
Depending on how your system is configured, you may have access to an enormous number of possible snap-ins, but the one we are going to be looking at right now is just the 'Certificates' snap-in.
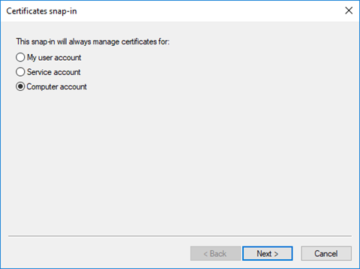
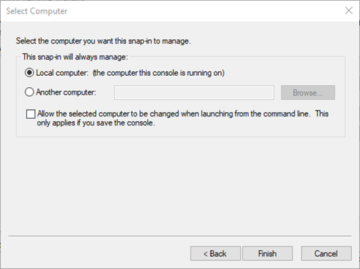
When we have clicked on 'Certificates', we will then want to click on the 'Add' button. This is a location that determines the context for our certificate- if we are obtaining/installing on a user, we will want to click on 'My user account'. Since we are obtaining/installing one for the system we are on, however, we will want to select 'Computer account' followed by 'Next'.
For this example we want to install the SSL certificate onto this computer, so we'll just keep it on 'Local computer' and then select 'Finish'.
This will bring us back to the Snap-ins selection screen where we can see how MMC is currently configured, after which we can click 'OK' to bring us back into the main program.
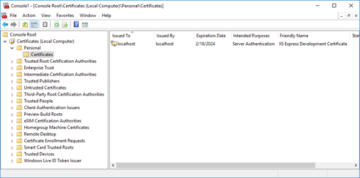
Once we are in the Certificates (Local Computer) snap-in, we will see a tree view of many different categories of Certificates. In this case, because we are dealing with identification for the server, we'll want to drill down into the 'Personal' category, followed by 'Certificates'.
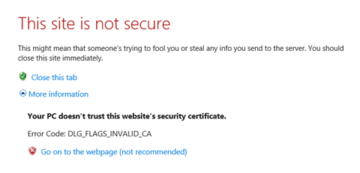
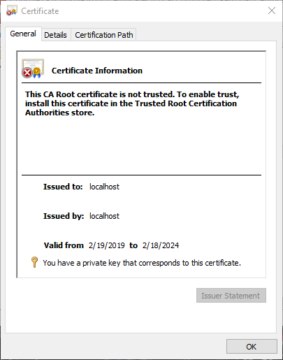
This will show us any certificates that have already been applied, including self-signed certificates. Self-signed certificates are generally not trusted by default on any systems other than the one that created it, and will generate an error upon navigating to them such as the one shown below.
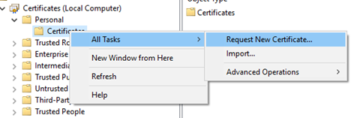
If we need to create a CSR in Active Directory, we'll want to right-click on either 'Personal' or the 'Certificates' immediately below that, select 'All Tasks', and finally click on 'Request New Certificate…'.
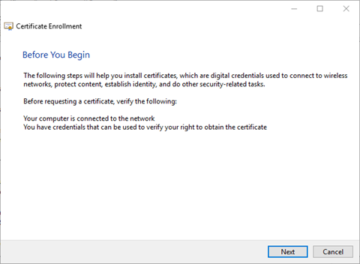
We will then be brought into the Certificate Enrollment wizard, which we can continue on with by clicking on 'Next'.
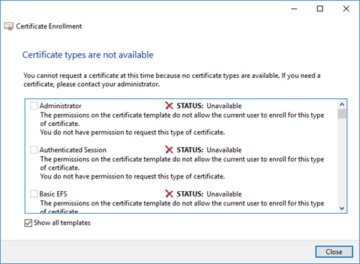
Beyond this point, you will see various enrollment methods that have been already configured for your environment through the use of Certificate Templates, or you can click on 'Add New' to manually go through an enrollment procedure as instructed by your Registrar. If we continue on through AD enrollment and it has not been configured yet, we will either see a blank screen or if we click on 'Show all templates', we will see the screen below.
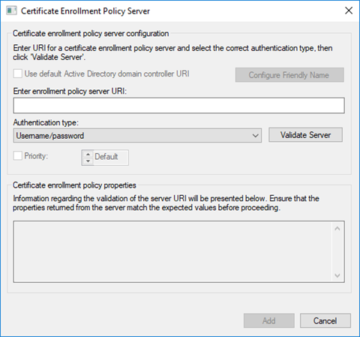
If on the other hand we click on 'Add New', we will be prompted to enter the location for the server we need to communicate with, along with a request for the type of authentication we will need to use for verification.
Importing certificates
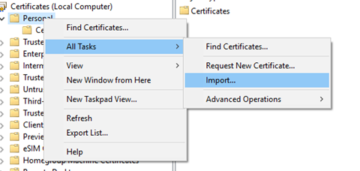
Whatever the means we use, if we need to install the certificate file ourselves, we will want to once again right-click on 'Personal', select 'All Tasks', then click on 'Import'.
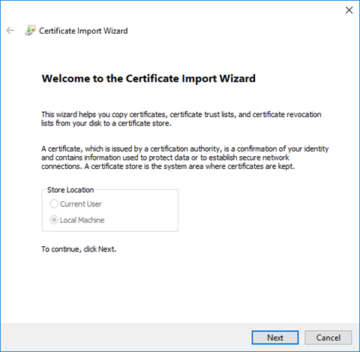
We will then be prompted by the Certificate Import Wizard, which we can get started on by clicking 'Next'.
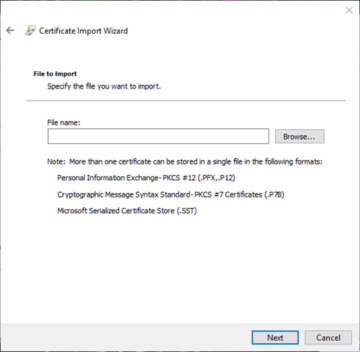
You'll be asked to provide the certificate, which can be one of many different file types as supported- not just the ones listed below, however if it is not a .PFX file your usage may be limited, as this archive can store multiple entities in a single file. Click on 'Browse' to navigate to your file.
After selecting your certificate, you may be prompted to enter a password that has been used to secure the file from being deployed onto unauthorized systems. After this has been completed, however, your certificate will be ready for use.
Double-clicking on the certificate will bring up the traditional view you may be used to if you have looked at certificates before in various web browsers.
You will be shown who it was issued by, the scope of the certificate, and its dates of validation. Please note that certificates have both start and end dates- which can be very important during the addition and removal of certificates during renewals.
Using an SSL Certificate
Now that the certificate has been installed on our system, we can continue on to the next step of pairing the certificate with a secure website on our system. To do that, we will want to go to 'Start', 'Control Panel', 'Administrative Tools', and finally 'Internet Information Services (IIS) Manager'.
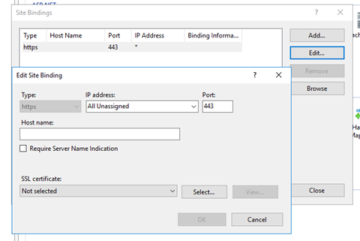
When we open up IIS, we'll want to drill down through 'Sites' and then click on the specific site we want to use the certificate for. Once we click on that site, we will want to click on 'Bindings' on the right side of the screen. Bindings shows us the exact URL's and IP addresses being used for the particular site we are working with. We'll want to click on the Binding in question and select 'Edit' to bring up the details screen.
In order to use a certificate for the site, we'll need to make sure that we are using HTTPS, and traditionally port 443. At the bottom of this screen, we will then see a dropdown menu to select our SSL Certificate. Once chosen, we can click on 'OK' and 'Close' to leave this area.
Certificates are incredibly versatile pieces of technology and useful for many different purposes. Having a reliable and trustworthy CA infrastructure is critical in a number of different applications, along with making sure that your certificates are always valid and up to date. If a certificate suddenly expires without being renewed beforehand, this can cause both user confusion and communication interruptions. It is vital therefore that we stay ahead of the curve when it comes to both maintaining our certificates and keeping track of where they have been installed in our environments.
Learn Windows 10 Host Security
![]()