Benefits of using a third-party pentesting company
Benefits of pentesting
The process of penetration testing (pen testing) is one of the best ways to visualize one’s own computer system—including its potential flaws and weaknesses—through the eyes of an outsider. It allows users to view the digital landscape from an threat perspective by launching a simulated cyberattack against a friendly computer system and looking for exploitable vulnerabilities. As a security measure, pen testing enables companies to:
- Avoid financial damage
- Enjoy uninterrupted service
- Manage risk more effectively
- Avoid client-side cyber attacks
- Improve existing security posture
- Assess response time to security threats
- Comply with existing security regulations
- Better protect themselves and their clients
- Protect their reputations and their product

FREE role-guided training plans
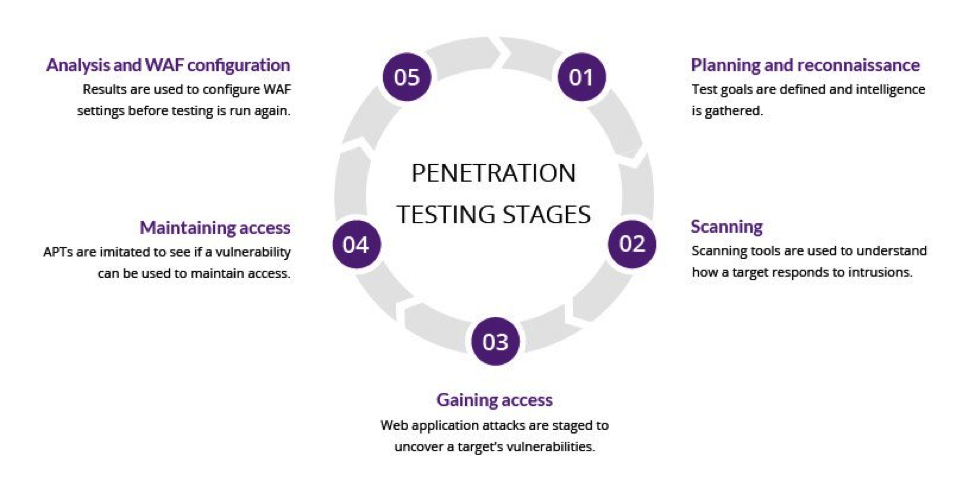
Pen testing involves a few stages:
- Planning and reconnaissance:
Define the goal of a test.
Locate systems to be addressed.
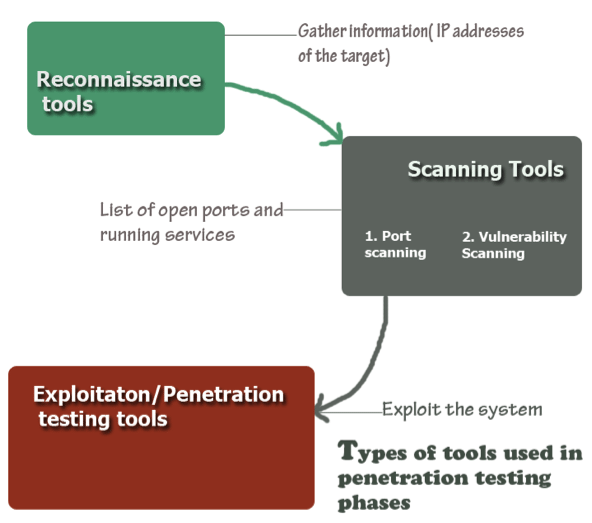
Find proper testing methods to use. - Scanning: Use static analysis to inspect an application’s code to assess how it behaves while running. Use dynamic analysis to inspect an application’s code while running. This allows for more practical scanning and offers a real-time view of overall performance.
- Gaining access: Use web application attacks like SQL injection, backdoors, and cross-site scripting to uncover weaknesses. Try to exploit these vulnerabilities by escalating privileges, stealing data, intercepting traffic, and such. This will provide information about how much damage they can cause.
- Maintaining exploit: Can the vulnerability be used to achieve an advanced persistent threat to a system, long enough for a hacker to gain deeper access? Given an attacker can hang out in a system for months before being detected, this is important information to have.
- Reviewing results: Use the results of this pen testing to compile a report noting specific vulnerabilities, the data that was accessed, and the amount of time spent without detection.
The third-party attacker
Sometimes trying to determine just how susceptible an organization and its infrastructure are to attack is difficult. But given the pressing importance of the question, there is no alternative to taking on the challenge with robust solutions. To answer this ongoing demand for understanding, many security consulting companies and Big Four auditors have started offering pen testing services to their clients. This specialized approach of “friendly cyberattack” can be a great way to evaluate the security of information systems and determine their readiness for the real virtual world.
The objective of this third-party testing is to probe around a system in an attempt to identify weaknesses and/or security holes in all areas of an organization, from online applications to supporting network landscapes to physical aspects of the premises. Unlike a simple vulnerability assessment, which only identifies weaknesses, a pen test will go the extra distance by actively exploiting any holes and establishing a deeper sense of potential risk. The vendor should then report all findings with complete honesty and transparency, as well as offer some realistic suggestions for improvement. Herein lies the main risk involved with third party pen testing, however, as not all providers have proven themselves trustworthy in the past. As a result, any organization looking to hire third party testers must review some essential points and critical questions before moving forward. The best way to do this is to thoroughly analyze the risks associated with both threat and vulnerability. Risk = Threat X Vulnerability
What are the risks of hiring a third-party pentester?
- Certain vulnerabilities or weaknesses could be missed by a low-quality provider.
- Sensitive information could be inadvertently damaged during a unprofessional pen test.
- The service provider could potentially reveal, abuse, or even lose sensitive information found during the scheduled pen test.
Like all services, third party pen testers range from the ultra-secure and professional to the mediocre to the downright corrupt, so it is up to the client to conduct the proper amount of due diligence when hiring such providers. And the of course, there is the matter of cost to consider, not to mention timeliness. High-quality providers should be able to report back to clients in an accessible, non-technical way that allows all facets of management to understand the findings. In most cases, employee actions factor into the efficacy of overall cybersecurity, so knowledge about pen testing results does not reside only with IT and security workers. It is just as important for Bill in accounting to understand the consequences of opening a strange email as it is for Jane in security management to visualize attack vectors.
Given these risks, why hire a third-party pentester?
- Outside vendors are more likely to find vulnerabilities the internal team hasn’t located.
- DIY network pen testing by unskilled professionals can lead to sluggish performance, possible downtime, or even a system crash leading to major business disruption.
- To provide clients with the assurance of expert online security in critical areas like storage, transactions, and data access.
- To ensure pen tests are performed by actual experts and skilled auditors (rather than inexperienced employees) who conduct such exercises on a regular basis, using best industry practices.
- To measure the quality of an organization’s incident management procedures, response time, and overall efficacy.
- Because it’s cheaper than training or hiring pen testing experts!
What constitutes a “high-quality” third-party pentester?
Communication: A good service provider should ensure the client has a clear objective for the test, with a realistic scope outlined in a formal proposal. A plan with limited scope, like one that applies only to a single system or application, may miss the chance to identify vulnerabilities in trust relationships between the target and other systems or some kind of end-user error. This step ensures both parties are on the same page and working toward a shared goal. For example, when the provider comes across a vulnerability in the system, should it just be recorded or actively exploited to confirm the finding? To avoid any misunderstandings, both parties must review and practices and agree upon how they will be carried out. The provider should also provide users with a single point of contact in case of emergencies.
Timing: Establishing a clear sense of when a pen test will be performed and how it can best avoid interrupting existing services is critical to a successful relationship between client and vendor. Defining this timetable may include delays to avoid times when the company is at work, or it may seek to intentionally run the test during operative hours to create the most authentic real-life scenario. Once the schedule is set, all parties should stick to it!
Non-Disclosure: During a pen test, sensitive information—like client data, trade secrets, and personal details—often comes to light, which means service providers should be willing to sign a non-disclosure agreement promising to respect the privacy of the company and never, ever share these findings with other entities, or worse—sell them.
Documented methodology: All third-party providers should be able to show clients their own, well-assembled testing methodology before work begins. Further, this documentation should make use of the commonly accepted manual known as Open Source Security Testing Methodology (OSSTMM). As a professional guide dedicated to a deep understanding of operational security and the interconnectedness of people, processes, systems, and software involved.
Insurance: All pen testing providers should have liability insurance capable of covering the price of data loss or any other revenue-damaging effect. This piece should be clearly detailed in their “Terms and Conditions” which will inform clients what to expect in the event of an unforeseen testing incident.
Of course, there are many other factors to consider when choosing a third-party provider, including overall competence, success rate, meaningful representation, positive references, and technical support. So regardless of the challenges involved with finding the right service, the benefits make the whole endeavor entirely worth it—and really, non-negotiable.
What’s the best way to evaluate third-party pen testing companies?
A pen test is only as good as the person implementing it, so it’s important to hire with integrity. When actively searching for the right provider, consider these areas:

What should you learn next?
- The scope of the pen test. What is the main objective of the pen test?
- The company’s overall qualifications and experience. Do they have specialized pen testers with full credentials and quality experience?
- The importance of social engineering. Should the test focus solely on the technical or include social engineering and phishing attacks to assess the human component of security?
- Deliverables at the end of the process. Will the company provide an acceptable service report at the end of the pen test?
- The value of regularity and consistency. Does the company offer ongoing scheduled tests for the future?
- The right price. What does the test cost and under what circumstances might the price go up?
- References are reassuring. Can the third-party tester provide testimonials or references from other customers?
While there are some significant risks involved with third party pen testing, the benefits found in a high-quality service can’t be denied. They offer increased knowledge, ability, and overall security to organizations who rely on their virtual strength to keep business flowing. Professionals looking to implement real security changes in their computer systems should be ready to collaborate with third party experts and use this knowledge boost confidence and strength.