Windows 7 Security Features
Windows 7 is an Operating System developed and released by Microsoft in 2009. It was designed to be a successor to the Windows Vista range of operating systems. Windows 7 builds upon the features and design philosophies of Windows Vista and adds several enhancements along the way.
Windows 7 primarily targets Home/Office users. It was the first Windows operating system to support the 64 bit Intel architecture. Design wise, Windows 7 is very similar to its predecessor Widows Vista, however it does have several enhancements such as Libraries, Jump Lists, etc.
Security in Windows
Windows-based operating systems have always been plagued with a host of security flaws and vulnerabilities, this is mainly because the systems were not designed with secure computing in mind. They are also a popular target for hackers due to these flaws. In today's increasingly connected world we cannot allow our systems to be compromised without dire consequences. Windows 7 has tried to address these issues by following a Secure Development Life Cycle (SDLC), i.e. developers enforced a strict code review of all new code and they performed refactoring and code review of older OS code.
Several of the major security improvements are given below in greater detail.
1. Date Execution Prevention (DEP)
During the execution of a process, it will contain several memory locations that do not contain executable code. Attackers use these sections to initiate code injection attacks. After arbitrary code has been inserted, they can carry out attacks such as buffer overflows. Data Execution Prevention is a security technique that is used to prevent the execution of code from such data pages. This is done by marking data pages as non-executable. This makes it harder for code to be run in those memory locations.
DEP is intended to be used with other mechanisms such as ASLR and SEHOP. When used together, it makes it very difficult for attacks to exploit the application using memory attacks. DEP support, though present in Windows 7, is opt-in, i.e. it is not enabled by default, but users are encouraged to enable DEP support.
DEP can be enabled system wide or on a per application basis. This is configured by the system administrator.
DEP types
There are two DEP implementations:
- Hardware enforced DEP
- Software enforced DEP
Hardware enforced DEP marks all memory locations as non-executable by default unless the location contains executable code explicitly. This helps prevent attacks that try to insert code from non-executable memory locations.
Hardware DEP makes use of processor hardware to mark memory as non-executable, this is done by setting an attribute at the specified memory location. Hardware enforced DEP requires the system to be using a DEP compatible processor. Both AMD and Intel have both released processors with DEP support.
- AMD based processors make use of the NX bit to signify non-executable sections of memory.
- Intel based processors make use of the XD (Execute disable) bit to signify the same.
Software enforced DEP
Software based DEP is less complex than its hardware dependent variant, it also has limited functionality. Software based DEP will run on any type of processor that can run Windows 7. It can protect only a limited number of system binaries.
Software based DEP can help defend against attacks that make use of the exception handling mechanism in Windows 7.
DEP in other Operating Systems
- DEP is found in other operating systems as well, however they mostly make use of hardware enforced DEP technologies. This varies according to the processor used.
- RedHat/CentOS Linux supports DEP through the ExecShield tool. It is enabled by default.
- Sun Solaris supports hardware enforced DEP on NX/XD enabled x86 systems. This setting must be enabled.
- Apple Mac OS X supports DEP on Intel processors using the XD bit, it is enabled by default.
- Android 2.3 and above support DEP
- FreeBSD has supported DEP from version 5.3 onwards
-
OpenBSD supports DEP through a custom implementation called W^X which can be used to mark pages as non-executable by default. W^X makes use of NX bit for its implantation support for XD bit is still forthcoming. W^X has been available from OpenBSD version 3.3 onwards.
2. Address Space Layout Randomization (ASLR)
Address space layout randomization is a technique to increase security from common memory based attacks such as buffer overflows and stack smashing. Older versions of Windows essential system processes often used predictable memory locations for their execution. This made it much easier for attackers to find critical components of the process, including the program stack and heap.
These addresses can then be used to launch buffer overflow attacks. To overcome this problem, ASLR was devised. ASLR randomizes several sections of the program, such as the stack, heap, libraries, etc. This makes memory addresses much harder to predict. Coupling ASLR with DEP makes it extremely difficult to carry out memory based attacks.
In order to use ASLR, programs must be compiled using the ASLR flag, only then will randomization occur during program runtime. Windows 7 completely supports ASLR based applications and libraries. This support will be included in all Windows systems from Windows Vista onwards.
ASLR in other Operating Systems
- ASLR is not restricted to Windows alone, it is found in other Operating systems as well. Linux supports a weaker form of ASLR, but it is present by default.
- OpenBSD has supported ASLR by default since its inception.
- MacOSX supports memory randomization by default for system libraries and applications that have been compiled with ASLR support.
- FreeBSD does not support ASLR fully as of yet, however they are in the process of developing it.
- DragonFly BSD supports ASLR it is based on the OpenBSD implementation.
-
Android 4.0 (Ice Cream Sandwich) supports ASLR to protect memory system and third party applications from memory exploits.
3. Structured Exception Handler Overwrite Protection (SEHOP)
Structured Exception Handler Overwrite Protection (SEHOP) is a technique used to prevent malicious users from exploiting Structured Exception Handler (SEH) overwrites. The SEH overwrite exploit was first demonstrated in Windows XP, since then it has become one of the most popular exploits in the hacker arsenal.
Several exploit frameworks including Metasploit make use of SEH overwrite techniques to execute code remotely. SEH works by subverting the 32 bit exception mechanism provided by the Microsoft operating system.
SEH exploits are generally carried out by using stack-based buffer overflow attacks to overwrite an exception registration record that has been stored in the thread's stack. The exception registration record consists of two records, the next pointer and the exception handler, also called the exception dispatcher. The attacker will try to overwrite the exception dispatcher and force an exception.
There are two methods to stop SEH exploits. The first technique requires the application to compiled using the /SAFESEH flag during the linking phase. This may not be feasible, because it requires the recompilation of the entire application.
The second method is used by SEHOP. Here dynamic checks are carried out to ensure that a thread's exception handler list is not corrupt before actually calling the exception handler.
SEHOP is enabled by default on Windows 7 and Windows 8 operating systems. It can be disabled if required through the modification of registry keys.
4. User Account Control (UAC)
User account control is a security feature first introduced in Windows Vista to limit administrative privileges only to authorized users. If an application tries to perform an administrative action, the user must authenticate before the action is carried out. This is useful, as it prevents malicious files from executing actions with administrative privileges.
UAC works by allowing temporary administrative access to the concerned user if he/she is able to authenticate themselves during the UAC prompt.
There are several actions that can trigger a UAC alert. Some of them are listed below:
- Running an Application as an Administrator
- Changes to system-wide settings or to files in %SystemRoot% or %ProgramFiles%
- Installing and uninstalling applications
- Installing device drivers
- Installing ActiveX controls
- Changing settings for Windows Firewall
- Changing UAC settings
- Configuring Windows Update
- Adding or removing user accounts
- Changing a user's account type
- Configuring Parental Controls
- Running Task Scheduler
- Restoring backed-up system files
-
Viewing or changing another user's folders and files
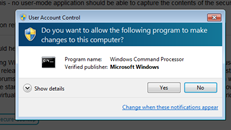
UAC also introduces the concept of Secure Desktop, wherein the entire desktop is dimmed during a UAC prompt, forcing the user to only interact with the elevation window.
Normal applications cannot interact with the secure desktop. This prevents spoofing attacks. UAC is enabled by default, but can be disabled from the Control Panel, but it is not advisable to do so.
UAC is similar in functionality to the sudo command found in UNIX based systems.
5. DNS System Security Enhancements (DNSSEC)
The DNS System Security Enhancements is a set of specifications used to secure information provided by the DNS system. The specification was devised by the IETF (Internet Engineering Task Force). DNSSEC support was first introduced to Windows 7 and Windows Server 2008 R2.
DNSSEC works through the use of extensions to improve upon the shortcomings of the DNS system to provide DNS clients with certain features such as:
- Origin authentication of data
- Authentication
- Data integrity
The original DNS system was not designed with security in mind, this has led to heavy exploitation of DNS systems. DNSSEC tries to add security without sacrificing backward compatibility. DNSSEC makes use of public key cryptography to digitally sign records for DNS lookup. The correct DNS record is authenticated using a chain of trust, which works with a set of verified keys from the DNS root zone, which is the trusted third party.
DNSSEC in other Operating Systems
DNSSEC is supported in many other operating systems.
- BIND, the most popular DNS name server, supports the latest version of the DNSSEC protocol
-
The Google public DNS server fully supports the DNSSEC protocol.
6. Bitlocker
Bitlocker is a Windows security feature that was first introduced for Windows Vista and then further enhanced for Windows 7. It provides full disk encryption capabilities for Windows 7, it is included as part of the operating system itself, and it does not require any third party plugins to function. It is only available for the Enterprise and Ultimate editions of Windows 7.
Bitlocker provides logical volume encryption, i.e. the drive to be encrypted must be partitioned into logical volumes for Bitlocker to work. Bitlocker requires at least two NTFS volumes, one for the OS itself (typically called C Drive) and another boot partition with a minimum size of 100MB. The boot partition is not encrypted by Bitlocker, as it is required for the system bootstrap process.
Bitlocker may be used in conjunction with the encrypting file system to provide increased security. The encrypting file system or EFS is another security feature for Microsoft Windows that was introduced for NTFS version 3.0 and above. It is supported on all Windows systems from Windows 2000 onwards.
EFS provides filesystem level encryption for the user while the operating system is running. This provides an additional layer of protection.
Both Bitlocker and EFS make use of 256 bit AES in CBC mode for its encryption needs. EFS also has several other algorithms to choose from.
Full disk encryption in other Operating Systems
Full disk encryption is not a new concept and there are many alternatives for it. Full disk encryption is supported by different operating systems in varying degrees.
- Linux supports two alternatives for full disk encryption, eCryptfs and dm-crypt. eCryptfs provides stacked file system level encryption. This is similar to EFS on Windows.
- FreeBSD provides full disk encryption through the GBDE (GEOM based Disk Encryption) framework. GBDE only supports 128 bit AES however.
-
FreeBSD also has another full disk encryption framework called GELI. GELI has support for many cryptographic algorithms such as AES, Blowfish, Triple DES, etc.
7. Improved Cryptography
Windows 7 features several enhancements in its Cryptographic subsystem. There are several new cryptographic algorithms to choose from, including Blowfish, AES, Triple DES, etc.
Windows 7 also includes support for Elliptic curve cryptography. The Kerberos protocol in Windows 7 has been updated to use AES encryption over DES.
The Windows LAN manager has been updated to use NTLM2 hashes by default instead of SHA1 or MD5 hashing algorithms.
8. Windows Firewall/Defender
Windows 7 includes a new and improved Windows Defender. Windows Defender is an anti-spyware and anti adware software that is included as part of the operating system itself. Windows Defender can be updated like an Anti-virus solution.
Windows Firewall is a host based firewall that is included with each copy of Windows. It has been extensively overhauled in Windows 7. It now provides full support for IPsec. Windows firewall also makes use of a new framework called Windows Filtering Platform (WFP). WFP provides improved packet filtering capabilities that are integrated into the TCP/IP stack.
9. Improved Authentication Mechanisms
Better authentication support was introduced in Windows 7. This includes support for Biometric access and Smart cards. User accounts can be authenticated using two-factor authentication, i.e. a combination of password and smart card.
The single sign-on feature has also been introduced. This can be used with smart-cards which can also be integrated with several other security services such as EFS. Winlogon has been upgraded from GINA (Graphical Identification and Authentication) to the Credential provider library. It also supports NTLM2 by default for generating password hashes. This is a significant improvement from the deprecated NTLM hashing algorithm. Winlogon is the interactive login manager for Windows based systems.
References
http://en.wikipedia.org/wiki/Address_space_layout_randomization
http://en.wikipedia.org/wiki/Security_and_safety_features_new_to_Windows_Vista#User_Account_Control
http://en.wikipedia.org/wiki/Data_Execution_Prevention
http://en.wikipedia.org/wiki/Windows_7
http://en.wikipedia.org/wiki/Encrypting_File_System
http://en.wikipedia.org/wiki/Domain_Name_System_Security_Extensions
http://www.microsoft.com/security/sir/strategy/default.aspx#!section_3_3
http://blogs.technet.com/b/srd/archive/2009/02/02/preventing-the-exploitation-of-seh-overwrites-with-sehop.aspx
http://www.dribin.org/dave/blog/archives/2006/04/28/os_x_passwords_2/
https://support.microsoft.com/kb/875352
http://support.microsoft.com/kb/956607
http://www.ghacks.net/2012/07/16/advanced-windows-security-activating-sehop/









