How to use AppLocker in Windows 10
What is AppLocker?
AppLocker is an application whitelisting feature which helps an organization to control what apps and files can be run by the user. AppLocker was first introduced with Windows 7 OS, Windows Server 2008 R2.
AppLocker provides a simple interface to prevent or block an application from running by unintended users. These include Windows Installer Files, executable files, dynamic-link libraries (DLLs), packaged app installers, scripts, packaged apps and so on.
Learn Windows 10 Host Security
AppLocker overview
AppLocker is inbuilt into Windows OS enterprise-level edition and needs no additional installation onto the system. For standalone systems, rules can be enforced using the Local Security Policy editor (secpol.msc). For a group of computers, it can be done using the Group Policy Management Console.
AppLocker rules
AppLocker is capable of blocking different file types. The following are the types of files AppLocker is capable of blocking.
- Executable files like .exe, .com
- Windows installer files like .mst, .msi and .msp
- Executable files like .bat, .ps1, .cmd, .js and .vbs
- DLL executables
- Packaged app installers like .appx
Creating AppLocker rules
The following are the steps to create a rule in AppLocker.
Type local security policy and click “Run as Administrator”.

Under Application Control Policies, right-click on Executable Rules under AppLocker as shown.
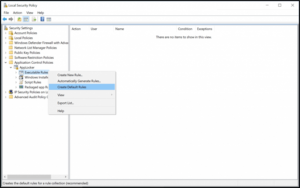
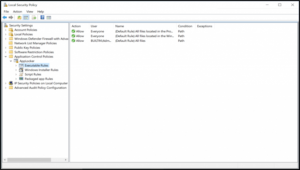
Click on Default Rules. Default Rules get created, as shown below.
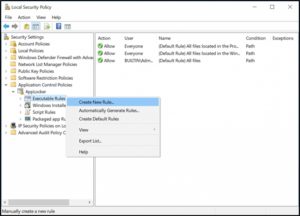
Create New Rule by right-clicking Executable Rules, as shown.
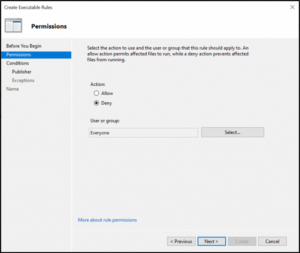
Click Next. Select Deny for denying certain files from getting executed. By default, rules applies to everyone, you can select User or Group as per the need:
Select File Hash, as shown.
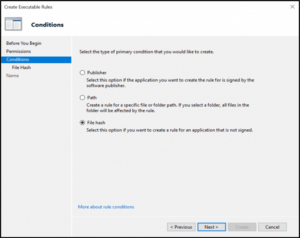
Select Browse Folders and navigate to the path for the executable/file you want to deny execution. We will deny Notepad++ from being executed, as shown.
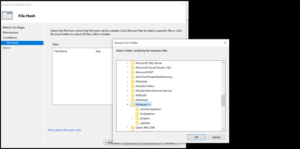
Click OK. Notepad++ Files not allowed to execute get populated, as shown.
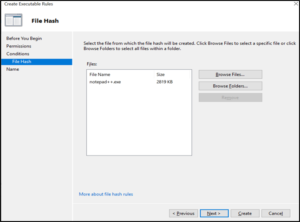
Click Next, give the name for the rule and click Create, as shown.
The rule to block Notepad++ gets created and users are not allowed to execute Notepad++ on the system. Now close Local Security Policy Editor.
That’s how simple it is to use AppLocker to block any file from getting executed.
Learn Windows 10 Host Security
Sources
- What Is AppLocker?, Microsoft
- Use AppLocker to create a Windows 10 kiosk that runs multiple apps, Microsoft
- AppLocker, Microsoft
- How to Use AppLocker to Allow or Block Executable Files from Running in Windows 10, Windows TenForums
- AppLocker in Windows 10 Enterprise, Michael Firsov (WordPress)







