Data execution prevention (DEP) in Windows 10
Does this sound familiar?
"Sorry, not on the list." "Oh come on! I was just in there five minutes ago! I just need to go get my coat." "Not on the list." "Okay." Five minutes later: "Still not on the list." "Oh come on, I spent like twenty bucks on this hat!" "Not. On. The. List."
Learn Windows 10 Host Security
Data execution prevention (DEP) is like a bouncer for a very exclusive club. If you're on the list, you can use that area as you like. You gain access to resources that you would not otherwise have and certain things are allowed to happen there that are protected from outside interference. But if too many people try to get in at once or if unauthorized people get in, it can potentially cause major problems.
Many operating systems have reserved memory areas that they run critical functions and programs in. This memory is limited, however, and if something isn't written correctly or something nasty gets in there that starts taking up far too much space, you end up with a buffer overflow situation. That may not sound bad at first, but it can give access to potentially critical data to programs and users that should not have access to it.
Fortunately, Windows 10 has protection for this area is enabled by default and must be disabled manually by the user if they wish to turn it off. We'll be going over what makes DEP important, why it should be kept on if at all possible, and if necessary how to disable it.
What is data execution prevention?
DEP, also known as executable space protection in more neutral terms, marks specific memory regions as non-executable. If something tries to execute code in those areas, it will throw an error. There are two different methods of creating this sort of protection: one hardware-based that produces very little overhead, or a software version of the same principles that can potentially cause some noticeable overhead.
Windows has had DEP available since Windows XP Service Pack 2 and Windows Server 2003 Service Pack 1, which at first was only designed to protect critical Windows Services. Over the years however, support for it grew and added in additional features such as Address Space Layout Randomization (ASLR) — a technique designed to prevent attacks from exploiting memory corruption vulnerabilities. It does this by shuffling around the locations used for different parts of processes, making it significantly more difficult for attacks to get the whole picture of what a program is doing.
Viewing DEP status in windows 10
To view if DEP is currently active on your system, you can click on Start and type in "View Advanced System Settings".
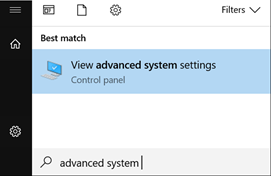
After you have brought up this screen, under the Performance section, click on Settings.
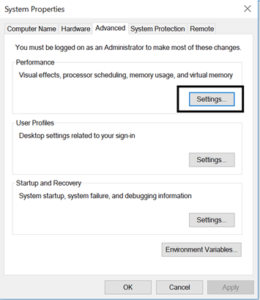
When the Performance Options screen appears, click on the Data Execution Prevention tab to bring up DEP settings.
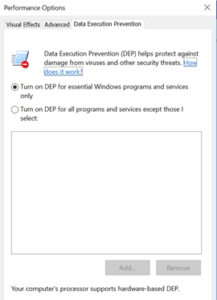
This will show you the current status of DEP on your system, as well as whether or not your hardware supports DEP on top of the Windows software implementation.
This also gives you the option to add in exceptions to DEP if required, but this should only be done if there are no other alternatives. You do this by clicking on the Add button as shown above and select the executable file that you need to exclude. Once this is done, you will need to restart Windows for it to take effect.
Disabling/enabling DEP
Like most Windows settings, DEP can be disabled if the user requests it. It cannot be disabled through a GUI interface at the present time, however, so the user must use the command line. Before we go through the steps on how to do this, why would someone want to disable this particular function?
One of the biggest strengths and weaknesses in Windows is its legacy — its ability to run applications written over two decades earlier. In the case of 64-bit applications, for example, most of these were created after DEP was implemented and would have been compiled with DEP in mind. 32-bit applications or old drivers not intended to be used on modern operating systems, on the other hand, may require additional modifications or exceptions in order to be used on Windows 10. This is especially true of applications designed to run code in emulation — programs that were originally meant for hardware or software that is long since out of date.
I must again stress just how much this is not recommended.
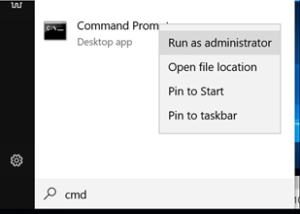
In order to disable DEP, you must first launch an elevated command prompt by clicking on Start and typing in CMD. Right-click on Command Prompt and select Run as Administrator.
Once at the command prompt, type in the following: BCDEDIT /SET {CURRENT} NX ALWAYSOFF
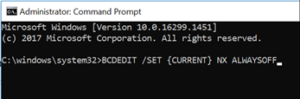
After pressing enter, Windows will acknowledge the change but will only take effect after a reboot. Please note that in certain instances, a BIOS setting will also need to be adjusted in order to disable DEP via this command — you will be prompted if it is required.
If you need to turn it back on after disabling DEP, go back to an elevated command prompt and type in the following: BCDEDIT /SET {CURRENT} NX ALWAYSON.
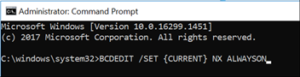
As before, Windows will acknowledge the change after pressing enter and this will only take effect after a reboot.
Conclusion
Data execution prevention is one of the most basic protections a Windows-based system can have, and unless absolutely necessary, it should always remain active. If you are using programs that have been developed to be used on a 64-bit operating system, most have been created with DEP in mind and should be fine. However, if you are required to use legacy code, you may need to create an exception for that specific program.
In any case, DEP should be treated with caution — keeping it at default unless there is a very valid reason to change it. While DEP is important, it is only one aspect of infosec for Windows 10.
Learn Windows 10 Host Security
Sources
- DEP/NX Protection, Microsoft
- DEP, Webopedia
- How To Disable DEP With The Windows 10 Command Line, TechJunkie
- Everything You Need to Know About Windows Data Execution Prevention or DEP, Major Geeks
- How to determine that hardware DEP is available and configured on your computer, Microsoft






