Discovering entry points
When people secure real world physical objects for example bank premises, they first secure obvious entry points like entrance, doors, exists and much more where from intruders will most likely attempt to gain entry. So, Entry Point is a point of failure that might enable a vicious intentional person to break the application and cause damage. For instance, you might duly lock your car along with all the windows, but you still offering access to your car to some extent. Could someone bypass the lock security without even having keys? Hence, you also need to examine your application security structure in the same way. Throughout this article, we shall dig in various entry points in software, website, etc... Moreover, ways to determine whether your application is applying them.
Essentials
As this article is designed to explain various entry points of a web or application software which typically, are points of interest for a hacker for exploitation. Thus, the seeker is supposed to have comprehensive indulgence including in code drafting, various website API involvement, and manipulation with systems commands, configuring environment variables, and cognizance about URL handlers, etc… in a moderate manner. Moreover, cognizance with a couple of tools related to process explorer, traffic monitoring, sniffing, must require.

FREE role-guided training plans
Entry points
An entry point where from input can be provided to your application is the finest place to breach the software. For security testing, it is required to have a good understanding of software data flows or inner working, so that weak points could be identified. However, you can't test every single piece of software as thoroughly as you might like. You need to prioritize where you will spend your time testing. In this context, DFD (data flows datagram) can be more conducive to find security threats in software. It is important that a security tester is aware of the entry points and how potentially malicious data can enter into the software. Some vulnerable points are fairly easy to identify just by thinking about the application. However, in some cases, it might be possible DFD or threat model for an application is no longer available. In fact, hackers generally, won't have any threat model blueprints available. Thus, they resort to special tactics which shall be discussed throughout this article in the forthcoming sections, how to gain and maintain access to an application without its DFD blueprints.
Listing common entry points
In this section, some the most common entry points that hackers typically adopt to probe for security loopholes in the software, are discussed in more detailed form.
Socket
Socket consist of an IP address and a port number is a bidirectional communication between applications owing to various protocols. Sockets are easy to connect to, and the data going over the network is not always safe. Sometimes, it can be extremely dangerous if the entry point found in the form of 'open' socket that is not well protected too. A hacker can monitor data, send malformed data from client/server, intercept data and perform MITM attack while data is being sent over a network in case of the open socket. If your application uses sockets, then the threat modeling process should have identified the availability this entry point. Windows OS shipped with a command line utility netstat.exe which helps you determine or enumerate open connections (sockets) along with process id as following.
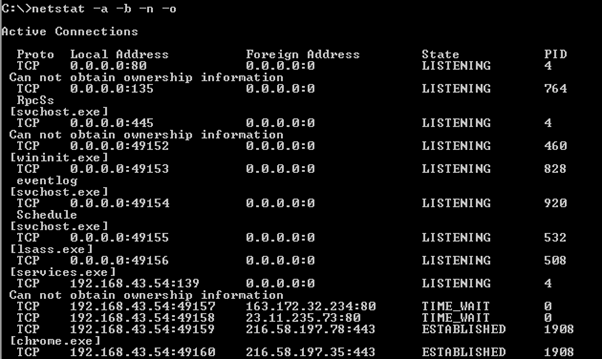
Figure 1: Netstat utility for listing open socket connections
Another method is to monitor the network traffic, if your application sends or receives data from the network using various network sniffing tools such as Ethereal, Wireshark or much more. You need to determine what is packets is carrying or contains. For example, hackers might seek for sensitive information.
Registry
The registry is a sort of hierarchical database of Windows operating system, enables installed application to store setting in the five keys that can be retrieved later. However, registry keys could be compromised and manipulated hackers accordingly even without having local access. For instance, they can trick a user into opening a rogue .reg file and then next time his data could be used. There are typically five registry keys in Windows operating system as;
- HKEY-USER
- HKEY_CURRENT_USER
- HKEY_LOCAL_MACHINE
- HKEY_CLASSES_ROOT
- HKEY_CURRENT_CONFIG
Permission over registry key portrayed a significant role for accessing particular stored data. The application generally, employed registry to store data such as database connection string, credentials, etc… for run-time retrieval. If the permission on these keys is set incorrectly, numerous exploitable cases could be occurring such as information disclosure, privilege escalation, buffer overflow, DDOS and much more.
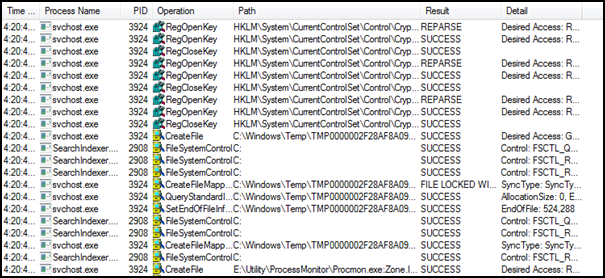
Figure 2: Process Explorer utility for gathering Registry key information
Which registry key are being accessed and permission on that key are two points of interest for a hacker and security tester in term of unleashing this entry point. You do not have access to source code, so it is almost impossible to determine which registry key is being accessed. For this, Process Explorer tool, you can judge which key is opened, read, or written for your application process. For determining permission, on the other hand, regedit.exe utility discloses the information as:

Figure 3: Regedit utility to view registry key permission
Programmatic interface
Programmatic Interface such as COM, DCOM, RPC's, ActiveX, and .NET Remoting enables communication between applications located on diverse platforms. Programmatic interface unfolds much functionality that an attacker can exploit as they are intended to be used by the application or run in the certain specific environment. However, detailed discussion about every programmatic interface is out of the scope of this paper, but certain tools might be conducive to enumerate programmatic interfaces used on computer as following;
- OleView: This tool views all the COM objects and their interface registered on the computer.
- Dcomcnf: This utility decomposes all the DCOM objects running on the computer.
- RpcDump: It displays all the RPC endpoints on a computer.
- Gacutil: It enlists all the managed assemblies that are registered on the computer.
Environment variable
System and application typically used an environment variable to store information such as path about current configuration environment and currently logged-on user. The system defines these variables and utilized by all computer users. However, data will not be safe if a program makes security decisions based on the stored information in those variables. However, hackers could only change the environment variable, unless they have compromised administrator account. From My Computer, select Properties, click the Advance tab, and then click the Environment variable button as;
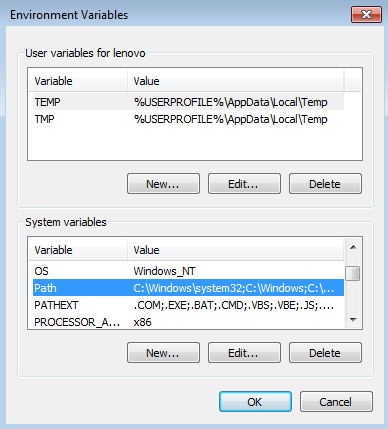
Figure 4: Environment variable configuration
'Process Explorer' tool determines which your application uses environment variable at runtime. The following figure is showing the environment variables used by 'Web Text Convertor' tools as following:
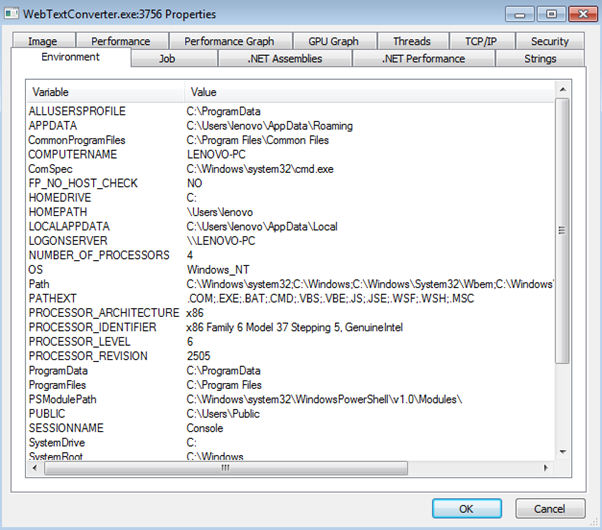
Figure 5: Process Explorer utility to view variables
Command-line argument
Command line argument supply data to perform certain functions in the application. This attack could not be triggered unless the hacker somehow tricks a user into typing in the malicious command line argument. Hacker might change the behavior of the application altogether to fulfill their vicious intent. For example, what if the hacker includes a command line to delete the file instead of opening it. By using /? -?, or –h, the application will reveal information about its usage, but the application could accept other arguments which never specified in the documentation. Process Explorer is a great utility to determine what the command line argument for an application when it is being launched. Here, an attacker might use the undocumented switches that can change the behavior of an application as;
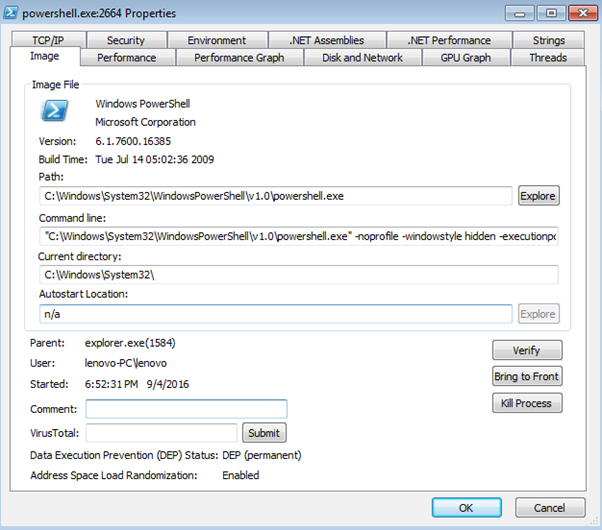
Figure 6: Process Explore to view extra CMD line arguments
Protocol handlers
Protocol handler starts with http or https, state the system which application is invoked to handle the data when the hyperlink is clicked. They enable a website to launch an application and easily perform the function for the user. However, protocol handlers could be dangerous if the calling application contains any confidential information. As they allow data to be passed to the registered application, they also become entry point that must be scrutinized for loopholes. It typically determines during the threat modeling whether your application installs a protocol handler. A tool called ViewPls.exe enumerates all of the protocols handlers on the machine and the application that handles them as following;
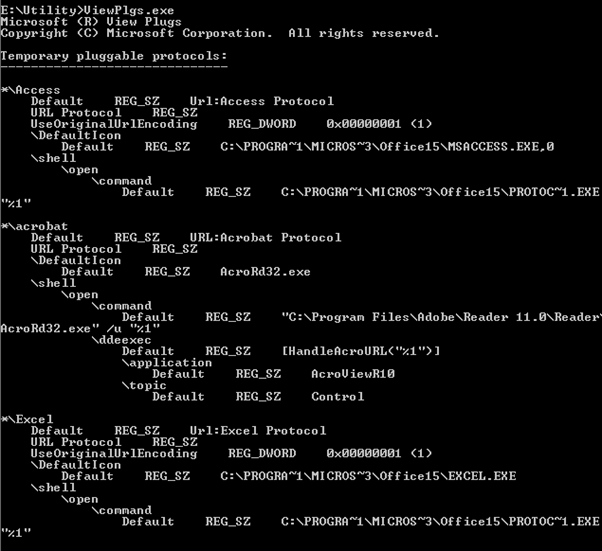
Figure 7: ViewPlgs.exe to view protocol handlers
Http header
HTTP typically uses ports 80 and operates over TCP protocol, enables data communication between client and server. It is popular because of its simplicity, here the clients (any browser such as Mozilla, Chrome are the client of HTTP) send the request to the server. If server processes the request, that request is an entry point into the system. To determine, whether an HTTP request is a vulnerable entry point, decompose the request into smaller sub-parts to figure out the entry points for your application as following;
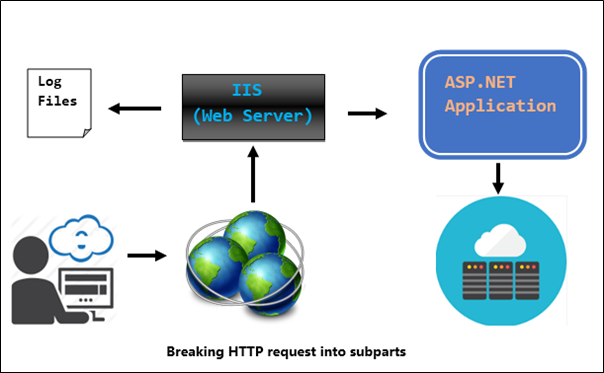
Based on the figure above, you can determine entry points on the ground of some conclusion like cookies, parsing of the query string or URI, View-state, Header (User-Agent/ Referrer), and ISAPI filter. The beauty of HTTP is that it is almost always allowed to pass through firewalls, which streamline the job of a hacker to easily send an HTTP request to an application that accepts such request. He can manipulate request freely in pursuit of breaking in. To detect vulnerability related to such entry point, traffic monitoring over HTTP port on 80 would be an appropriate undertaking.
Securing entry points
The software you are testing accepts inputs that can come directly from the user. However, it is not always obvious when input might cause a security vulnerability. In fact, no security flaws are exploited when the data is first entered into the application in some circumstance. In security testing, it is important that you first identify and scrutinize such entry points as follows
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
- Never rely on the accuracy of DFD and threat model. Otherwise, you miss entry points.
- It is rather a good idea to attack yourself the suspected vulnerability (entry points).
- Categorized high-level entry points for penetration testing perspective.
- Calculate the level of access needed for each entry points.
- Determine the level of damage an entry point can cause.
Conclusion
Entry points enumerated in this articles enables data that is potentially regulated by a hacker to gain access to an application. Hence, it is a good programming practice to assume earlier any input that originates from these sources is potentially malicious. It is crucial in security testing to identify as many entry points as you can. The best to way to defense against such type of attacks, the more you research about your application regarding entry points, better you will be able to target your security testing efforts, and otherwise hackers could exploit the vulnerabilities that you missed.
Sources
- Microsoft Support
- Archive - MSDN blog
- Protocols - W3
- Microsoft support
- Sysinternals







